Overview of Aviatrix ActiveMesh
ActiveMesh is an Aviatrix Encrypted Transit Network architecture where both primary gateways and backup gateways forward packets in a load balancing fashion. The architecture statistically doubles the network throughput. In addition, in ActiveMesh mode, multiple remotes sites can be connected to the Aviatrix Transit gateways.
| ActiveMesh is enabled by default, and cannot be disabled. |
The diagram below shows an ActiveMesh deployment between Spoke and Transit where each Spoke Gateway in a VPC/VNet builds two IPsec tunnels to the primary and backup transit gateways and forwards packets to both of them inside the tunnel. The load balance mechanism leverages ECMP protocol.
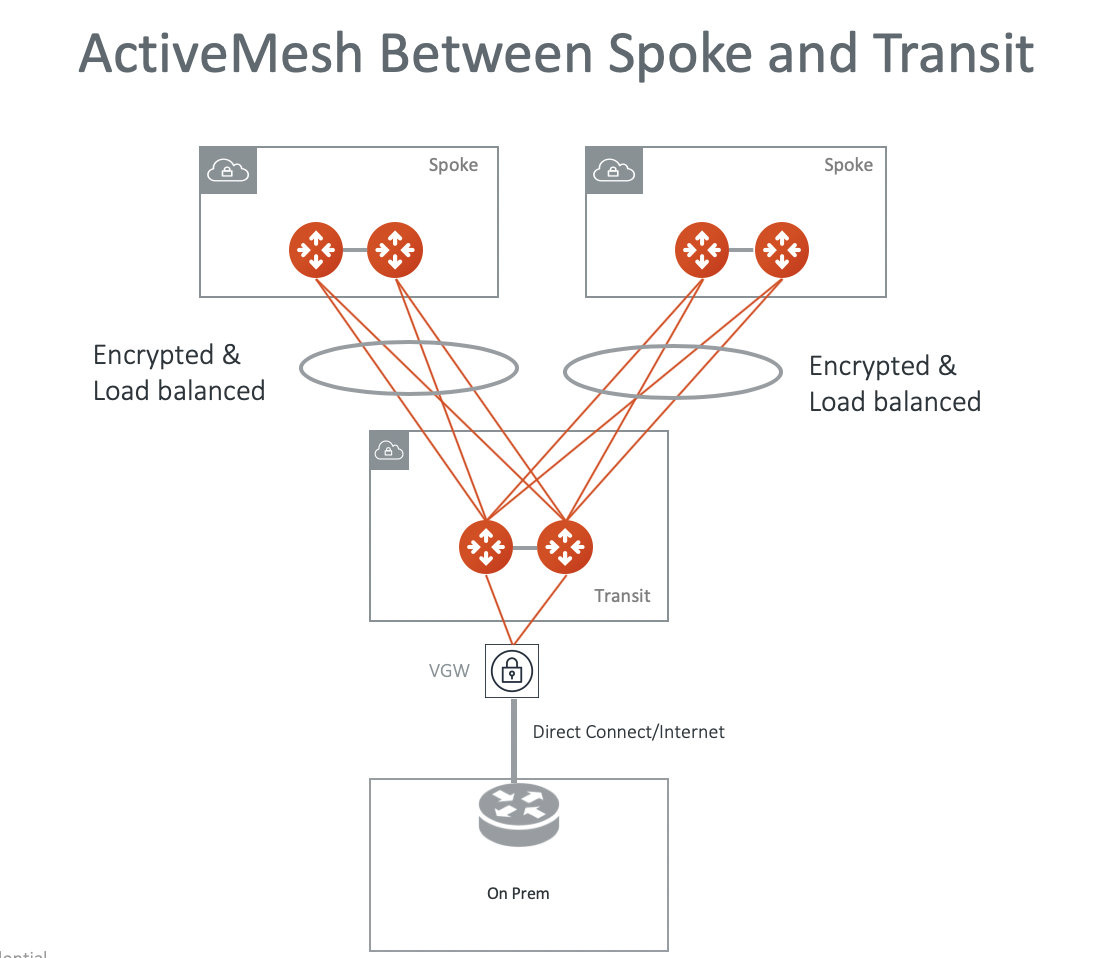
When Aviatrix Controller detects that an ActiveMesh gateway is down, Controller automatically starts it again. Once the gateway comes up, it participates in packet forwarding again.
