Configuring FortiGate in AWS
Example Config for FortiGate VM in AWS
In this document, we provide an example to set up the FortiGate Next Generation Firewall instance for you to validate that packets are sent to the FortiGate Next Generation Firewall for VPC-to-VPC and from VPC-to-Internet traffic inspection.
The Aviatrix Firewall Network (FireNet) workflow launches a FortiGate Next Generation Firewall instance at this step. After the launch is complete, the console displays the FortiGate Next Generation Firewall instance with the public IP address of its management/egress interface and allows you either to download the .pem file for SSH access to the instance, or to access the FortiGate web page.
Here is the Firewall information in this example for your reference. Please adjust it depending on your requirements.
| Example setting | Example value |
|---|---|
Firewall Image |
Fortinet FortiGate Next-Generation Firewall |
Firewall Image Version |
6.2.3 |
Firewall Instance Size |
c5.xlarge |
Egress Interface Subnet |
Select the subnet whose name contains "FW-ingress-egress." |
Key Pair Name (Optional) |
The .pem file name for SSH access to the firewall instance. |
Attach |
Check |
|
The FortiGate Next Generation Firewall instance has two interfaces as described below. Additionally, firewall instance eth1 is on the same subnet as FireNet gateway eth2 interface. |
| Fortigate VM instance interfaces | Description | Inbound Security Group Rule |
|---|---|---|
eth0 (on subnet -Public-FW-ingress-egress-AZ-a) |
Egress or Untrusted interface |
Allow ALL |
eth1 (on subnet -dmz-firewall) |
LAN or Trusted interface |
Allow ALL (Do not change) |
Below are the steps for initial setup.
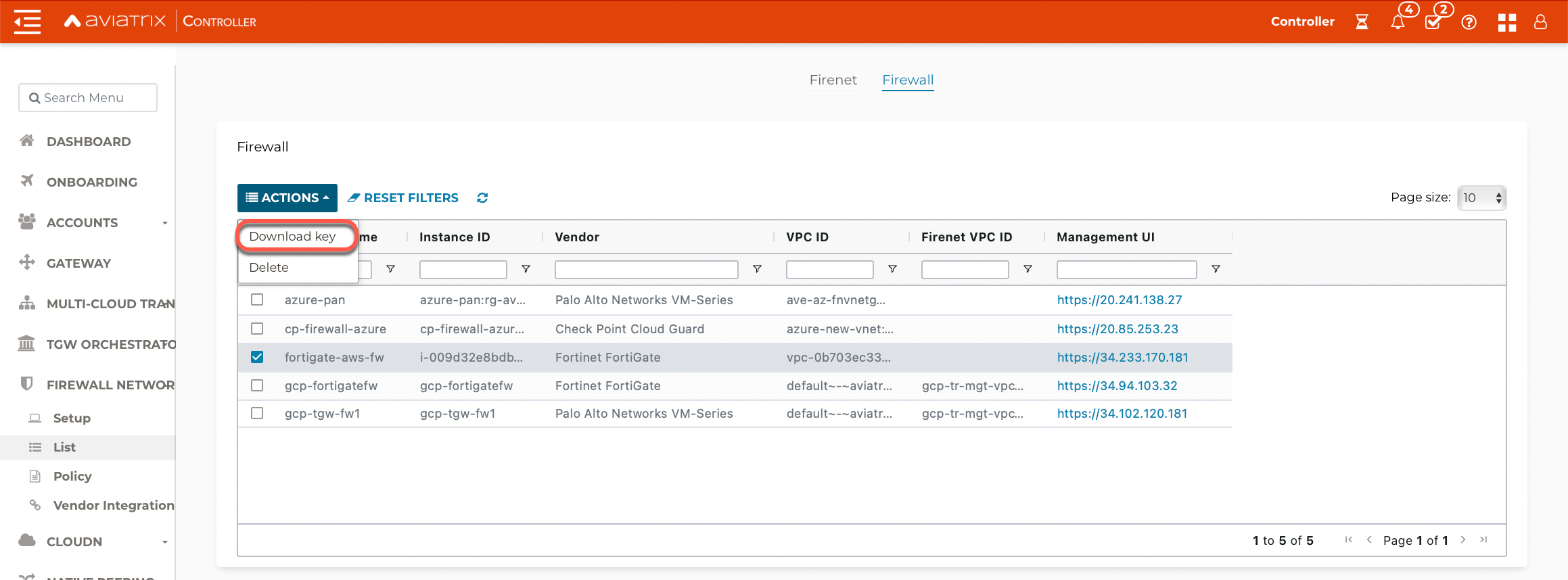
Downloading FortiGate Next Generation Firewall Access Key
After this step in the workflow is completed, select the firewall on the Firewall Setup > List > Firewall page and click Download key in the Actions menu to download the .pem file.
If you get a download error, usually it means the FortiGate Next Generation Firewall instance is not ready. Wait until it is ready, refresh the browser and then try again.
