Deploy an Edge Transit Gateway on Equinix Network Edge
This document provides instructions to deploy a primary Edge Transit Gateways on Equinix Network Edge.
For an overview of Aviatrix Edge, see About Aviatrix Hybrid Cloud Edge.
Topology
The following diagram shows an example of network connectivity for Edge Transit Gateway to Transit Gateways in the cloud and Edge Spoke Gateway at remote site.
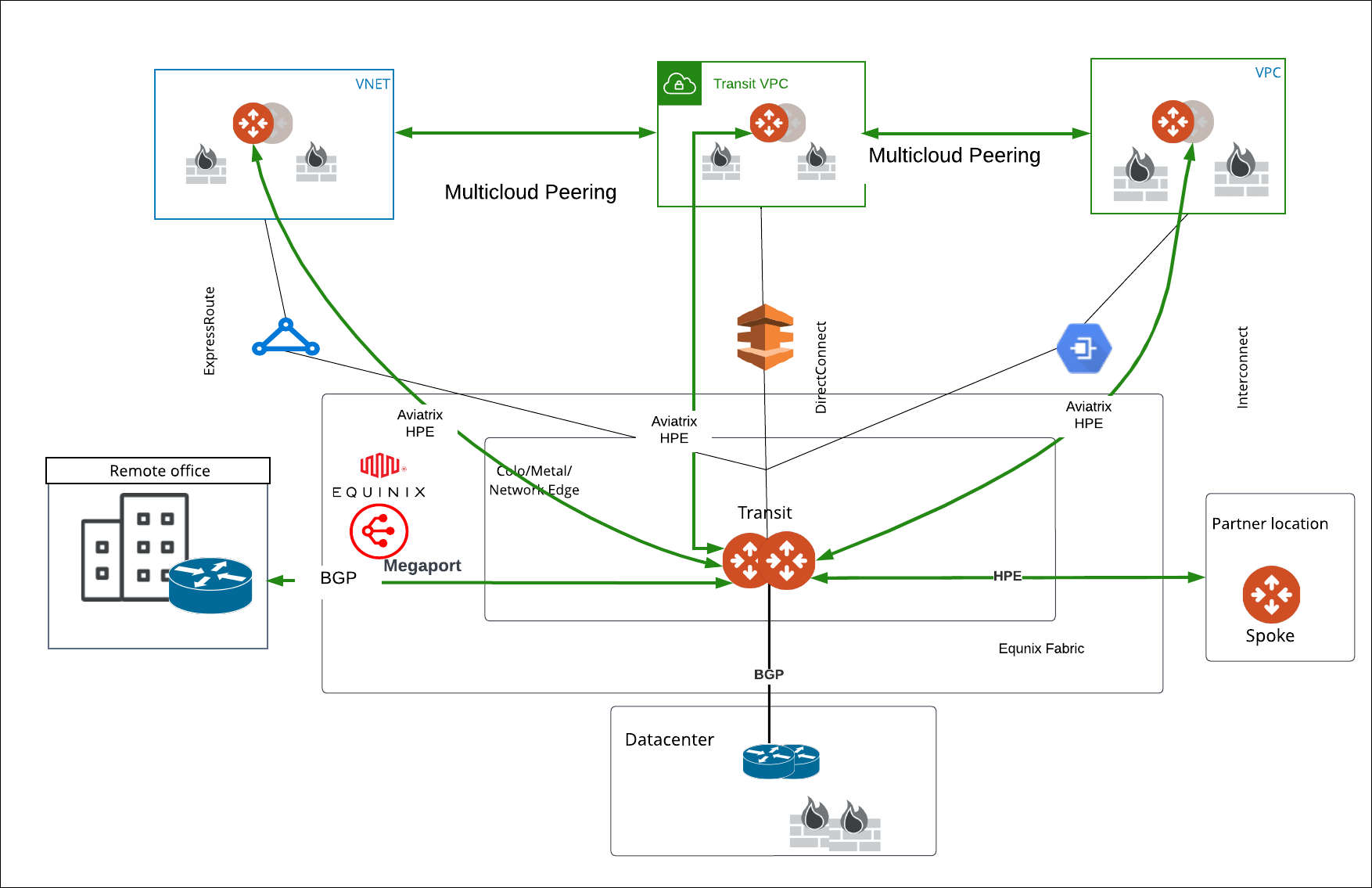
Prerequisites
Before you deploy an Edge Transit Gateway on the Equinix platform, ensure the prerequisite steps are complete.
Deploy the Primary Edge Transit Gateway (Equinix)
To deploy an Edge Transit Gateway, first you need to generate the cloud-init file in CoPilot, then deploy the Edge gateway in Equinix using the cloud-init file:
Next Steps
-
For high availability (HA) and redundancy, you can create and deploy HA Edge Transit Gateway. See Deploy a HA Edge Transit Gateway (Equinix).
-
For hybrid, multicloud, or LAN-side connectivity, you can attach the Edge Transit Gateway to multiple Aviatrix gateways . See Edge Gateway Attachments.
-
For remote site connectivity, you can connect the Edge Transit Gateway to remote devices. See Edge Gateway External Connection.