Aviatrix Gateway to FortiGate
This document describes how to configure an IPsec tunnel between an Aviatrix Gateway and a FortiGate firewall using Aviatrix Site2Cloud. This task is divided into two parts:
-
Configure a Site2Cloud tunnel in Aviatrix CoPilot.
-
Configure a VPN tunnel and related components in the FortiGate Firewall.
Setting up External (S2C) Connection
-
In Aviatrix CoPilot, launch an Aviatrix Transit Gateway.
-
Navigate to Networking > Connectivity > External Connections (S2C) and click Add New to create a Site2Cloud connection using the values for one of the below options (for either you can select either PSK or certificate-based authentication).
-
After the connection is created, select the vertical ellipsis
 menu for that connection and select Download Configuration.
menu for that connection and select Download Configuration. -
Select Generic from the Vendor dropdown list and click the Download to download the external (S2C) configuration. Use this configuration file to configure the tunnels and interfaces in your Fortinet FortiGate firewall.
FortiGate Configuration
The configuration and screenshots below make the following three assumptions:
-
There are two interfaces on the FortiGate:
-
Interface port1 is an externally facing interface.
-
Interface port2 is an internally facing interface.
-
-
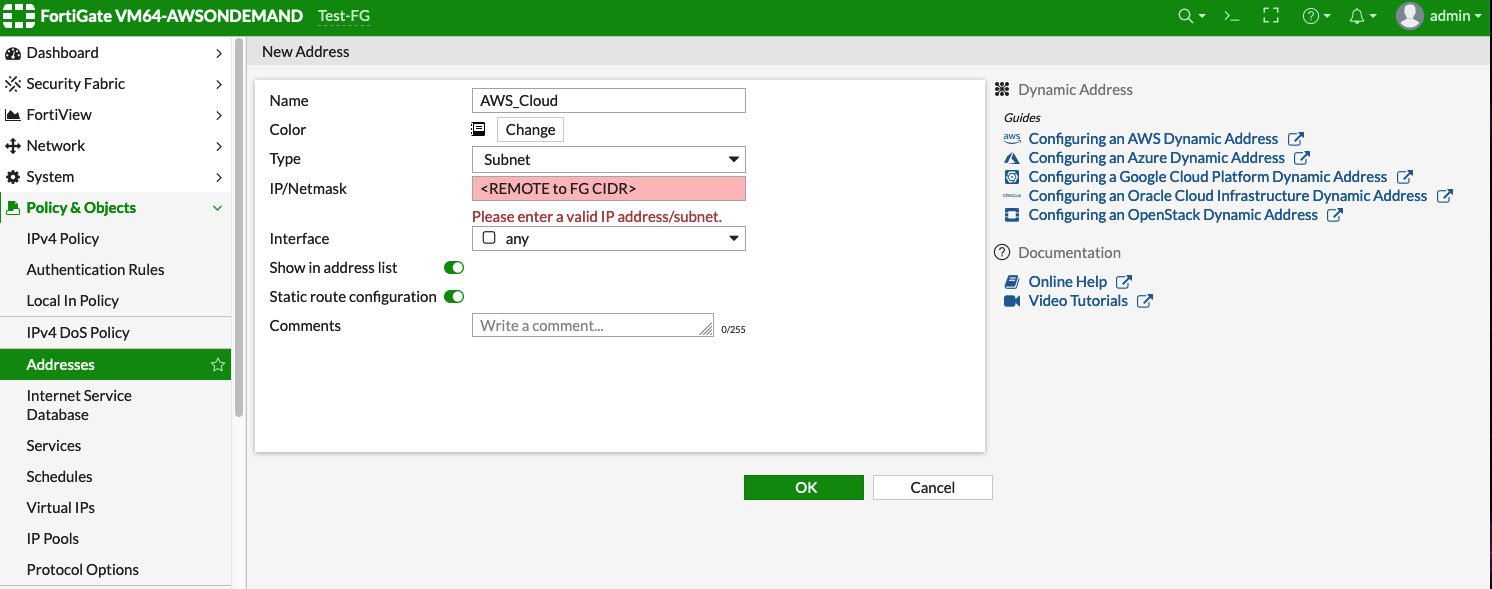
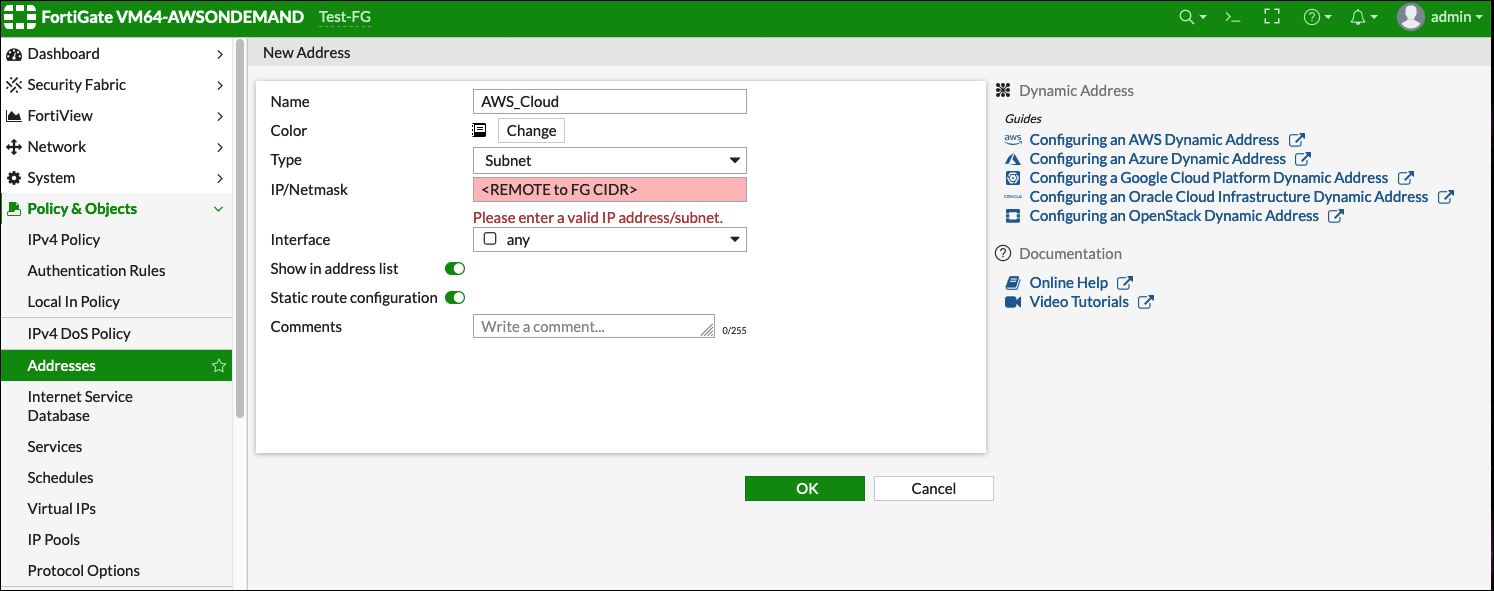
You have a subnet in AWS, Azure, or GCP in a VPC/VNet that has an Aviatrix Gateway. This subnet is defined as "10.0.0.0/16" for the examples below but it can be any valid CIDR range.
In the examples below this range is referred to as AWS_Cloud.
-
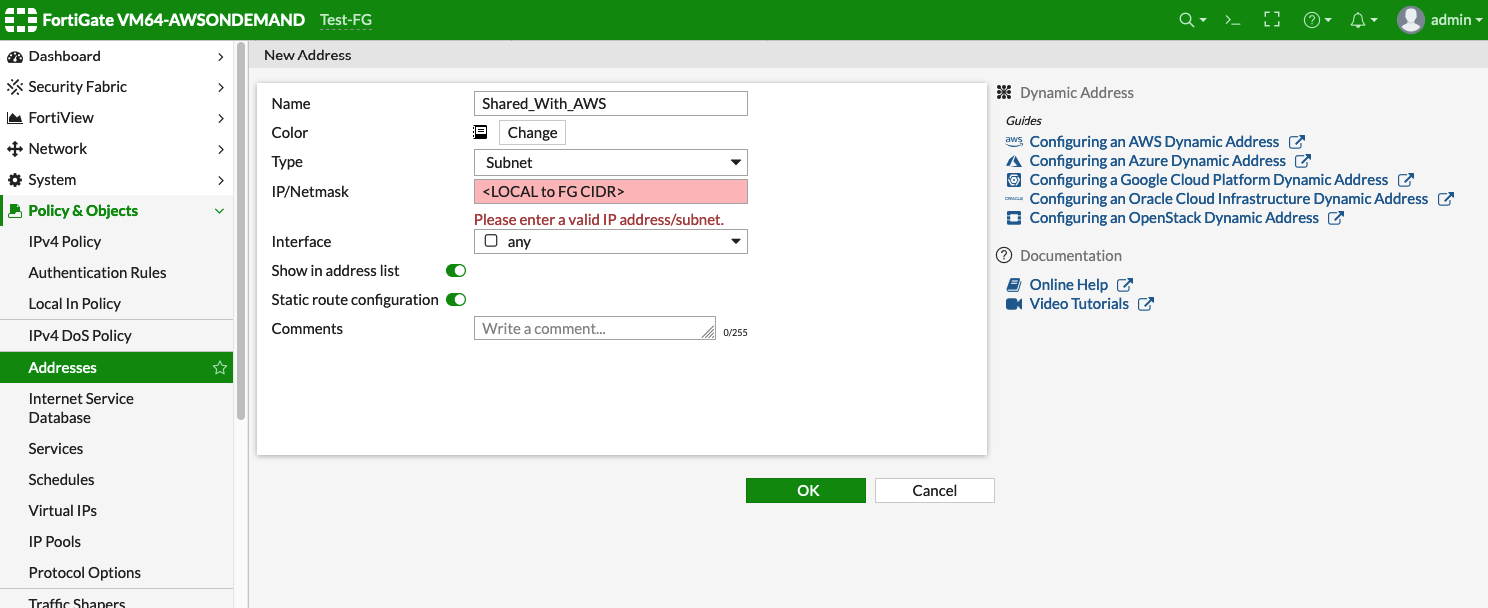
You have a subnet behind your FortiGate firewall that will be accessible in the cloud. This subnet is defined as "172.16.0.0/20" in the examples below but it can be any valid CIDR range.