Logging in to the FortiGate Next Generation Firewall
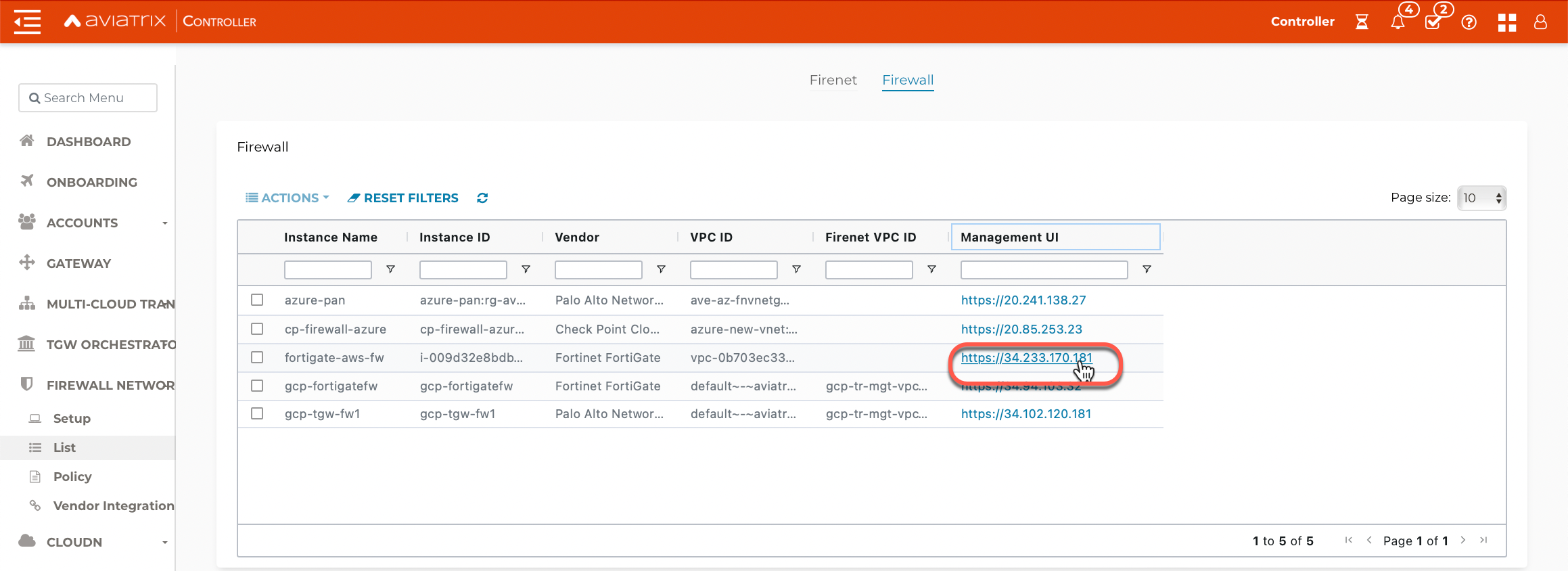
In the Aviatrix Controller, navigate to Firewall Network > List > Firewall and click on the Management UI link. This takes you to the FortiGate Next Generation Firewall you just launched. The username is 'admin' and the default password is the Instance ID of the firewall, which you can copy from the Firewall tab. You are prompted to change this password after logging on.
|
If the Management UI link does not open on your default browser, try another browser (such as Chrome or Firefox). |
Resetting FortiGate Next Generation Firewall Password
Once logged in with the default password, it will ask you to set a new password.
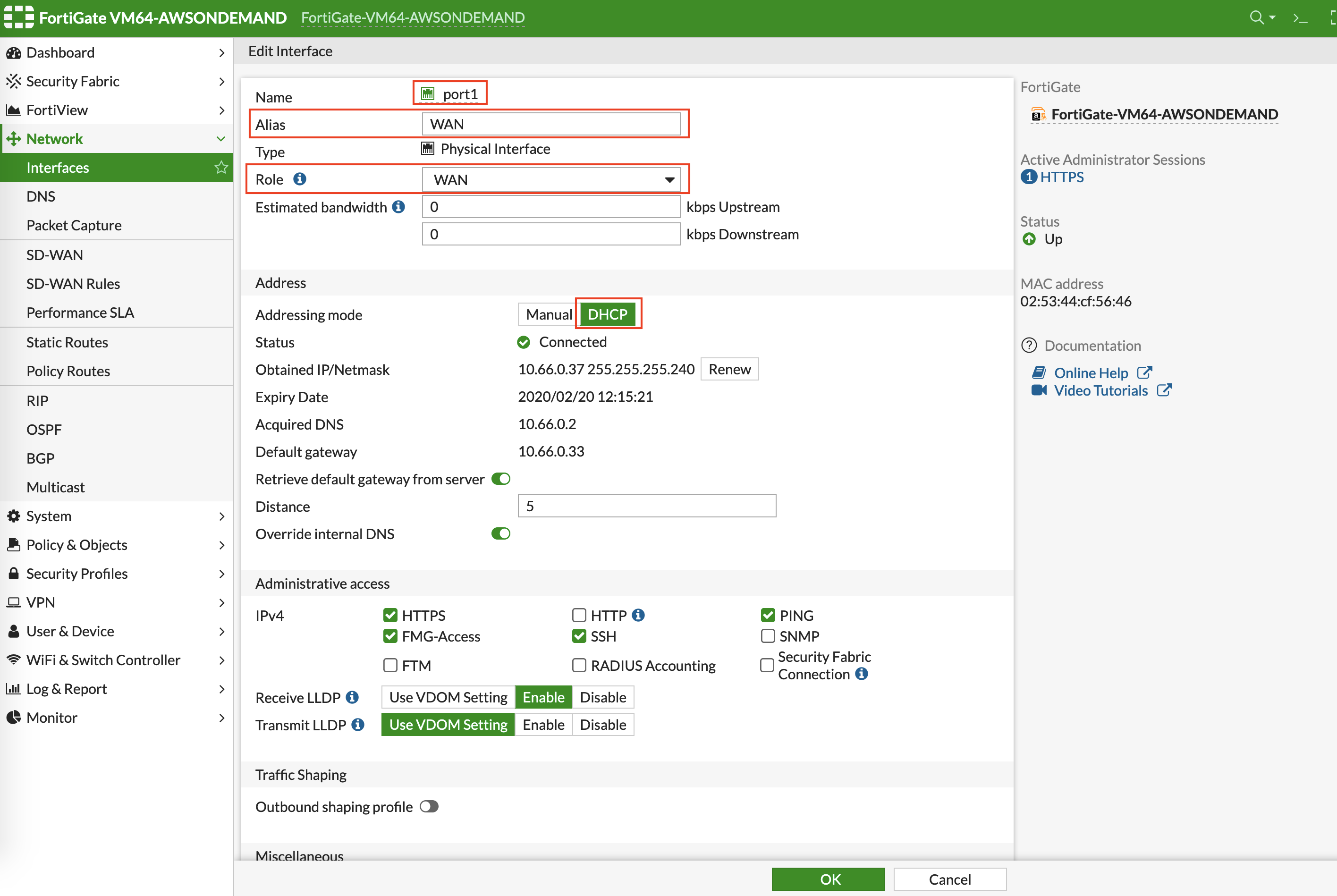
Configuring FortiGate Next Generation Firewall port1 with WAN
After logging in with the new password, go to the page to configure Physical Interface port1 as per the following screenshot.
-
Select the interface with port 1 and click Edit.
-
Enter an Alias (i.e.: WAN) for the interface.
-
Specify appropriate role (WAN).
-
Enable DHCP to ensure FW retrieve private IP information from the AWS console.
-
Enable Retrieve default gateway from server.
Configure FortiGate Next Generation Firewall port2 with LAN
Go to the page Network > Interfaces to configure Physical Interface port2 as per the following screenshot.
-
Select the interface with port 2 and click Edit.
-
Enter an Alias (i.e.: LAN) for the interface.
-
Specify appropriate role (LAN).
-
Enable DHCP to ensure FW retrieve private IP information from AWS console.
-
Enable Administrative Access: IPv4 > HTTPS.
-
Disable Retrieve default gateway from server.
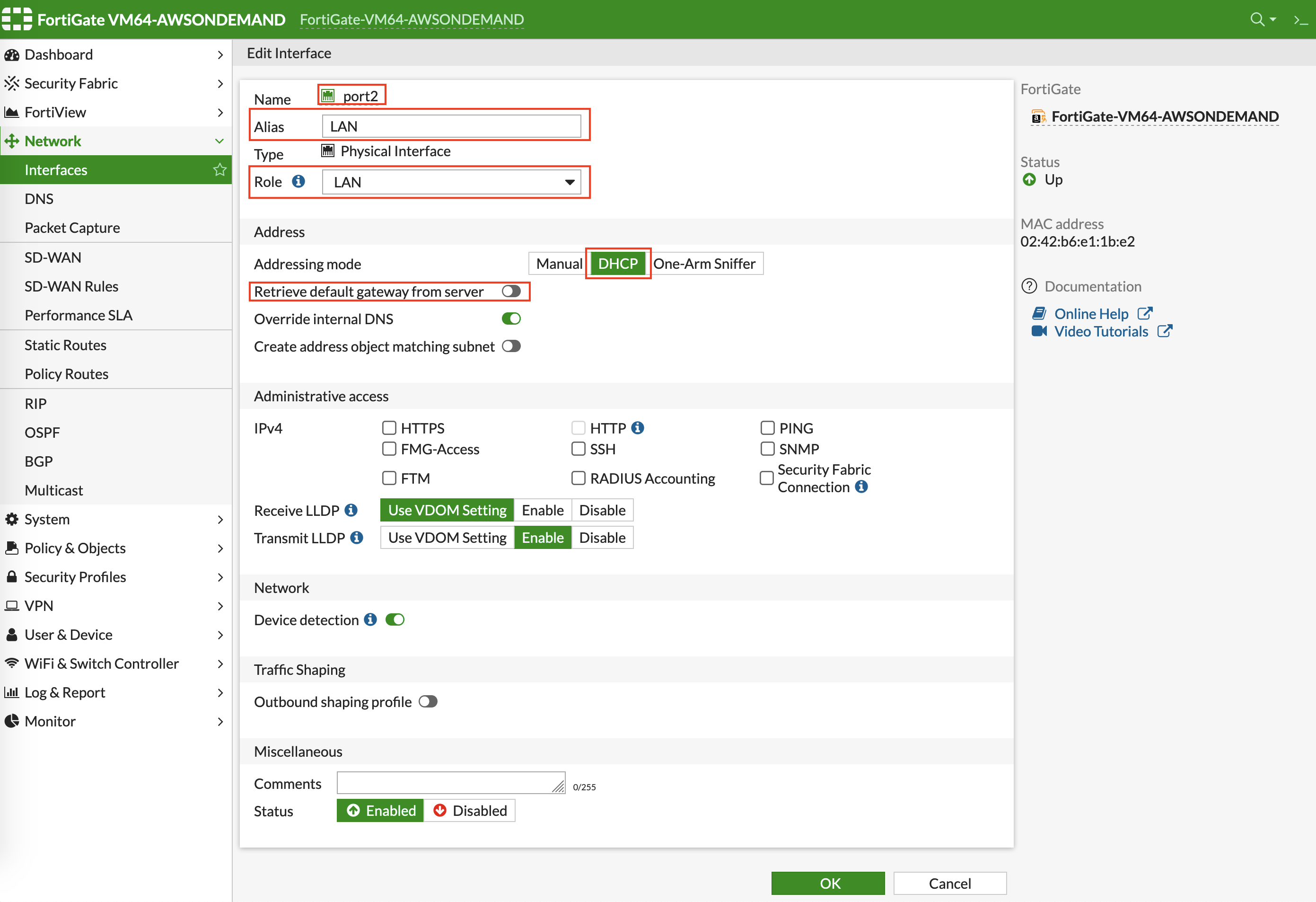
Creating Static Routes for Routing of Traffic VPC to VPC
Packets to and from TGW VPCs, as well as on-premises, will be hairpinned off the LAN interface. As such, you need to configure appropriate route ranges that you expect traffic for packets that need to be forward back to TGW. For simplicity, you can configure the FW to send all RFC 1918 packets to LAN port, which sends the packets back to the TGW.
