Transit FireNet Workflow for OCI
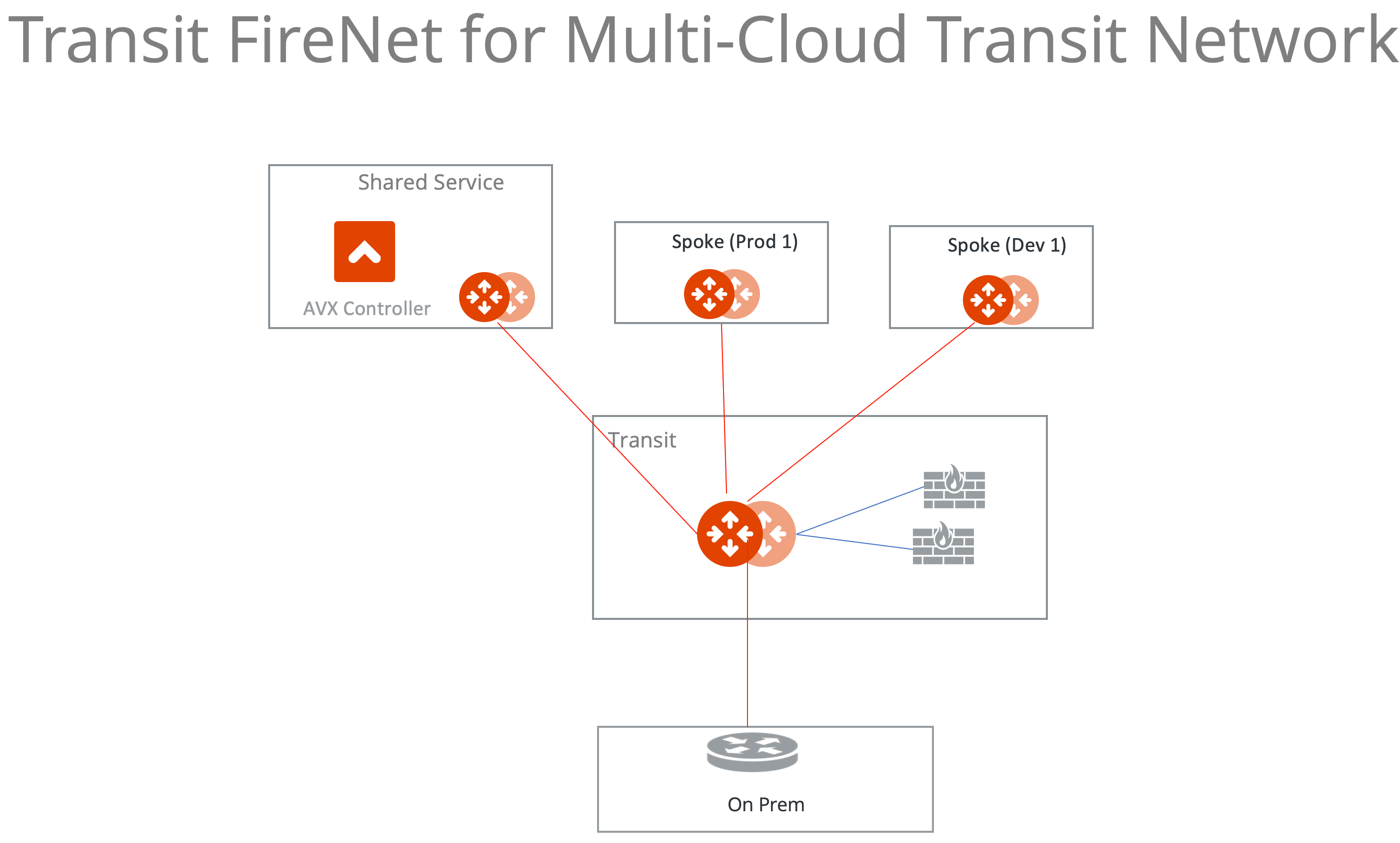
Aviatrix Transit FireNet allows you to deploy firewalls functions for the Aviatrix Multi-Cloud Transit architecture. With Transit FireNet feature, the Firewall Network (FireNet) function is integrated into the Aviatrix Transit gateway.
In this example, three VCNs with Aviatrix gateways will be deployed, one Aviatrix transit gateway and two Spoke Gateways (DEV and PROD) will be attached to it.
The transit VCN will have a firewall of supported vendors (Check Point, Palo Alto Networks and Fortinet etc.) deployed in it. Please see the diagram below for more details.
Once the infra is in-place then the policy will be created to inspect the east-west and north-south traffic.
