Configuring Palo Alto in AWS
Example Config for Palo Alto Network VM-Series in AWS
This document provides an example for setting up the VM-Series to validate that packets are indeed sent to the VM-Series for VPC-to-VPC and from VPC-to-internet traffic inspection.
For using the bootstrap method to set up the VM-Series, follow this document.
The VM-Series in Azure can be set up using this guide.
The Aviatrix Firewall Network (FireNet) workflow launches a VM-Series at this step in the process. After the launch is complete, the console displays the VM-Series instance with the public IP address of its management interface and allows you to download the .pem file for SSH access to the instance.
Below are the steps for initial setup.
Downloading VM-Series Access Key
After this step is completed, you can download the .pem file by selecting the firewall on the Firewall Network > List > Firewall page and clicking Actions > Download key.
If you get a download error, usually it means the VM-Series is not ready. Wait until it is ready, refresh the browser, and then try again.
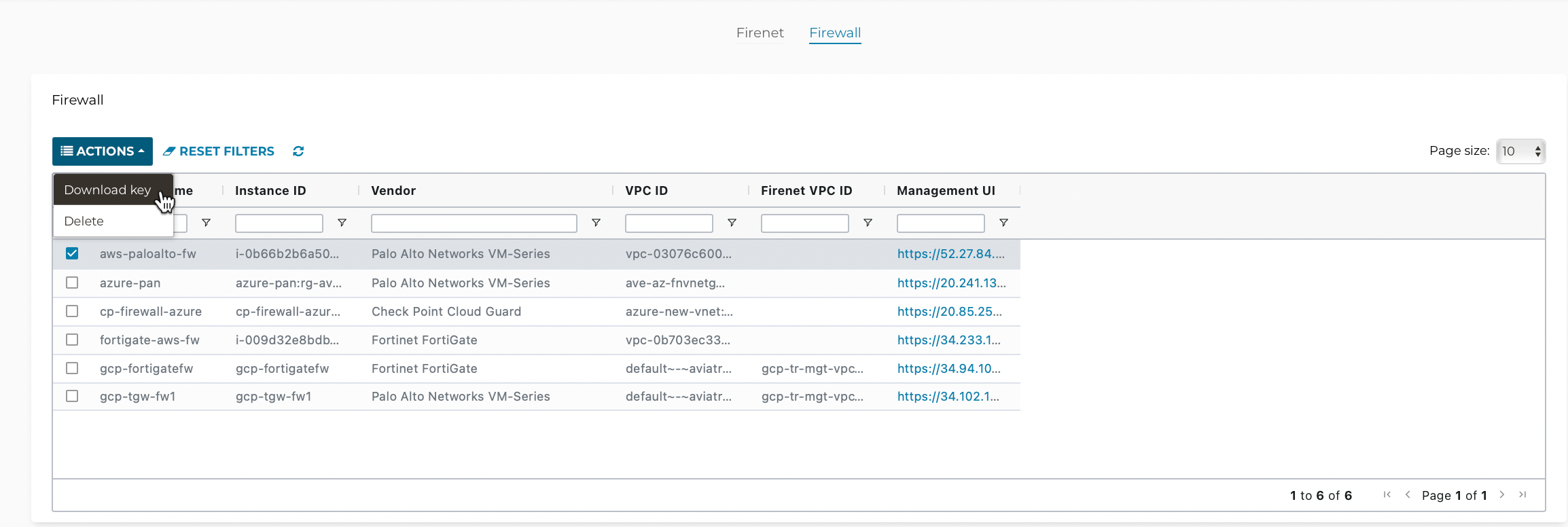
Resetting VM-Series Password
| After you download the .pem file, change the file permission to 600. If you are asked to enter a password during the login, the VM-Series is still not ready. Wait and try again. It usually takes up to 15 minutes for the VM-Series to be ready. When the VM-Series is ready, you will no longer be prompted for a password. |
For Metered AMI, open a terminal and run the following command.
ssh -i <private_key.pem> admin@<public-ip_address> configure set mgt-config users admin password commit
For BYOL, open a terminal and run the following command.
ssh -i <private_key.pem> admin@<public-ip_address> configure set mgt-config users admin password set deviceconfig system dns-setting servers primary <ip_address> commit
Terminate the SSH session.
Logging in to VM-Series
Go back to the Aviatrix Controller. Go to this step of the Firewall Network workflow. Click the Management UI link. This takes you to the VM-Series you just launched.