In this example, we configure all traffic for RFC 1918 to be sent out of the LAN interface.
In the FortiGate UI, go to Network > Static Routes to create a Static Route as the following screenshot.
-
Click Create New.
-
Enter the destination route in Destination.
-
In Gateway Address, you will need to enter the AWS default gateway IP on subnet -dmz-firewall.
|
The subnet CIDR for -dmz-firewall is 10.66.0.96/28, thus the AWS default gateway IP on this subnet is 10.66.0.97. |
-
The interface will be the LAN (port2).
-
Configure an appropriate admin distance if you expect overlapping routes that need to be prioritized.
-
Enter comments as necessary.
-
Repeat the steps above for RFC 1918 routes.
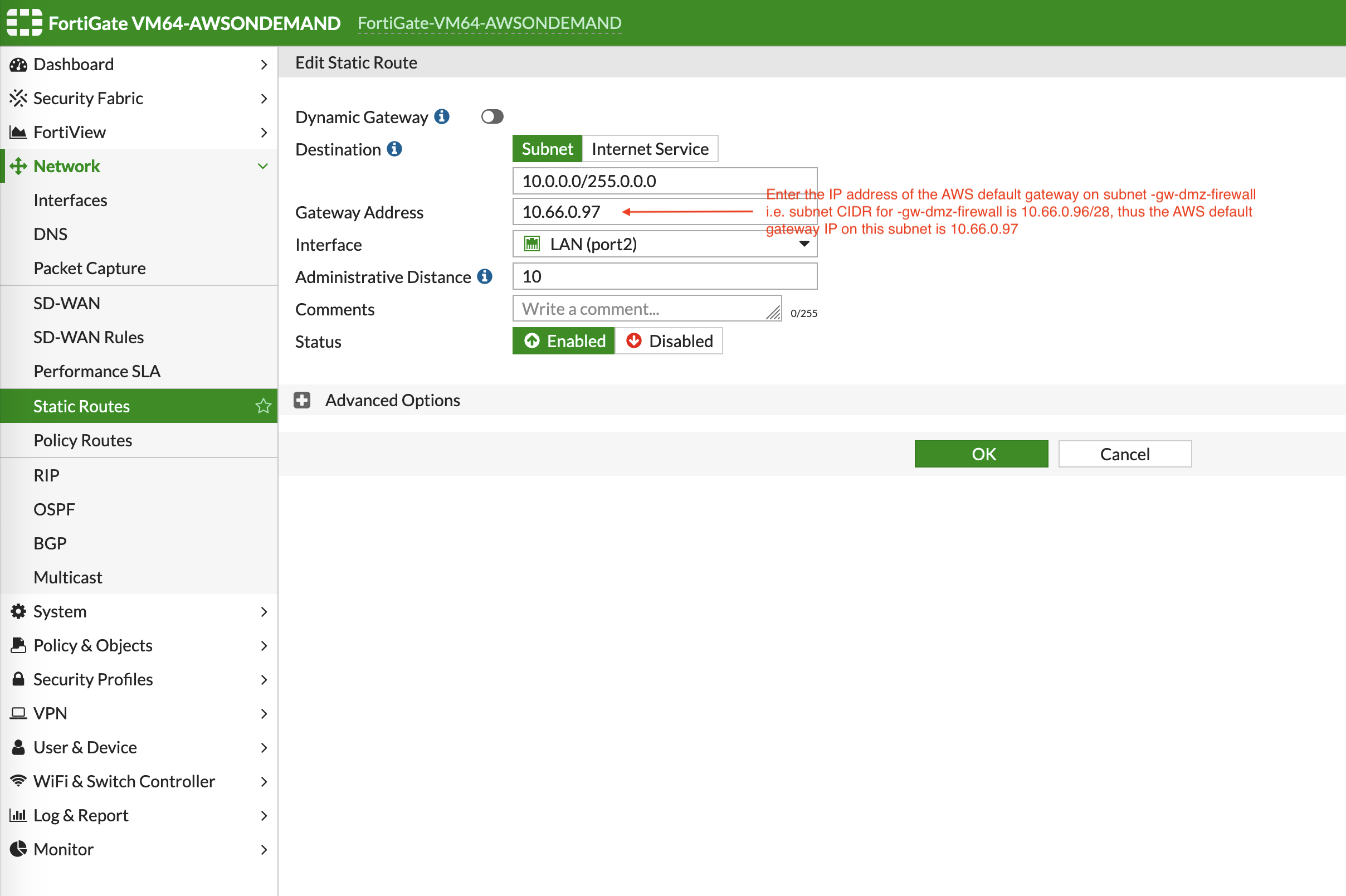
Those static routes can also be reviewed by navigating to Monitor > Routing Monitor.
(Optional) Firewall Vendor Integration
Integrating a FortiGate firewall with the Aviatrix Controller enables the Controller to make automatic route updates to the FortiGate routing tables. You may also manually enable the integration with your CSP management tools. FortiGate integration is supported in AWS, Azure, and GCP clouds.
Integrate the FortiGate firewall with the Aviatrix Controller:
-
Generate a Firewall API Token from FortiGate. This token is required to integrate the FortiGate firewall with the Controller.
-
In the FortiGate UI, go to System > Admin Profiles > Create New.
-
Enable the Read/Write option for Network and click OK.
-
Navigate to System > Administrators > Create New > REST API Admin.
-
Supply a Username and choose the Admin Profile from the previous step, and click OK.
-
Copy the generated token. It will only be displayed once.
-
Go to Aviatrix Controller > Firewall Network > Vendor Integration (ensure that you have already enabled egress for this firewall).
-
Enter the vendor firewall information into the Controller.
-
Click Save, then Show, then Sync to enable the Aviatrix Controller and FortiGate firewall integration.
The Aviatrix Controller is now enabled to make automatic route updates to the FortiGate routing tables.
Configuring Basic Traffic Policy to Allow Traffic VPC-to-VPC
In this step, you will configure a basic traffic security policy that allows traffic to pass through the firewall. Given that Aviatrix Gateways will only forward traffic from the TGW to the LAN port of the Firewall, you can set your policy condition to match any packet that is going in/out of the LAN interface.
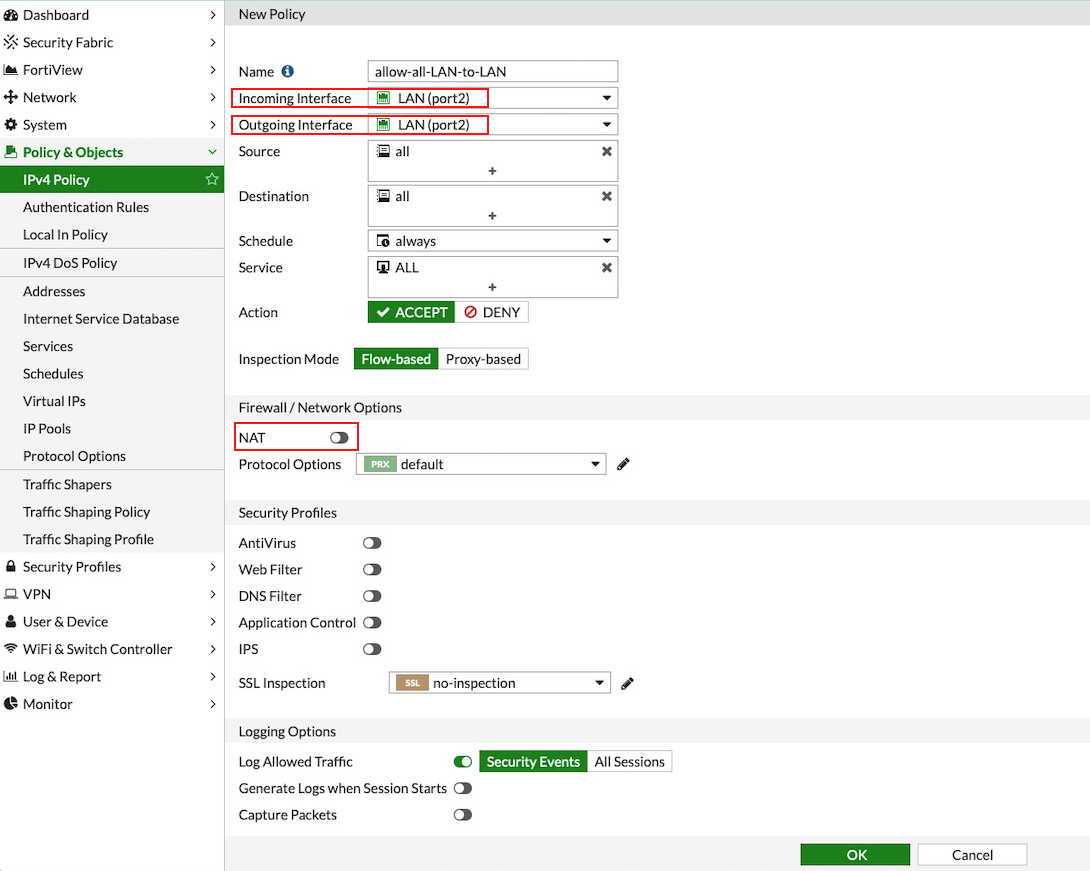
Navigate to Policy & Objects > IPv4 Policy > Create New / Edit to configure the policy as shown in the following table.
| Field | Value |
|---|---|
Name |
Configure any name for this policy |
Incoming Interface |
LAN (port2) |
Outgoing Interface |
LAN (port2) |
Source |
Click on the + sign and add all |
Destination |
Click on the + sign and add all |
Schedule |
always |
Service |
ALL |
Action |
ACCEPT |
NAT |
Disabled |
After validating that your TGW traffic is being routed through your firewall instances, you can customize the security policy to your requirements.
