Transit Gateway Multi-Peer BGP over LAN with Azure Route Server Workflow
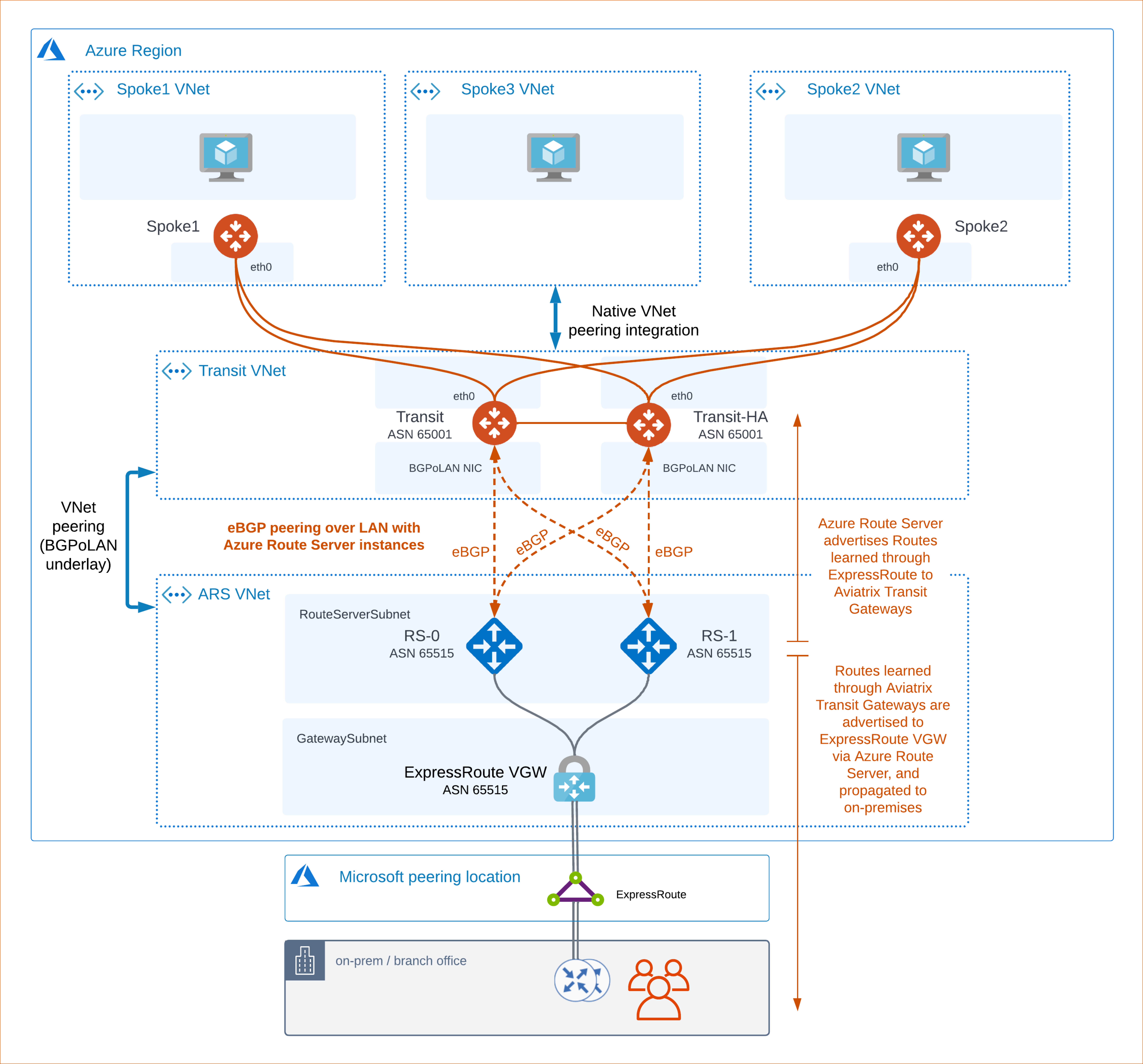
The Aviatrix Platform allows Azure Route Server (ARS) integration for on-premises connectivity using Azure ExpressRoute with no overlay. Azure Route Server is a managed service with high availability. It provides a mechanism for exchanging routes between Azure Software Defined Networking (SDN) and Network Virtual Appliances (NVAs) dynamically through Border Gateway Protocol (BGP). You can achieve full-mesh high availability by running two BGP peering endpoints.
