Network Segmentation
Aviatrix Multicloud Transit Network Segmentation provides network isolation and better security. It does this through network domains and connection policies. These apply to the Aviatrix Transit network. Both Spoke and Transit networks deploy Aviatrix Gateways across multi-region and multi-cloud.
The CoPilot Network Segmentation page enables you to configure network segmentation. It also shows visualizations of your network domains and how they can or cannot connect to each other. The key use case for building network domains is to segment traffic for an enhanced security posture.
| Aviatrix does not currently support duplicated CIDRs that cross domains or Transit networks. Overlapping CIDRs advertised from on-prem to different Spoke network domains connected to one Aviatrix Transit gateway is not supported. |
About Network Domains
When you identify groups of Spoke and Edge VPC/VNets in your infrastructure with the same requirements from a networking point of view (network reachability), you may want to group them so that you can apply connection policies at the group level. You can group them as members of an Aviatrix network domain. A network domain is an Aviatrix enforced network of one or more Spoke or Edge VPC/VNets. You use the network domains with connection policies. This achieves the network isolation for inter-VPC/VNet connectivity that you want for your network. You can have up to 200 network domains on each Aviatrix Transit Gateway.
The following diagram shows two network domains, one named Blue and one named Green.
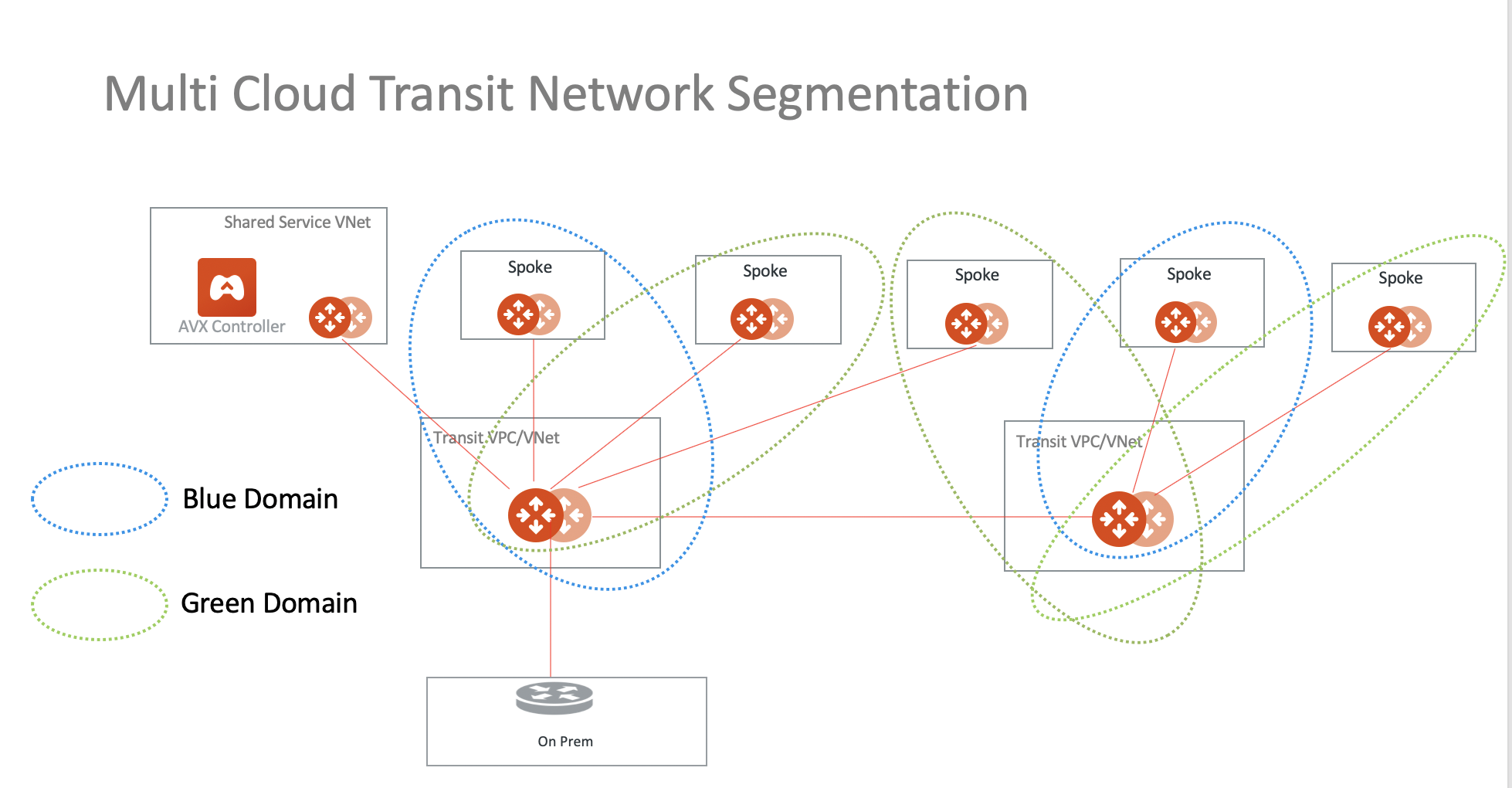
In the above diagram, Spokes associated with the Blue Domain can communicate with each other, and Spokes associated with the Green Domain can communicate with each other. However, there is no cross-communication between the Blue and Green Domains unless you configure a connection policy. These connection policies are implemented with Aviatrix Transit where both Spokes and the Transit VPC/VNet deploy Aviatrix gateways.
