Aviatrix Transit Gateway to External Devices
This document describes the worklow to connect Aviatrix Transit Gateway to an external device.
For an overview of external device connection options to the Aviatrix Transit Gateway, see Connecting Aviatrix Transit Gateway to External Devices.
Workflow
-
Launch a Transit Gateway
If you have not launched an Aviatrix Transit Gateway, then follow the instructions for launching an Aviatrix Transit Gateway in the Multicloud Transit Network Workflow.
-
External device connection settings
Provide the following information to set up external device connection (Multi Cloud Transit > Setup > External Connection) and click OK. For ActiveMesh design notes, see ActiveMesh Design Notes.
Setting Value External Device
Select this option to build a connection to a remote site.
BGP
Select BGP if the Transit GW runs dynamic routing with remote site.
Static Remote Route-Based
Select this option if the remote site supports route-based VPN with static configuration.
Static Remote Policy-Based
Select this option the remote site supports policy-based VPN with static configuration. The caveat in this mode is the remote site must always initiate the traffic. This function has been moved to Site2Cloud.
IPsec
Select this option to run BGP and build a IPsec connection to a remote site.
Remote Subnet(s) (Static Remote Route-based only)
Remote subnet for remote route-based IPsec tunnel connection.
GRE
Select this option to run BGP and build a GRE connection to a remote site.
LAN
Select this option to run BGP and data plane by LAN interface with an instance in the same VPC or VNet.
VPC Name/Site ID
The Transit VPC/VNet ID where Transit GW was launched.
Connection Name
A unique name to identify the connection to external device.
Aviatrix Transit GW BGP ASN
The BGP AS number the Transit GW will use to exchange routes with external device.
Primary Aviatrix Gateway
The Transit GW you created in Step 1.
Algorithms
Optional parameters. Leave it unselected if you don’t know.
AWS VGW Account Name (AWS VGW only)
The name of the AWS VGW account.
IKEv2
Select the option to connect to the remote site using IKEv2 protocol.
Enable Remote Gateway HA
Select this if there are two external devices. If selected, you also need to enter the following backup information: Remote BGP AS Number, Remote Gateway IP, Pre-shared key, Local Tunnel IP, Remote Tunnel IP.
Over Private Network
Select this option if your underlying infrastructure is private network, such as AWS Direct Connect and Azure ExpressRoute. See the "How does it work" section for more details. When this option is selected, BGP and IPsec run over private IP addresses.
Remote BGP AS Number
When BGP is selected, the BGP AS number the external device will use to exchange routes Aviatrix Transit GW.
Remote Gateway IP
IP address of the remote device. If "Over DirectConnect" is selected, enter the private IP address of the external device.
Pre-shared Key
Optional parameter. Leave it blank to let the pre-shared key to be auto generated.
Local Tunnel IP
Optional parameter. This field is for the tunnel inside IP address of the Transit Gateway. Leave it blank.
Remote Tunnel IP
Optional parameter. This field is for the tunnel inside IP address of the external device. Leave it blank.
Over DirectConnect (Backup)
Select this option if HA is enabled.
Remote BGP AS Number (Backup)
When BGP is selected, the remote ASN for backup should be the same as the primary remote ASN.
Remote Gateway IP (Backup)
IP address of the remote device. If "Over Private Network" is selected, enter the private IP address of the external device.
Pre-shared Key (Backup)
Optional parameter. Leave it blank to let the pre-shared key to be auto generated.
Local Tunnel IP (Backup)
Optional parameter. This field is for the tunnel inside IP address of the Transit Gateway. Leave it blank.
Remote Tunnel IP (Backup)
Optional parameter. This field is for the tunnel inside IP address of the external device. Leave it blank.
VGW Region (AWS VGW only)
The AWS region where VGW is created.
VGW ID (AWS VGW only)
VGW that is created in the VGW region in the AWS VGW account.
VNG Name (Azure VNG only)
Select the VNG Name (only displays if a Primary Aviatrix Gateway is selected).
-
Download the configuration
After the configuration is done, a connection is created. Download the configuration file.
-
Go to Site2Cloud on the left sidebar.
-
Select the connection you created with Connection Name.