Aviatrix integrates with Azure Route Server by treating the Azure Route Server as a BGP over LAN peer and exchanging routes using BGP. This enables Azure cloud networks to connect to on-premise or branch locations and provides connectivity across hybrid environments. Customers who use high-speed Azure ExpressRoute connectivity with no encryption for hybrid environments can exchange routes between the Aviatrix Transit Gateways and the on-premise network connected via ExpressRoute. This solution provides you with an enterprise-grade transit network.
The diagram below shows Azure Route Server integration with Aviatrix Transit Gateways. Full mesh is enabled so that both Transit Gateways peer with the two Azure Route Server IP endpoints in the Azure Route Server.
This document provides instructions on how to build an Aviatrix Transit Gateway to External Device (Azure Route Server) using BGP over LAN in Azure.
Prerequisites
Ensure the following prerequisites are met:
-
The Aviatrix Controller is updated to software version 6.8 or above.
-
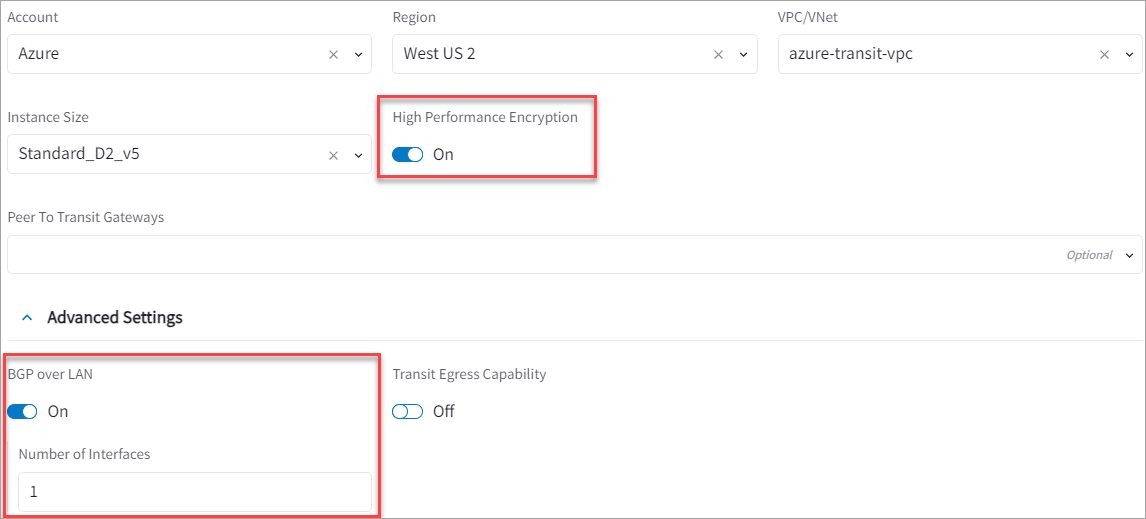
Aviatrix Transit Gateways are deployed with High Performance Encryption (HPE) and with BGP over LAN enabled. You only need to configure one BGP over LAN interface to peer with both Azure Route Server instances.
-
A BGP ASN is assigned to the Transit Gateways (configure by going to CoPilot > Cloud Fabric > Gateways > Transit Gateways tab, select the Transit Gateway and go to Settings > Border Gateway Protocol (BGP) > Local AS Number).
-
Complete the following tasks in Azure:
-
Create a VNet to deploy the Azure Route Server.
-
Deploy the Azure Route Server in this VNet by referring to the applicable Azure documentation.
-
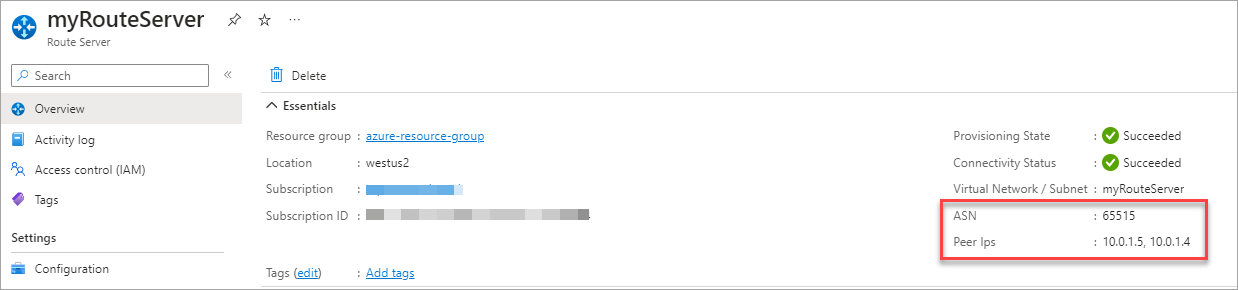
Go to your Route Server > Overview and record the ASN and the private IP addresses of the Azure Route Server endpoints you created. You will use these later in the Aviatrix CoPilot configuration.
