TGW Approval
TGW VPN and TGW Direct Connect Gateway (TGW DXGW) dynamically learns BGP routes from remote peer. Aviatrix CoPilot periodically pulls the TGW route table and propagate these routes to Spoke VPCs route table that have connection policy to the VPN.
There are scenarios where you require an approval process before these learned CIDRs propagation take place. For example, a specific TGW VPN may be connected to a partner network and you need to make sure undesirable routes, such as the default route (0.0.0.0/0) are not propagated into your own network and accidentally bring down the network.
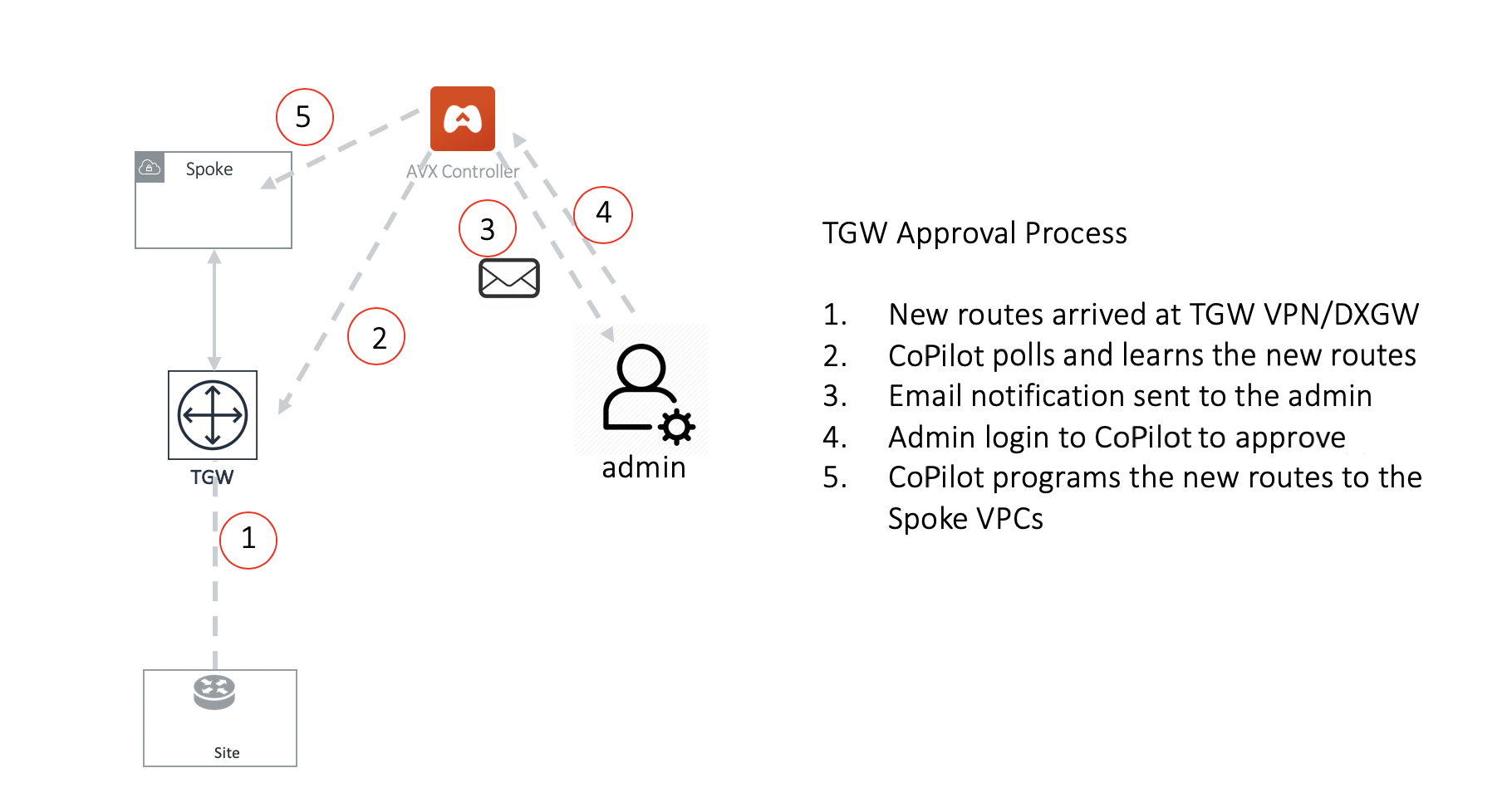
Approval is enabled on per TGW VPN and TGW DXGW bases. When Approval is enabled on a TGW VPN, dynamically learned routes trigger an email to the CoPilot admin.
To review Approvals:
-
Go to Networking > Connectivity > select the AWS TGW tab > select the AWS TGW > select the Approval tab.
-
Click on the AWS TGW Attachment dropdown to select the attachment to review.
-
Make sure Learned CIDR Approval is enabled.
-
All routes appear, both unapproved and already approved.
-
To approve an unapproved route, click Approve in its row. Now, the route can be propagated.
-
To disapprove an approved route, click Remove in its row.
-
How the Approval Feature Works
When Learned CIDR Approval is enabled, TGW route table route propagation to the connected Network Domain is turned off. That is, the TGW VPN/DXGW learned routes are statically programmed into the TGW route table of connected Network Domains after the routes are approved.
This is illustrated in the following two examples.
Example 1: Two TGW VPN/DXGW in the same domain
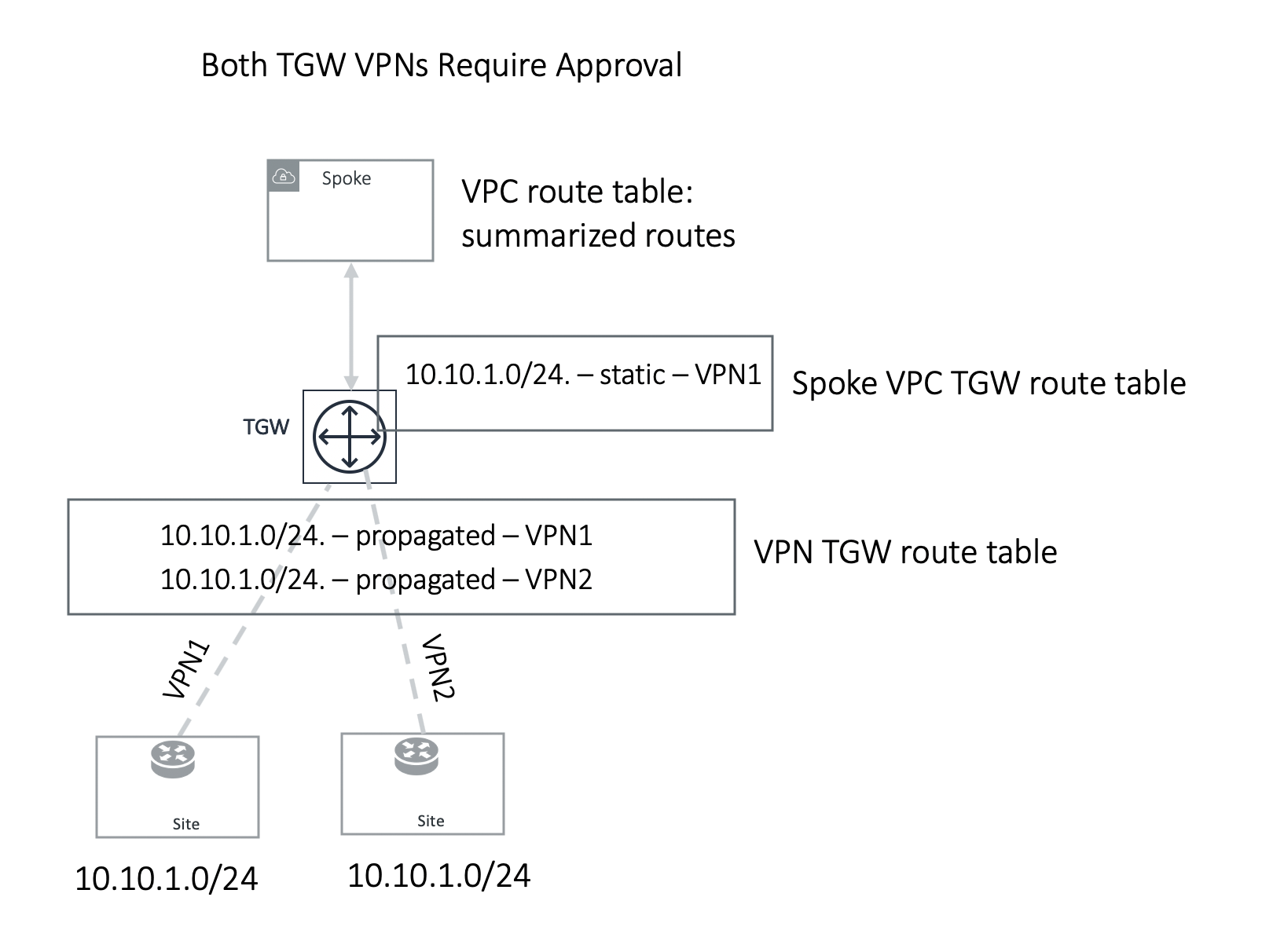
In the example above, two identical VPN CIDRs 10.10.1.0/24 are advertised to two TGW VPNs but are in the same domain. Both have Approval enabled. Whichever VPN attachment learns the CIDR first and is approved, its attachment is programmed into Spoke associated TGW route table, in this case, VPN1 attachment is approved first and is programmed into the Spoke associated TGW route table. VPN2 CIDR should continue to remain in pending list. If VPN1 withdraw route 10.10.1.0/24, you can initiate approval by moving the VPN2 pending CIDR to the approved panel, and this time it should be programmed.