Login with Username "admin". The password is the password you set in the previous step.
Dynamic Updates
-
From Device > Dynamic Updates > Click Check Now > download and then install the latest versions of Applications and Threats Wildfire updates.
-
Click Check Now again to download and then install the latest version of Antivirus.
Configuring VM-Series ethernet1/1 with WAN Zone
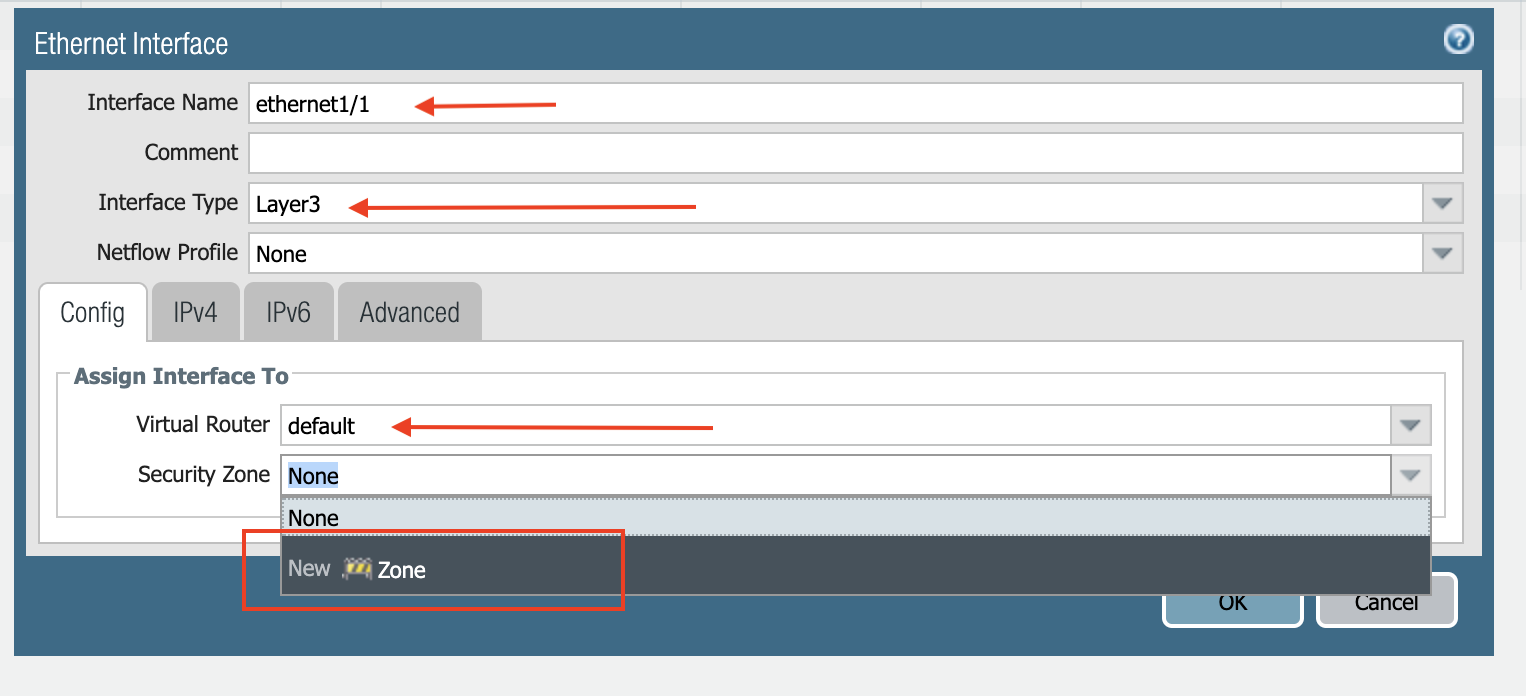
Once logged in, click on the Network tab to see a list of ethernet interfaces. Click ethernet1/1 and configure as per the following screenshot.
-
Select the Network tab.
-
Click ethernet1/1.
-
Select layer3 for Interface Type.
-
Select the Config tab in the popup Ethernet Interface window.
-
Select default for Virtual Router at the Config tab.
-
Click New Zone for Security Zone to create a WAN zone.
-
At the next popup screen, name the new zone WAN and click OK.
