General Guidelines for Migrating from Legacy ThreatIQ and Geoblocking to Distributed Cloud Firewall
If you configured ThreatIQ and/or Geoblocking prior to Controller version 7.2.4820, you can upgrade to Distributed Cloud Firewall (DCF) and its ExternalGroup functionality. DCF-powered Threat and Geo functionality provides more granular configuration and can be pushed to any DCF-supported gateways.
| You cannot use ThreatIQ and/or Geoblocking in conjunction with DCF and ExternalGroups. |
| These are generalized guidelines only. Reach out to Aviatrix Support for assistance with this migration. |
Upgrading ThreatIQ to ThreatGroups (Threat Feeds under ExternalGroups)
ThreatIQ is located at Security > ThreatIQ.
| Currently there is no Custom ThreatGroup creation. |
-
Any VPC/VNets that are not currently protected on the Threat IQ > Configure Exclusion List for VPCs page should have a SmartGroup configured that excludes those VPC/VNets from threat analysis.
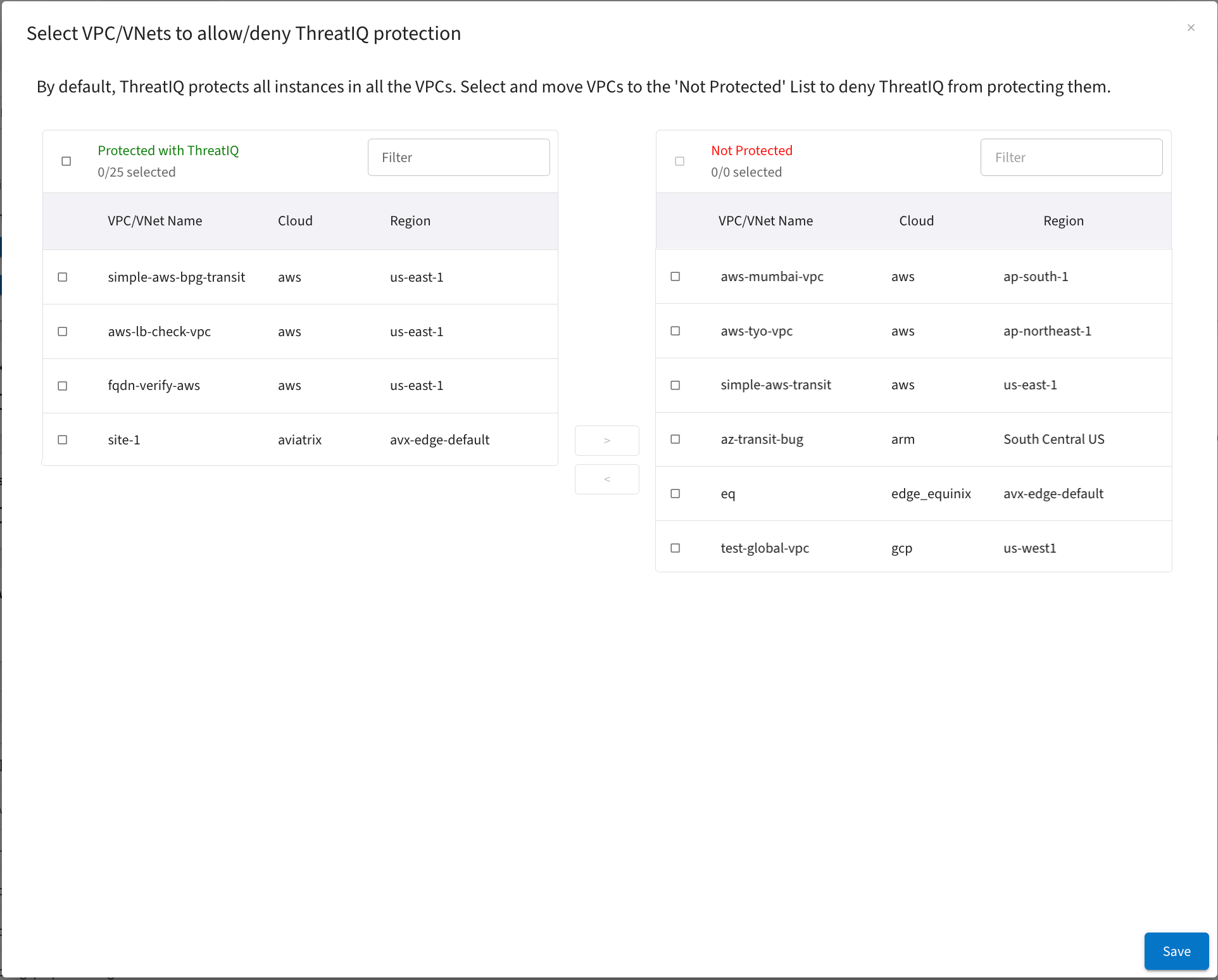
-
For any custom threats you have configured on the ThreatIQ > Custom Threat list, you should create a SmartGroup named Custom Threat List that contains all the threat IPs from the list.