(Optional) Configuring Basic Traffic Policy to Allow Traffic VPC to Internet
In this step, we will configure a basic traffic security policy that allows Internet traffic to pass through the firewall. Given that Aviatrix Gateways will only forward traffic from the TGW to the LAN port of the Firewall, you can set your policy condition to match any packet that is going into the LAN interface and going out of the WAN interface.
First you enable egress inspection:
-
In the Aviatrix Controller, navigate to Firewall Network > List > Firenet.
-
Select a Transit FireNet in the list and click Details.
-
Scroll down to Egress through Firewall and click Enable.
-
Verify the Egress status on the Firewall Network > List > Firenet page.
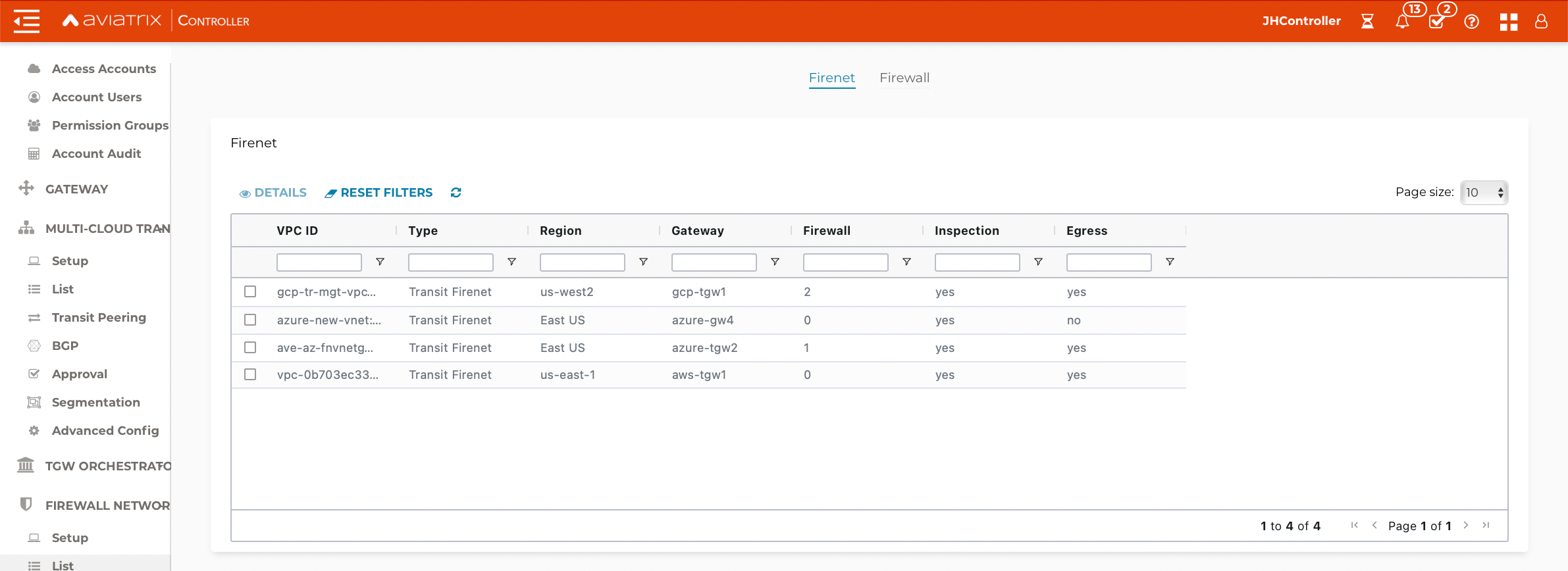
You then create the new traffic policy in the FortiGate UI:
-
Navigate to Policy & Objects > IPv4 Policy > Create New / Edit to configure the policy as per the following table.