-
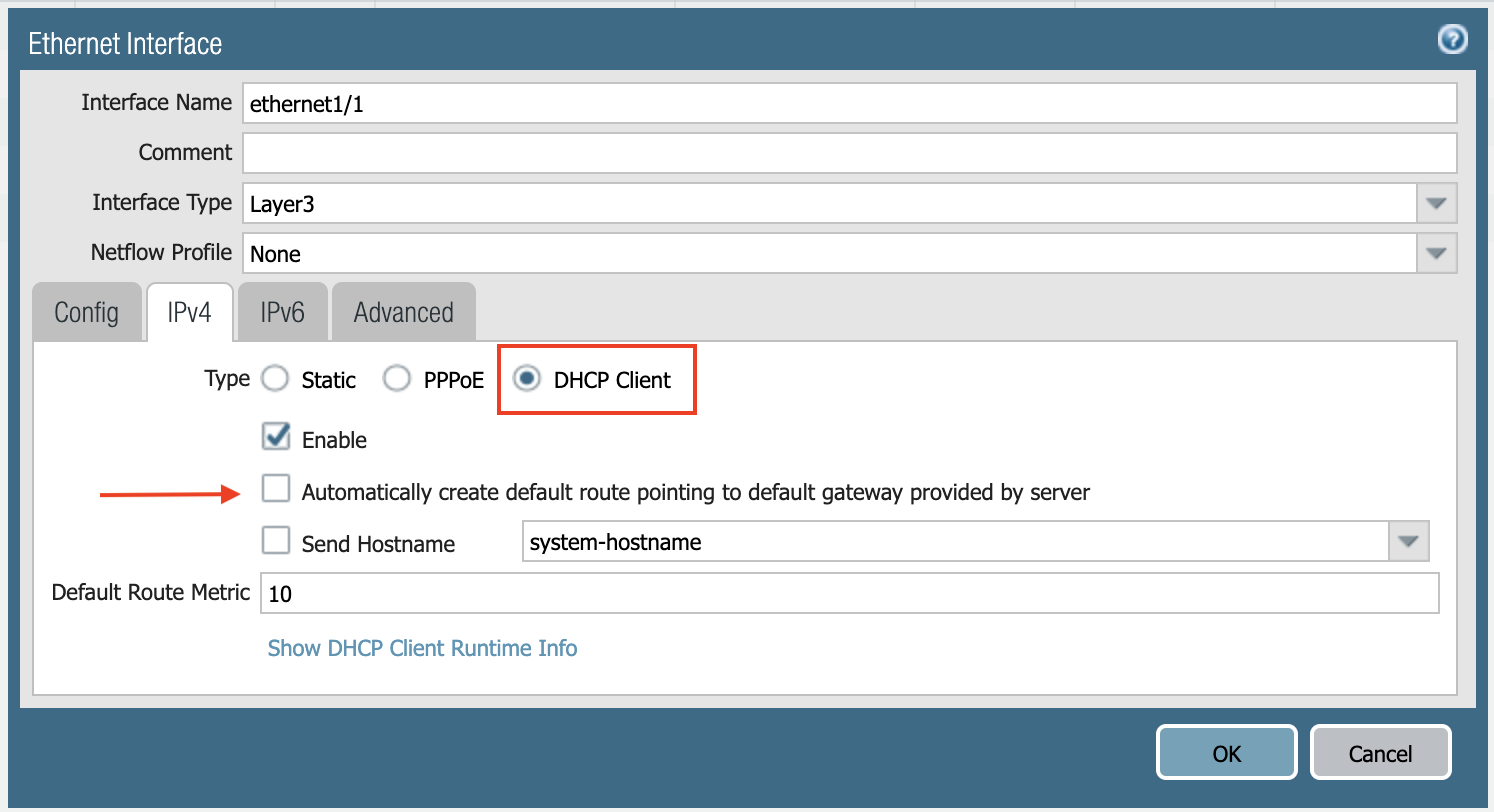
Select the IPV4 tab in the popup Ethernet Interface window.
-
Select DHCP Client.
-
Clear the Automatically create default route pointing to default gateway provided by server checkbox as shown below.
-
Click Commit. Once Commit is complete, you should see the Link State turn green at the Network page for ethernet1/1.
Configuring VM-Series ethernet1/2 with LAN Zone
Repeat the steps from Configuring VM-Series ethernet1/1 with WAN Zone section above for ethernet1/2. Name the new zone LAN.