In the examples below, this range is referred to as Shared_With_AWS.
Configuring Named Address Ranges in FortiGate
Access the FortiGate Dashboard. Under Policy & Objects > Addresses, create two new addresses: AWS_Cloud and Shared_With_AWS.
Creating an IPsec Tunnel on FortiGate
-
Log in to the FortiGate and access the Dashboard.
-
In the VPN menu, select IPsec Wizard.
-
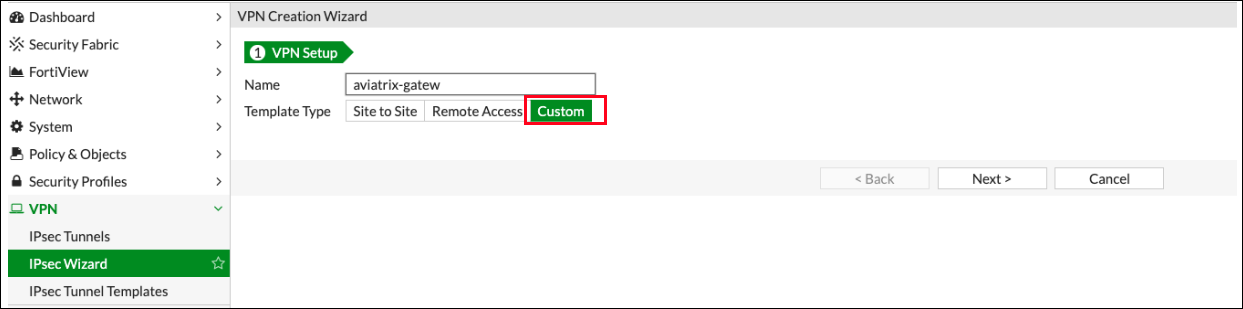
Change the Template Type to "Custom."
-
Enter any value as the Name. For this example, we are using "aviatrix-gatew."
-
Click Next >.
-
Fill out the Network fields as recommended below:
Field |
Expected Value |
Name |
aviatrix-gatew (for example) |
Template Type |
Custom |
New VPN Tunnel Tab
Complete the Network fields on the New VPN Tunnel tab as follows:
Network section of New VPN Tunnel Tab
| Field | Expected Value |
|---|---|
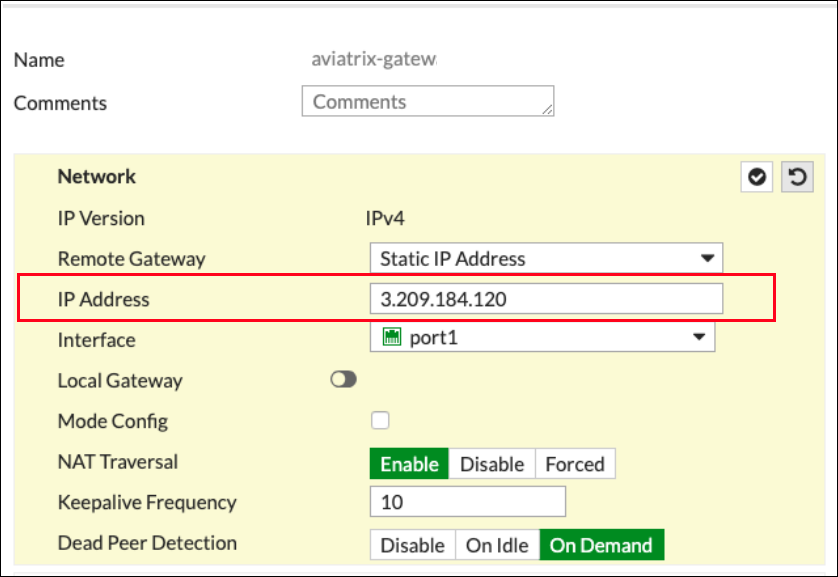
IP Version |
IPv4 |
Remote Gateway |
Static IP Address |
IP Address |
Public IP address of Aviatrix Gateway |
Interface |
Select the Appropriate Port/Interface |
Local Gateway |
Disabled |
Mode Config |
Unmark this checkbox |
NAT Traversal |
Enable |
Keepalive Frequency |
Any value |
Dead Peer Detection |
On Demand |
Forward Error Correction |
Unmark this checkbox |
Advanced Options |
Disabled |
Authentication section of New VPN Tunnel Tab
| Field | Expected Value |
|---|---|
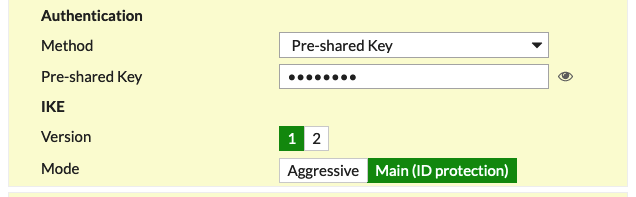
Method |
Pre-shared Key |
Pre-shared Key |
Enter the value from the downloaded configuration or the value typed in to the field in Aviatrix Site2Cloud |
IKE Version |
1 |
IKE Mode |
Main (ID protection) |
Phase 1 Proposal section of New VPN Tunnel Tab
| Field | Expected Value |
|---|---|
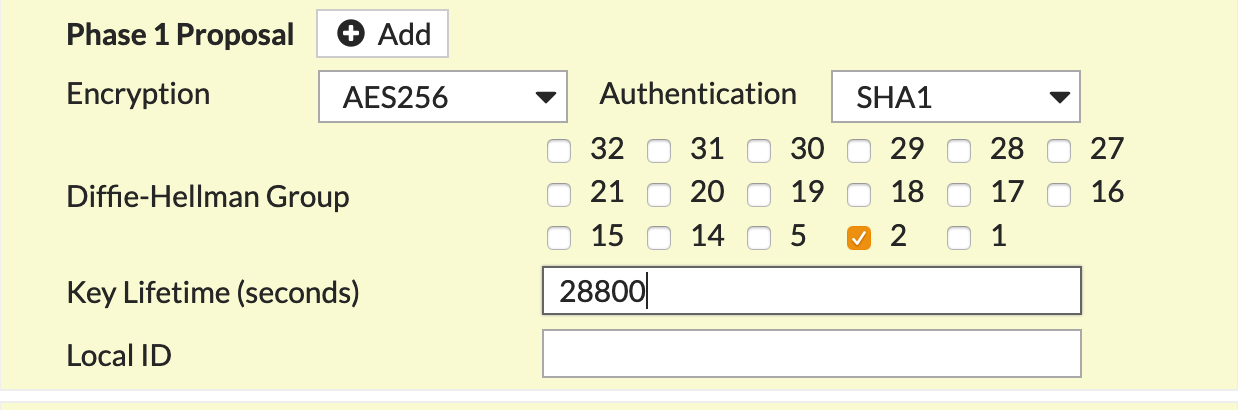
Encryption |
Match value specified in Aviatrix S2C configuration (Phase 1 Encryption) |
Authentication |
Match value specified in Aviatrix S2C configuration (Phase 1 Authentication) |
Diffie-Hellman Group |
Match value specified in Aviatrix S2C configuration (Phase 1 DH Groups) |
Key Lifetime (seconds) |
28800 |
Local ID |
Leave Blank |
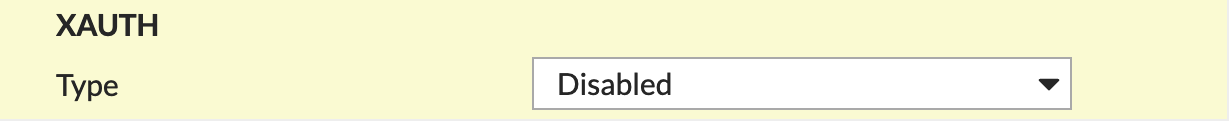
XAUTH section of New VPN Tunnel Tab
| Field | Expected Value |
|---|---|
Type |
Disabled |
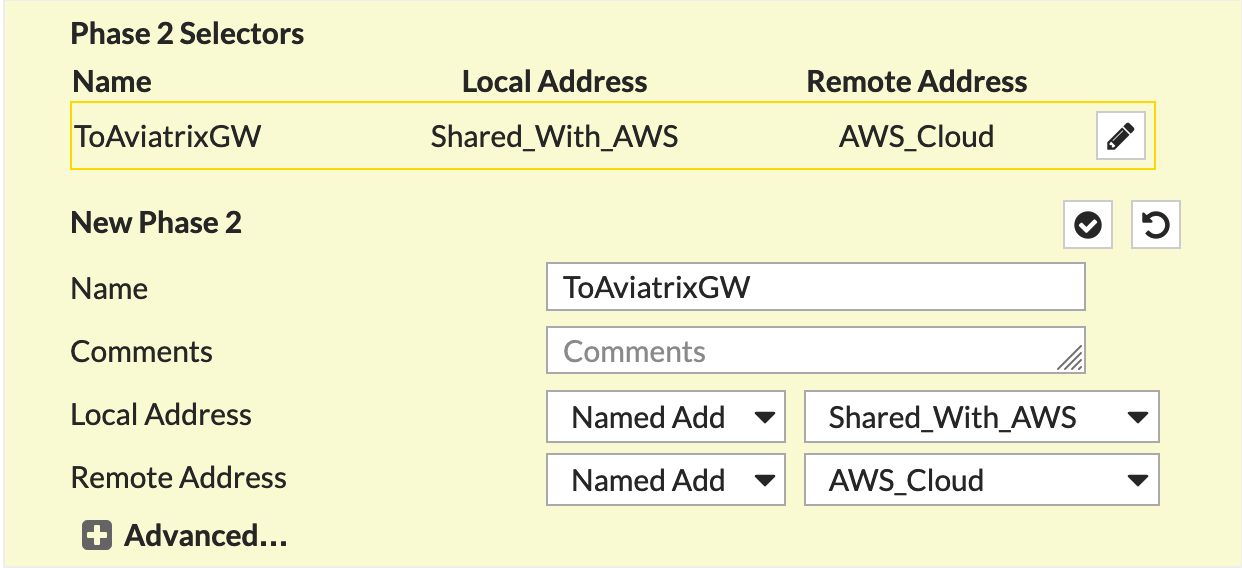
Phase 2 Selectors > New Phase 2 seciton of New VPN Tunnel Tab
| Field | Expected Value |
|---|---|
Name |
Any String Value |
Comments |
Any String Value |
Local Address |
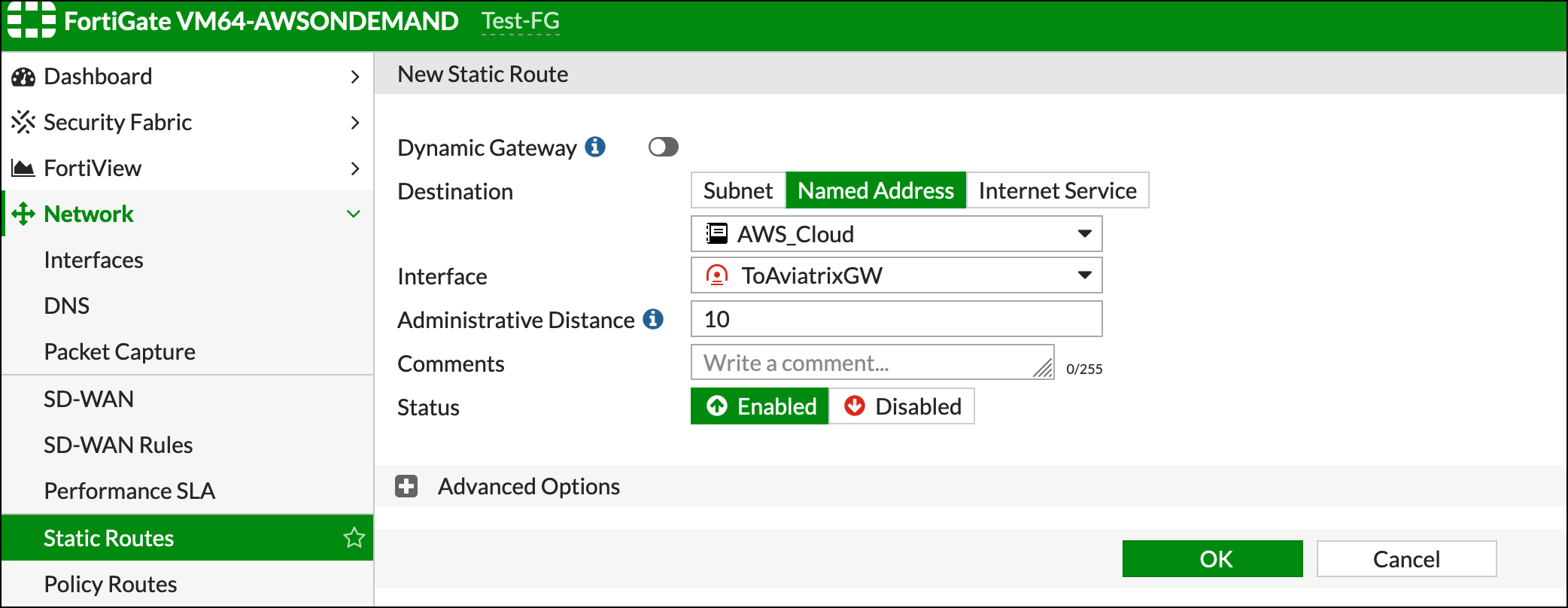
Named Address - Shared_With_AWS |
Remote Address |
Named Address - AWS_Cloud |
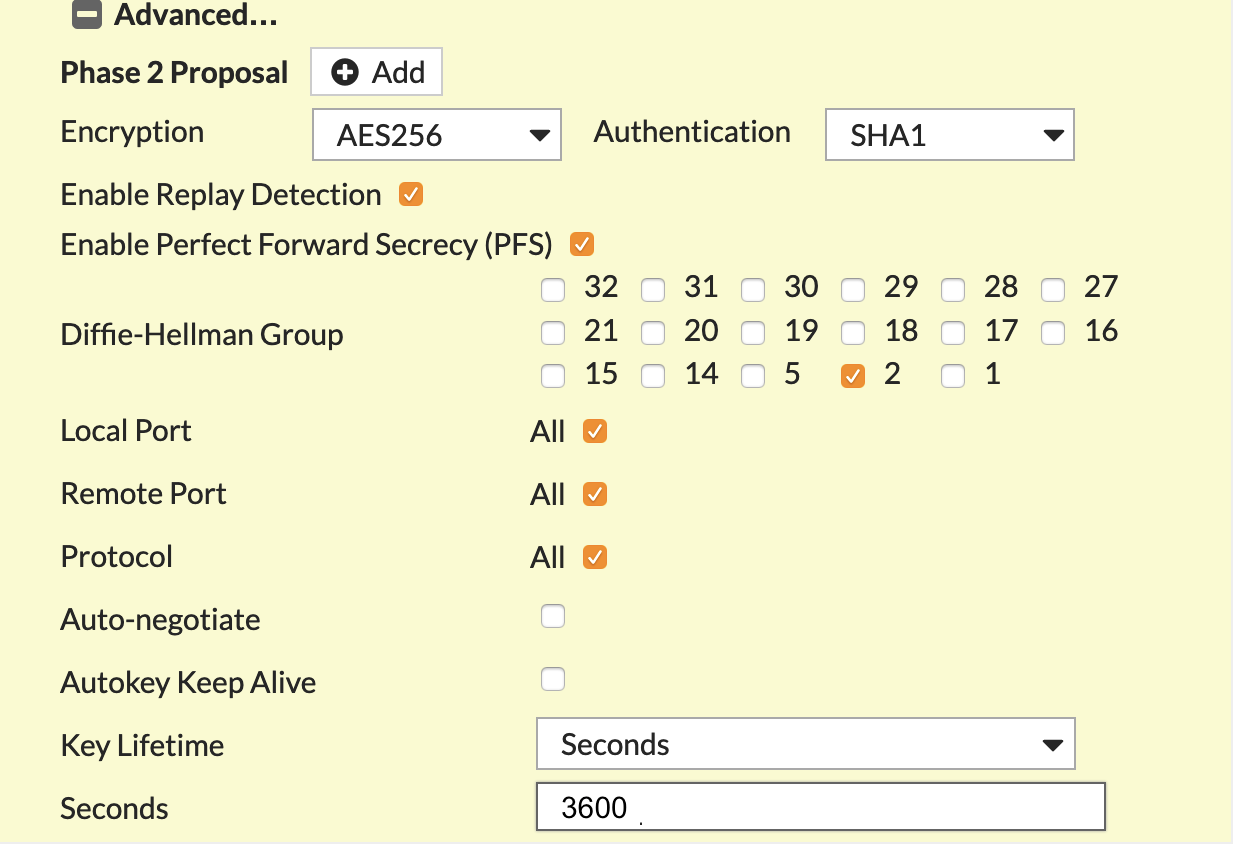
Advanced section of New VPN Tunnel Tab
|
Obtain the values from the downloaded configuration file. |
| Field | Expected Value |
|---|---|
Encryption |
Match value specified in Aviatrix S2C configuration (Phase 2 Encryption) |
Authentication |
Match value specified in Aviatrix S2C configuration (Phase 2 Authentication) |
Diffie-Hellman Group |
Match value specified in Aviatrix S2C configuration (Phase 2 DH Groups) |
Key Lifetime (seconds) |
3600 |
-
Click OK.