| This segmentation works with Azure native Spoke VNets. |
When you create a network domain, you give it a unique name, specify the Spoke and Edge VPC/VNets that are members of it, and specify any connection relationships you want it to have with other network domains.
Spoke and Edge VPC/VNets within a given network domain communicate with each other via an Aviatrix Transit Gateway that is enabled for network segmentation. You must enable Transit Gateways for network segmentation before creating network domains that will use those Transit Gateways for communication.
When a network domain is saved, the Aviatrix Controller dynamically programs and updates all applicable VPC/VNet route tables so that instances in different Spoke and Edge VPC/VNets in the same network domain can communicate with each other.
A network domain also applies to the hybrid connection from Aviatrix Transit Gateway to on-prem or remote sites. Each BGP peer or connection can be associated with one network domain.
Configuring Network Segmentation for Inter-VPC/VNet Connectivity
-
In CoPilot, go to Networking > Network Segmentation or search for Network Segmentation in the navigation search.
-
Enable network segmentation on each of the Aviatrix Transit Gateways in your network that will route traffic between network-domain members.
-
Create your network domains and connection policies.
-
Verify that your network segmentation.
Enabling Network Segmentation on the Transit Gateway
This section describes how to enable network segmentation for inter-VPC/VNet connectivity using network domains. You must enable network segmentation on all Transit Gateways that will route traffic between the Aviatrix network domains.
These instructions apply if you are using the Aviatrix CoPilot user interface to build network segmentation.
| You cannot enable a Transit Gateway for network segmentation if it is being used as a Transit FireNet. |
To enable a Transit Gateway for network segmentation:
-
In CoPilot, go to Networking > Network Segmentation or search for Network Segmentation in the navigation search.
-
In the Network Domain view, click Transit Gateways.
-
Toggle the network segmentation option to Enabled for each Transit Gateway in your infrastructure that will route traffic for the Spoke and Edge VPC/VNets that will be members of your network domains.
-
Click Save.
The selected Transit Gateways are now enabled for network segmentation.
If you disable network segmentation on a Transit Gateway that connects Spoke and Edge VPC/VNets that are members of a network domain, the Spoke and Edge VPC/VNets will no longer be able to communicate with each other using that Transit Gateway.
Creating the Network Domain and Connection Policy
Create a network domain to be used for network segmentation, which will also create a connection policy and associate a Spoke/Edge Gateway to the network domain. See also About Network Domains.
|
Before creating an Aviatrix network domain, verify that you have enabled network segmentation on the Transit Gateways that will route traffic for its members. TGW Domains only display in the Associations list if an AWS TGW has been attached to a Transit Gateway. |
To create a network domain:
-
In CoPilot, go to Networking > Network Segmentation or search for Network Segmentation in the navigation search.
-
In the Network Domain view, click + Network Domain.
-
In the Create Network Domain dialog, configure the following:
Field Description Name
Specify a unique name for the network domain. You cannot change the network domain name after it is saved.
A network-domain name can only have letters, digits, a hyphen (-), and an underscore (_). The name must start with a letter and must have 2-27 characters. For example, Dev_Domain.
Associations
Select the Spoke or Edge Gateway(s), or TGW Domain, that are to be members of this network domain. Network domain members can communicate with each other but cannot communicate with members of other network domains unless you configure them to do so in the Connect to Network Domain field.
The TGW Domain will display as <AWS TGW name>:<domain name>
After you select an association it is unavailable for any other network domains you create.
Connect to Network Domain
Specify the connection relationship of this network domain to other network domains. When you specify a connection relationship, it means the spokes in this network domain can communicate with Spoke/Edge Gateways of the other network domain.
| In the Associations drop down list, the associated Transit Gateway name is displayed beneath the name of the Spoke/Edge Gateway or AWS TGW that you select. |
-
Click Save.
When you save the network domain configuration, Aviatrix Controller dynamically programs and updates the applicable VPC/VNet route tables so that instances in different Spoke and Edge VPC/VNets in the same network domain (and in connected network domains, if applicable) can communicate with each other.
