OpenVPN AWS TGW
This document describes OpenVPN AWS TGW.
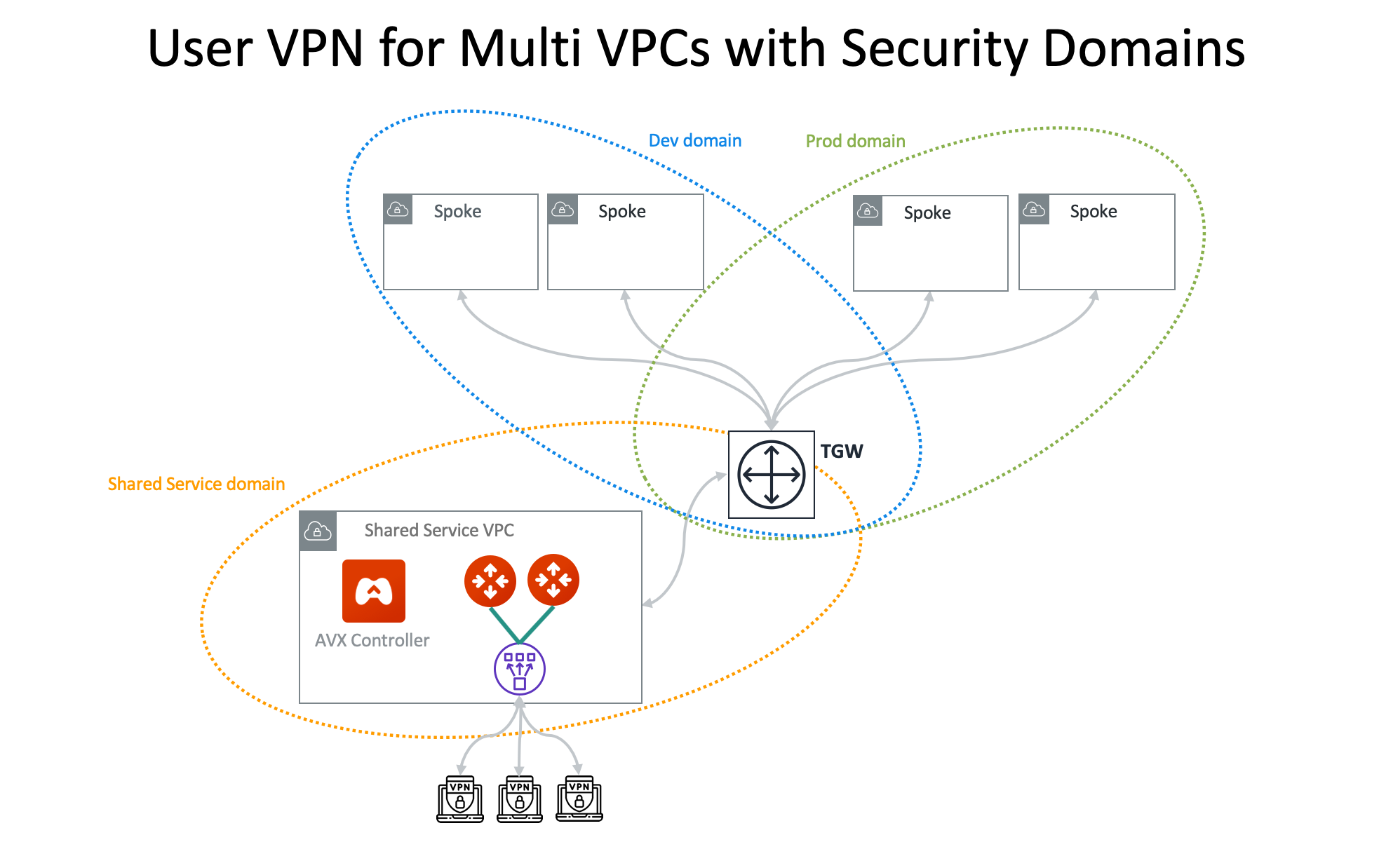
Use AWS Transit Gateway to Access Multiple VPCs in One Region
This reference guide will show how you can use an AWS Transit Gateway (TGW) to allow remote users to connect to multiple VPCs in the same region. Please see the overview images below for reference. In this walkthrough, it is assumed you have created VPCs in your environment. If not, you can create and deploy VPCs directly from the Aviatrix Controller under the Useful Tools menu. See Create a VPC.
Creating a TGW
The first step is to create a TGW from the Aviatrix Controller.
-
Log into to the Aviatrix Controller.
-
Navigate to the TGW Orchestrator tab on the left side of the screen and click Plan.
-
Next, select your cloud type. In this case, it is AWS. Fill in the remaining information, name the TGW, and click Create.
To learn more about Transit Gateway deployment, see Aviatrix TGW Orchestrator FAQ.