-
Configure the VNet Peering Between Transit and Azure Route Server VNets
You need to configure the VNet peering between the VNet that is hosting the Azure Route Server and the Aviatrix Transit VNet. Follow these steps to configure the peering parameters from the Azure Route Server VNet to the Aviatrix Transit VNet.
| If you are using Terraform, make sure to explicitly set the argument “allow_forwarded_traffic” to “True” for both VNet peerings. |
-
Launch the Azure Portal.
-
Go to Virtual networks and select your Route Server VNet.
-
Under Settings, click Peerings.
-
On the Peerings page, click Add.
-
On the Add peering page, select the following options:
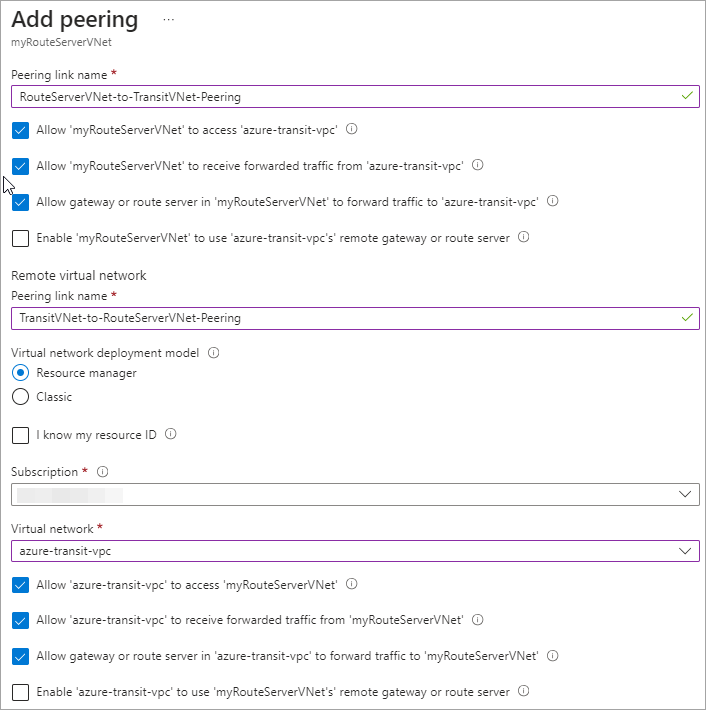
-
-
Click Add.
Configure the BGP peering Between Azure Route Server and Transit Gateways
-
In Aviatrix CoPilot, go to Cloud Fabric > Gateways, select your primary Transit Gateway and click Gateway Diagnostics. Then, click Interface Stats and record the IP address assigned to the BGP over LAN interface. Repeat this step for the HA Transit Gateway.