-
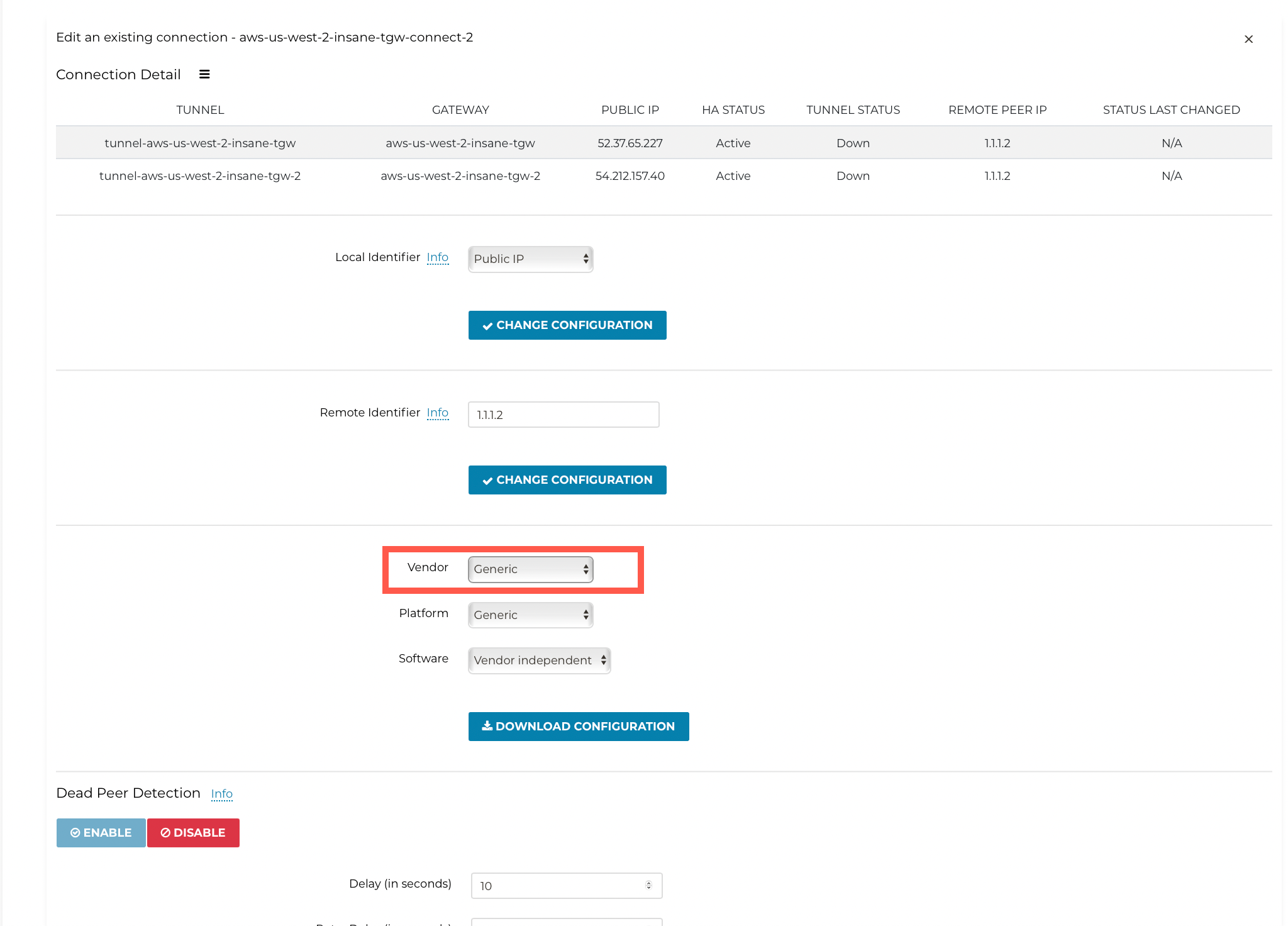
Select the Generic for Vendor type.
-
Click Download Configuration.
-
-
Configure the External Device
Use the information provided in the configuration file to configure the on-prem device with IPsec tunnel and BGP.
See:
Disconnecting the External Device
To disconnect the external device:
-
Go to MULTI-CLOUD TRANSIT > Setup > External Connection tab.