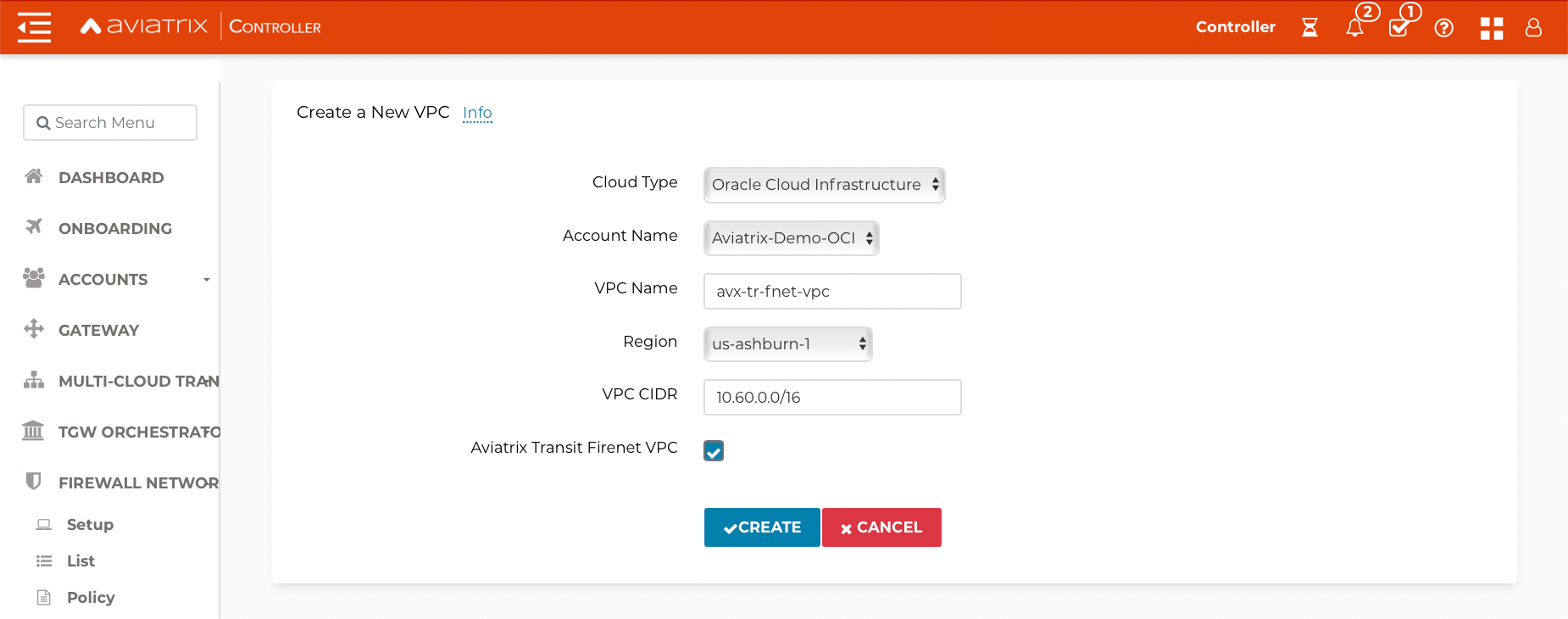
Create Transit VCN
VCNs can be created manually on OCI or directly from Aviatrix Controller.
-
Login to the Aviatrix Controller with username and password
-
Navigate to Useful Tools > Create A VPC.
-
Add one VCN for Transit FireNet Gateway and select Aviatrix FireNet VPC option as shown below.
-
Create two more VCNs with no option/checkbox selected for Spoke Gateways.
