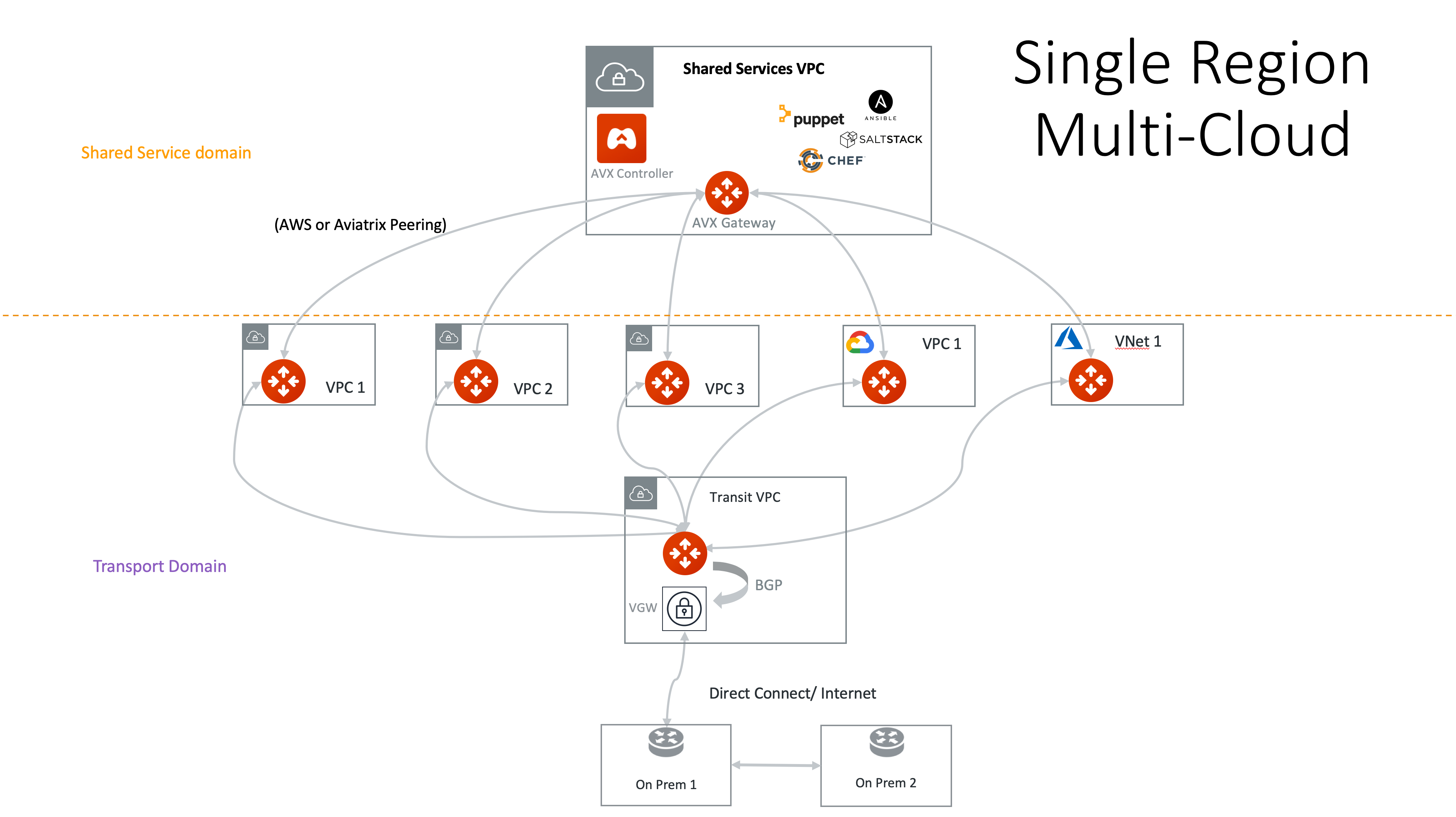
Single-Region Multicloud Transit Network Workflow
This document provides instructions to build a hub-and-spoke network model across multiple clouds in a single-region with Aviatrix Spoke and Transit Gateways.