-
Scroll down to Disconnect AWS VGW / External Device / Azure VNG section.
-
Select the Transit Gateway in the dropdown menu, and click Detach.
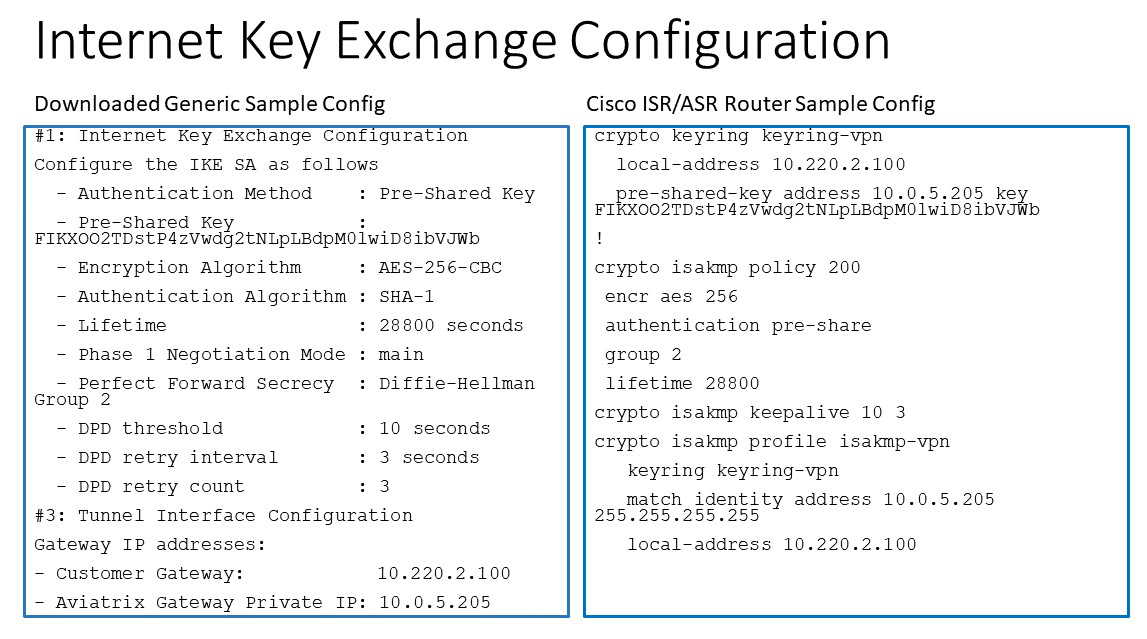
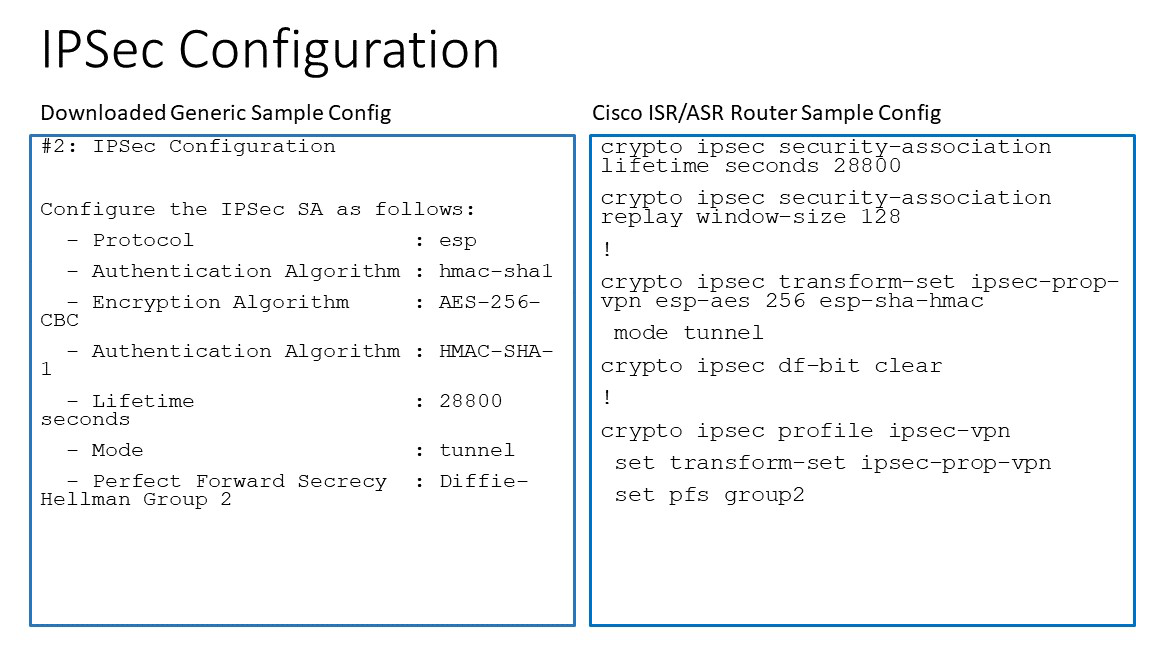