Key advantages of ActiveMesh
The key benefits of ActiveMesh are improved network resiliency, failover convergence time and performance.
ActiveMesh for Transit Gateway Peering
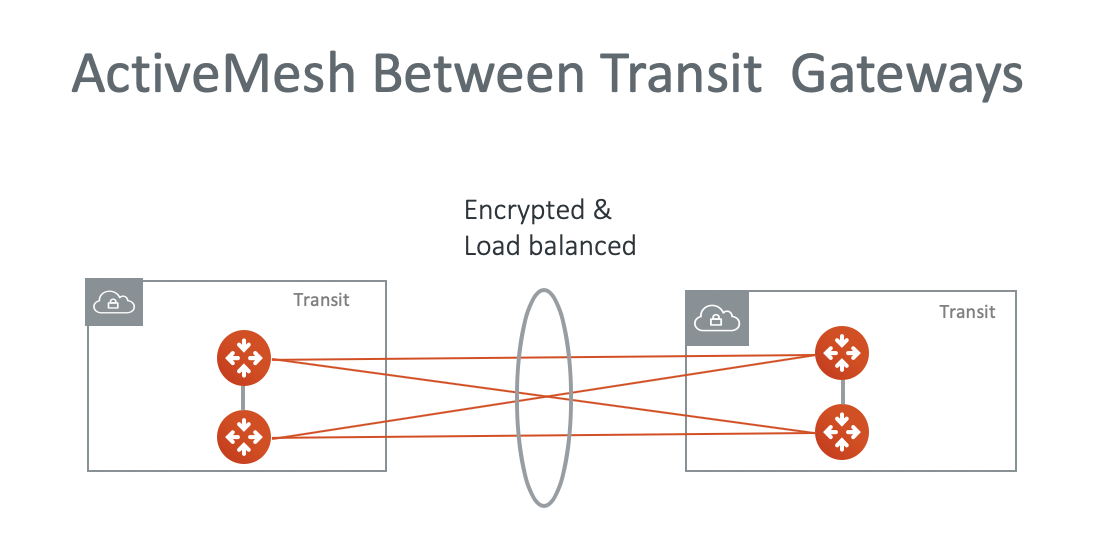
ActiveMesh can be applied to connect two Transit GWs. There are 4 tunnels established between the Transit GWs, as shown in the diagram below.
ActiveMesh Connection to VGW
Each Transit GW connecting to the VGW in ActiveMesh mode has two VPN tunnels to the VGW.
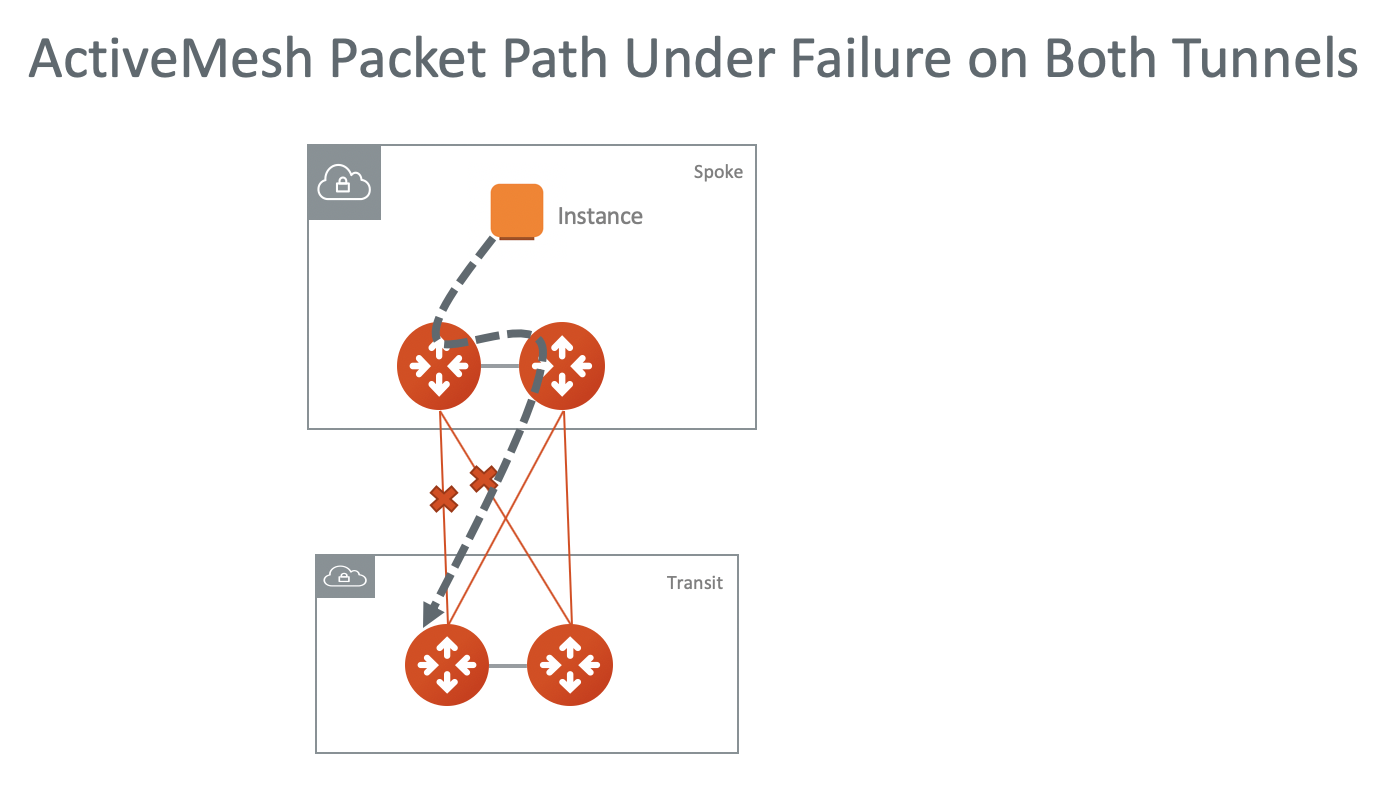
Link Between two ActiveMesh Gateways
The link between two ActiveMesh gateways is used to forward packets when both tunnels are down for one of the ActiveMesh gateway.
For example, in a spoke VPC/VNet, virtual machine (EC2/GCE) traffic is forwarded to the ActiveMesh primary gateway which then forwards traffic to the AVX Transit GW. If both tunnels between the ActiveMesh spoke gateway and the Transit GW are down, the packet is forwarded by the ActiveMesh primary gateway to the backup ActiveMesh gateway.
Enabling ActiveMesh for Route Based and Policy Based VPN
ActiveMesh enables the Aviatrix Transit Gateway to connect to multiple remote sites over IPsec VPN tunnels.
When you configure VPN to remote sites from MULTI-CLOUD TRANSIT > Setup > External Connection (Connect to VGW/External Device/Azure VNG in the Transit Network workflow, the VPN tunnel is built with route based VPN on the Aviatrix Transit Gateway.
ActiveMesh Transit Gateway supports both remote route based VPN and remote policy based VPN tunnels. In both cases, the Aviatrix Transit Gateway operates in route based mode.
| If the remote site is policy based static VPN, traffic must be initiated from the remote site. |
On the other hand, when you configure VPN to remote sites from Site2Cloud page and select a Transit Gateway, the VPN tunnel is built with policy based VPN.
How do Spoke gateways load balance traffic from EC2 instance?
VPC route table points to only one Spoke Gateway, so there is no load balancing for traffic initiated from virtual machine instances. But once the traffic arrives at the gateway for transmission to the Spoke VPC/VNet, the traffic is load balanced across the ActiveMesh peering to the Spoke VPC/VNet Gateways.