Network Domain Connections
It may be easiest to create network domains first, and then click the Edit icon ![]() to connect the domains (using the Connect to Network Domain field).
to connect the domains (using the Connect to Network Domain field).
Connecting network domains allows you to identify groups of Spoke and Edge Gateways/AWS TGW domains that have the same requirements from a networking point of view, and to apply connection policies at a group level. Two connected domains imply that Spoke and Edge Gateways in each domain can communicate with each other despite being in different domains.
Verifying the Network Segmentation Configuration
-
In CoPilot, refer to the Networking > Network Segmentation > Logical, Physical, or Regional View visualizations. You should see your network domains. See Network Segmentation Visualizations for a description of the visualizations.
If there are no network domains configured, or there are no gateways attached to network domains, you see a message to this effect on the Overview tab. -
Log in to compute instances that are running in separate Spoke and Edge VPC/VNets that are members of the same network domain and verify they are allowed to connect to each other and not allowed to connect to Spoke and Edge VPC/VNets that are not members of the network domain.
-
Log in to compute instances that are running in different Spoke and Edge VPC/VNets that are members of different network domains that have a connection relationship and verify they are allowed to connect to each other.
Managing the Network Segmentation Configuration
Editing Your Network Segmentation Configuration
To edit a network domain:
-
On the Networking > Network Segmentation > Network Domains tab, click the Edit
 icon.
icon. -
In the Edit Network Domain dialog, configure the following:
Field Description Associations
Select the Spoke or Edge Gateway(s), or TGW Domain, that are to be members of this network domain. Network domain members can communicate with each other but cannot communicate with members of other network domains unless you configure them to do so in the Connect to Network Domain field.
The TGW Domain will display as <AWS TGW name>:<domain name>
After you select an association it is unavailable for any other network domains you create.
Connect to Network Domain
Specify the connection relationship of this network domain to other network domains. When you specify a connection relationship, it means the spokes in this network domain can communicate with Spoke/Edge Gateways of the other network domain.
Note the following points about changing a network segmentation configuration:
-
For Transit Gateways that route traffic in your segments, you can disable them from network segmentation. You should only do this if there are no longer network domains relying on them for connectivity.
-
For a given network domain, you can change its members (disassociate a Spoke or Edge gateway from it or associate new Spoke or Edge Gateways to it) and connection relationships to other domains at any time.
-
If you decide to switch network domains for a given Spoke or Edge Gateway, you must first disassociate the Spoke or Edge Gateway from the network domain it is currently a member of before associating it with another network domain. For example, if you want a Spoke to be in Domain_Dev instead of Domain_Prod, you must first remove the Spoke from the associations list of Domain_Prod and save the domain, and then add the Spoke to the associations list of Domain_Dev and save the domain.
-
Currently, you cannot change the name of a network domain after it has been saved. If you want to use a different name for an existing network segment, you must disassociate all Spoke and Edge Gateways and connection relationships from them and create a new network domain with those configurations with the new name.
-
Network Segmentation Visualizations
In Networking > Network Segmentation > Overview, CoPilot uses visual elements to demonstrate the segments of your Aviatrix transit network that can and cannot communicate with each other if you created Aviatrix enforced network domains. The segments (network domains) and their ability to communicate with each other is dictated by the connection relationships you configure. You can enable network segmentation in Aviatrix Controller or in Aviatrix CoPilot. After your network segmentation configuration is enabled and saved, CoPilot dynamically shows the logical and physical view of your network-domain segments and their connection relationships in the network graph logical and physical views.
In Logical View, CoPilot lists the defined network domains and shows how they can and cannot communicate with each other (Network Domain Relationships). CoPilot also shows the connectivity between gateway VPCs/VNets (Spoke/Edge or Site2Cloud instances) based on their network domains (Multi Cloud Network Domain Connectivity). The thick colored lines on the circle’s edge represent the network domain assigned to the gateway’s nodes resting on them and the thin colored lines within the circle represent the connectivity between the gateways.
In Physical View, CoPilot shows how Spoke/Edge VPCs/VNets can communicate with other spoke VPCs/VNets based on their allowed network-domain connection relationships. When you hover over a Spoke/Edge node on the circle, the thin colored lines within the circle represent the connectivity from that Spoke/Edge to other Spokes/Edges allowed to communicate with it.
In Regional View, CoPilot shows how Spoke/Edge VPC/VNets can communicate with other Spoke/Edge VPC/VNets based on their Gateway Regions. When you hover over a Spoke/Edge node on the circle, the thin colored lines within the circle represent the connectivity from that Spoke/Edge to other Spokes/Edges allowed to communicate with it.