-
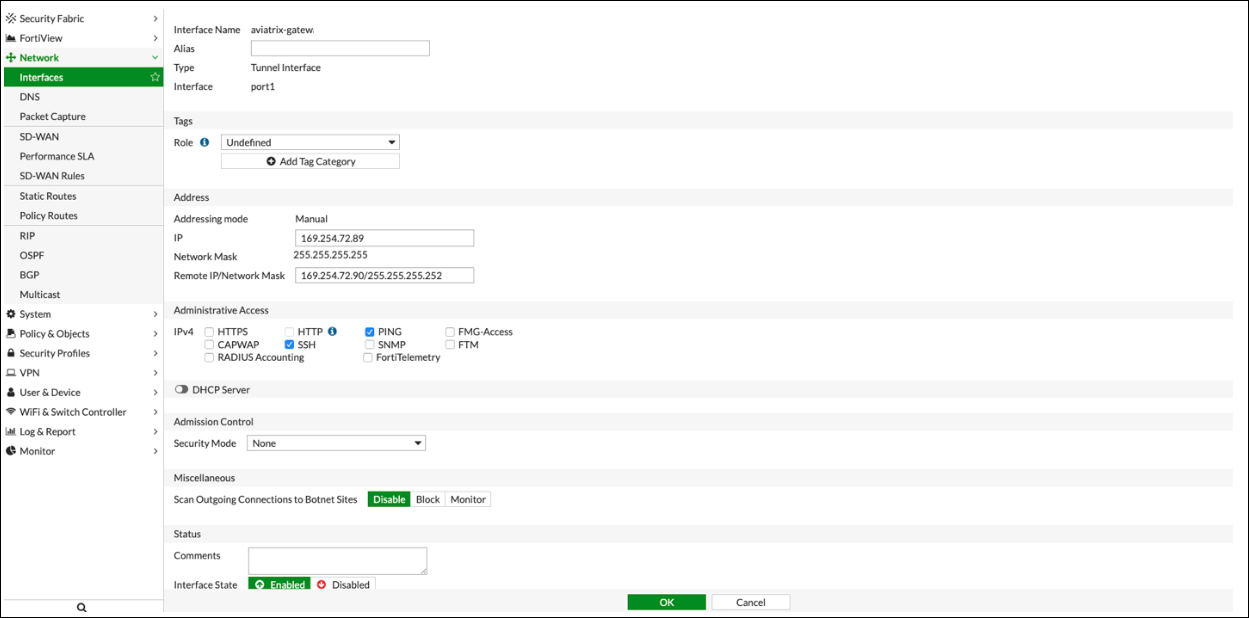
Navigate to Network > Interfaces.
-
Click on the Tunnel created above (e.g. aviatrix-gatew) and assign the IP address from the downloaded configuration file.
Configure IPv4 Policy
-
Go to Policy & Objects > IPv4 DoS Policy.