| Field | Value |
|---|---|
Name |
Configure any name for this policy |
Incoming Interface |
LAN (port2) |
Outgoing Interface |
WAN (port1) |
Source |
Click on the + sign and add all |
Destination |
Click on the + sign and add all |
Schedule |
always |
Service |
ALL |
Action |
ACCEPT |
NAT |
Enable |
|
The NAT function needs to be enabled on this VPC to Internet policy. |
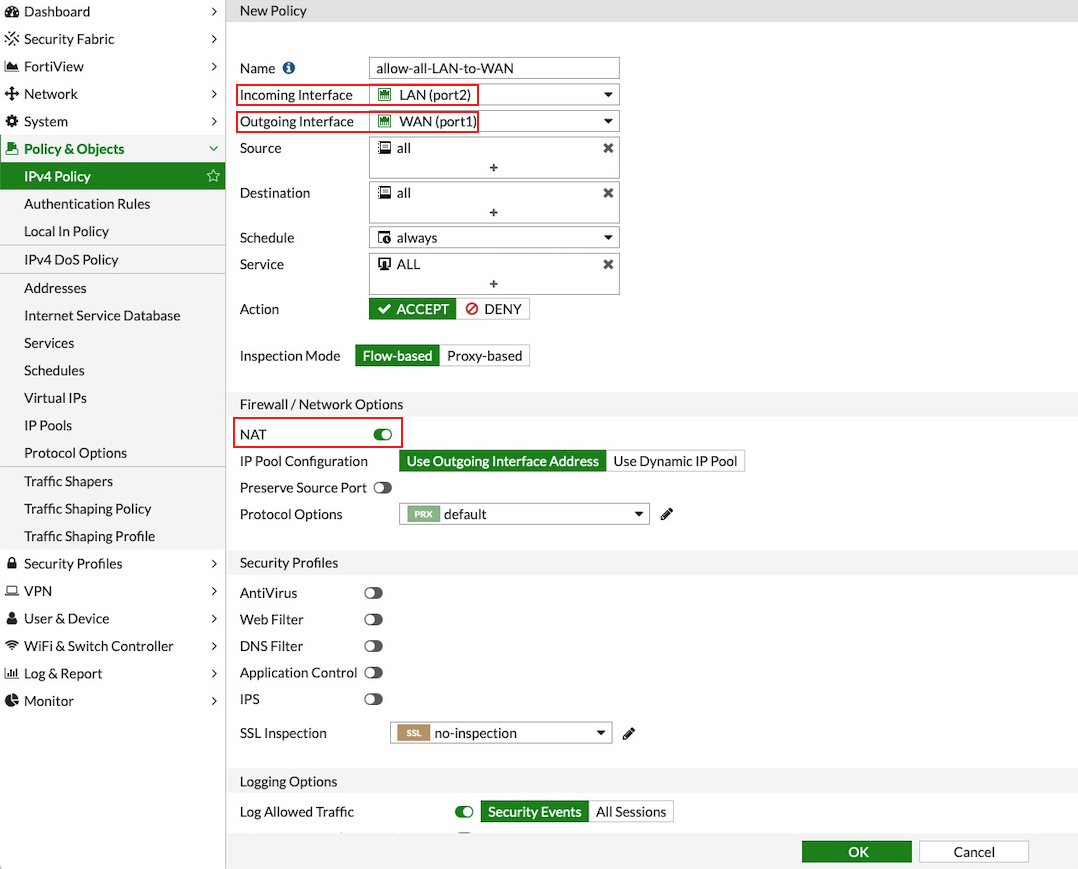
After validating that your TGW traffic is being routed through your firewall instances, you can customize the security policy to your requirements.
Ready to Go
Now your firewall instance is ready to receive packets.
The next step is to specify which Network Domain needs packet inspection by defining a connection policy that connects to the firewall domain. This operation is done by this step in the Firewall Network workflow. In addition, attach VPC to TGW by Step 1 in the TGW Orchestrator Build workflow.
For example, deploy Spoke-1 VPC in Network_Domain_1 and Spoke-2 VPC in Network_Domain_2. Build a connection policy between the two domains. Build a connection between Network_Domain_2 to Firewall Domain.
Viewing the Traffic Log
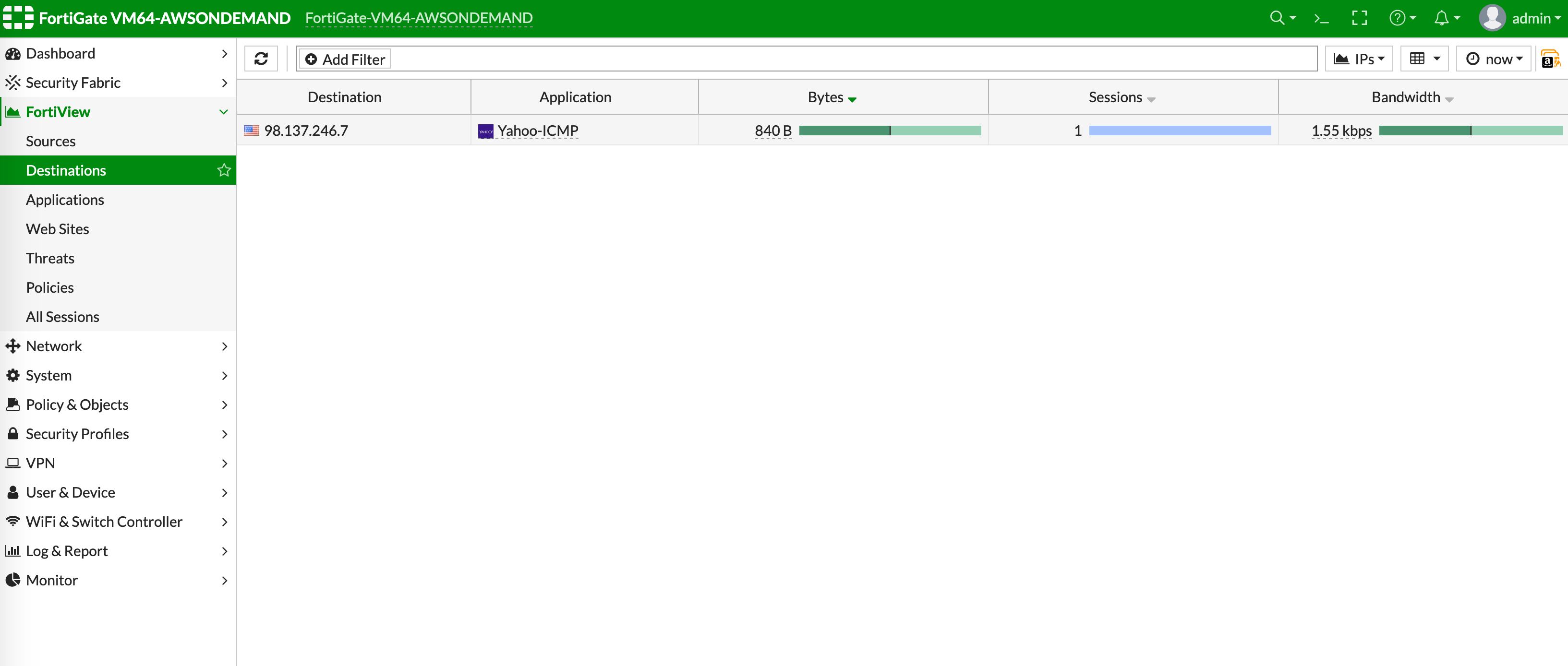
You can view if traffic is forwarded to the firewall instance by logging in to the FortiGate Next Generation Firewall console. Go to FortiView > Destinations.