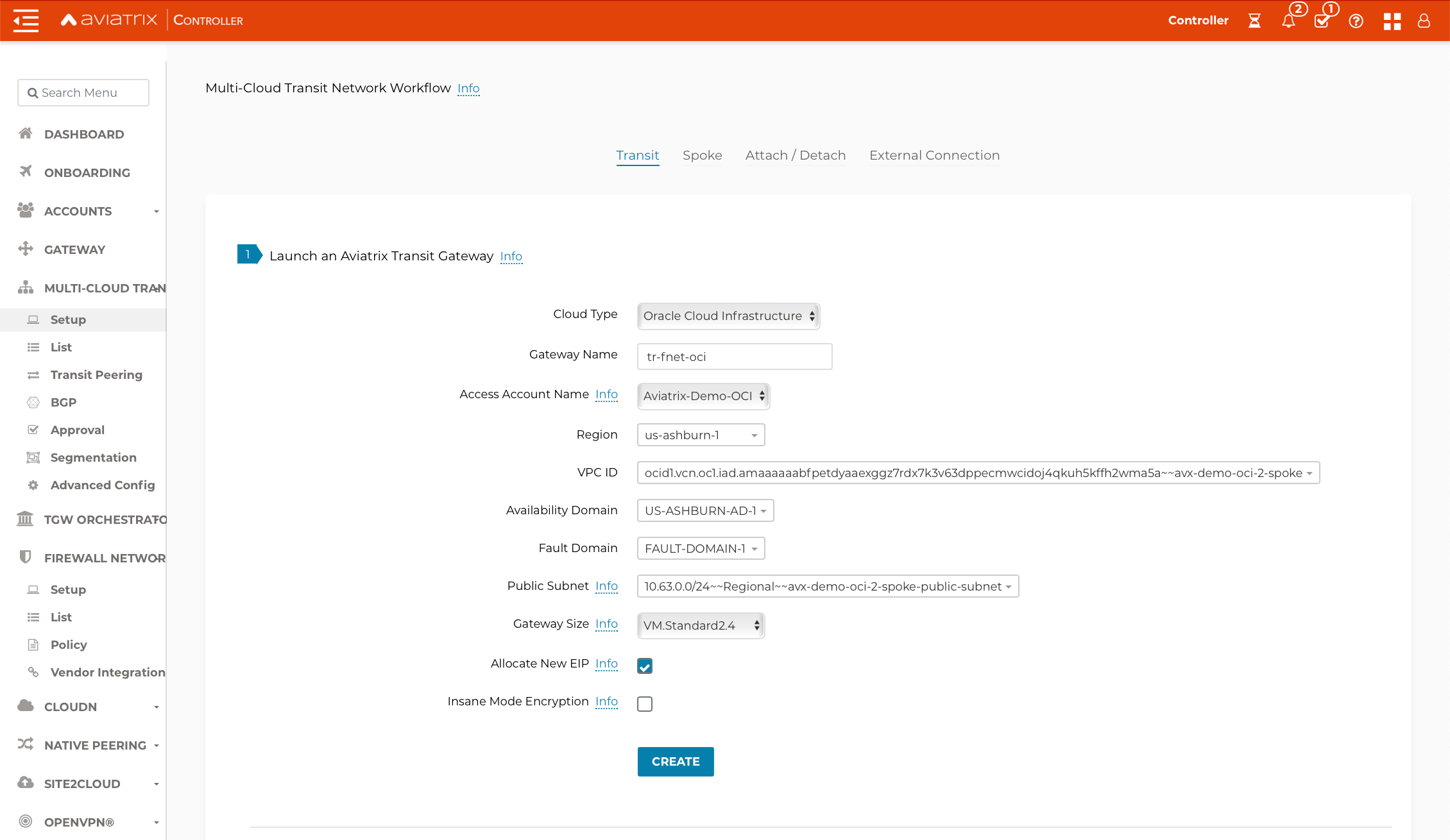
Deploy the Transit Aviatrix Gateway
Transit Aviatrix Gateway can be deployed using the Transit Gateway Workflow.
Prerequisite for OCI
Transit FireNet builds on the Aviatrix Transit Network solution where Aviatrix gateways are deployed in Transit VCN and/or in Spoke VCN in OCI.
Make sure the deployment meets the following specifications:
-
ActiveMesh 2.0 is required. To migrate to ActiveMesh 2.0, see Migrating from Classic Aviatrix Encrypted Transit Network to Aviatrix ActiveMesh Transit Network.
-
Select the option Enable Transit FireNet when launching the Aviatrix Transit Gateway.
-
Aviatrix Transit Gateway minimum instance size should be VM.Standard2.4 or more
|
Transit FireNet High Performance mode is not supported in Release 6.4. |
Procedure
-
Navigate to Multi-Cloud Transit > Setup > #1 Launch an Aviatrix Transit Gateway.
-
Select the OCI Cloud Type.
-
Choose virtual machine size VM.Standard2.4.
-
Enable High Performance Mode for higher throughput (optional).
-
Enable Transit Gateway HA by navigating to Multi-Cloud Transit > Setup > #2 (Optional) Enable HA to an Aviatrix Transit Gateway.
ActiveMesh is enabled by default.
