Azure Transit Network Design Patterns
There are many design patterns for networking and networking security deployment in the cloud. This document summarizes these design patterns that apply to Azure networks.
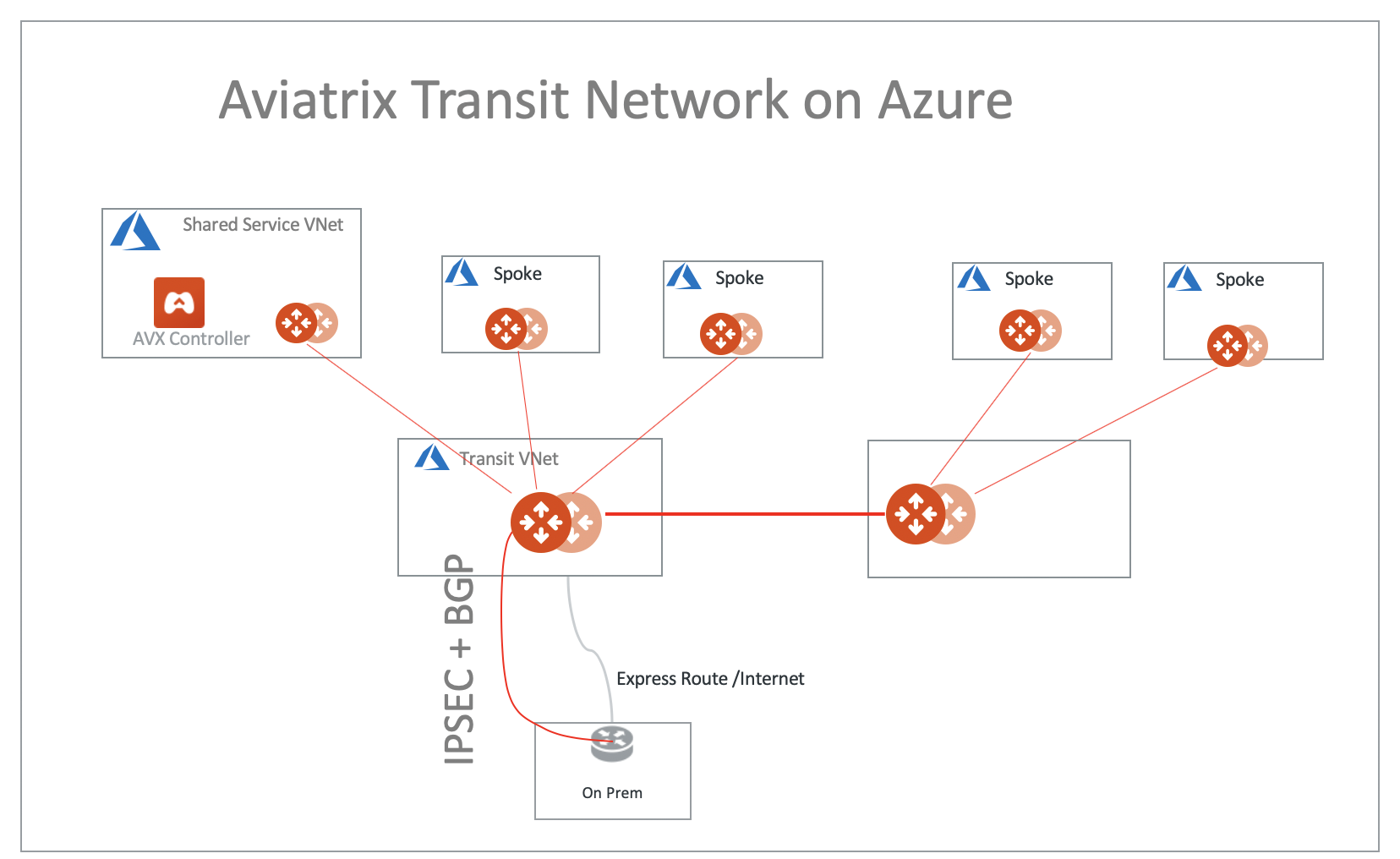
Aviatrix Encrypted Transit Network
In this design, all packets in flight between Spoke VNets and Transit to on-prem are encrypted.
|
Aviatrix Transit supports high performance (High Performance Encryption Mode) IPsec performance over ExpressRoute and Azure Peering. |
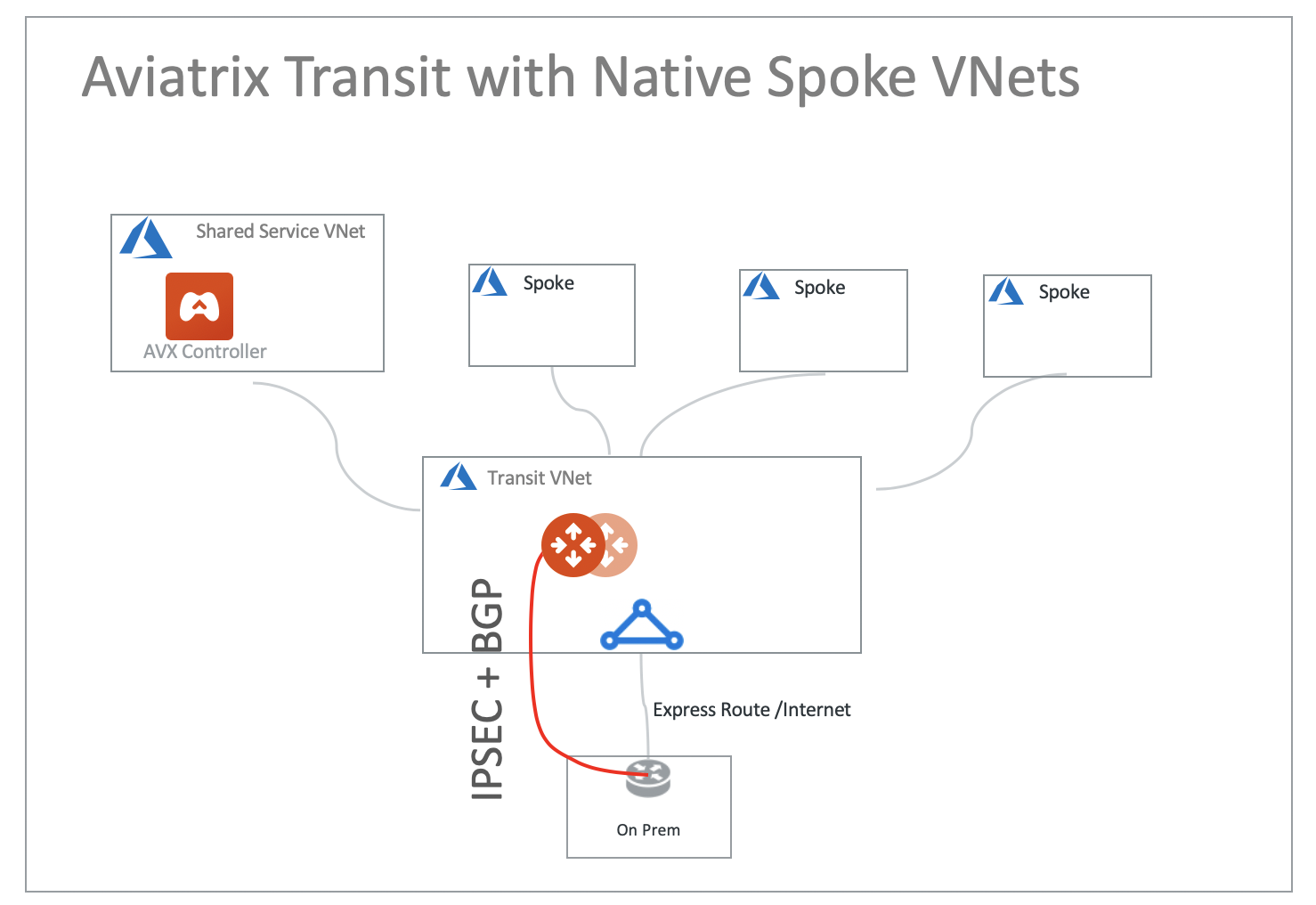
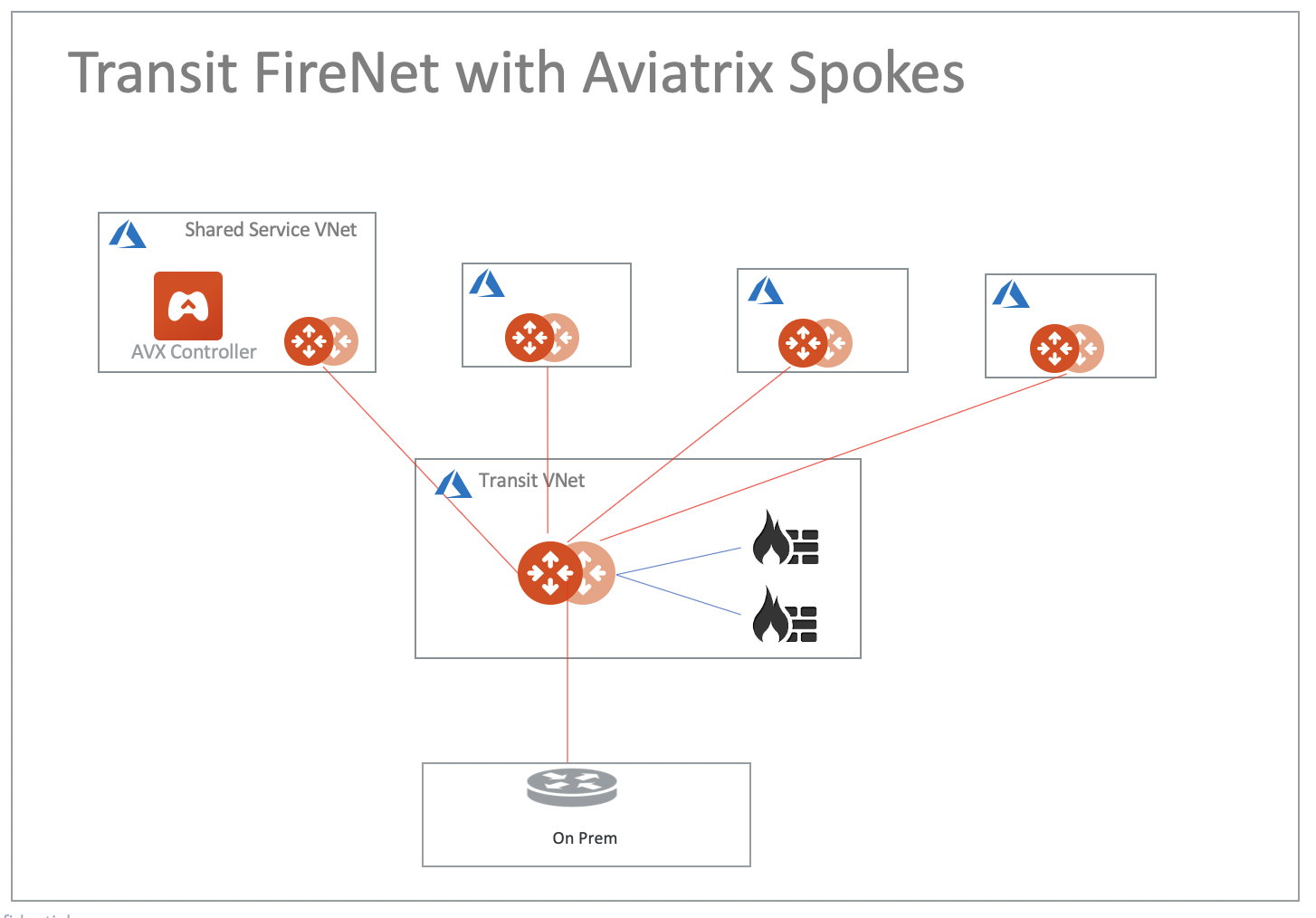
Transit FireNet with Aviatrix Spokes
You can apply firewall inspections for east-west, north-south and ingress/egress traffic.
Transit FireNet with Native Spokes
Firewall inspections can be applied to native Spoke VNet, on-prem to transit and north-south traffic.
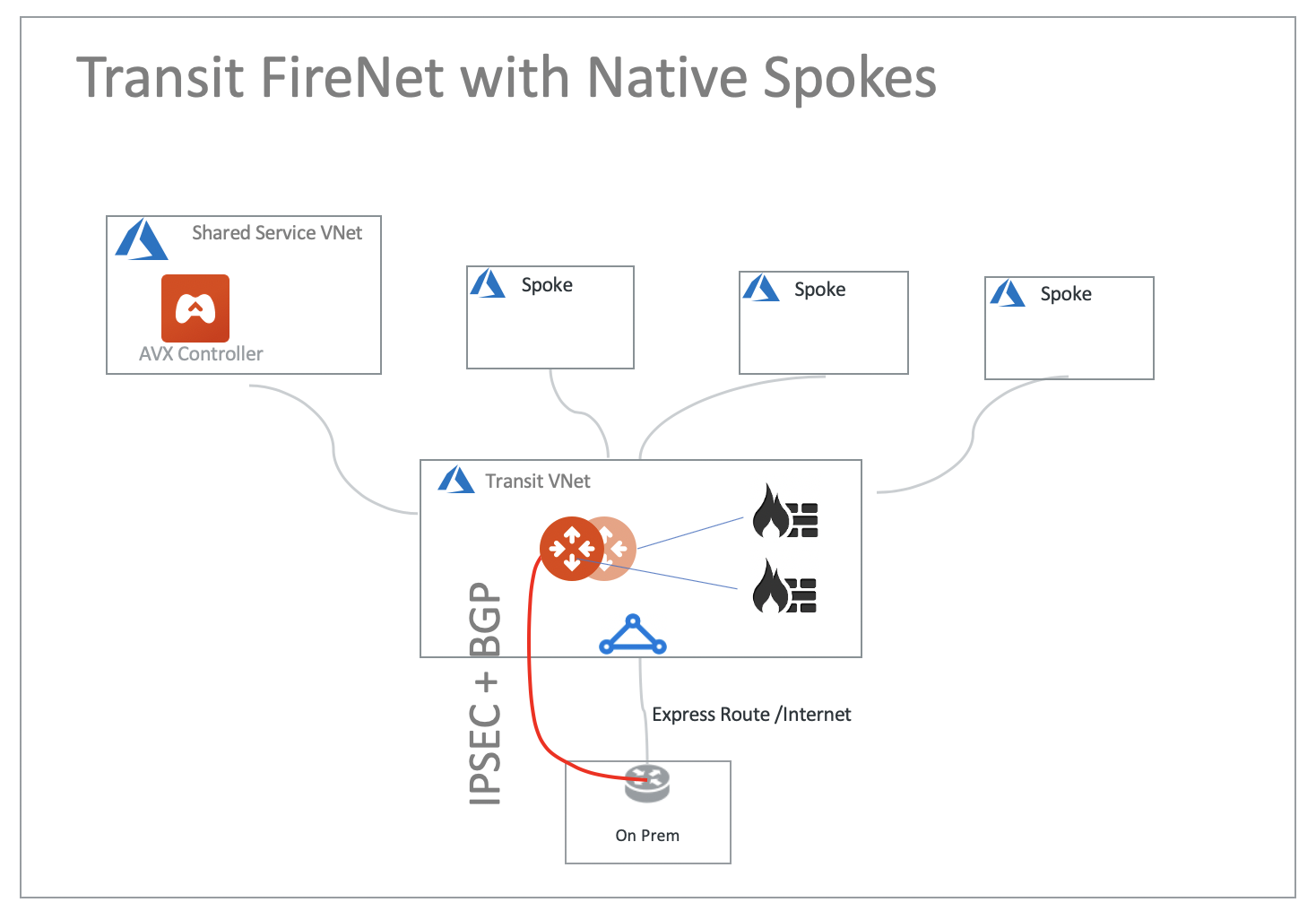
See Transit FireNet Workflow for Azure for more details.
SD-WAN Integration
If you have multiple sites to connect to the cloud, you can use an Aviatrix Transit Gateway to terminate the many Site2Cloud to branch offices.
Alternatively, you can use a SD-WAN termination point in the VNets to connect to the branches.
Both options can be described in the diagram below.
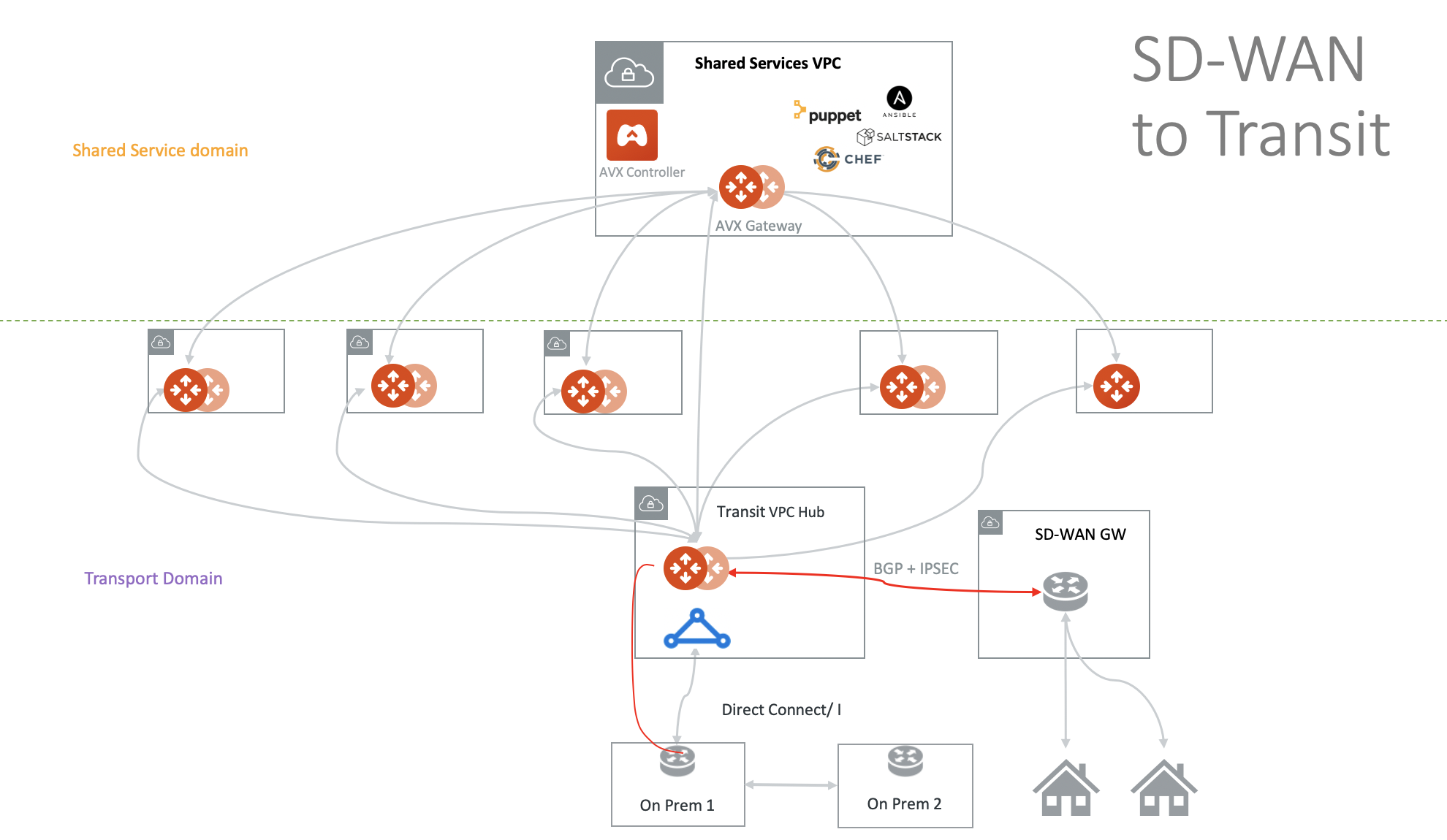
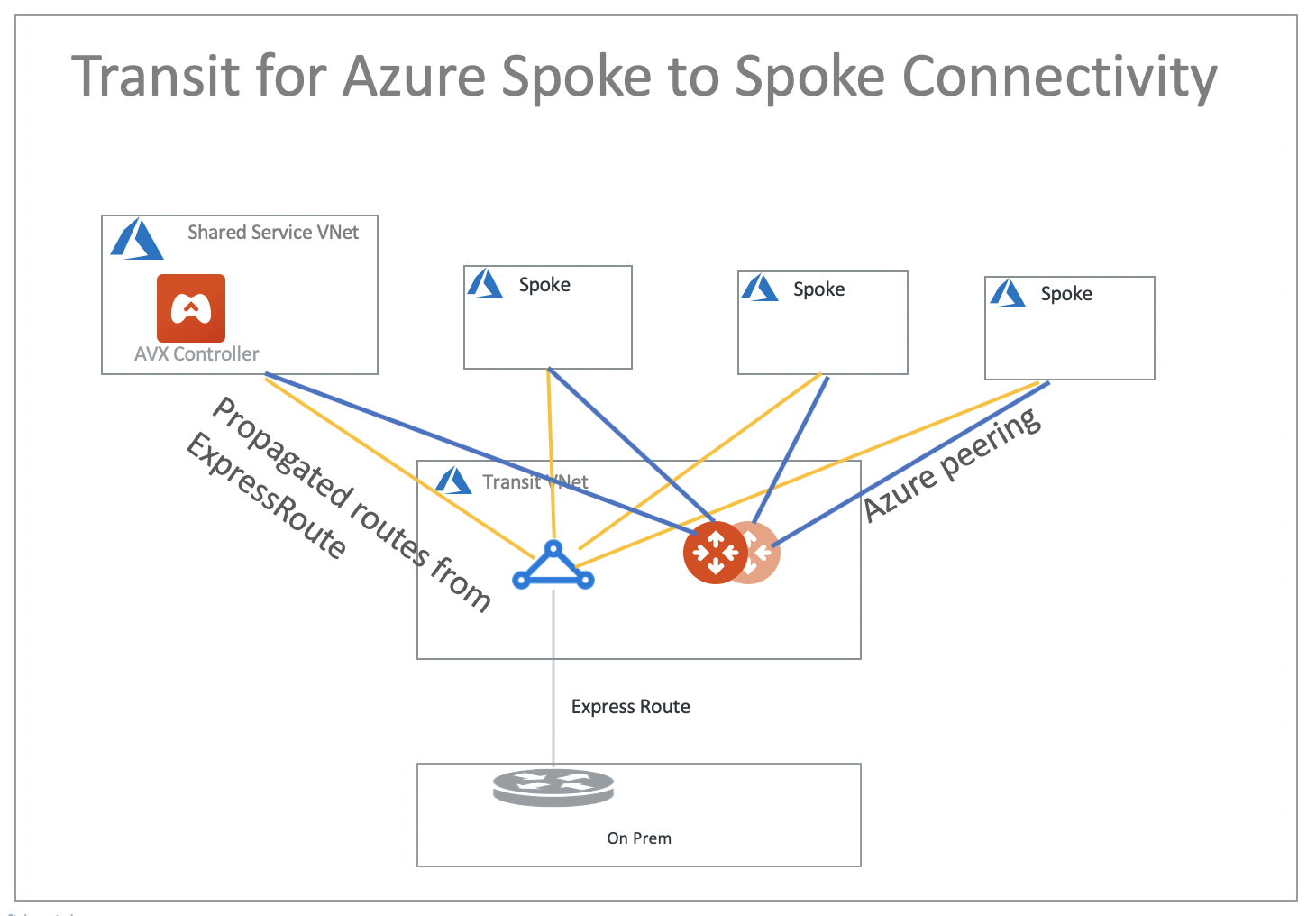
Aviatrix Transit Gateway for Azure Spoke-to-Spoke Connectivity
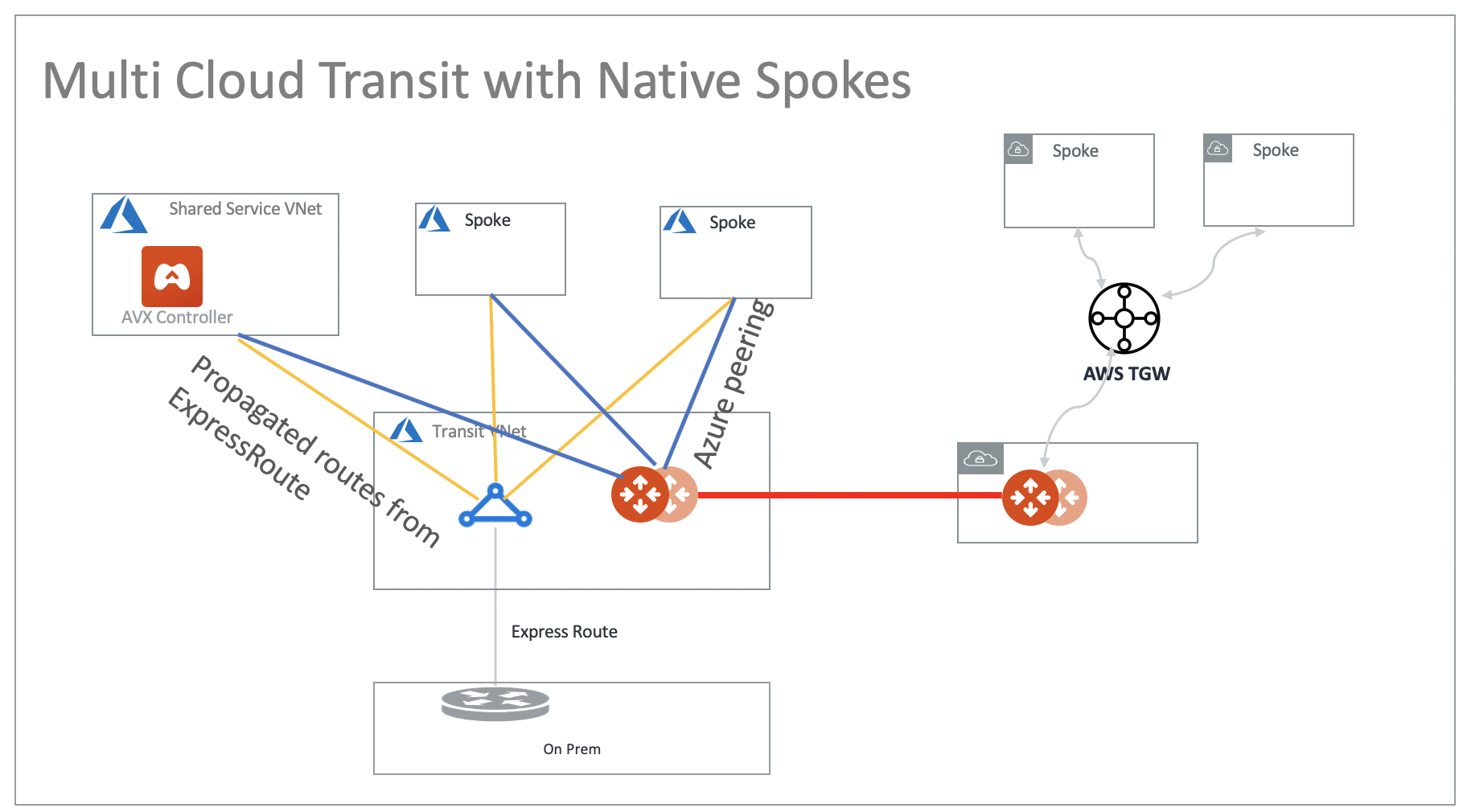
If you use Azure ExpressRoute gateway to connect Spoke VNets to on-prem, you can use Aviatrix Transit Gateway for Spoke-to-Spoke connectivity, as shown in the diagram below. To connect Spoke VNet, follow the instructions in Multicloud Transit Network workflow.