About Groups
Groups in CoPilot serve as versatile constructs for organizing and managing Aviatrix resources within multicloud networks. These groupings allow for the logical organization of resources across different subscriptions, cloud accounts, regions, and VPC/VNets, catering to various organizational structures or aspects. They are reusable and support seamless querying for diverse Aviatrix features. While some groups focus on filtering and securing internet-bound traffic, others aid in threat protection, provide geographical context for implementing location-based policies, or provide access to SaaS-based services such as Azure and GitHub. Together, these groups offer a comprehensive solution for resource organization, security, and management within Aviatrix deployments.
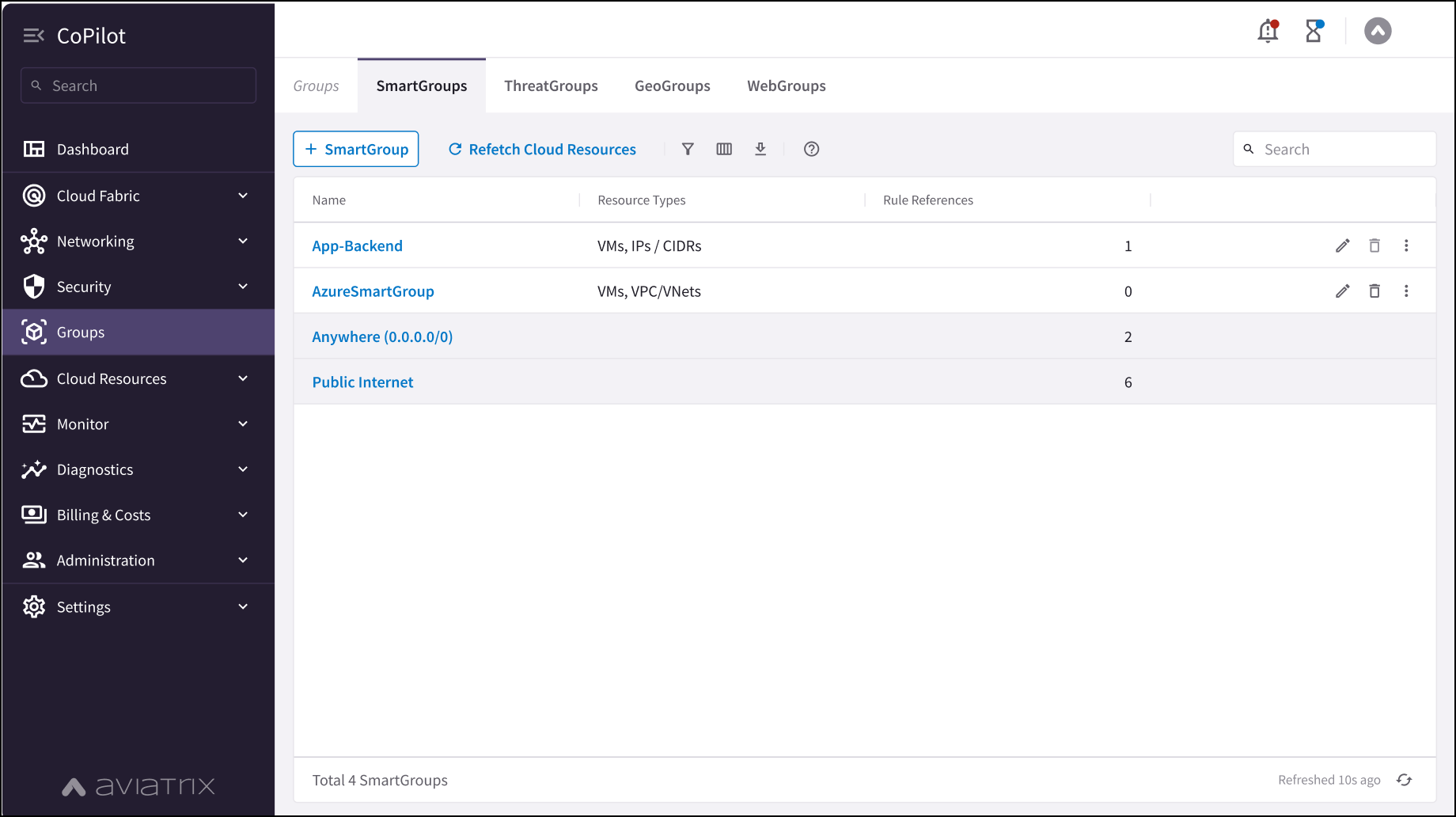
The available group types are:
-
ExternalGroups: Use the pre-populated data from the Feeds tab to create ExternalGroups. These groups can contain countries, threat feeds, and SaaS-based services (Azure and GitHub).
You can clone SmartGroups and ExternalGroups by clicking the vertical ellipsis icon ![]() next to the group and selecting Clone SmartGroup or Clone ExternalGroup.
next to the group and selecting Clone SmartGroup or Clone ExternalGroup.
|
You must create the groups (SmartGroups, WebGroups, ExternalGroups) and external connections you need before creating any Distributed Firewall rules that utilize these groups or external connections. WebGroups and ExternalGroups are only visible if the Distributed Cloud Firewall feature is enabled. |