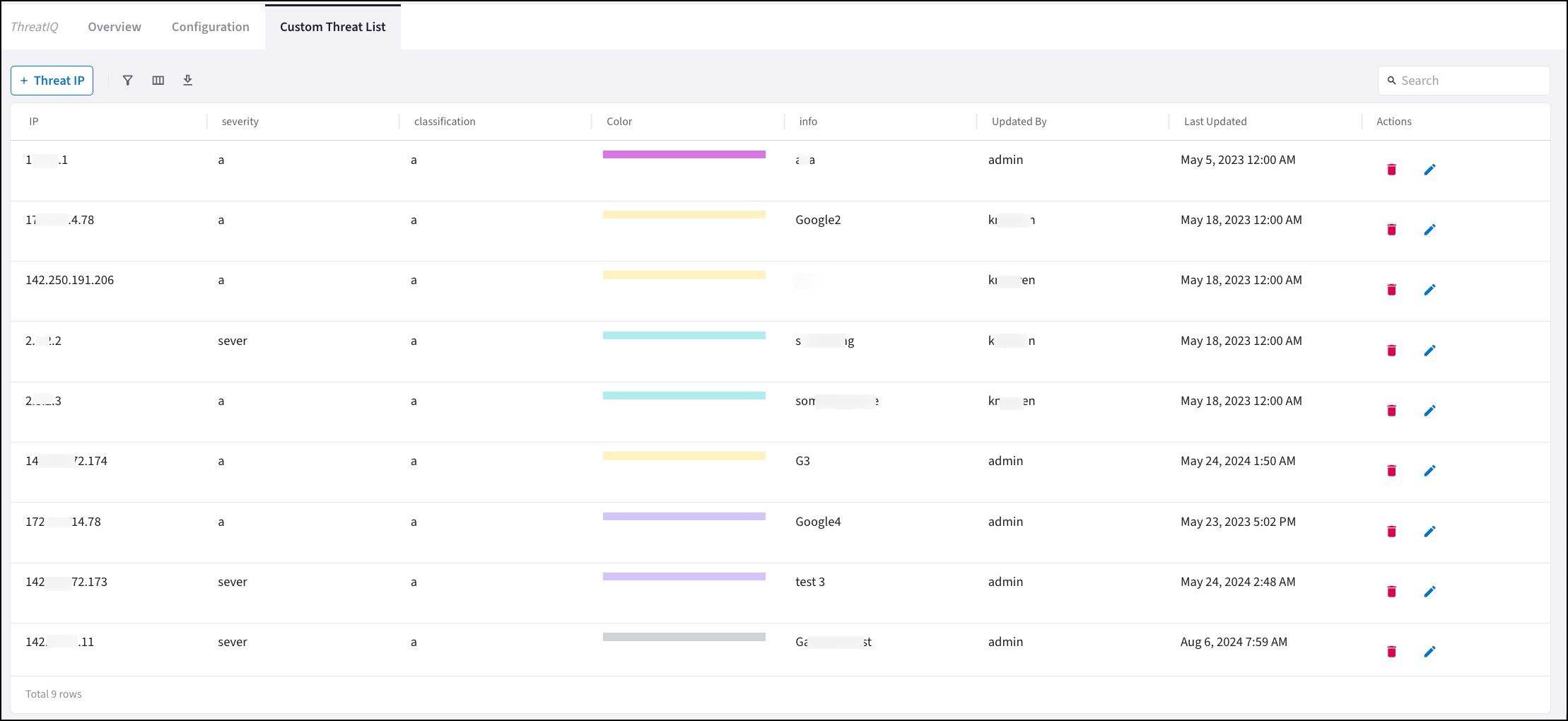
-
Check if ThreatIQ > Advanced Settings is set to Append or Prepend. This determines where new ThreatIQ firewall rules were added. When you create your threat-based DCF rules, Aviatrix recommends that these be at the top of the set of rules.