VPC-to-VPC Traffic
Launch one instance in Spoke-1 VPC and one in Spoke-2 VPC. Start pinging packets from an instance in Spoke-1 VPC to the private IP of another instance in Spoke-2 VPC where one or both of the Network Domains are connected to Firewall Network Domain. The ICMP traffic should go through and be inspected on the firewall.
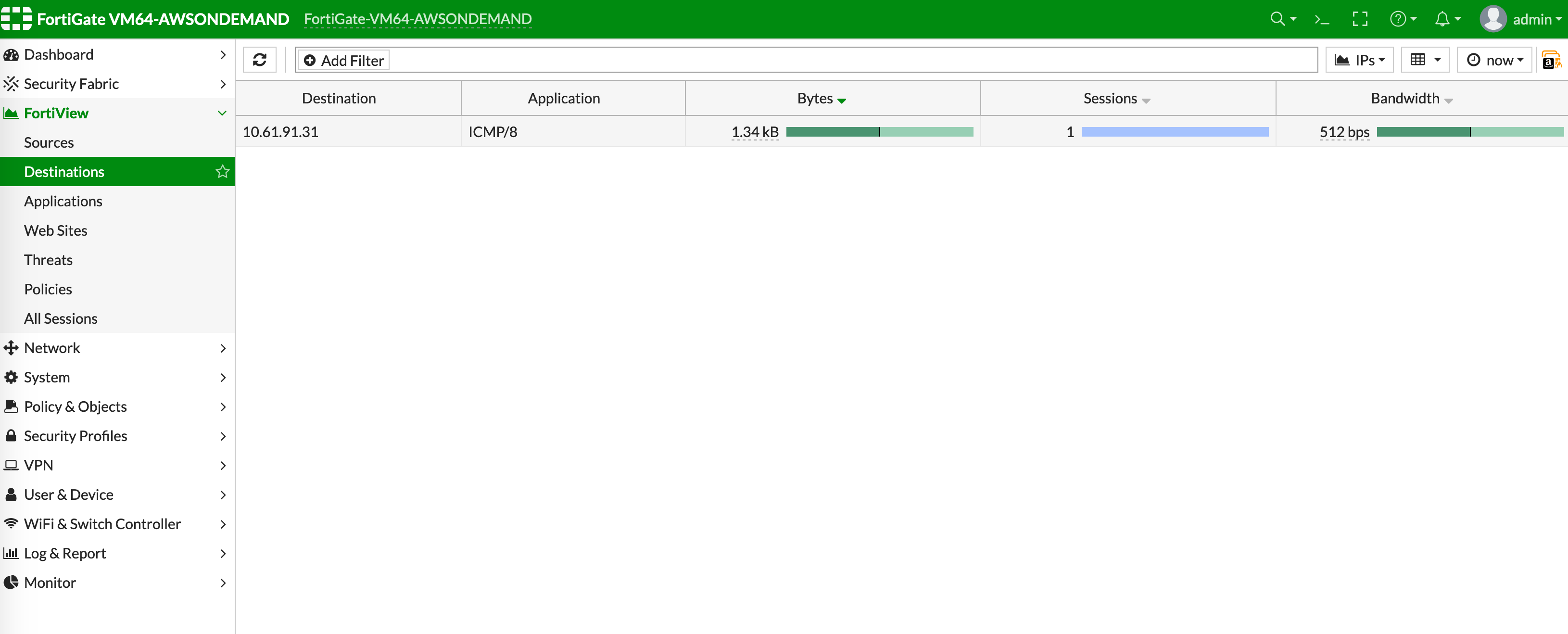
[Optional] VPC to Internet Traffic
Launch a private instance in the Spoke VPC (i.e. Spoke-2 VPC) where the Network Domain (i.e. Network_Domain_2) is connected to Firewall Network Domain. Start pinging packets from the private instance to the Internet service to verify egress function. The ICMP traffic should go through and be inspected on the firewall.