Please see an example below for Transit FireNet GW:
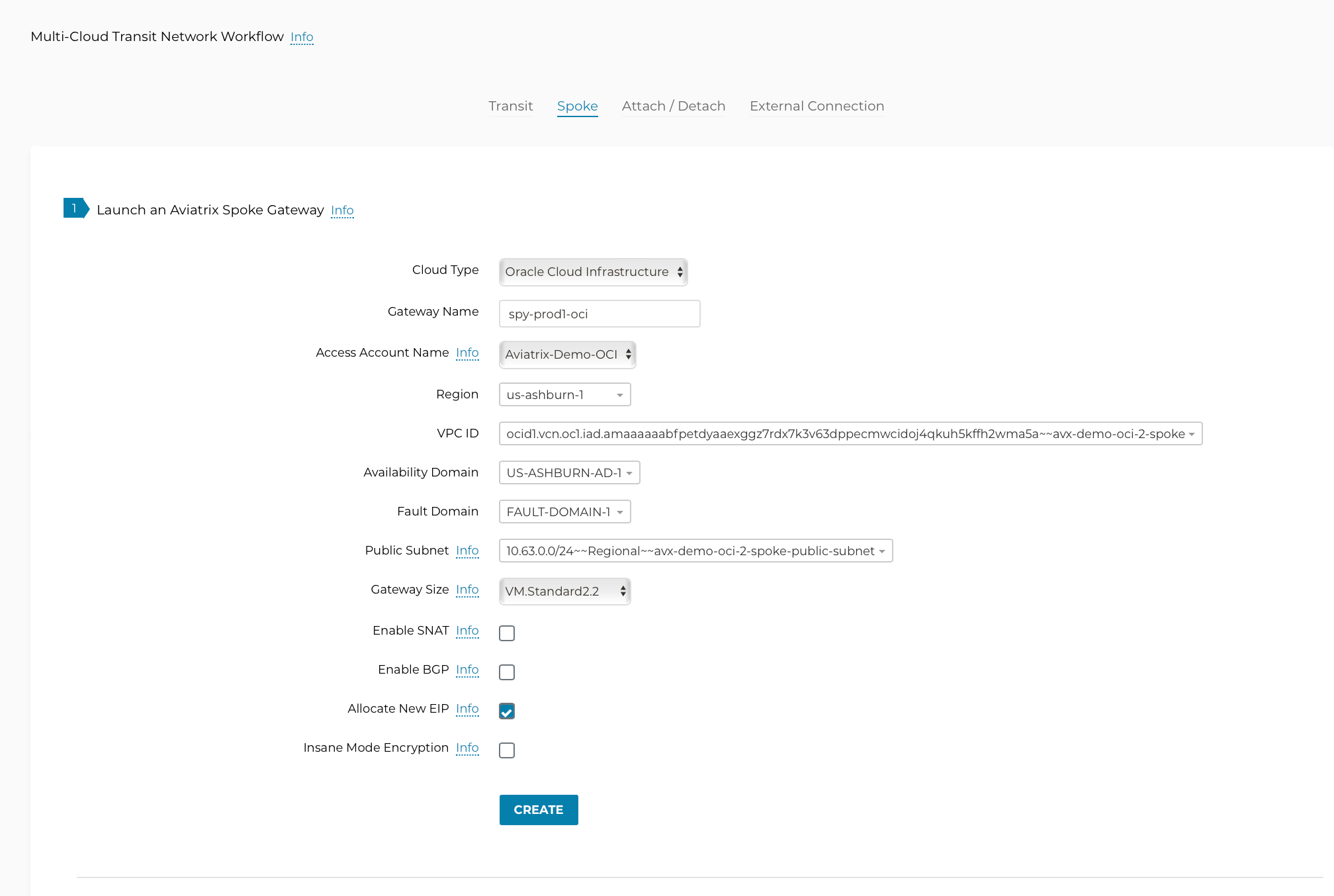
Deploy Spoke Gateways
Now that we have Aviatrix Transit Gateway, we can deploy Aviatrix Spoke Gateways in the spoke VCN using Aviatrix Spoke Gateway Workflow.
-
Navigate to Multi-Cloud Transit > Setup > Spoke > #1 Launch an Aviatrix Spoke Gateway.
-
Deploy a Spoke Gateway (GW) in each of the spoke VCNs using the correct Account and VCN information.
-
Choose the Public Subnet.
-
Enable Spoke Gateway HA on the same tab.
Attach Spoke Gateways to Transit Network
Now that Transit and Spoke gateways are deployed, you must connect them.