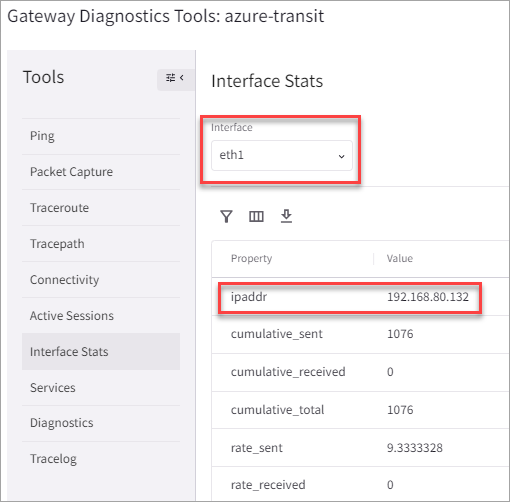
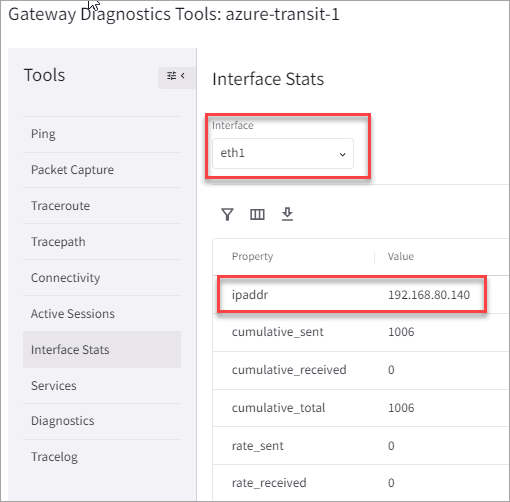
-
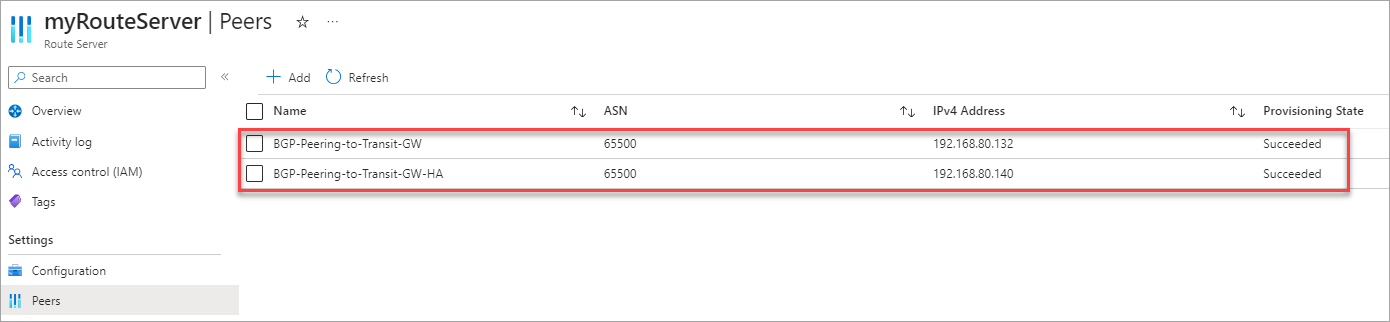
In your Azure portal, go to Route Servers > select your Azure Route Server > Peers, and click Add.
-
Configure the Azure Route Server peering to both remote Aviatrix Transit Gateways in the Transit VNet by specifying the ASN you configured for your Aviatrix Transit Gateways and the IP address of the BGP over LAN network interface on each Transit Gateway. Refer to the Prerequisites section to find the ASN number.
-
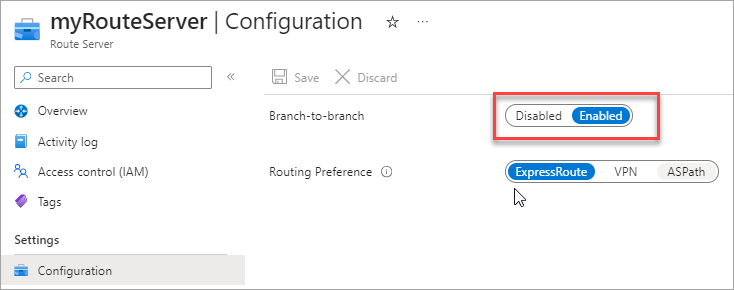
Go to Route Servers > select your Azure Route Server > Configuration.
-
Next to Branch-to-branch, select Enabled.
This option allows the Azure Virtual Network Gateways to propagate the routes the Azure Route Server has learned from the Aviatrix Transit Gateways. It is disabled by default.
Configure the BGP over LAN External Connection to Azure Route Server
In Aviatrix CoPilot:
-
Go to Networking > Connectivity > External Connections (S2C) tab.
-
Click + External Connection.
-
Provide the following information.
Parameter
Description
Name
A name for this connection.
Connect Local Gateway To
-
Select the External Device radio button.
-
Click on the dropdown menu and select BGP over LAN.
Local Gateway
Transit Gateway to connect to Azure Route Server.
Local ASN
Transit gateway’s Local AS Number.
Remote ASN
65515
Azure Route Server always resides in ASN 65515 and cannot be changed. Remote vnet:rg:sub
Route Server VNet.
BGP ActiveMesh
Set this toggle to On.
When you select BGP Activemesh, Aviatrix Controller creates two peers from each Transit Gateway to both instances of Azure Route Server. This is required for the correct operation of Azure Route Server.
Learned CIDR Approval
This is Off and disabled by default unless the Local Gateway you select has Learned CIDR Approval turned On; the Connection option selected, and the BGP connection selected. Then it is On by default (not editable).
When this setting is On, an approval process is set up for gateway learned CIDRs for this BGP external connection. This approval process improves security for your network. If an unapproved CIDR address attempts to access the connection, CoPilot sends an approval email to the CoPilot admin so that the admin can approve or block access.
Remote LAN IP
Azure Route Server instance 0 IP Address.
Refer to the Prerequisites section to find Azure Route Server IP addresses. Local LAN IP
Primary Transit Gateway BGP over LAN IP Address.
-
-
Click + Connection to add a new connection.
Parameter Description Remote LAN IP
Azure Route Server instance 1 IP Address.
Local LAN IP
HA Transit Gateway LAN IP Address.
-
Click Save.
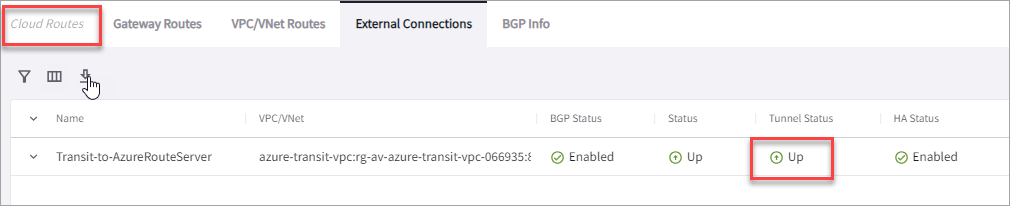
Verifying the LAN Connection Status
You can check the tunnel status by going to Diagnostics > Cloud Routes > External Connections. Confirm that Tunnel Status is Up and that HA Status (Activemesh for the Route Servers) and BGP Status is enabled.
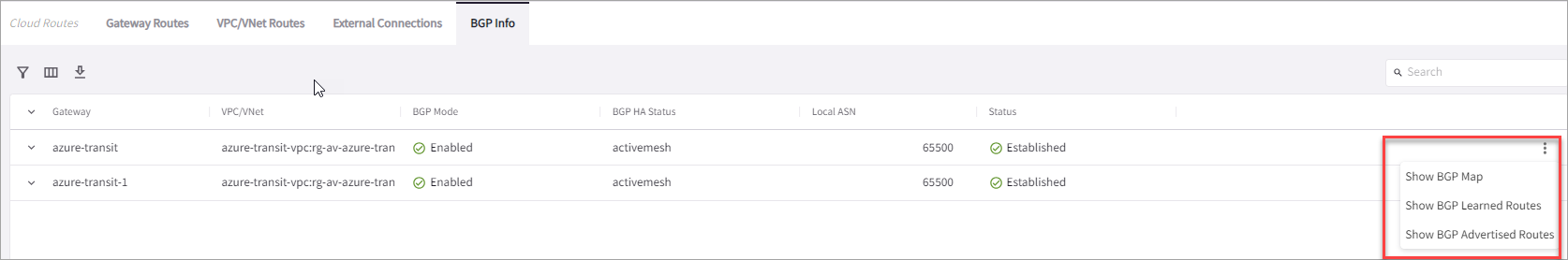
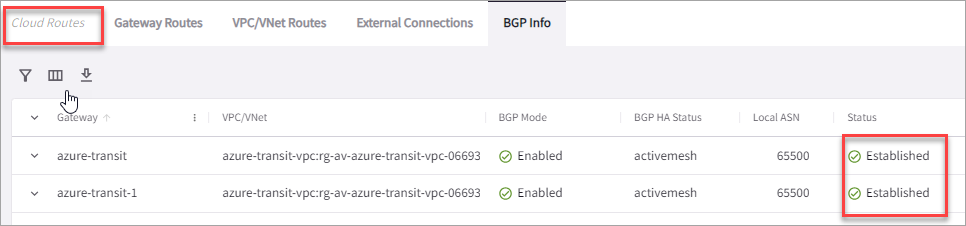
Verifying the BGP Session Status
You can check the BGP session status by going to Diagnostics > Cloud Routes > BGP Info. The Status should be Established. If some external connections for the selected Transit Gateway are Not Established, the overall BGP Status for the Transit Gateway is Partially Established.
You can also check the BGP Learned and Advertised routes.