Aviatrix SAML Authentication on Okta IdP
Overview
Aviatrix allows for centralized management of user access by integrating with your chosen Identity Provider (IdP) (in this case, Okta) via SAML. This allows you to control user access to Controller and CoPilot, as well as user access to the cloud environment using Aviatrix UserVPN (if desired).
This guide provides an example on how to configure Aviatrix to authenticate against Okta. When SAML is configured, your Aviatrix CoPilot acts as the Service Provider (SP) that redirects the user to the IdP for authentication.
Pre-Deployment Checklist
Before configuring SAML integration between Aviatrix and Okta, make sure the following is completed:
-
The Aviatrix Controller is deployed.
-
You have a valid Okta account with admin access.
-
You have downloaded and installed the Aviatrix SAML VPN client.
Aviatrix VPN Client
All users must use the Aviatrix VPN client to connect to the system. Download the client for your OS here.
Custom SAML Request Template (Optional)
This can be used in either the Controller/CoPilot or the UserVPN SAML setup.
<?xml version="1.0" encoding="UTF-8"?> <samlp:AuthnRequest xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol" ID="$ID" Version="2.0" IssueInstant="$Time" Destination="$Dest" ForceAuthn="false" IsPassive="false" ProtocolBinding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" AssertionConsumerServiceURL="$ACS"> <saml:Issuer xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion">$Issuer</saml:Issuer> </samlp:AuthnRequest>
Configuration Steps
Follow these steps to configure Aviatrix to authenticate against your Okta IDP:
-
Create an Okta SAML App for Aviatrix.
-
Retrieve Okta IDP metadata.
-
Launch an Aviatrix Gateway.
-
Create Aviatrix SAML SP Endpoint.
-
Test that the Integration is set up correctly.
-
Create Aviatrix VPN User.
Creating an Okta SAML App for Aviatrix
|
This step is usually done by the Okta Admin. |
-
Log in to the Okta Admin portal.
-
Follow Okta documentation to create a new application.
Field Value Platform
Web
Sign on method
SAML 2.0
-
General Settings
Field Value Description App name
Aviatrix
This can be any value. It will be displayed in Okta only.
App logo
Aviatrix logo
Aviatrix logo (optional)
App visibility
N/A
Leave both options unchecked
-
SAML Settings
-
General
Field Value Single sign on URL
https://[host]/flask/saml/sso/[SP Name](host = Controller IP)Audience URI (SP Entity ID)
https://[host]/(host = Controller IP)Default RelayState
Name ID format
Unspecified
Application username
Okta username
[host]is the hostname or IP of your Aviatrix CoPilot. For example, "https://copilot.demo.aviatrix.live."[SP Name]is an arbitrary identifier. This same value should be used when configuring SAML in Aviatrix CoPilot.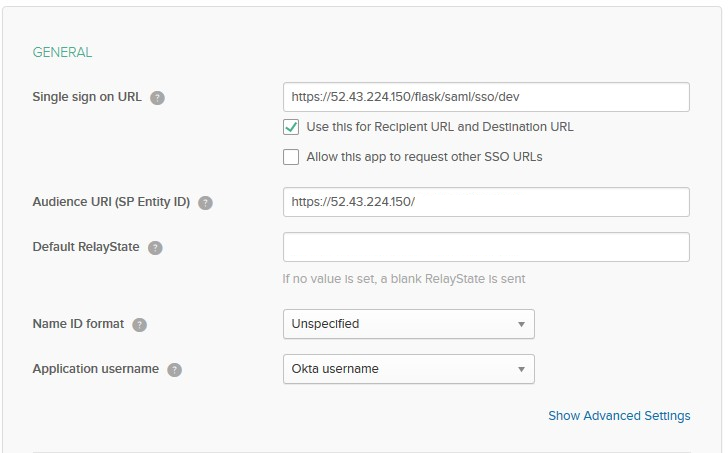
-
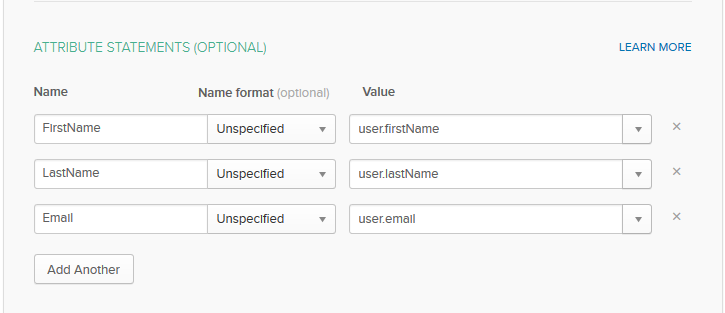
Attribute Statements
Name Name format Value FirstName
Unspecified
user.firstName
LastName
Unspecified
user.lastName
Email
Unspecified
user.email
-
Retrieving Okta IDP Metadata
|
This step is usually completed by the Okta admin. |
After the application is created in Okta, go to the Sign On tab for the application. Then, click View Setup Instructions.
Look for the section titled "Provide the following IDP metadata to your SP provider."
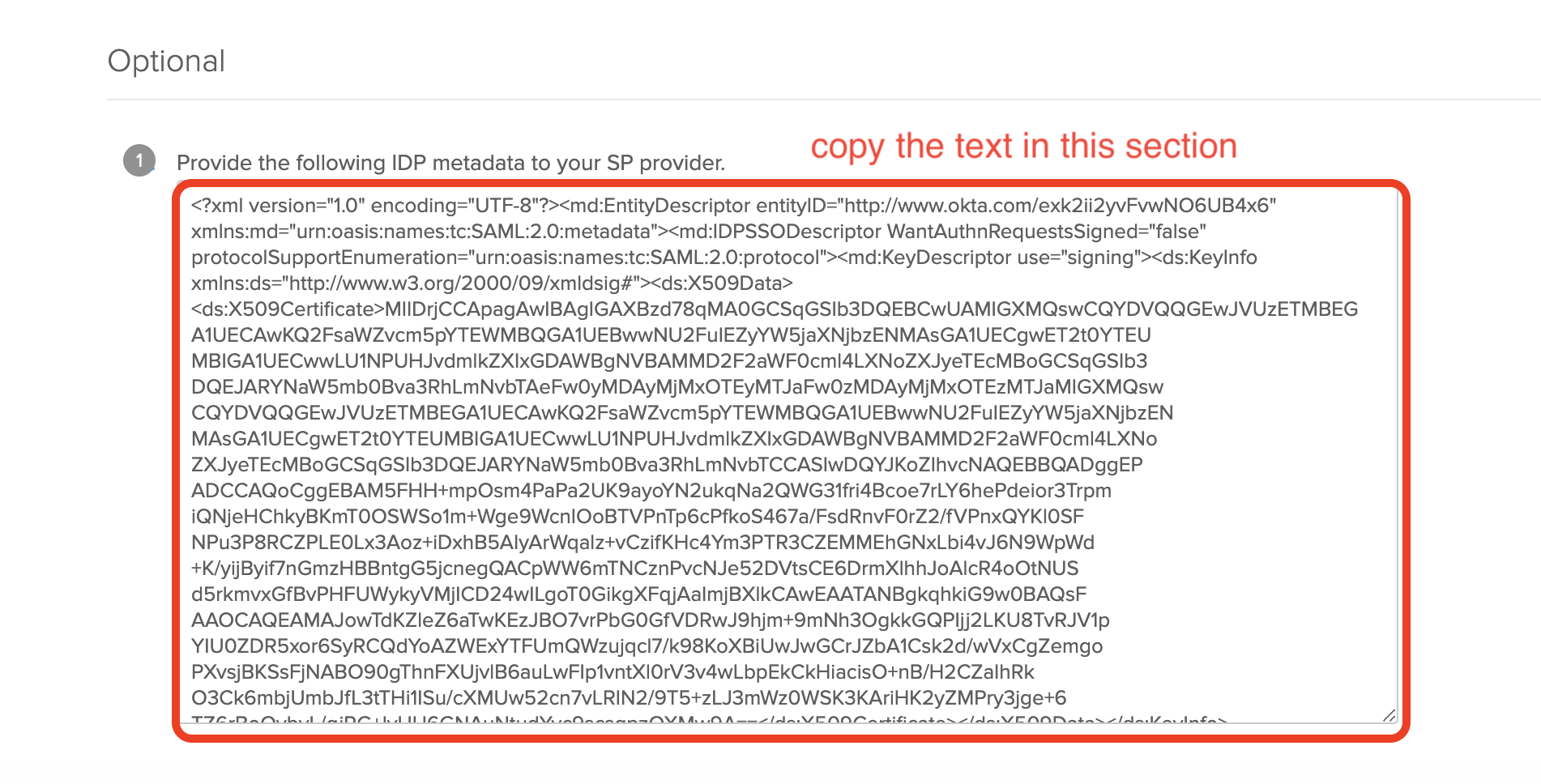
|
Copy the text displayed. This value will be used to configure the SAML "IDP Metadata URL" field in Aviatrix CoPilot. |
You need to assign the application to your account. Please follow steps 11 through 14 at Okta documentation.
Creating Aviatrix SAML Endpoint
|
This step is usually completed by the Aviatrix admin. |
-
Go to Aviatrix CoPilot > CloudFabric > UserVPN > select the Settings tab.
-
Under SAML, click + SAML Endpoint.
-
Enter the following information:
Field Value Name
SP Name(Use the same name you entered in the Okta Application previously)IDP Metadata Type
Text
IDP Metadata Text
Value Copied from Okta(Paste the value copied from Okta SAML configuration)Entity ID
Hostname
-
Click OK.
Testing the Integration
-
Start the Aviatrix VPN Client.
If you don’t start the client, you will receive a warning from the browser in the last step of this process
-
Log into Aviatrix CoPilot > Cloud Fabric > UserVPN > select the Settings tab.
-
Under SAML, find the SAML endpoint. In the Test column, select the link provided.
-
You should be redirected to the IdP. Now, you can log in and should be redirected back to CoPilot.
You will need to assign the new Okta application to a test user’s Okta account before clicking Test.
Now, you can log in and should be redirected back to CoPilot.
If everything is configured correctly, once you have authenticated you will be redirected back to CoPilot and the window will close.
Creating a VPN User
-
Create a new VPN user. Use the VPN gateway created above.
Validate
-
Go to Aviatrix CoPilot > CloudFabric > UserVPN > select the Users tab.
-
Download the configuration for your test user created in the previous step.
-
Open the Aviatrix VPN Client application.
-
Click Load Conf and select the file downloaded.
-
Click Connect.
|
SAML VPN supports shared certificates. You can share the certificate among VPN users or create more VPN users. |