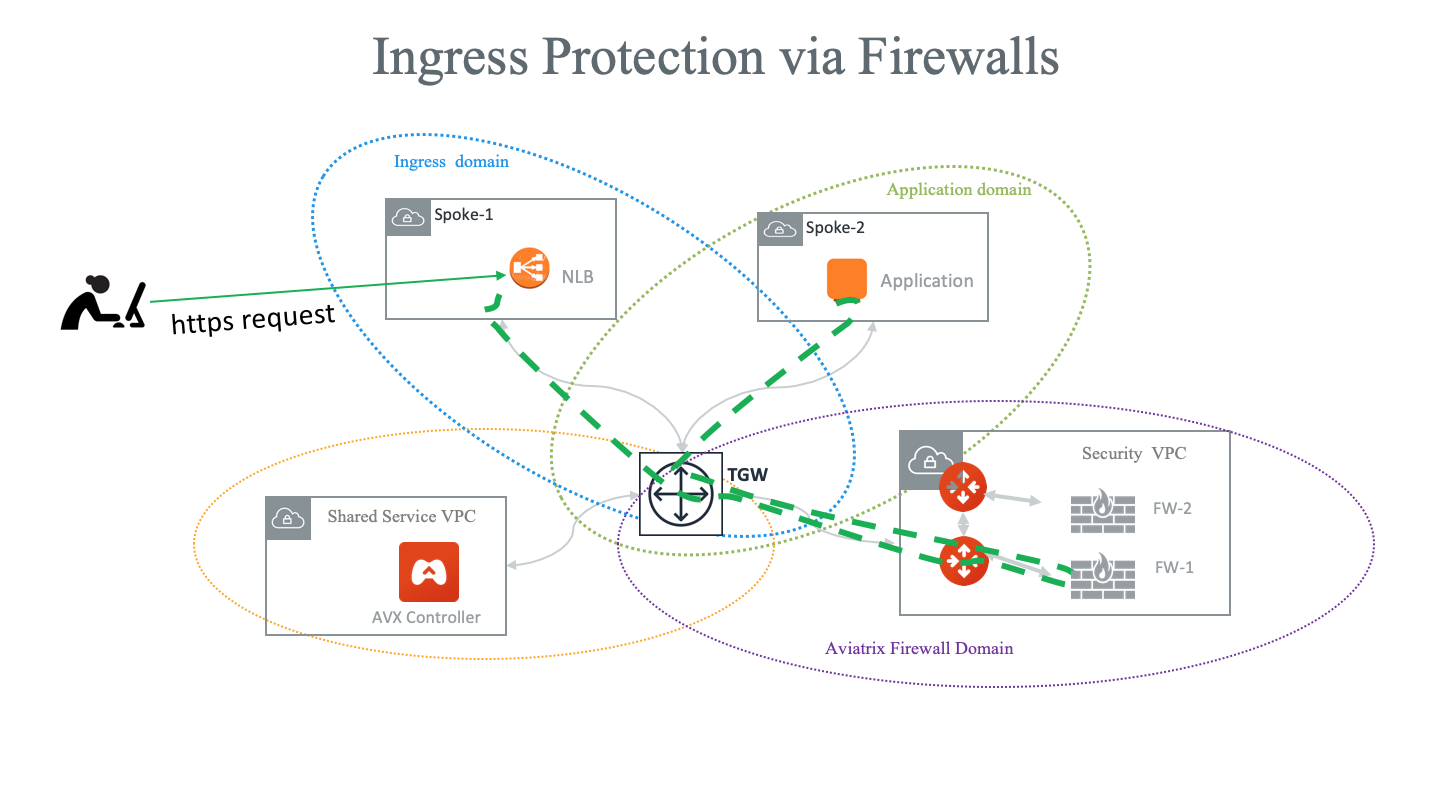
FireNet Ingress Traffic Inspection
| If the FireNet deployment is for both Egress and Ingress traffic, you need to SNAT on the firewall instance to its LAN or Trusted Interface IP (eth2 interface). The rule is that for a source IP address that comes from NLB or a vendor load balancer such as an F5 private IP address, it is translated to a firewall interface eth2 private IP address. |
Ingress Traffic Inspection
Follow the Ingress firewall instructions to deploy the solution for Ingress traffic inspection.
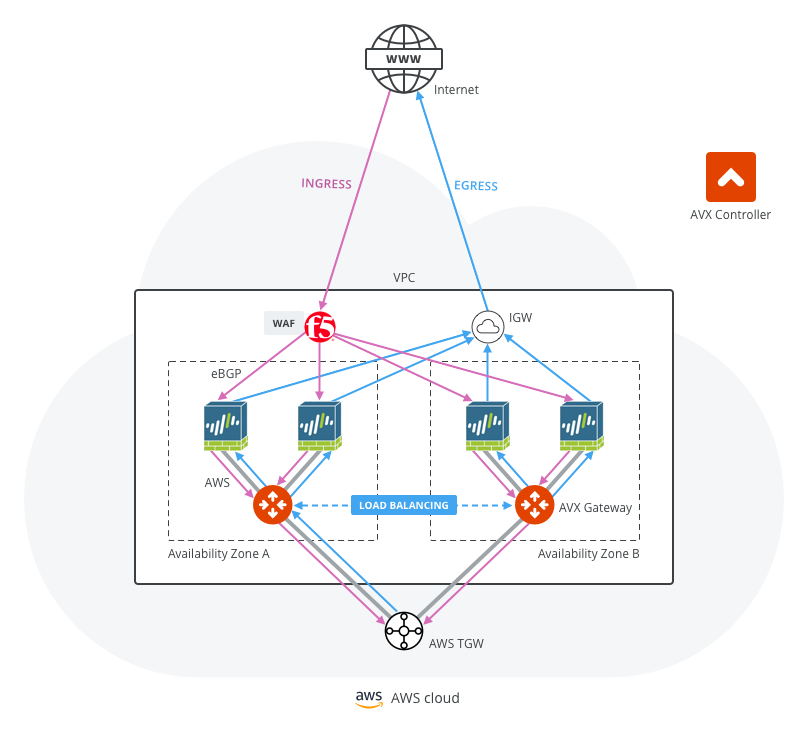
Ingress Directly through Firewall
Another often configured Ingress Egress design pattern is to have the traffic forward to firewall instances directly as shown in the diagram below. In this design pattern, each firewall instance must configure SNAT on its LAN interface that connects to the Aviatrix FireNet gateway. The drawback of this design is that the source IP address is not preserved when traffic reaches the application. If you need to preserve source IP address, refer to this recommended design for Ingress.
For more information, follow the FireNet workflow.
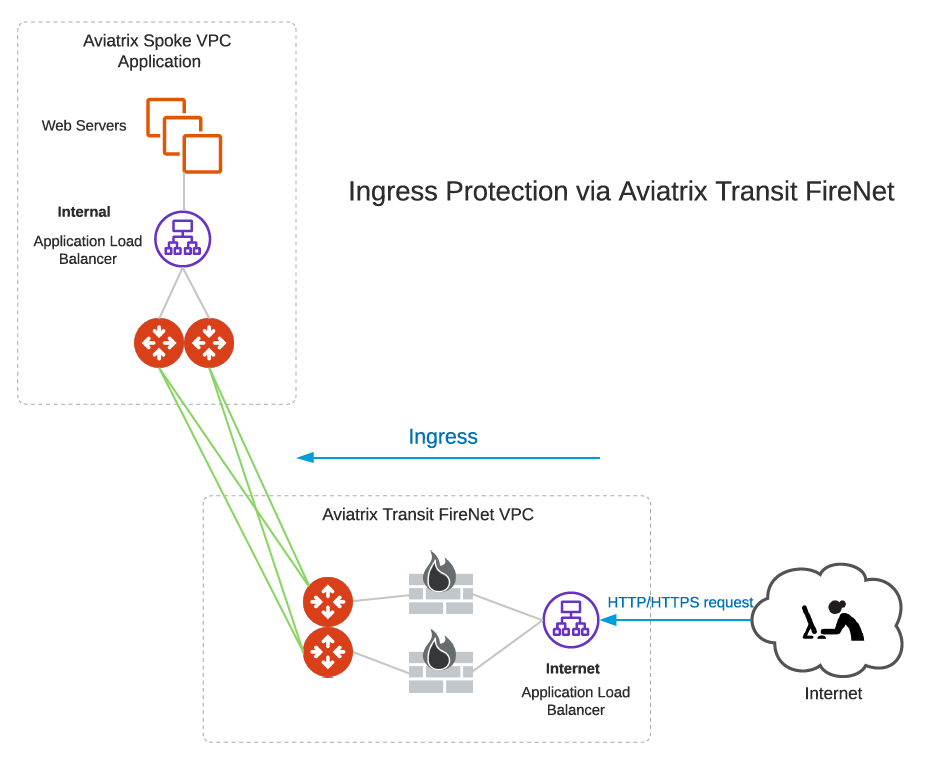
Ingress Protection via Aviatrix Transit FireNet
This Ingress Protection design pattern is to have the traffic forward to firewall instances directly in Aviatrix Transit FireNet VPC/VNet as shown in the diagram below. In this design pattern, each firewall instance must configure (1) SNAT on its LAN interface that connects to the Aviatrix FireNet Gateway and (2) DNAT to the IP of application server/load balancer. The drawback of this design is that the source IP address is not preserved when traffic reaches the application.
For an example configuration workflow, see Ingress Protection via Aviatrix Transit FireNet with FortiGate.