-
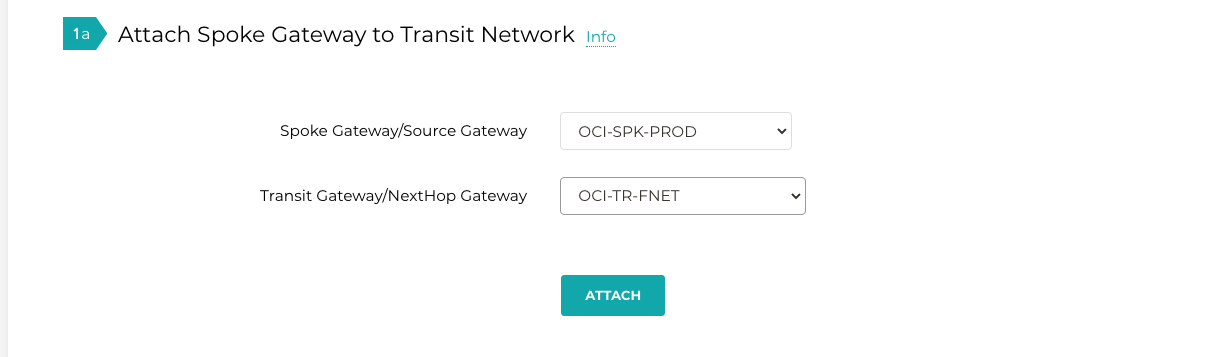
Navigate to Multi-Cloud Transit > Setup > Attach/Detach #1a Attach Spoke Gateway to Transit Network.
-
Select one spoke at a time and attach to the Transit Gateway.
|
By default, a Transit Gateway will not route traffic between Spoke Gateways. |
Enable Connected Transit
By default, Spoke VCNs are in isolated mode where the Transit will not route traffic between them. To allow the Spoke VCNs to communicate with each other, we need to enable Connected Transit.
-
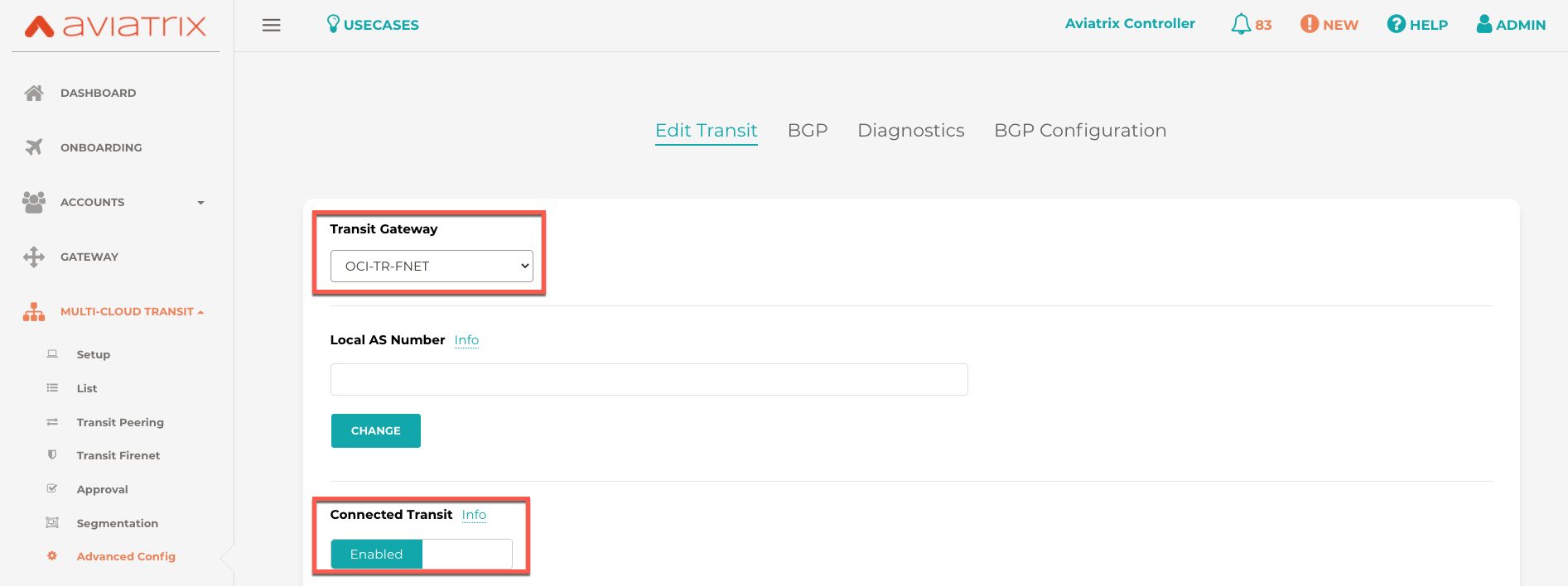
Navigate to Multi-Cloud Transit > Advanced Config > Edit Transit.