Click Commit. Once Commit is complete, you should see the Link State turn green at the Network page for ethernet1/2.
If Keepalive via Firewall LAN Interface is enabled in Firewall Network > Advanced, ensure that ping is allowed in the Firewall LAN interface configuration: FireNet keep alive.
Configuring Allow Outbound Policies
-
Navigate to Policies > Security > Click Add.
-
Name the policy "Outbound," then select the Source tab.
-
Select LAN zone > Destination tab.
-
Select WAN zone > Click OK.
Configuring NAT for Egress
If you would also like to enable NAT to test egress, use the following steps:
-
Navigate to Policies > NAT and click Add.
-
Select the General tab and name the policy.
-
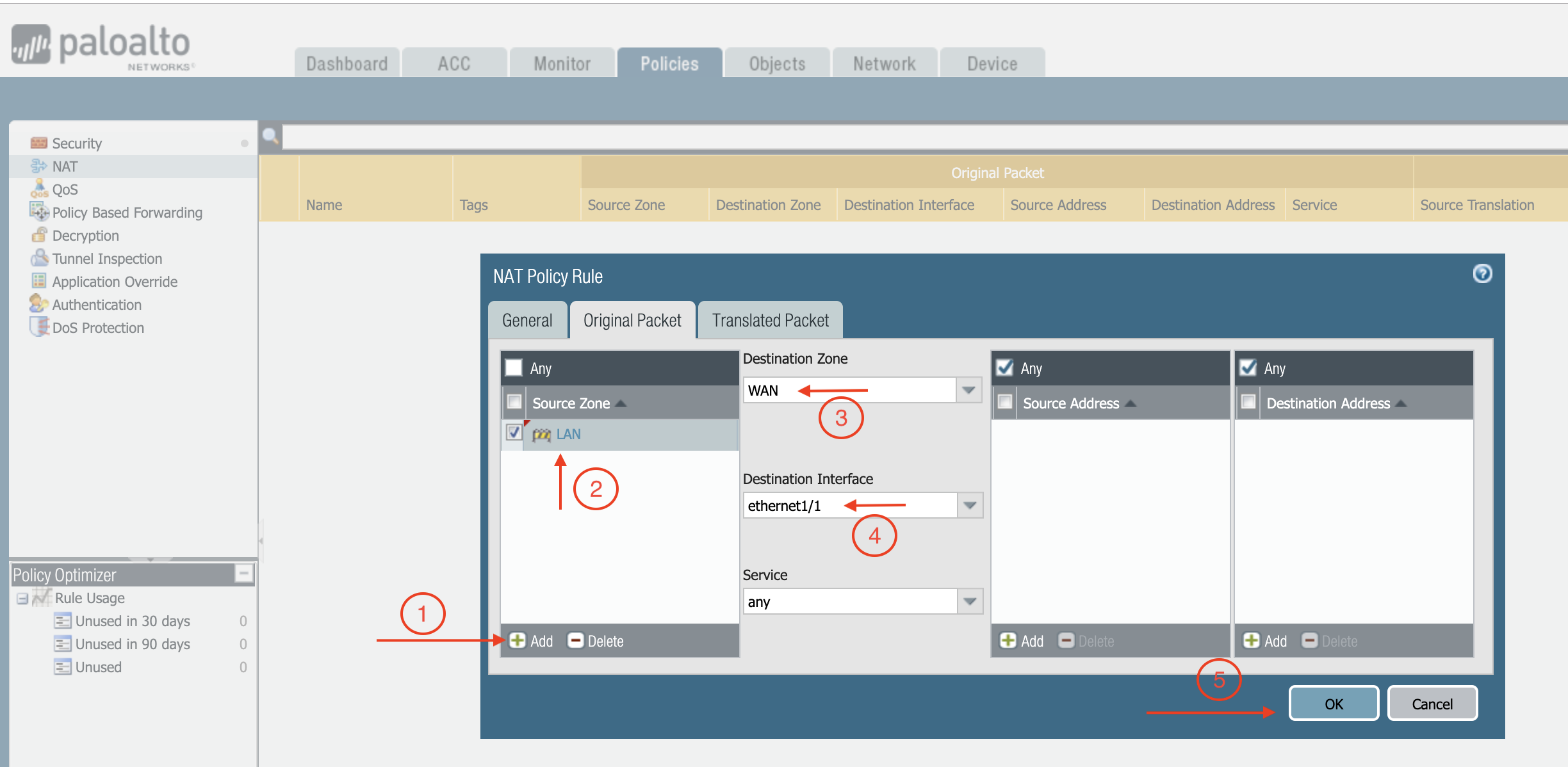
Click Original Packet.
-
At Source Zone, click Add, and select LAN.
-
At Destination Zone, select WAN.
-
At Destination Interface, select Ethernet1/1, as shown below.
-
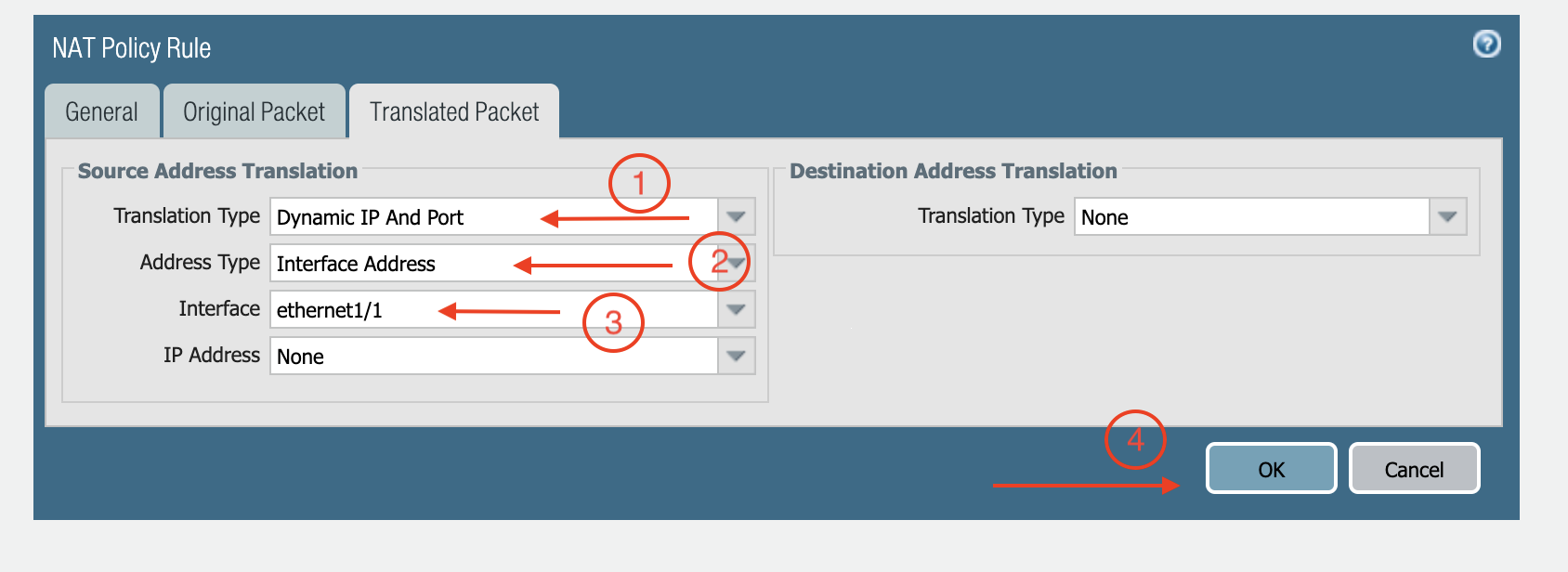
Click Translated Packet. At Translation Type, select Dynamic IP And Port.
-
At Address Type, select Interface Address.
-
At Interface, select ethernet1/1, as shown below.
Setting up API Access
For the Aviatrix Controller to automatically update firewall instance route tables, monitor firewall instance health, and manage instance failover, you need to set up API access permissions.
Follow the instructions here to enable API access.
Ready to Go
Now your firewall instance is ready to receive packets.
The next step is to specify which Network Domain needs packet inspection by defining a connection policy that connects to the firewall domain. This is done by Configuring Allow Outbound Policies (see the section above) in the Firewall Network workflow.
For example, deploy Spoke-1 VPC in Network_Domain_1 and Spoke-2 VPC in Network_Domain_2. Build a connection policy between the two domains. Build a connection between Network_Domain_2 to Firewall Domain.
Launch one instance in Spoke-1 VPC and Spoke-2 VPC. From one instance, ping the other instance. The ping should go through.