Example 2: One TGW VPN requires approval and another one does not
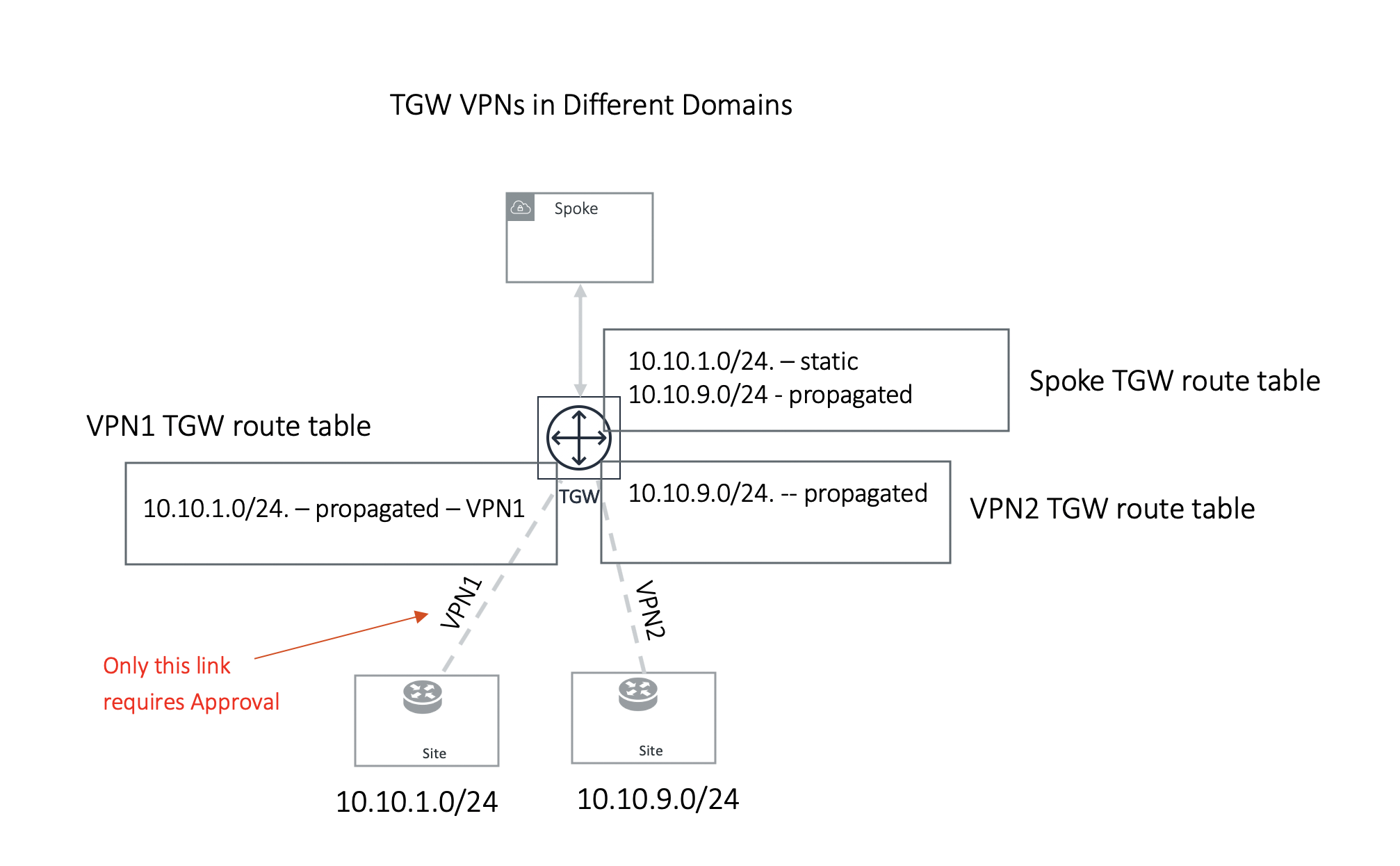
In the second example, TGW VPN2 link 10.10.9.0/24 is in a different domain and does not require approval. Its route is propagated to the Spoke TGW route table, while TGW VPN1 link 10.10.1.0/24 is statically programmed to Spoke TGW route table after approval is initiated by the customer.
Note in the second example, if TGW VPN2 link advertises the same network CIDR 10.10.1.0/24, this CIDR will be propagated first and TGW VPN1 approval request will be rejected and the CIDR 10.10.1.0/24 from TGW VPN1 remains in the approval pending list.