-
Create two new IPv4 policies:
-
Outbound traffic from FortiGate (Shared_With_AWS) to Aviatrix (AWS_Cloud)
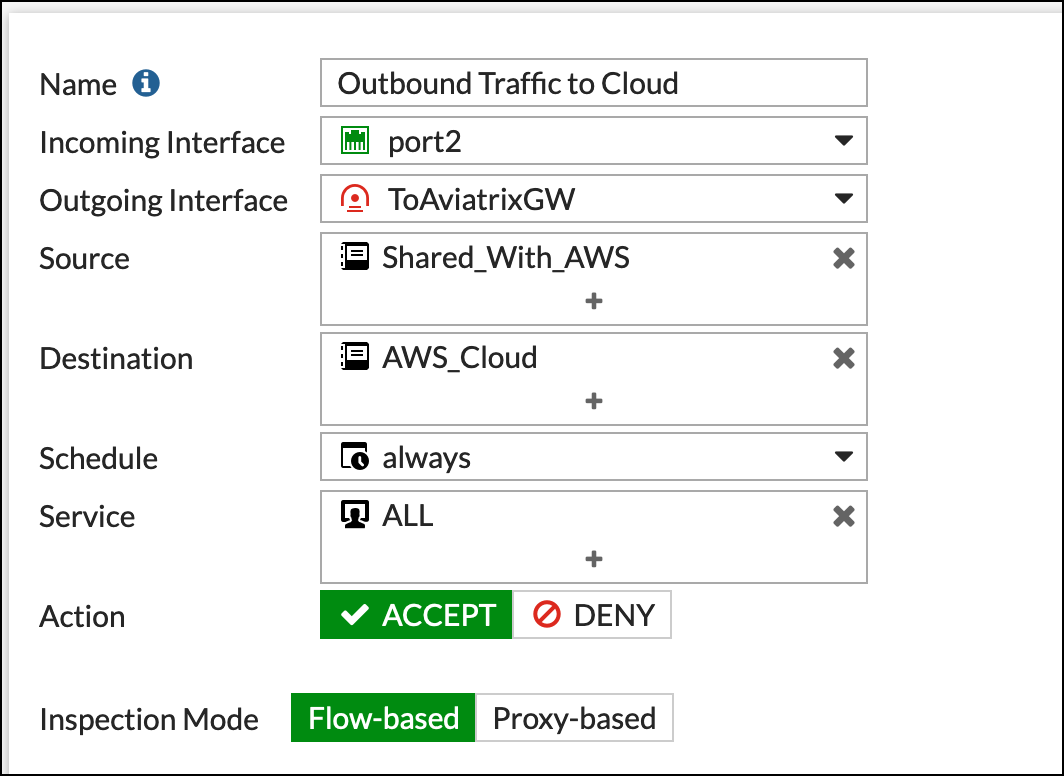
-
Inbound traffic from Aviatrix (AWS_Cloud) to FortiGate (Shared_With_AWS)
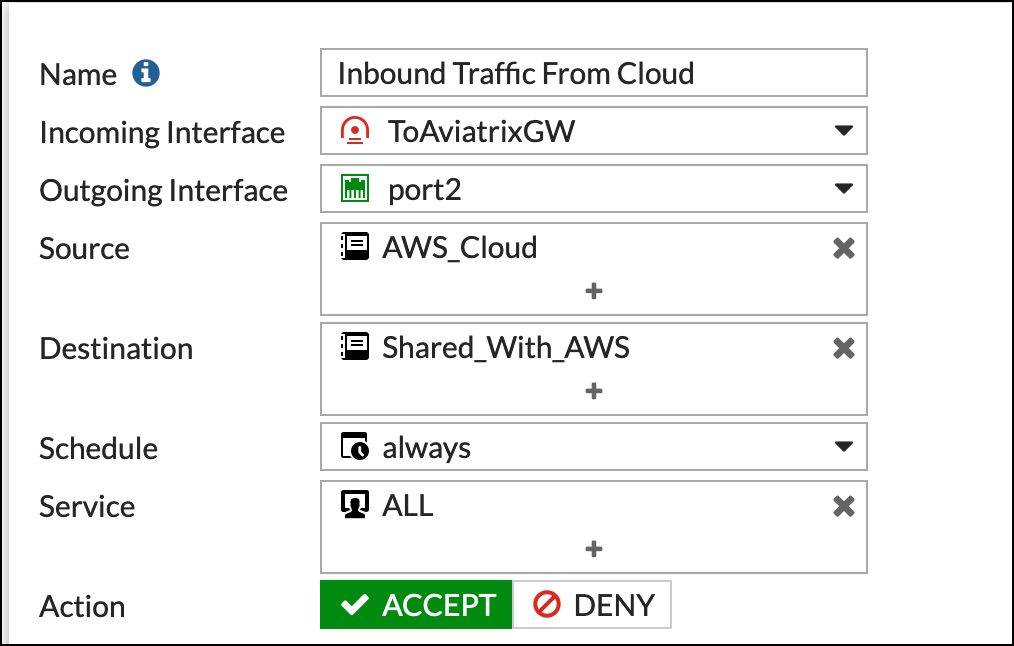
-
|
The reference to port2 in the screenshots should be replaced with your own interface name that represents the internal facing interface. |
|
Be sure to select ACCEPT for "action" and select ALL for "service." |
Troubleshoot
Error Message
failed to get valid proposal
no suitable proposal found
Solution
Check that the Phase 1 authentication, encryption, and Diffie-Hellman groups match on both sides.
If you are experiencing low IPsec throughput, you may want to configure two commands on the Fortigate.
config system global set ipsec-asic-offload disable end
configure system global set ipsec-hmac-offload disable end