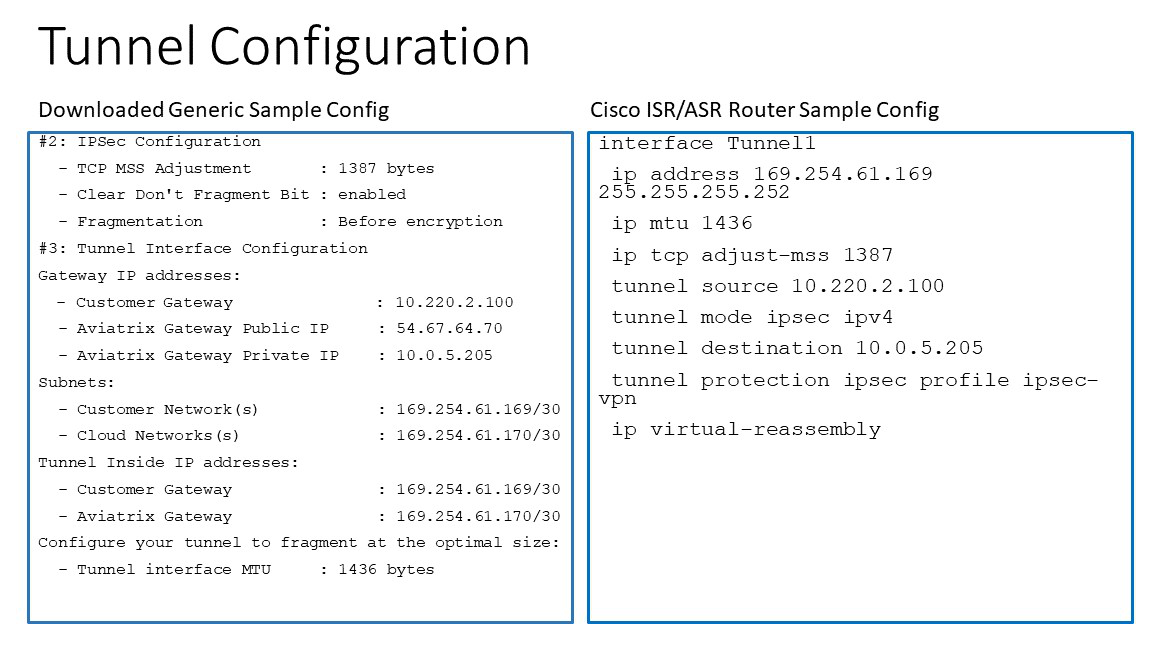
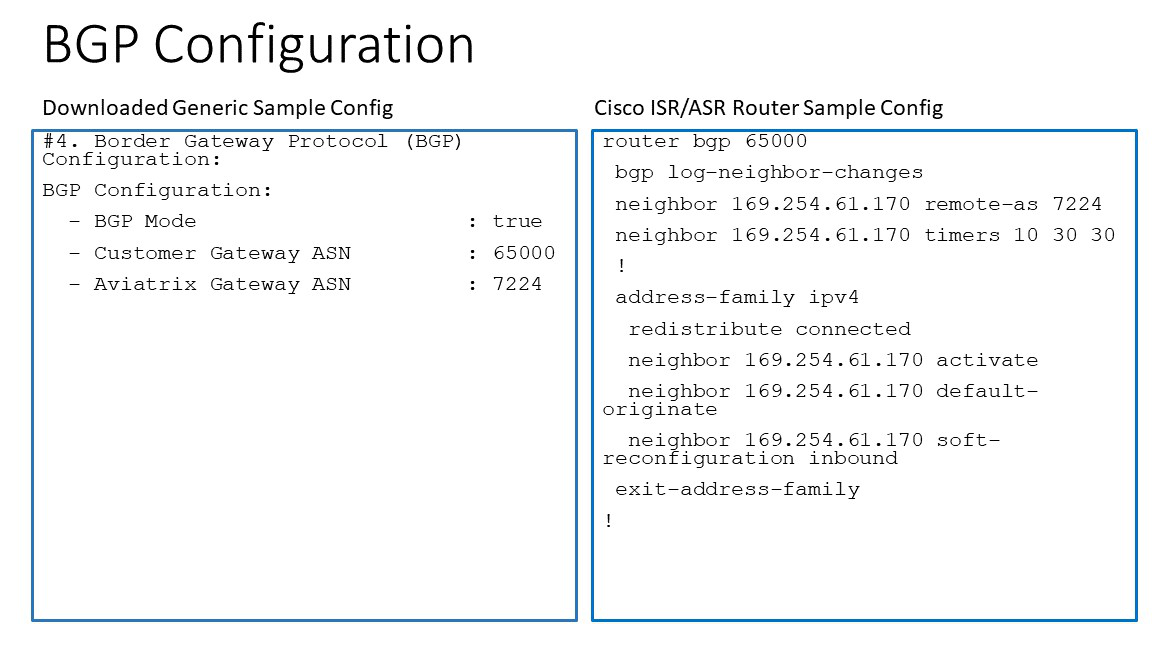
Appendix 1: Transit Connection to Cisco ISR/ASR Over the Internet
The following is the topology used for the sample configuration below:
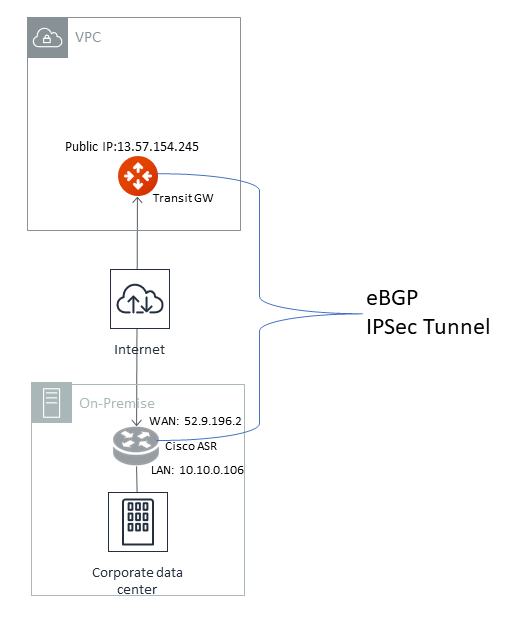
Since over Internet, an Aviatrix Transit Gateway and Cisco ISR/ASR use each other’s public IP to create an IPsec tunnel and establish a BGP connection.