The hub-and-spoke model consists of an Aviatrix Transit Gateway and a set of Spoke Gateways, as shown in the diagram below. The network traffic flows between the Spoke VPCs through the Transit VPC.
Prerequisites
-
If you have not launched an Aviatrix Controller, refer to the following Guides for your Cloud Service Provider:
-
If this is your first time using Aviatrix, make sure to go through the Controller on-boarding process and create an Aviatrix account that corresponds to an IAM role.
-
Identify a VPC or VNet in a region where you want to launch the Transit Gateway, and name it Transit VPC or VNet.
We recommend using the Aviatrix Create a VPC tool with the option Transit + FireNet to create a Transit VPC/VNet that has all the necessary subnets and route tables fully populated. For a Transit network in AWS, see Prerequisites for a Transit Network in AWS.
-
Create a VGW or reuse an existing VGW.
The VGW should not be attached to the Transit VPC or VNet if you plan to launch Transit Gateway in the same VPC or VNet. This VGW can be attached to a different VPC or VNet if this VPC or VNet CIDR is different from the Transit VPC or VNet where the Transit Gateway is launched or in a different region and account. This VGW should be connected to on-premises either over Direct Connect or over the Internet.
Configuration Workflow
While the instructions below reference AWS, the workflow applies to any public cloud in which Aviatrix Transit Network is supported.
Follow these steps to build a single-region multicloud Transit Network:
Creating a Transit Gateway
To create a primary and Highly Available (HA) Transit Gateway instances, provide the Transit Gateway general details, then assign the subnet and IP addresses for the gateway instances.
-
In Aviatrix CoPilot, go to Cloud Fabric > Gateways > Transit Gateways tab.
For quick access, at the top of the navigation panel, type Transit Gateways in the search bar. -
Click + Transit Gateway and provide the following general information.
Parameter
Description
Name
A name for the Transit gateway.
The name must begin with a letter, may include only letters, numbers, underscores, and dashes (excluding special characters or spaces), and must not exceed 50 characters in length.
Cloud
The Cloud Service Provider (CSP) where to create the Transit Gateway.
When you select AWS and Azure, you can use the dropdown menu to select Standard or Global, China, or GovCloud.
Account
The cloud access account for creating the Transit Gateway.
Region
The cloud region in which to create the Transit Gateway.
VPC/VNet
The VPC or VNet in the selected region in which to create the Transit Gateway.
If the selected Transit gateway will be used in a Transit FireNet workflow, selecting a VPC/VNet that has the Transit + FireNet function enabled means that a particular set of /28 subnets have been created across two availability zones. This function is enabled when the VPC/VNet is created.
Instance Size
The gateway instance size.
-
When selecting Transit Gateway instance size, choose a t2 series for Proof of Concept (POC) or prototyping only. Transit Gateway of t2 series instance type has a random packet drop of 3% for packet size less than 150 bytes when interoperating with VGW. This packet drop does not apply to Spoke Gateway.
-
When selecting the gateway size, note that the size you select affects your IPsec performance. You can change the Transit Gateway size later.
High Performance Encryption
To enable High Performance Encryption (HPE) for the Transit Gateway, set this toggle to On.
HPE enables 10Gbps and higher IPsec performance between two single Aviatrix Gateway instances or between a single Aviatrix Gateway instance and on-prem Aviatrix appliance.
You cannot set High Performance Encryption to On or Off after the Transit Gateway is created.
Support for IPv6
To enable IPv6 addressing and routing for the Transit Gateway, set this toggle to On
Fill the Account, Region, and VPC/VNet fields before enabling IPv6 support.
Attach to Transit Gateways
The Transit Gateway(s) to peer with this Transit Gateway.
In the Advanced Settings section, set the advanced gateway settings that may apply.
Parameter
Description
Transit Egress Capability (all clouds except OCI and Alibaba)
To add Transit Egress Capability to this Transit Gateway, set this toggle to On.
Transit Gateways that have Transit Egress Capability enabled can have attachments added in the Transit FireNet workflow, or be selectable in the Transit Egress workflow.
For Azure and GCP, selecting Transit Egress Capability must occur when the gateway is created. Otherwise, it will not display as an available Transit Gateway in the Transit FireNet or Transit Egress workflows.
Gateway Load Balancer (AWS only)
For AWS, if you enable Transit Egress Capability you can also enable the Gateway Load Balancer option, which creates a load balancer within the selected VPC. If this option is enabled here it will show as On and disabled if you add Transit FireNet to this gateway as part of the Transit FireNet workflow.
Subnet (GCP only)
For GCP, if you enable Transit Egress Capability you must also select a subnet.
BGP over LAN (Azure)
To enable BGP over LAN connections for this Transit Gateway, set this toggle to On.
For Azure, also enter the number of BGP over LAN interfaces you need (maximum is eight).
BGP over LAN (GCP)
To enable BGP over LAN connections for this Transit Gateway, set this toggle to On.
For GCP, select the subnet on which to apply the BGP over LAN connection.
For GCP, you cannot set BGP over LAN to On after the Transit Gateway is created.
In the Instances section, assign the subnets and IP addresses for the Transit Gateway instances.
Parameter Description Attach to Subnet
The subnet in which to create the gateway instance.
For best practice, select a different subnet in a different availability zone from the other Transit gateway instance.
Public IP
The public IP address of the gateway instance.
(AWS only) To allocate a new EIP, leave Public IP as Allocate New Static Public IP.
To create a highly available (HA) gateway instance, click + Instance and assign the subnet and IP address.
-
A Transit gateway supports up to 15 HA gateway instances.
-
The gateway instances are created in active-active mode.
In the Resource Tags section, you can add custom resource tags for the Transit Gateway.
-
Click + Resource Tag.
-
Enter a key to identify the resource and a value for the Key. The Key must be unique.
-
Click the checkmark icon to add the key:value pair to the resource tags.
-
Click the Tick button to save it.
-
-
Click Save.
You can monitor the progress of the gateway creation by going to CoPilot > Monitor > Notifications > Tasks tab. Click the expand arrow next to the gateway name to see the progress.
Creating a Spoke Gateway
To create a primary and Highly Available (HA) Spoke Gateway instances, provide the Spoke Gateway general details, then assign the subnet and IP addresses for the gateway instances.
-
In Aviatrix CoPilot, go to Cloud Fabric > Gateways > Spoke Gateways tab.
For quick access, at the top of the navigation panel, type Spoke Gateways in the search bar. -
To create a Spoke Gateway, click + Spoke Gateway and provide the following information.
Parameter
Description
Name
A name for the Spoke Gateway.
The name must begin with a letter, may include only letters, numbers, underscores, and dashes (excluding special characters or spaces), and must not exceed 50 characters in length.
Cloud
The Cloud Service Provider (CSP) where to create the Spoke Gateway.
For AWS and Azure, you can use the dropdown menu to select Standard or Global, China, or GovCloud.
Account
The cloud access account for creating the Spoke Gateway.
Region
The cloud region in which to create the Spoke Gateway.
VPC/VNet
The VPC or VNet in the selected region in which to create the Spoke Gateway.
Instance Size
The gateway instance size.
When selecting the gateway size, note that the size you select affects your IPsec performance.
High Performance Encryption
To enable High Performance Encryption (HPE) for the Spoke Gateway, set this toggle to On.
HPE enables 10Gbps and higher IPsec performance between two single Aviatrix Gateway instances or between a single Aviatrix Gateway instance and on-prem Aviatrix appliance.
You cannot turn High Performance Encryption On or Off after the Spoke Gateway is created.
Support for IPv6
To enable IPv6 addressing and routing for the Transit Gateway, set this toggle to On
Fill the Account, Region, and VPC/VNet fields before enabling IPv6 support.
Attach to Transit Gateway
Select the Transit Gateway to attach to the Spoke Gateway.
Attach to Egress Transit FireNet
Select the Egress Transit FireNet to attach to the Spoke Gateway.
This option is only available if an Egress Transit FireNet has been created. In the Advanced Settings section, set the advanced gateway settings that may apply.
Parameter
Description
BGP (all clouds)
To enable the Spoke Gateway to run BGP connection to external routers and dynamically exchange routes, set this toggle to On.
BGP over LAN (Azure)
To enable BGP connection over LAN:
-
Set this toggle to On.
You must set both BGP and BGP over LAN settings to On to enable BGP over LAN connection on the Spoke Gateway. -
Enter the number of LAN interfaces you need (maximum is eight) for the BGP connection.
You cannot delete an interface after the Transit Gateway is created.
Global VPC (GCP)
To connect the Spoke Gateway to a global VPC, set this toggle to On.
In the Instances section, assign the subnet and IP address for the Spoke Gateway instances.
Parameter Description Attach to Subnet
The subnet in which to create the Spoke gateway instance.
For best practice, select a different subnet in a different availability zone from the other Spoke gateway instances.
Public IP
The public IP address of the gateway instance.
(AWS only) To allocate a new EIP, leave Public IP as Allocate New Static Public IP.
To create a highly available (HA) gateway instance, click + Instance and designate the subnet and IP address of the gateway instance.
-
A Spoke Gateway can have up to 15 HA gateway instances.
-
All gateway instances are created in active-active mode.
-
A BGP-enabled Spoke Gateway can have only two HA gateway instances.
-
A Spoke Gateway with Site2Cloud or customized SNAT and DNAT enabled can have only two HA gateway instances.
In the Resource Tags section, you can add custom resource tags for the Transit Gateway.
-
Click + Resource Tag.
-
Enter a key to identify the resource and a value for the Key. The Key must be unique.
-
Click the checkmark icon to add the key:value pair to the resource tags.
-
Click Save.
-
-
Click Save.
You can monitor the progress of the gateway creation by going to CoPilot > Monitor > Notifications > Tasks tab. Click the expand arrow next to the gateway name to see the progress.
Creating a Spoke to Transit Attachment
To attach a Spoke Gateway to a Transit Gateway:
-
In Aviatrix CoPilot, go to Cloud Fabric > Gateways > Spoke Gateways.
-
In the table, locate the Spoke Gateway you want to attach and click the Manage Gateway Attachment icon on the right side of its row.
-
In the Manage Gateway Attachment dialog, click the Transit Gateway tab and then click + Attachment and provide the following information.
Parameter
Description
Transit Gateway
The Transit Gateway to attach to the Spoke Gateway.
In the Advanced section, set the advanced settings that may apply.
Parameter
Description
Customize Route Table Attachment
Enables custom route tables when set to On.
From the Select Route Tables dropdown menu, select the custom route table(s) to attach to this Spoke Gateway.
Max Performance
Creates the maximum number of High Performance Encryption (HPE) tunnels for the Transit-to-Spoke attachment when set to On. The number of tunnels that are created depends on the gateway instance sizes.
-
Max Performance option is valid only when both the Spoke and Transit Gateways are launched with HPE enabled and are in the same cloud type.
-
When the Spoke and Transit Gateways are launched in different cloud types, only one tunnel is created (even when HPE is enabled for both the Spoke and Transit Gateway).
If Max Performance is Off, only one tunnel is created (even when HPE is enabled for both the Spoke and Transit Gateway).
To switch between multiple tunnels or one tunnel, detach and reattach the Spoke Gateway to the Transit Gateway.
-
-
To attach this Spoke Gateway to another Transit Gateway, click + Attachment again and provide the attachment details.
-
Click Save.