-
Select the correct Transit Gateway at the top of the page and slide Connected Transit to Enabled.
Configure Transit Firewall Network
Now that Transit and Spoke Gateways have now been deployed, you deploy and enable the Firewall for traffic inspection.
Let’s start with enabling the firewall function and configuring the FireNet policy.
-
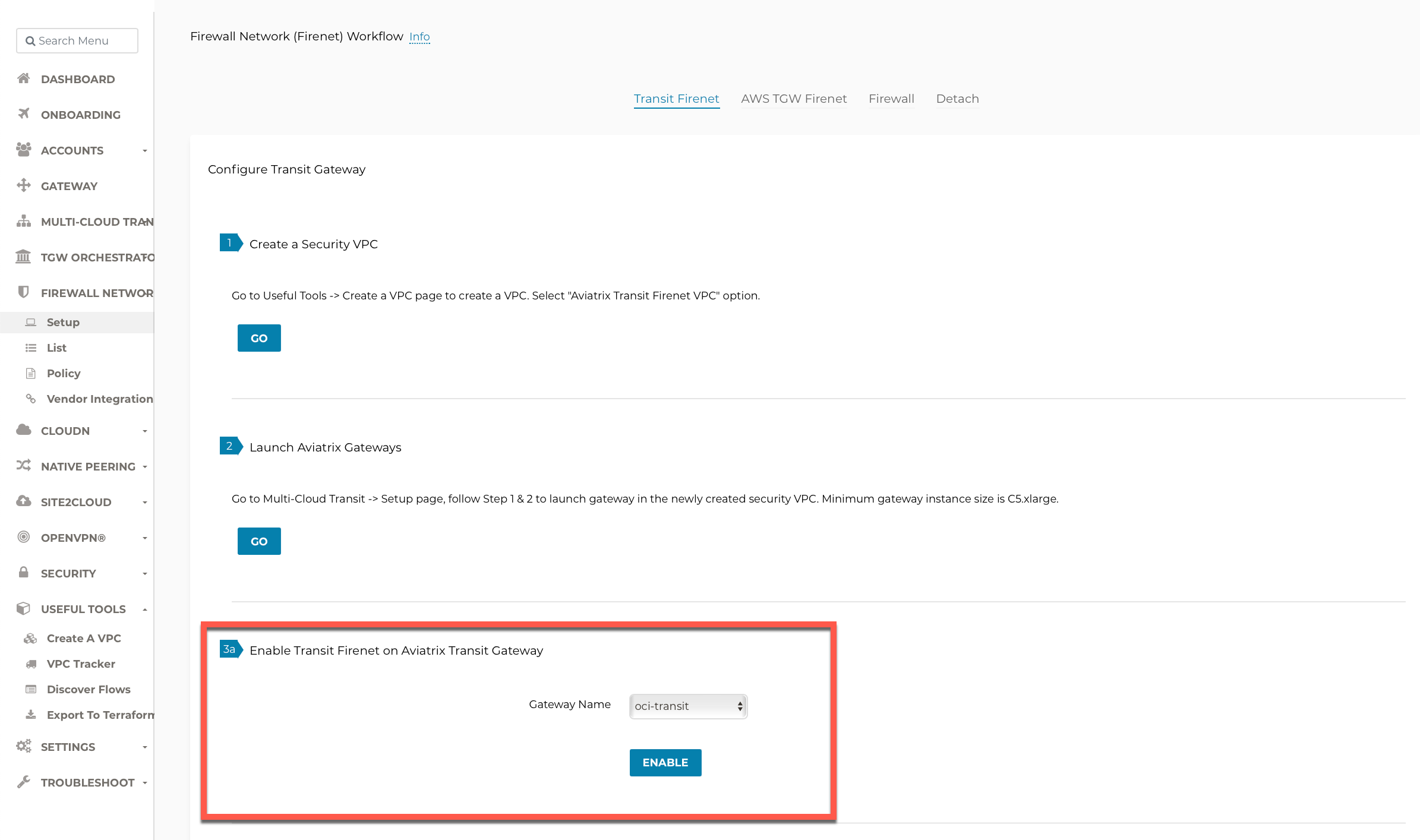
Navigate to Firewall Network > Setup > Transit FireNet > #3a Enable Transit FireNet on Aviatrix Transit Gateway.
-
Choose the Aviatrix Transit Gateway and Click Enable.