The following diagrams display mappings between a sample configuration from Step 2 above and its corresponding Cisco ISR/ASR router configuration:
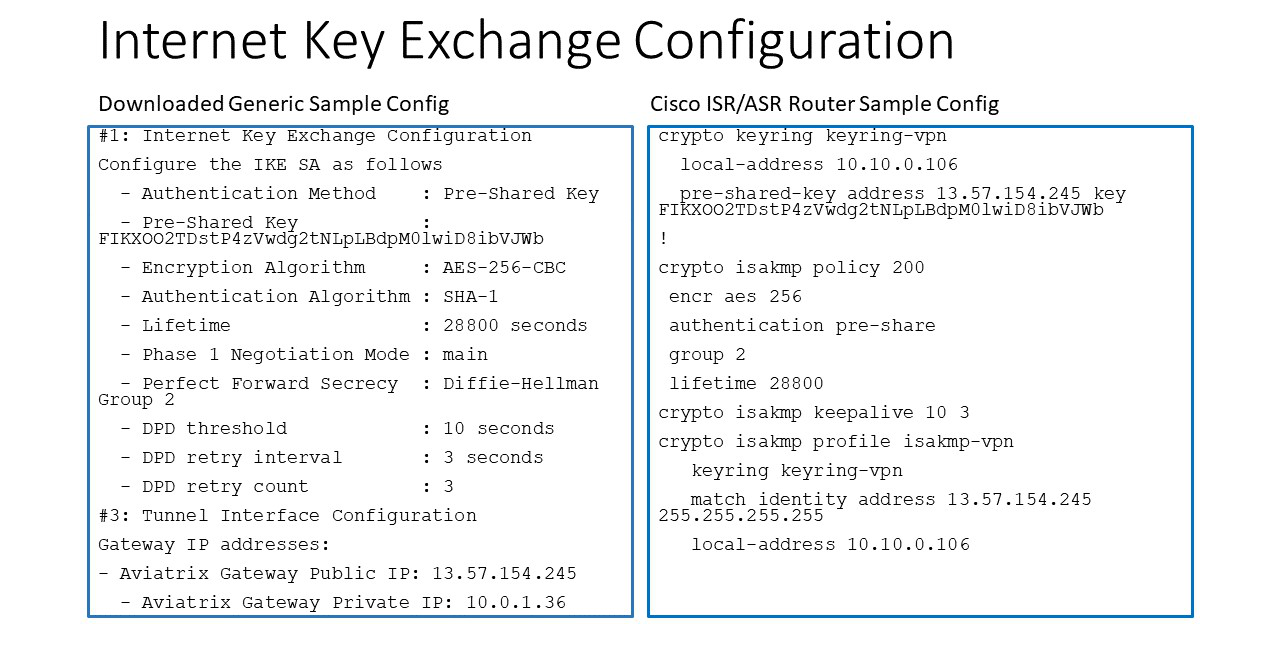
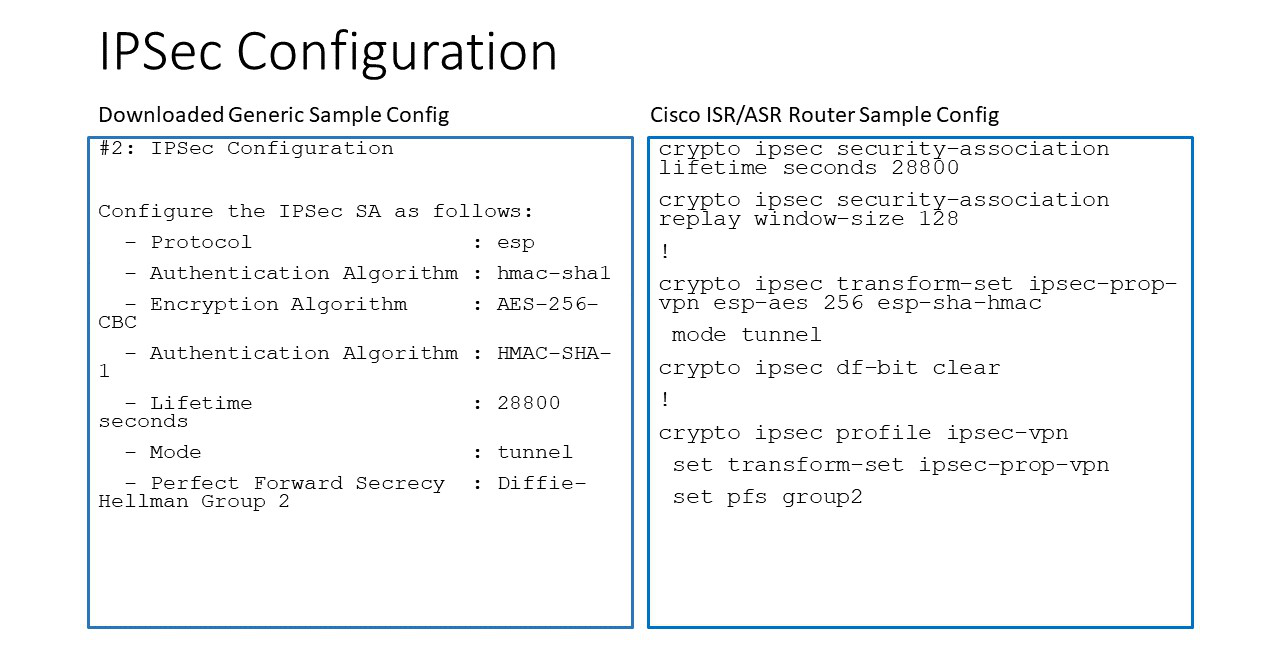
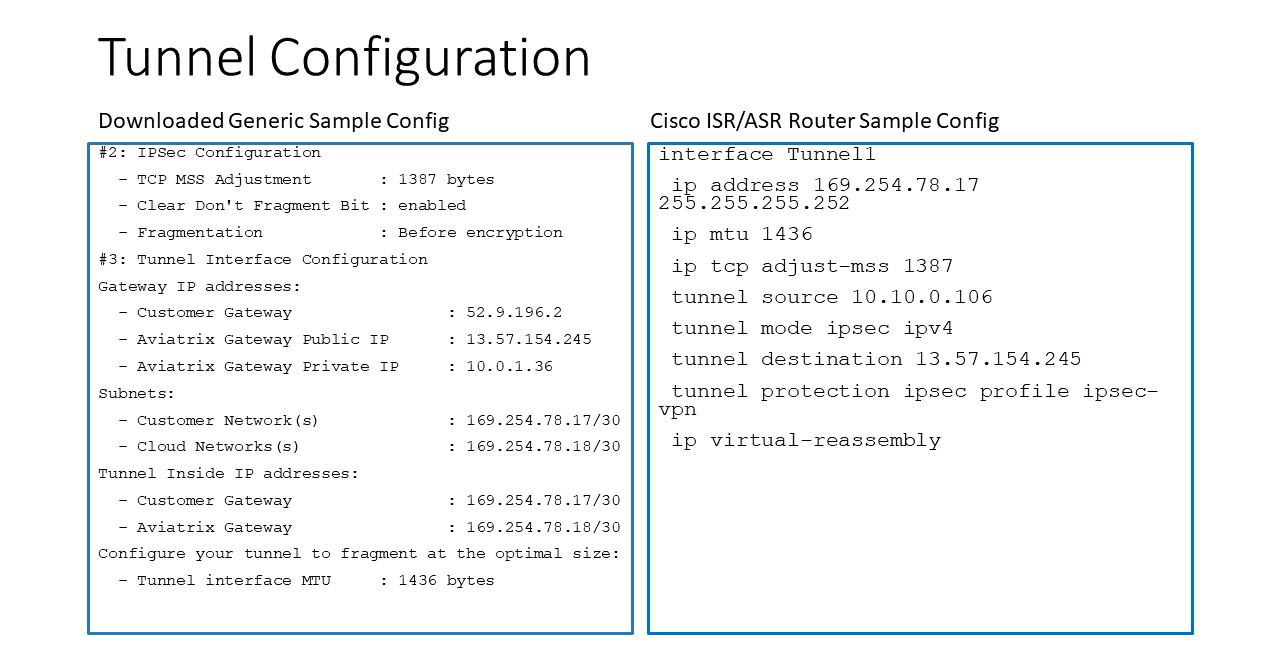
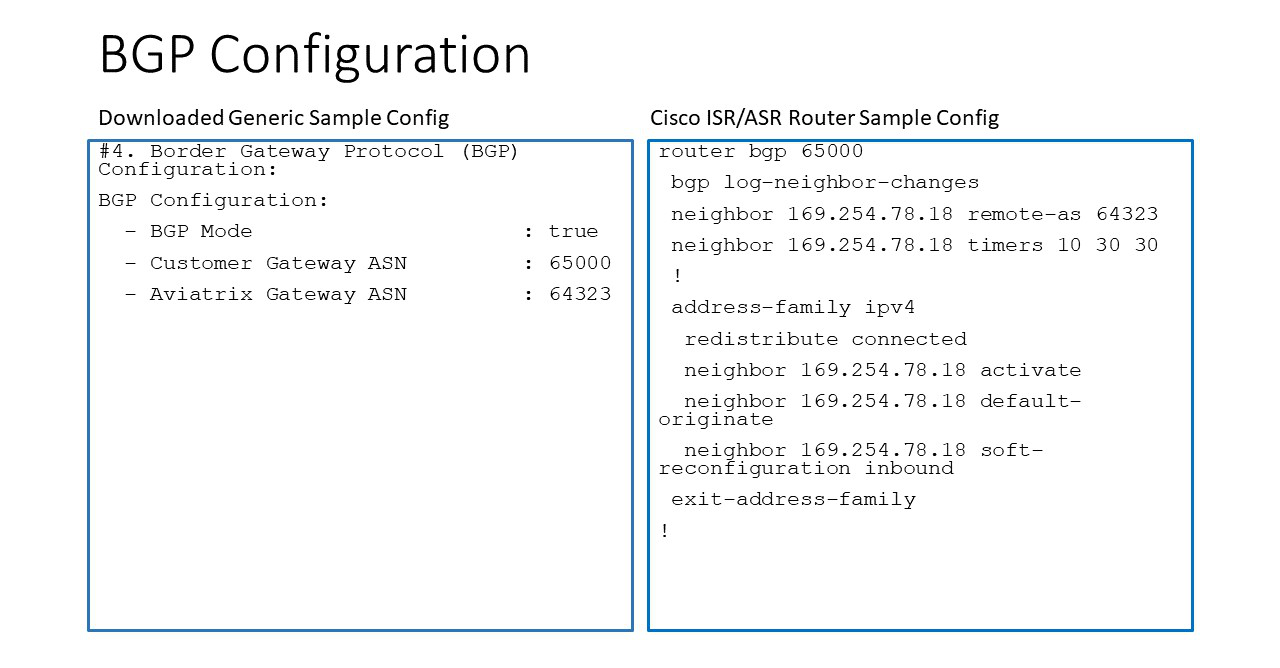
Appendix 2: Transit Connection to Cisco ISR/ASR over Direct Connect