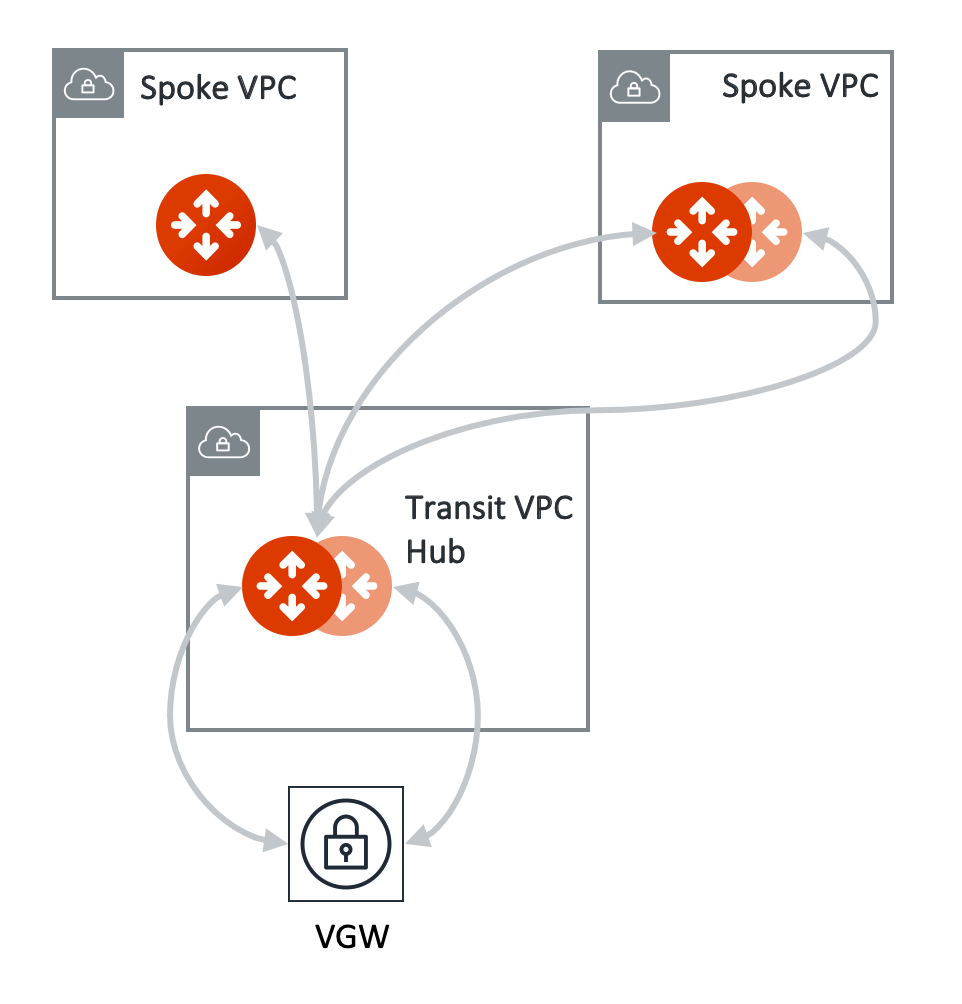
View the Network Topology
You can view the network topology in CoPilot by going to Cloud Fabric > Topology page. For more information about using the topology map, see Gaining Visibility into Your Network Topology.
View the Gateway’s Connections and Route Tables
You can view the Spoke and Transit Gateway connections and route table information.
In CoPilot:
-
Go to Cloud Fabric > Gateways, and select the Spoke or Transit Gateway to open the gateway’s page.
-
To view the gateway’s connections, click the Attachments tab.
-
To view the gateway’s route tables, click the VPC/VNet Route Tables tab, then from the Route Table dropdown menu, select a route table to view the routes.
Transit Network APIs
You can automate multicloud Transit Network configuration by using Terraform. To learn more about Terraform, please see the Terraform Registry.
If you are building a single-region multicloud Transit Network (by following this Multicloud Transit Network Workflow), you can follow this Terraform example.
Related Topics
-
You can peer Transit Gateways to expand your Aviatrix Transit Network across multiple regions and clouds. See Multi-Region Multicloud Transit Gateway Peering Workflow.
-
You can segment your Aviatrix Transit Network to create network isolation and enhance security. To learn more, see Network Segmentation.
-
You can connect the Transit Gateway to external devices such as on-premises firewalls and routers to connect to your datacenter. See Connecting the Transit Network to On-Premises.
-
You can connect the Transit Gateway to an Edge Gateway to extend your Aviatrix Transit Network to the network edge. see Hybrid Cloud Connectivity.