-
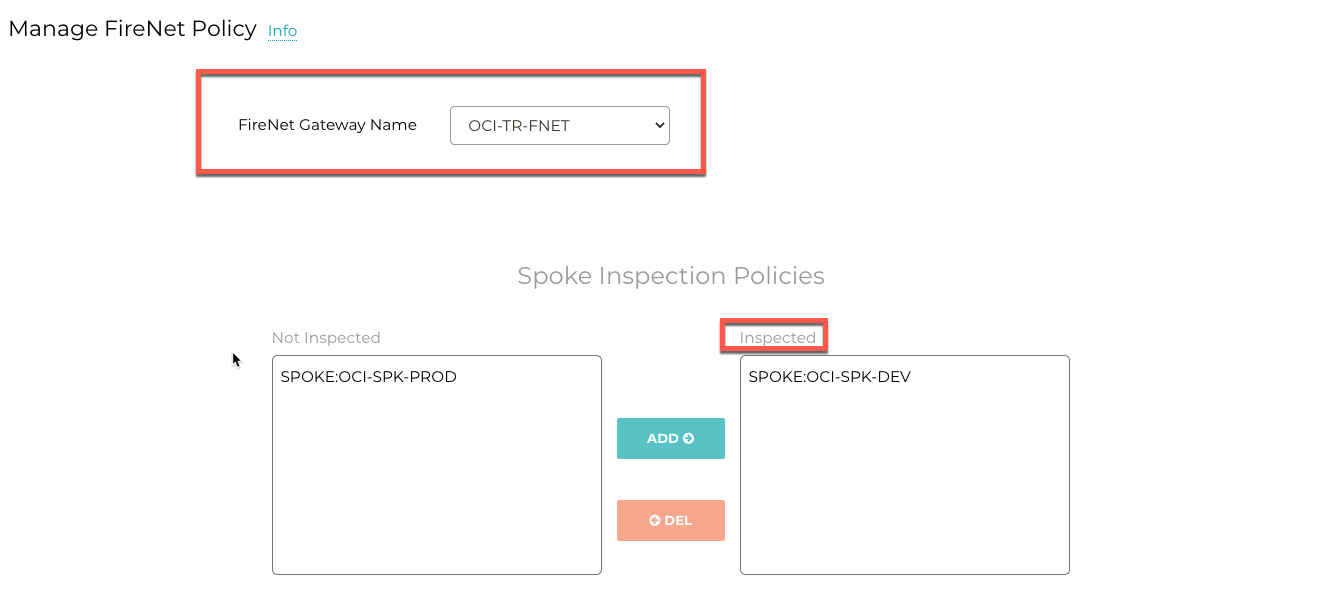
Navigate to Firewall Network > Policy.
-
Add spokes to the Inspected box for traffic inspection
|
By default, FireNet inspects ingress (INET to VCN) and east-west traffic (VCN to VCN) only. |
Launch and Associate Firewall Instance
This approach is recommended if this is the first Firewall instance to be attached to the gateway.
This step launches a Firewall instance and associates it with one of the FireNet gateways.
|
The Firewall instance and the associated Aviatrix FireNet gateway above must be in the same AZ, and, we recommend that the Management Interface Subnet and Egress (untrust dataplane) Interface Subnet should not be in the same subnet. |
Launch and Attach
-
Go to Aviatrix Controller’s console and navigate to Firewall Network > Setup > Firewall.
-
Provide all the required input as shown in the table and click Launch .
|
The vendor’s firewall may take some time after launch to be available. |
| Setting | Value |
|---|---|
VPC ID |
The Security VNET created in Step 1. |
Gateway Name |
The primary FireNet gateway. |
Firewall Instance Name |
The name that will be displayed on Azure Console. |
Firewall Image |
The OCI Image that you have subscribed. |
Firewall Image Version |
Firewall supported software versions. |
Firewall Instance Size |
Firewall virtual machine size. |
Management Interface Subnet. |
Select the subnet whose name contains "gateway and firewall management" |
Egress Interface Subnet |
Select the subnet whose name contains "FW-ingress-egress". |
Username |
Applicable to Azure deployment only. "admin" as a username is not accepted. |
Authentication Method |
SSH Public Key |
Key Pair Name (Optional) |
The .pem file name for SSH access to the firewall instance. |
Attach (Optional) |
By selecting this option, the firewall instance is inserted in the data path to receive packet. If this is the second firewall instance for the same gateway and you have an operational FireNet deployment, you should not select this option as the firewall is not configured yet. You can attach the firewall instance later at Firewall Network → Advanced page. |
Advanced (Optional) |
Click this selection to allow Palo Alto firewall bootstrap files to be specified. |
Palo Alto VM-Series Specifications
Palo instance has three interfaces as described below.
| Palo Alto VM interfaces | Description | Inbound Security Group Rule |
|---|---|---|
eth0 (on subnet -Public-gateway-and-firewall-mgmt) |
Management interface |
Allow SSH, HTTPS, ICMP, TCP 3978 |
eth1 (on subnet -Public-FW-ingress-egress) |
Egress or Untrusted interface |
Allow ALL |
eth2 (on subnet -dmz-firewall) |
LAN or Trusted interface |
Allow ALL (Do not change) |
Note that firewall instance eth2 is on the same subnet as FireNet gateway eth2 interface.