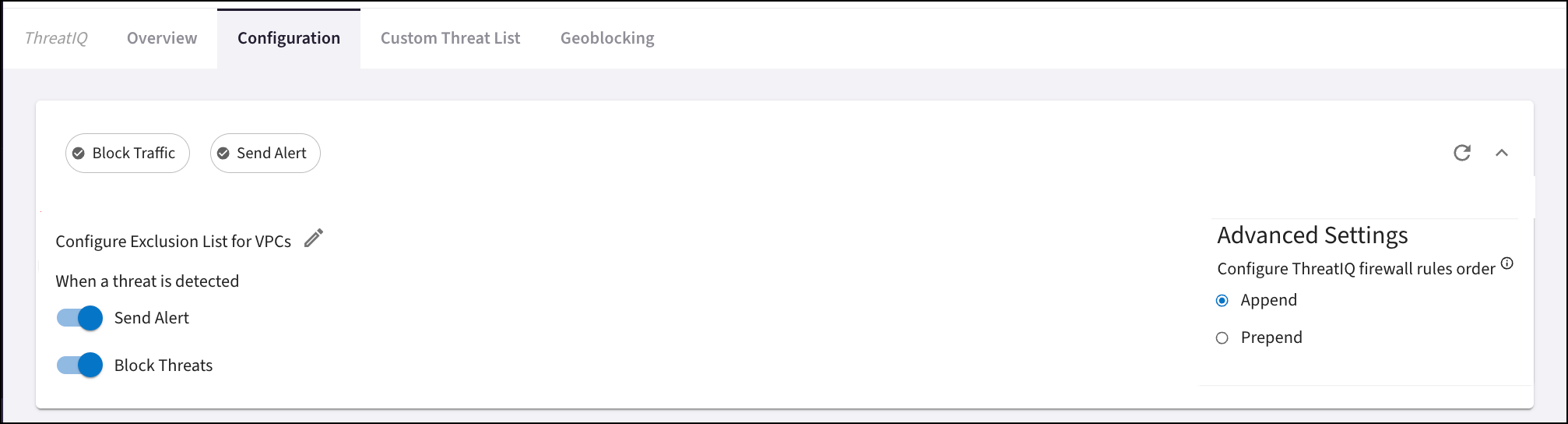
Upgrading Geoblocking to ExternalGroups (Countries)
| The Geoblocking tab is only visible if configured prior to Controller version 7.2.4820. |
| Prior to Controller version 7.2.4820, Geoblocking was global, meaning that if the status of a country was set to Blocked, all IPs from that country were blocked. With ExternalGroups > Countries, you have the choice to block specific IPs to and from a country. |
-
Click on every country you have blocked on the Security > ThreatIQ > Geoblocking tab and then click the download
 icon to capture the list of blocked IPs for each country.
icon to capture the list of blocked IPs for each country.
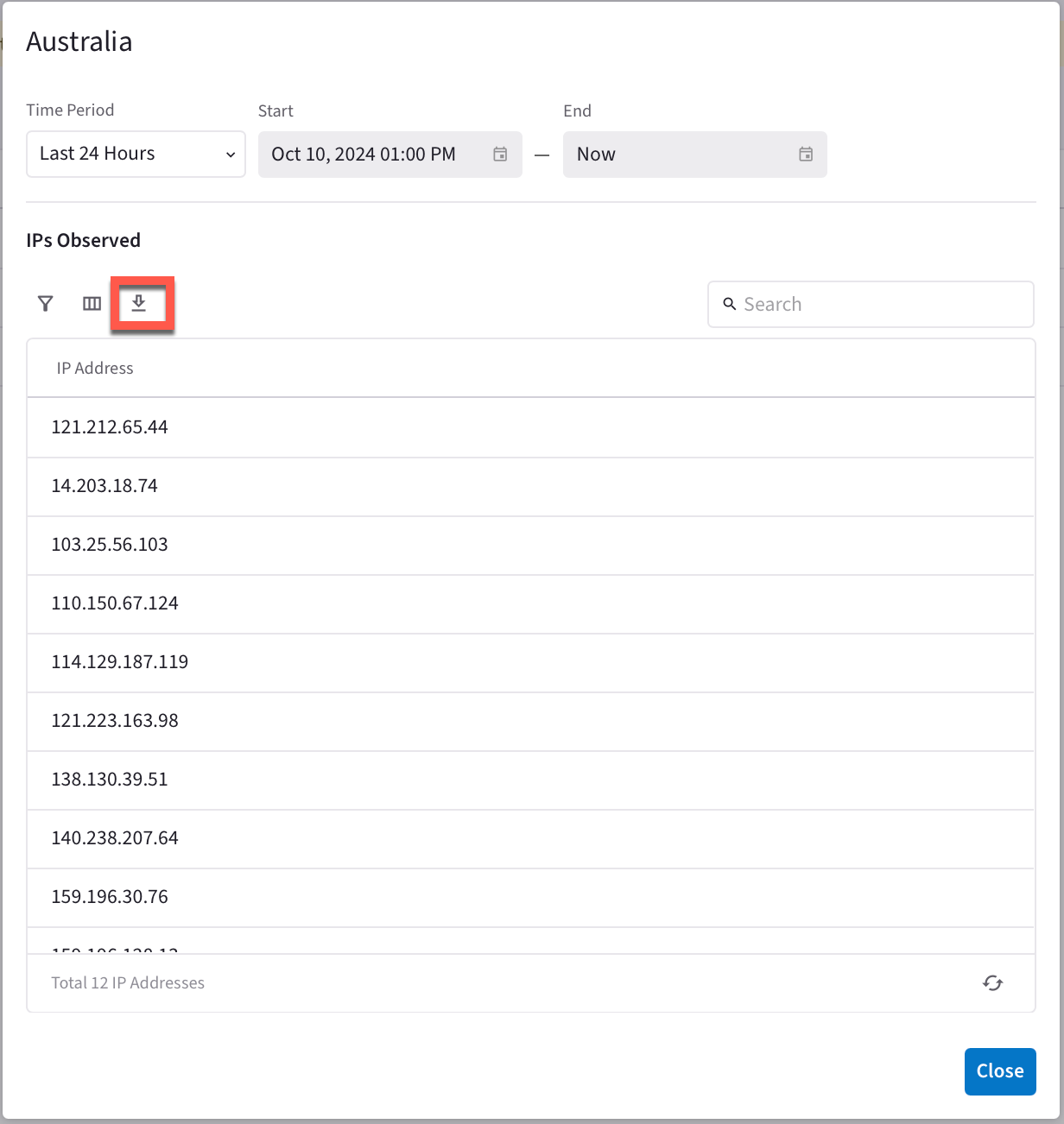
-
Create your country-based ExternalGroups, based on the information in your downloaded Country IP lists.
Creating DCF Rules
Create DCF rules that encompass the threat and Country information above.
|
If ThreatIQ did not have any exception VPCs, ignore Rules 1 and 2. If you configured the Custom Threat List in ThreatIQ, add the Custom Threat List SmartGroup created above to Rule 3 as a Source, and to Rule 4 as a Destination. |
If ThreatIQ had exception VPCs create the following DCF rules:
-
Rule 1: Threat Exception Inbound Rule where:
-
the Source Group is the ThreatGroups database and the Destination Group is the ThreatIQ Exclusion VPC list.
-
Action is Permit.
-
-
Rule 2: Threat Exception Outbound Rule where:
-
Source Group is the Threat Exclusion VPCs SmartGroup and the Destination is the ThreatGroups database.
-
Action is Permit.
-
-
Rule 3: Inbound Threat Protection Rule where:
-
the Source Group is the Default ThreatGroup (under ExternalGroups > Threat Feeds) and the Destination Group is Anywhere.
-
Action is Deny.
-
-
Rule 4: Outbound Threat Protection Rule where:
-
Source Group is Anywhere and the Destination is the Default ThreatGroup (under ExternalGroups > Threat Feeds).
-
Action is Deny.
-
Create these geo-based (Countries under ExternalGroups) DCF rules:
-
Rule 5: Inbound Geo Block Rule where:
-
Source Group is Any; Destination is the list of (blocked) countries.
-
Action is Deny.
-
-
Rule 6: Outbound Geo Block Rule where:
-
Source Group is List of Countries; Destination is Any.
-
Action is Deny.
-
Final Steps
Contact Aviatrix Support for final steps (including disabling ThreatIQ and Geoblocking) and testing the configuration.