Distributed Cloud Firewall Overview
Distributed Cloud Firewall (DCF) uses micro-segmentation to provide granular network security rules for distributed applications in the Cloud. Distributed Cloud Firewall enables network policy enforcement between SmartGroups, GeoGroups, or ThreatGroups you define in a single cloud or across multiple clouds.
|
Aviatrix strongly recommends using Distributed Cloud Firewall and its integration with GeoGroups and ThreatGroups to monitor for threats and enable geoblocking. If you are an existing user of ThreatIQ and/or Geoblocking (prior to Controller version 7.2.4820), use these migration recommendations to start using DCF with GeoGroups and ThreatGroups. You cannot use ThreatIQ and/or Geoblocking in conjunction with DCF and ThreatGroups/GeoGroups. |
Supported Cloud Providers and Gateways
Distributed Cloud Firewall is supported for the following clouds:
-
AWS, AWS GovCloud, AWS China
-
Azure, Azure Government, Azure in China
-
GCP, Google for Government
-
OCI, Oracle Government Cloud, Oracle China
The following gateway types are supported:
-
Spokes attached to a Transit Gateway
-
Spokes detached from a Transit Gateway
-
Public Subnet Filtering Gateways (enable PSF Gateways with DCF here)
-
External connections (Site2Cloud) (enable External Connections with DCF here):
-
Terminating on a Spoke Gateway
-
Terminating on a Transit Gateway (L4 only)
-
-
Edge as Spoke Gateway (L4 only; non-CSP tag)
| DCF rules will not be applied to traffic originating or terminating on Aviatrix gateways. |
Minimum Spoke Gateway Sizing
-
3583MB required for L7 with IDS
-
3583MB required for IDS and TLS Decryption
Minimum Spoke gateway sizing is provided in the following table.
| Cloud | L4 only | L4 with External Groups | L7 with TLS Decryption only | L7 with TLS Decryption and IDS |
|---|---|---|---|---|
AWS |
t3.micro or equivalent (non-production only) |
t3.medium or larger |
t3.small or equivalent |
t3.medium or larger |
Azure |
Standard_B1ms |
Standard_B2s |
Standard_B1ms |
Standard_B2ms |
GCP |
n1-standard-1 |
n1-standard-2 |
n1-standard-1 |
n1-standard-2 |
Distributed Cloud Firewall can be used to control Egress traffic by enabling Source NAT on the gateway configuration, and creating policies with WebGroups.
|
As of Controller 7.1, Distributed Cloud Firewall with WebGroups is the recommended method for configuring and implementing Egress Security. This document describes Egress functionality available in the Aviatrix Controller in Controller 7.1 and later. For information on configuring the legacy Egress FQDN solution, click here. Distributed Cloud Firewall is in Preview mode for earlier Controller versions. See Aviatrix Feature Availability by Controller Version for more information. |
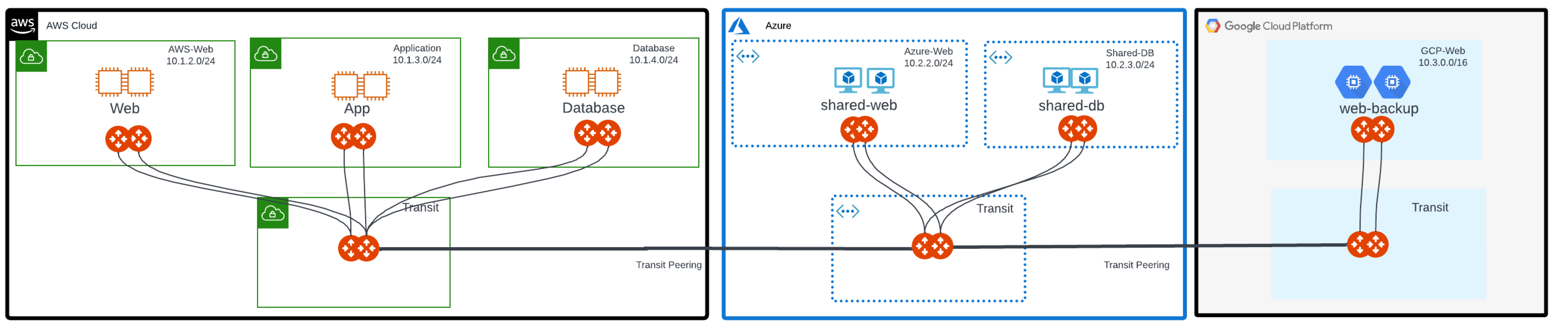
Use Cases
Use cases where you might implement Distributed Cloud Firewall are:
-
Workload isolation: in a typical tiered application, you may want to isolate tiers that do not require access to each other. For example, in a Shopping Cart application, there could be workloads for product inventory, billing, and a Product Logging app. Since the Shopping Cart application does not need to communicate with the Product Logging app, this traffic should be blocked.
-
Quarantine compromised machines: You can isolate a compromised machine by placing it in its own SmartGroup and blocking communication to that SmartGroup.