Launch VM Series from Aviatrix Controller automatically set it up the Palo Alto Network VM-Series firewall. User should be able to login to the VM-Series console with given username and password during launch.
|
For Panorama managed firewalls, you need to prepare Panorama first and then launch a firewall. When a VM-Series instance is launched and connected with Panorama, you need to apply a one time "commit and push" from the Panorama console to sync the firewall instance and Panorama. |
|
If VM-Series are individually managed and integrated with the Controller, you can still use Bootstrap to save initial configuration time. Export the first firewall’s configuration to bootstrap.xml, create an IAM role and Bootstrap bucket structure as indicated above, then launch additional firewalls with IAM role and the S3 bucket name to save the time of the firewall manual initial configuration. |
Associate an Existing Firewall Instance
This step is the alternative step to Launch and Attach. If you already launched the firewall (Check Point, Palo Alto Network or Fortinet) instance from Azure Console, you can still associate it with the FireNet gateway.
In the Aviatrix Controller navigate to Firewall Network > Setup → Firewall and associate a firewall with the correct FireNet Gateway.
Configure Firewall Interfaces
Palo Alto VM-Series
Follow Configure PaloAlto VM-Series Example in OCI to properly configure PAN VM-Series.
Step 9: Vendor Firewall Integration
Vendor integration dynamically updates firewall route tables. The use case is for networks with RFC 1918 and non-RFC 1918 routes that require specific route table programming on the firewall appliance
-
Go to Firewall Network > Vendor Integration > Select Firewall, fill in the details of your Firewall instance.
-
Click Save, Show and Sync.
Step 10: Enable Health Check Policy in Firewall
Aviatrix Controller uses ICMP or ping to check the health of firewall every 5 seconds. User needs to enable this port in firewall as per given instruction.
Palo Alto Network (PAN)
By default, VM-Series do not allow ICMP or ping. Pleas follow the given steps to enable it:
-
Login to VM-Series with username and password.
-
Go to Network → Interface Mgmt under Network Profiles and click "Add".
-
Give any name in "Interface Management Profile", check ping checkbox under Administrative Management Service and click "OK".
-
Attach Profile with LAN interface. Network → Interfaces → Select LAN Ethernet Interface → Advanced → Management Profile → Select appropriate profile.
Step 11: Example Setup for "Allow All" Policy
After a firewall instance is launched, wait for 5 to 15 minutes for it to come up. Time varies for each firewall vendor. In addition, please follow example configuration guides as below to build a simple policy on the firewall instance for a test validation that traffic is indeed being routed to firewall instance.
Palo Alto Network (PAN)
For basic configuration, Follow PaloAlto VM-Series Example Step 8 to add the Allow-all policy.
Step 12: Verification
There are multiple ways to verify if Transit FireNet is configured properly:
-
Aviatrix Flightpath - Control-plane Test
-
Ping/Traceroute Test between Spoke VCNs (East-West) - Data-plane Test
Flight Path Test for FireNet Control-Plane Verification
Flight Path is a very powerful troubleshooting Aviatrix tool which allows users to validate the control-plane and gives visibility of end to end packet flow.
-
Navigate to Troubleshoot→ Flight Path
-
Provide the Source and Destination Region and VCN information
-
Select ICMP and Private subnet, and Run the test
|
VM instance will be required in OCI, and ICMP should be allowed in security group. |
Ping/Traceroute Test for FireNet Data-Plane Verification
Once control-plane is established and no problem found in security and routing polices. Data-plane validation needs to be verified to make sure traffic is flowing and not blocking anywhere.
- There are multiple ways to check data-plane
-
[arabic]
-
One way is to SSH to Spoke instance (e.g. DEV1-VM) and ping other Spoke instance (e.g PROD1-VM) to make sure no traffic loss in the path.
-
Ping/traceroute capture can also be performed from Aviatrix Controller. Go to TROUBLESHOOT → Diagnostics and perform the test.
-