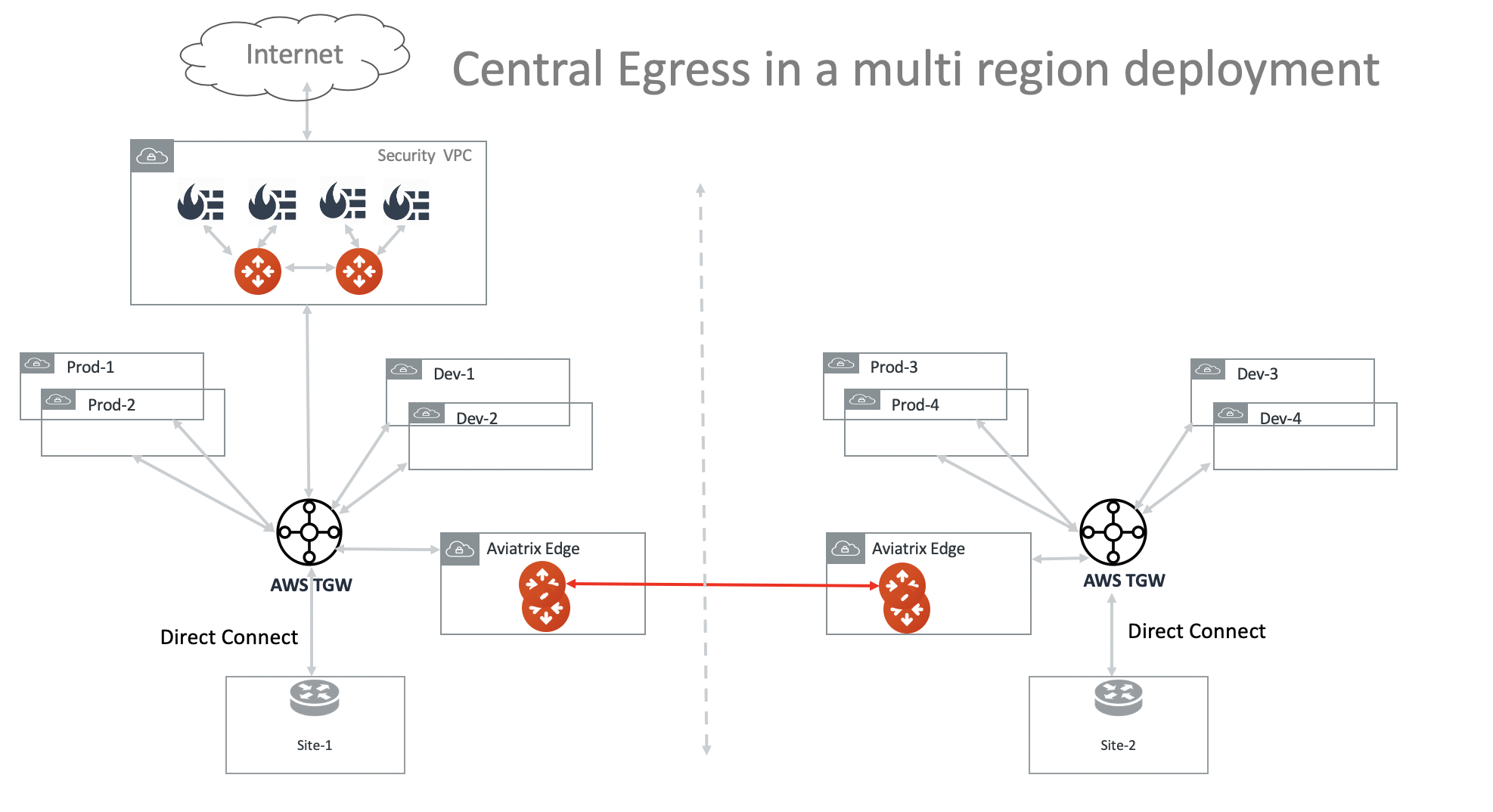
Planning Your Centralized Egress Deployment
Launching & Associating Aviatrix FQDN Gateway
If you perform one of the previous two steps, then you must be using a third party firewall instance. Skip this step.
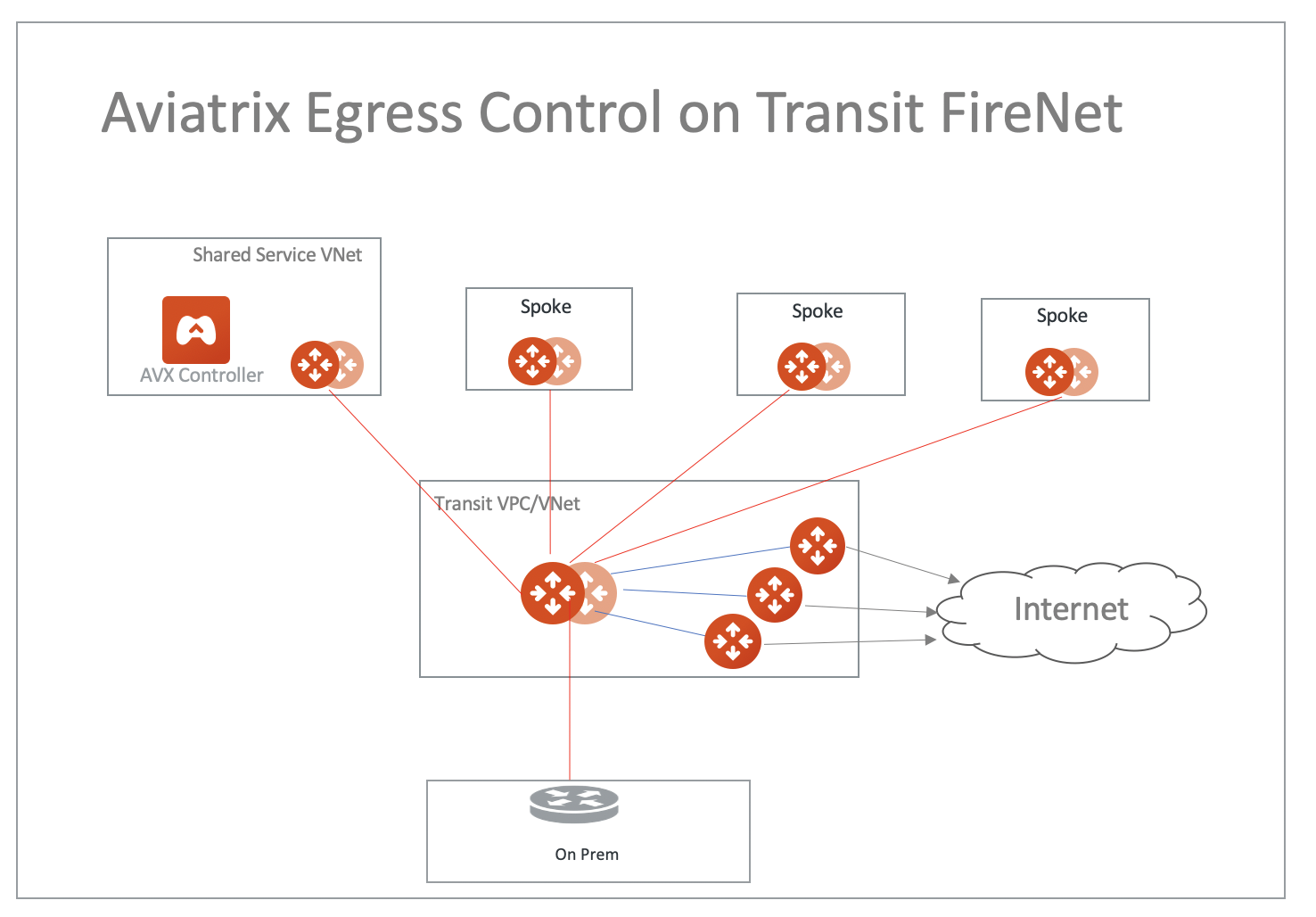
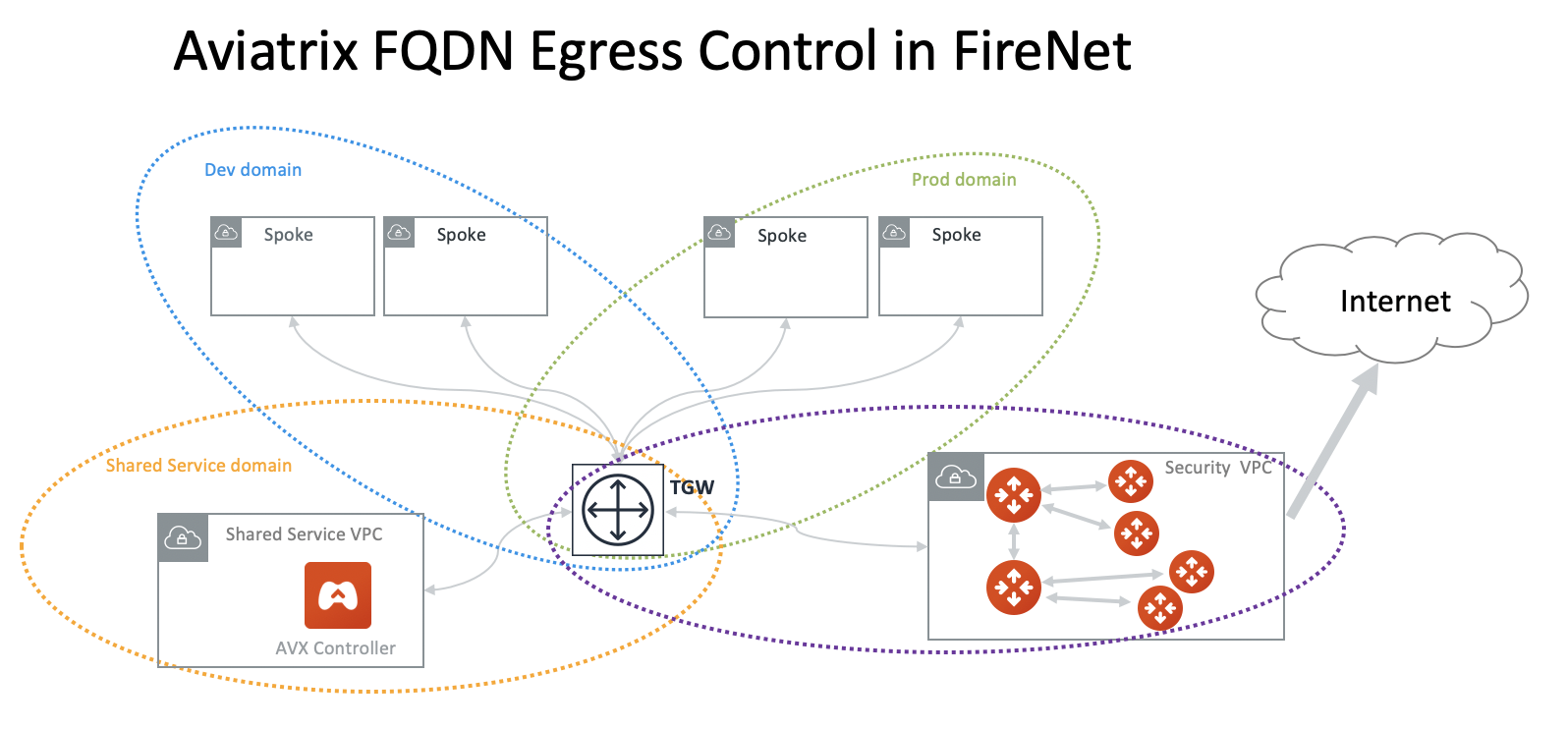
This option is to deploy an Aviatrix FQDN gateway in a FireNet environment for a centralized scale out egress whitelist solution, as shown below.
|
If a deployed Aviatrix FQDN gateway has no FQDN whitelist attached to it, the FQDN gateway acts as a NAT gateway and it will pass all traffic to all destination sites. To add whitelist policies, follow how to configure FQDN instructions. |
This option is available in AWS and Azure. It applies to Multicloud Transit, Azure native Spoke transit, and TGW based transit.
| Setting | Value |
|---|---|
VPC ID |
The Security VPC/VNet. |
Gateway Name |
The primary FireNet Gateway. |
FQDN Gateway Subnet |
The public subnet on which Aviatrix FQDN gateway will be launched. |
FQDN Gateway Size |
The Aviatrix FQDN gateway instance size, starting from t2.micro. |
FQDN Gateway Name |
The Aviatrix FQDN gateway name. Note you cannot change the name once the gateway instance is launched. |
Attach |
Attach this FQDN gateway to the primary FireNet Gateway. |