The following is the topology used for the sample configuration below:
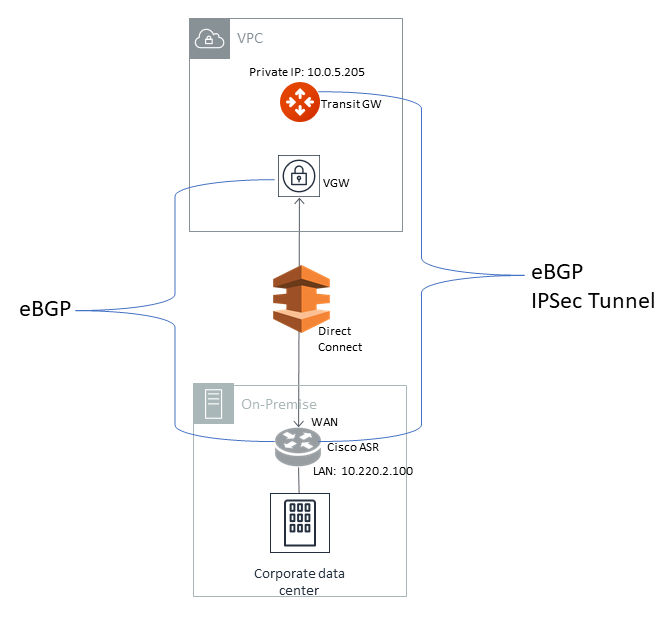
Since over Direct Connect, the Aviatrix Transit Gateway and Cisco ISR/ASR use each other’s private IP to create an IPsec tunnel and establish BGP connection.
|
The ASN number of the Aviatrix Transit GW entered at BGP Local AS Number of Step 1 above should be the same as VGW’s ASN number (7224 in this example). Without it, the Transit VPC/VNet CIDR advertised from VGW to on-prem ASR/ISR will be advertised by ASR/ISR back to the Aviatrix Transit GW. With the same ASN number, Aviatrix Transit GW will drop the route to Transit VPC/VNet CIDR. |
The following diagrams display mappings between a sample configuration from Step 2 above and its corresponding Cisco ISR/ASR router configuration: