Multicloud Multi-Region Network Workflow
This document describes his document describes using Aviatrix Transit Gateways and Spoke Gateways to set up a multicloud transit network across multiple regions.
Overview
Companies are relying more and more on multiple cloud (multicloud) providers. However, setting up the connectivity between those providers is difficult. And, maintaining and monitoring the tunnels is time-consuming and cumbersome to troubleshoot.
Aviatrix simplifies this by providing simple, point-and-click tunnel creation between cloud providers. Additionally, Aviatrix gives you a single, centralized location from which to troubleshoot and monitor your connections.
Getting Started
The Aviatrix Controller automates, monitors, and reacts to events in each cloud environment on your behalf. In order to do this, we’ll need to configure a few things in each cloud to support this.
We’ll walk through these steps in the following sections. Once complete, you can connect to one or both cloud providers.
Start by logging into the Azure Portal.
Installing Aviatrix Controller from the Azure Marketplace
The first step is to install the Aviatrix Controller from the Azure Marketplace. Select the Aviatrix Cloud Gateway to AWS and GCP from the Marketplace. Configure the new VM to meet your preferences and requirements. Be sure to allow inbound connections on port 443. Once ready, launch the new VM and continue to the next step.
Preparing your Azure Account
While the VM is being deployed in the selected region, configure the following items:
Registering Aviatrix with Active Directory ###
-
Go to the Azure Active Directory (available from the left navigation panel or More Services).
-
Click Properties (available under Manage on the left inner navigation bar).
Copy and save the Directory ID for later use. It will be referred to again as the Application Endpoint.
-
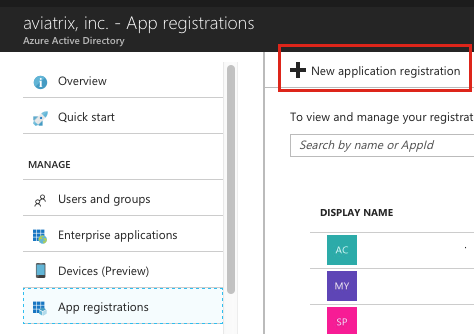
Click App registrations (available under Manage on the left inner navigation bar).
-
Click + New application registration along the top.
-
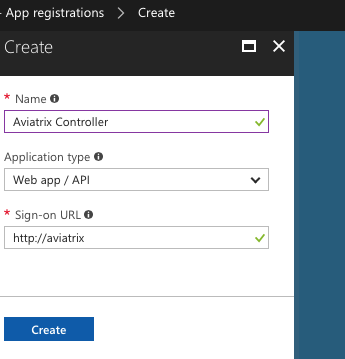
Populate the fields as follows:
| Field | Value |
|---|---|
Name |
Aviatrix Controller |
Application type |
Web app / API |
Sign-on URL |
-
Click Create.
Adding a Key #
-
Find and select the application you just registered in the list displayed.
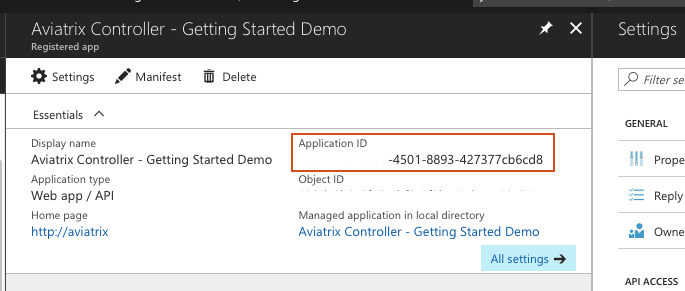
Copy and save the Application ID for later. It will be referred to again later in this document as the Application Client ID.
-
Click Keys in the Settings pane on the right.
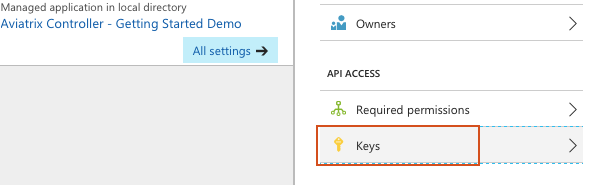
-
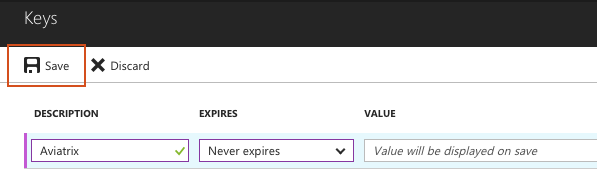
Enter a new row:
| Field | Value |
|---|---|
Key description |
Aviatrix |
Expires |
Never expires |
-
Click Save.
-
Copy the displayed key value and save it for later.
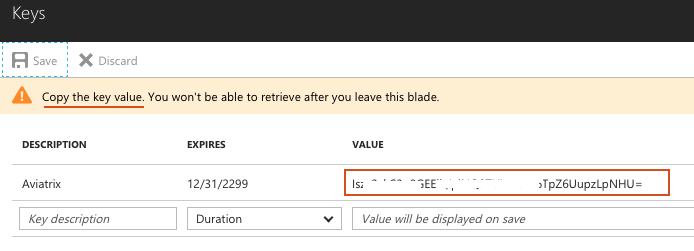
|
Save this value. It will be referred to again later in this document as the Application Client Secret. |
-
Exit the Keys window.
Adding Required Permissions
-
Select the Aviatrix Controller application registration again (you may already be on it).
-
Click Required permissions just above Keys.
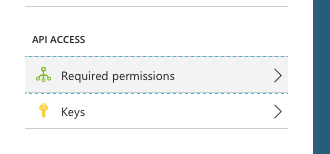
-
Click + Add button.
-
Click Select an API (on the right).
-
Find and select Windows Azure Service Management API.
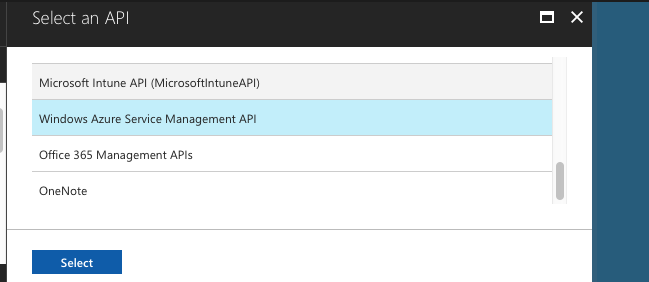
-
Click Select.
-
In the Enable Access panel, mark the Access Azure Service Management as organization users (preview) checkbox.
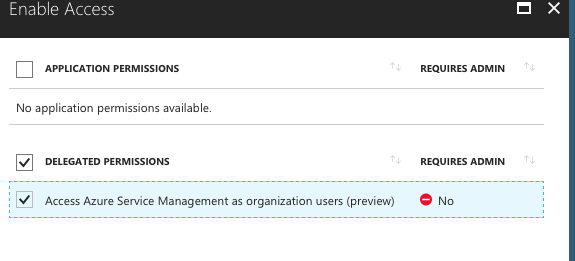
-
Click Select.
-
Click Done.
-
Exit the Required Permissions panel.
Granting Permissions to Aviatrix Controller
-
Go to the Subscriptions service (available from the left navigation panel or from More Services).
-
Click on the subscription where Aviatrix Controller is installed.
|
Copy and save the Subscription ID for later. |
-
Click Access Control (IAM).
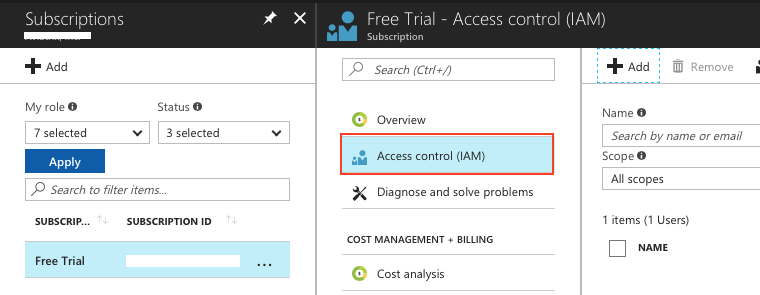
-
Click + Add.
-
Populate the fields as follows:
| Field | Value |
|---|---|
Role |
Contributor |
Assign access to |
Azure AD user, group, or application |
Select |
Aviatrix Controller |
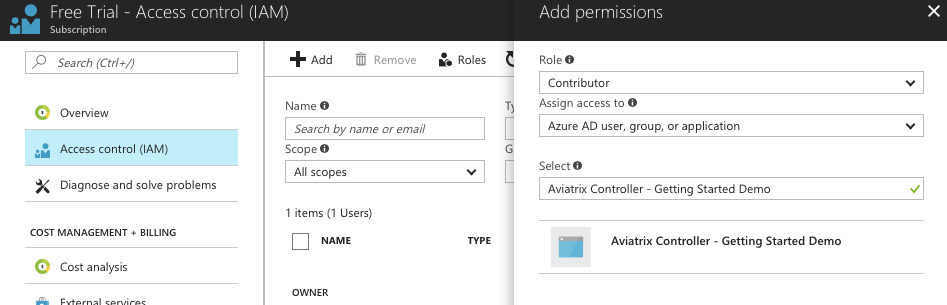
-
Click Save.
-
Exit the Access control (IAM) panel.
Configuring Aviatrix
Your Aviatrix Controller should be up and running by now. Go back to the Microsoft Azure portal and find the newly created instance. Open it and copy the Public IP address.
Open a browser and navigate to https://<public ip address>/ .
|
You may receive a warning about the certificate not matching. You can safely ignore this and continue to the page. |
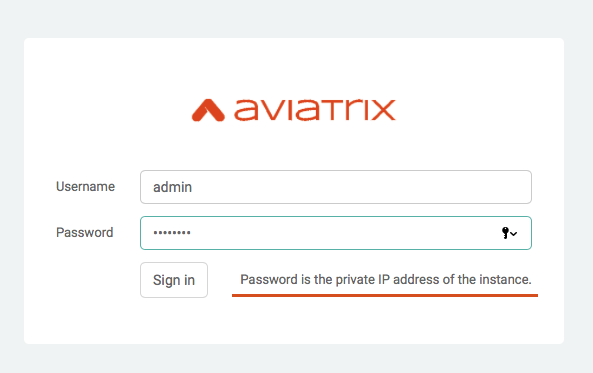
When you arrive at the login prompt, log in with the Username "admin." The password is the private IP address of the Azure instance.
|
Find the Private IP address on the instance page by selecting Networking. |
After logging in, you will be prompted to provide your email address. This is used for alert notifications as well as for password recovery. Enter your email address and click OK.
Set the admin password to something you will remember and click Save.
If you require a proxy for this instance to get to the internet, enter that now. Otherwise, click Skip.
Finally, the software will be upgraded. Click Run button and the latest version of the Controller will be downloaded and installed. This will take a few minutes. Once complete, the login prompt will appear.
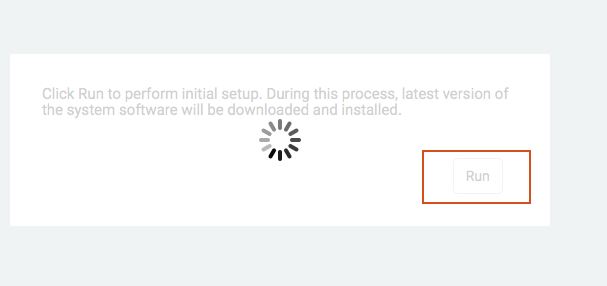
Log in with the username "admin" and the new password.
Azure
After logging in, click Azure ARM to connect Aviatrix to your Azure account.

Creating the Account
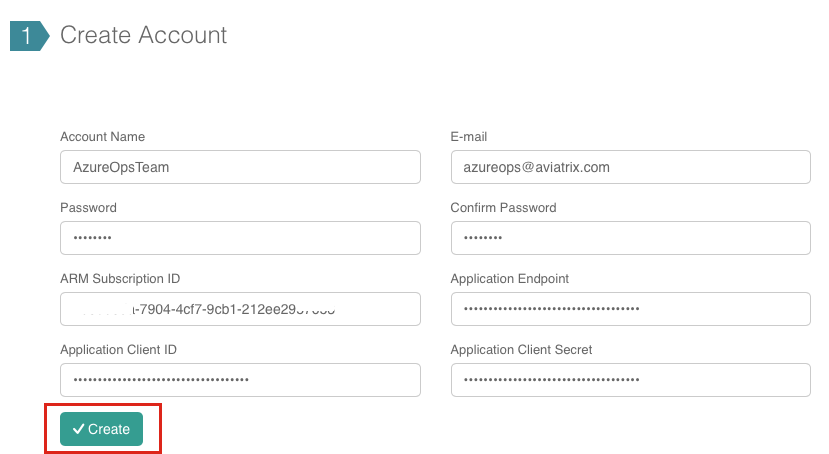
Fill out the fields as follows:
| Field | Expected Value |
|---|---|
Account Name |
The login/username for users who will have admin access to Azure resources. For example, AzureOpsTeam. |
The e-mail address for this team. |
|
Password |
Password for login to the controller |
Confirm Password |
|
ARM Subscription ID |
The Subscription ID you saved in a previous step. |
Application Endpoint |
The Application Endpoint (i.e., the Directory ID) retrieved earlier. |
Application Client ID |
The Client ID (i.e., the Application ID) saved earlier. |
Application Client Secret |
The Client Secret (i.e., the key value) displayed earlier. |
Once complete, click Create button at the bottom of the form.
Accepting License Agreement
Before you can automate launching an Aviatrix Gateway, you must first subscribe to the Aviatrix Companion Gateway in the Azure Marketplace.
-
Search for "aviatrix companion gateway."
-
Select the result.
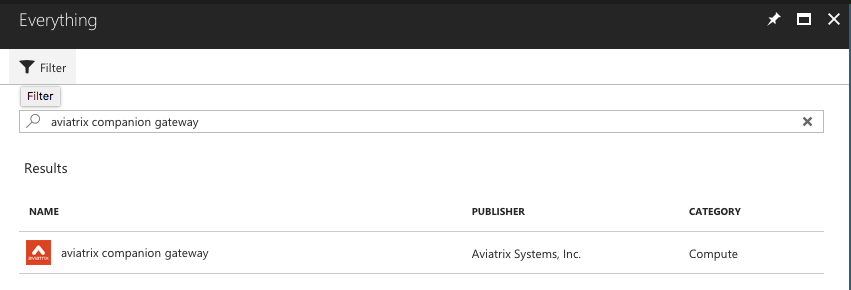
-
Click on the link at the very bottom titled "Want to deploy programmatically? Get started ➔".
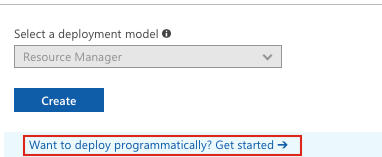
-
Click Enable status button.
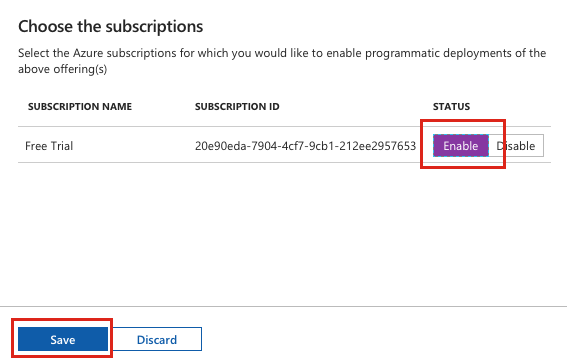
-
Click Save.
Creating a Gateway
The Controller can now automate creating a Gateway within Azure. Switch back to the browser tab or window with the Aviatrix Controller.
Click Gateway in the left navigation bar:
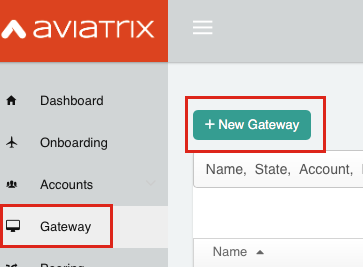
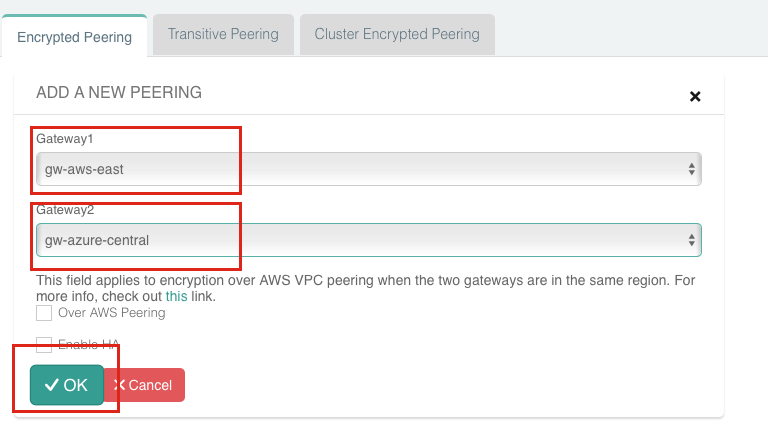
Next, click + New Gateway. Populate the Gateway Name and select the appropriate Region, VNet, and Public Subnet. The Gateway Size can be left at the smallest size. It can be scaled up (and out) later if needed.
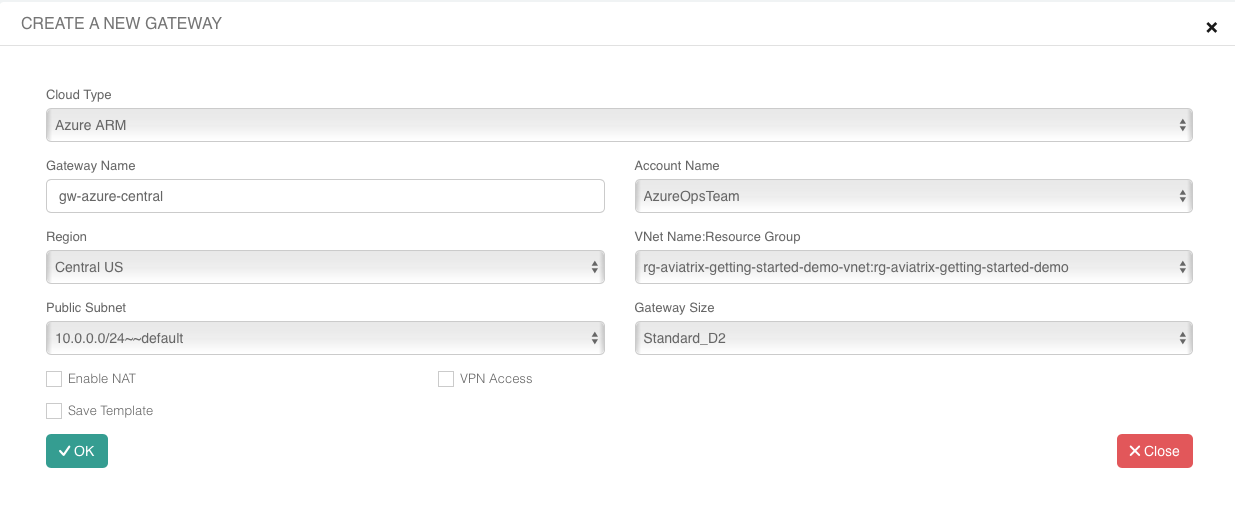
Click OK to create the Gateway automatically. This will take a few minutes as it creates the instance in the selected region and sets up the appropriate route table entries, etc.
Once complete, click X Close.
Now you have a Gateway in Azure that can connect to either AWS, GCP, or both.
AWS
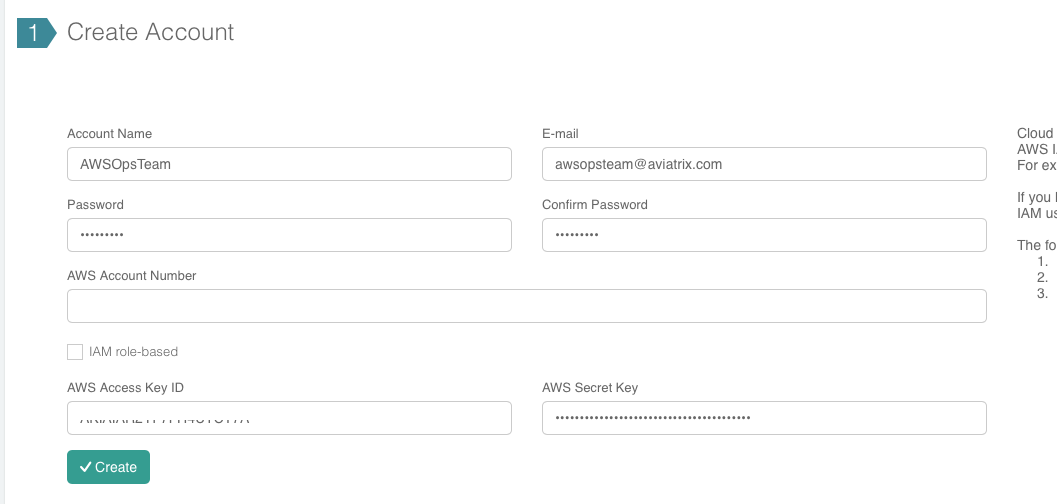
Creating the Account:
-
Go to the Onboarding section on your Controller.

-
Click AWS.
Fill out the fields as follows:
| Field | Expected Value |
|---|---|
Account Name |
The login/username for users who will have admin access to AWS resources. For example, AWSOpsTeam. |
The e-mail address for this team. |
|
Password |
Password for login to the controller |
Confirm Password |
|
AWS Account Number |
You can find your account number on the AWS billing page |
IAM role-based |
Leave this unchecked for now. For production use, you’ll want to use IAM roles with specific permissions. |
AWS Access Key ID |
An admin user’s AWS access key ID |
AWS Secret Key |
An admin user’s AWS secret key |
Once complete, click Create at the bottom of the form.
Deploying a Gateway in AWS
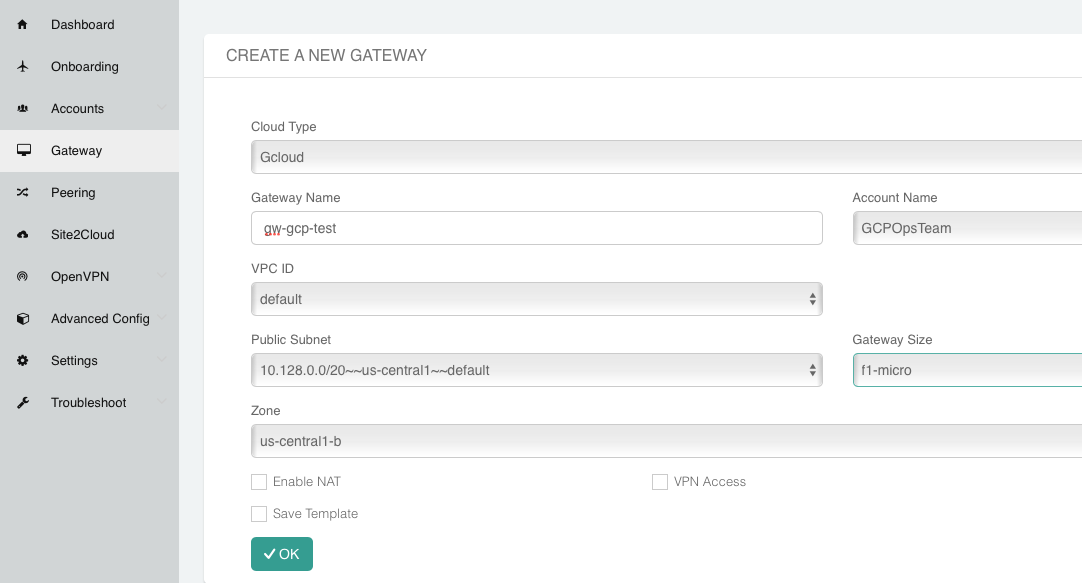
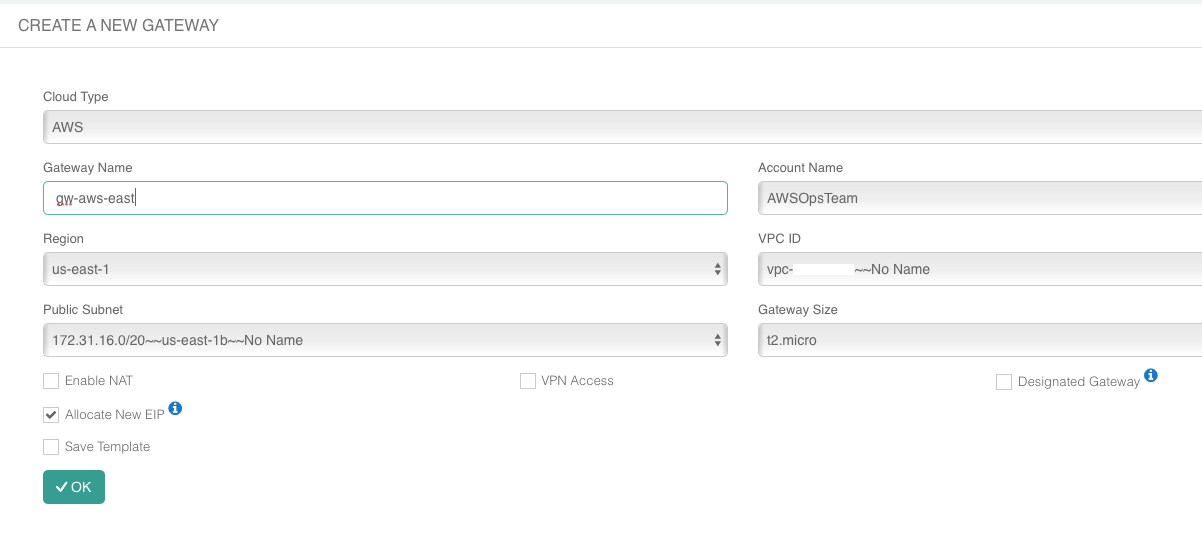
Head back over to the Gateways section in the Aviatrix Controller and click + New Gateway.
-
Select AWS for Cloud Type.
-
Enter a Gateway name.
-
Select the appropriate values for Region, VPC ID, and Public Subnet.
-
Set the default Gateway Size at t3.large.
-
Mark the Allocate New EIP checkbox so a new Elastic IP will be allocated on creation.
-
Click OK when ready.
TipCreate a new VPC for testing.
GCP
Preparing your Google Cloud Account
The Aviatrix Controller requires a few settings to be enabled in order for it to be able to interact with your Google Cloud account.
-
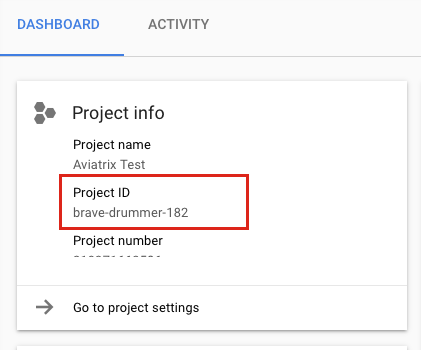
From the Google Cloud Console Dashboard, copy and save the Project ID.
-
Enable GCloud Messaging Service. The Controller relies on Google Cloud Pub/Sub APIs to communicate with the Gateways in GCP. Enable these APIs by going to the APIs & services Dashboard for the selected project. Select Enable APIs and Services at the top of the page.
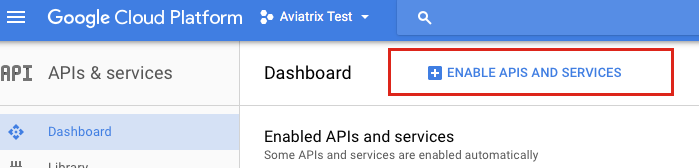
Select Google Cloud Pub/Sub API from the list. Then, click Enable.
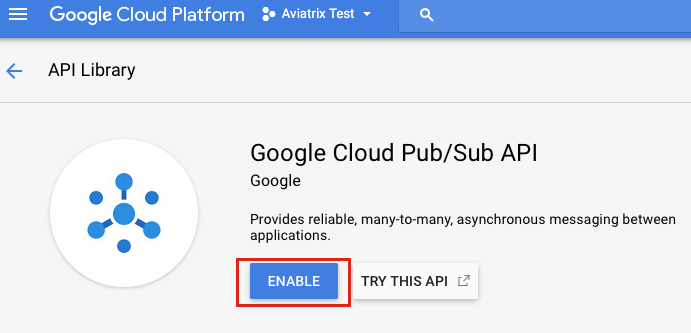
-
Create a Credentials File. Navigate back to the APIs & services Dashboard and select Credentials (or click here).
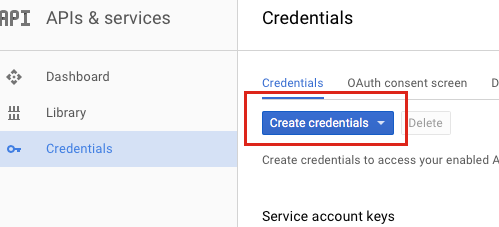
Click the Create credentials dropdown menu and select Service account key.
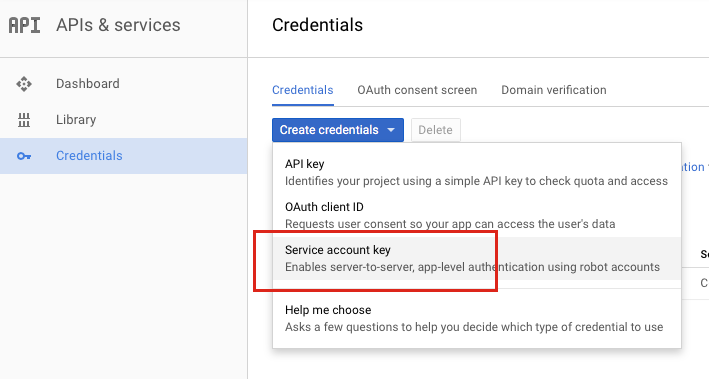
Select Compute Engine default service account for the Service account and select JSON for Key type.
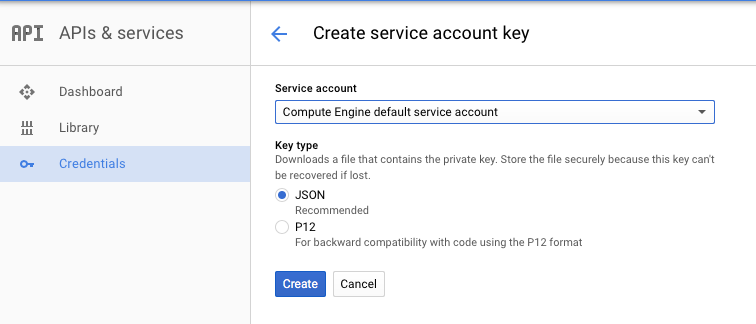
Then, click Create. A file will be downloaded to your computer. Find it and store it in a safe location. Then, click Close.
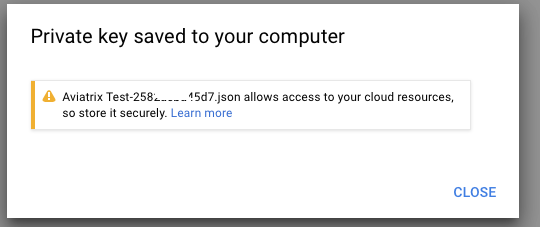
You are now ready to connect the Aviatrix Controller to your Google Cloud Platform account.
Create Account
-
Go to the Onboarding section on the Aviatrix Controller.

-
Click GCloud.
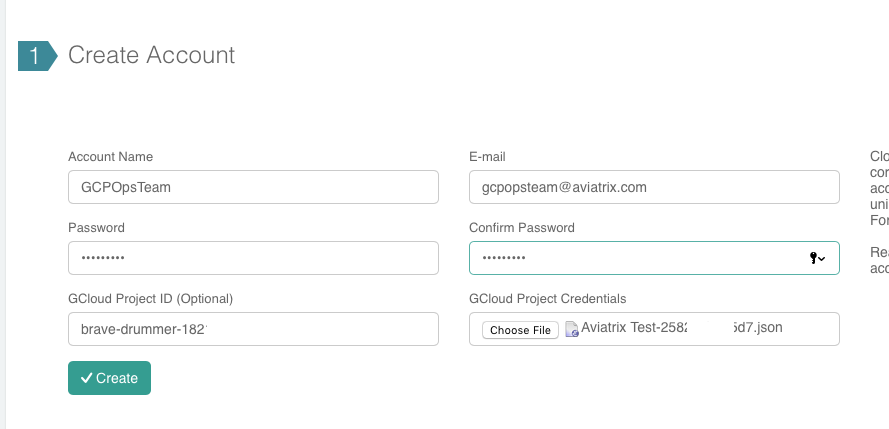
Fill out the fields as follows:
| Field | Expected Value |
|---|---|
Account Name |
The login/username for users who will have admin access to Google Cloud resources. For example, "GCPOpsTeam." |
The e-mail address for this team. |
|
Password |
Password for login to the Controller |
Confirm Password |
|
GCloud Project ID |
The Project ID saved earlier |
GCloud Project Credentials |
Select the credentials file created in an earlier step. |
Once complete, click Create at the bottom of the form.
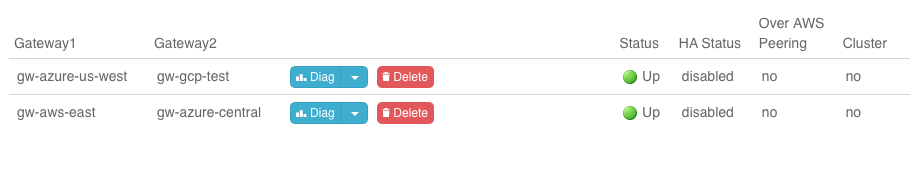
Summary
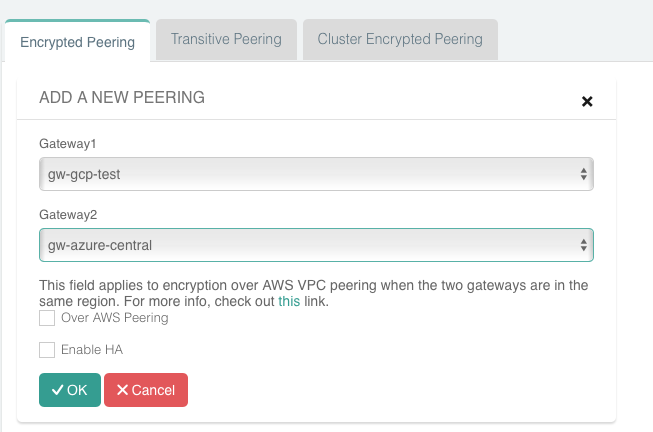
If you peered your Azure account with both AWS and GCP, then you should see something like this on your Aviatrix Controller Dashboard:
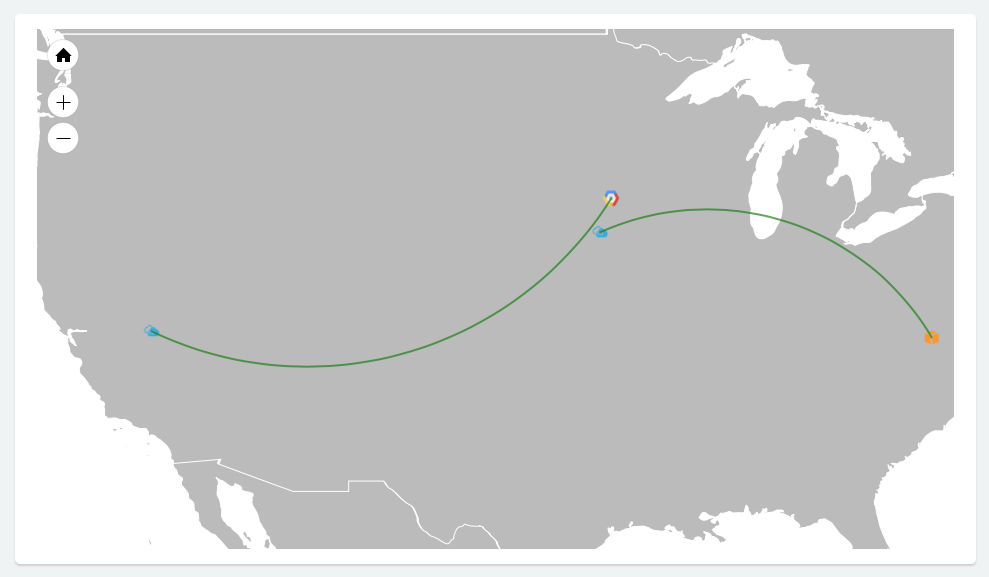
Now that you have the accounts established, you can easily add connectivity to other VPCs in either AWS or GCP. And, of course, you can also connect AWS to GCP.