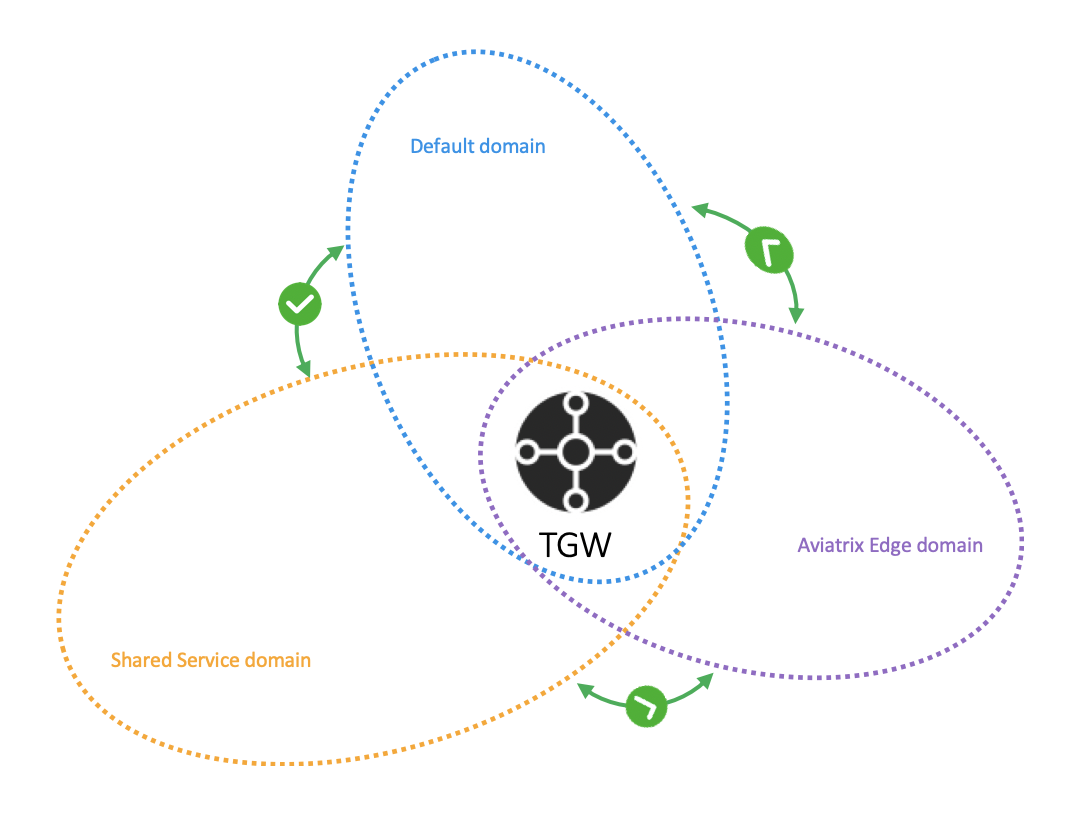
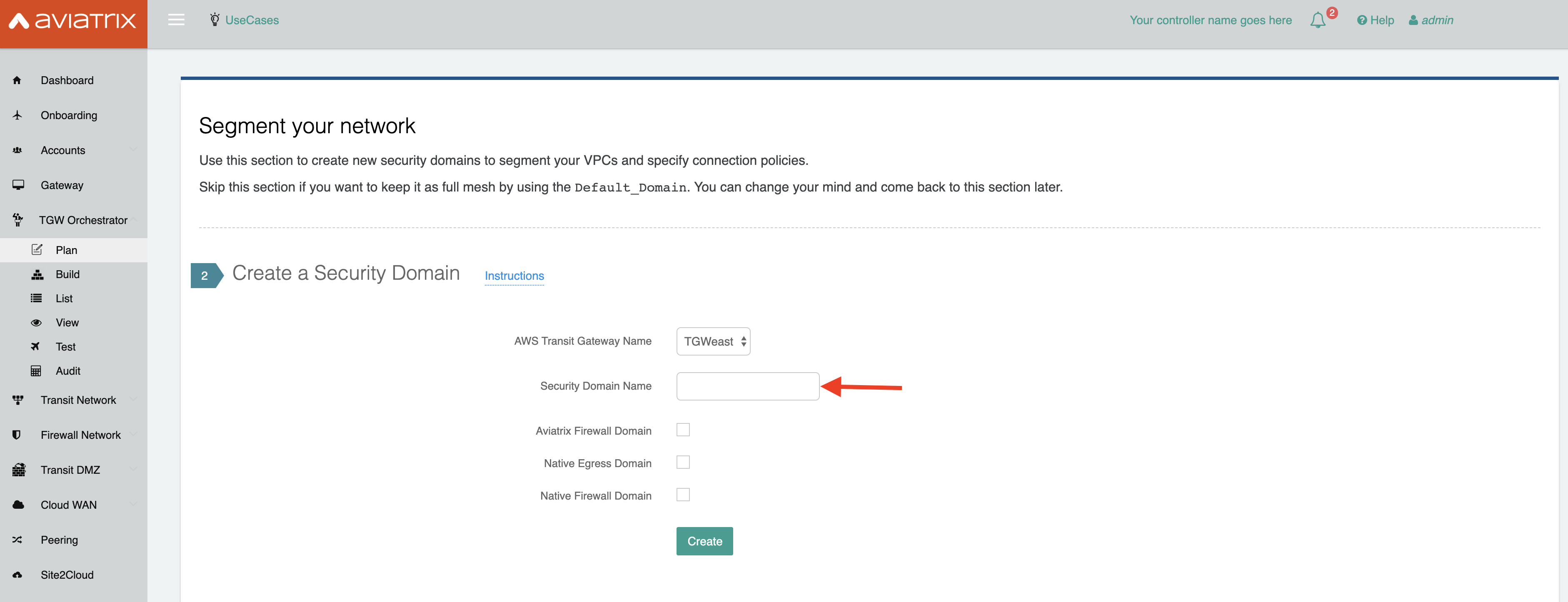
Creating a Security Domain
In the same section, under Step 2 (titled "Segment your network") in the TGW Orchestrator is the "Create a Security Domain" step. Scroll down to see this step. For this design, create three security domains:
-
Shared Service Domain
-
Dev Domain
-
Prod Domain
-
First, select the AWS Transit Gateway Name you created in the previous step from the dropdown menu.
-
Next, name the first Security Domain Name "Shared Service Domain" and click Create.
-
Repeat this process for the other two domains.
-
Building Connection Policies
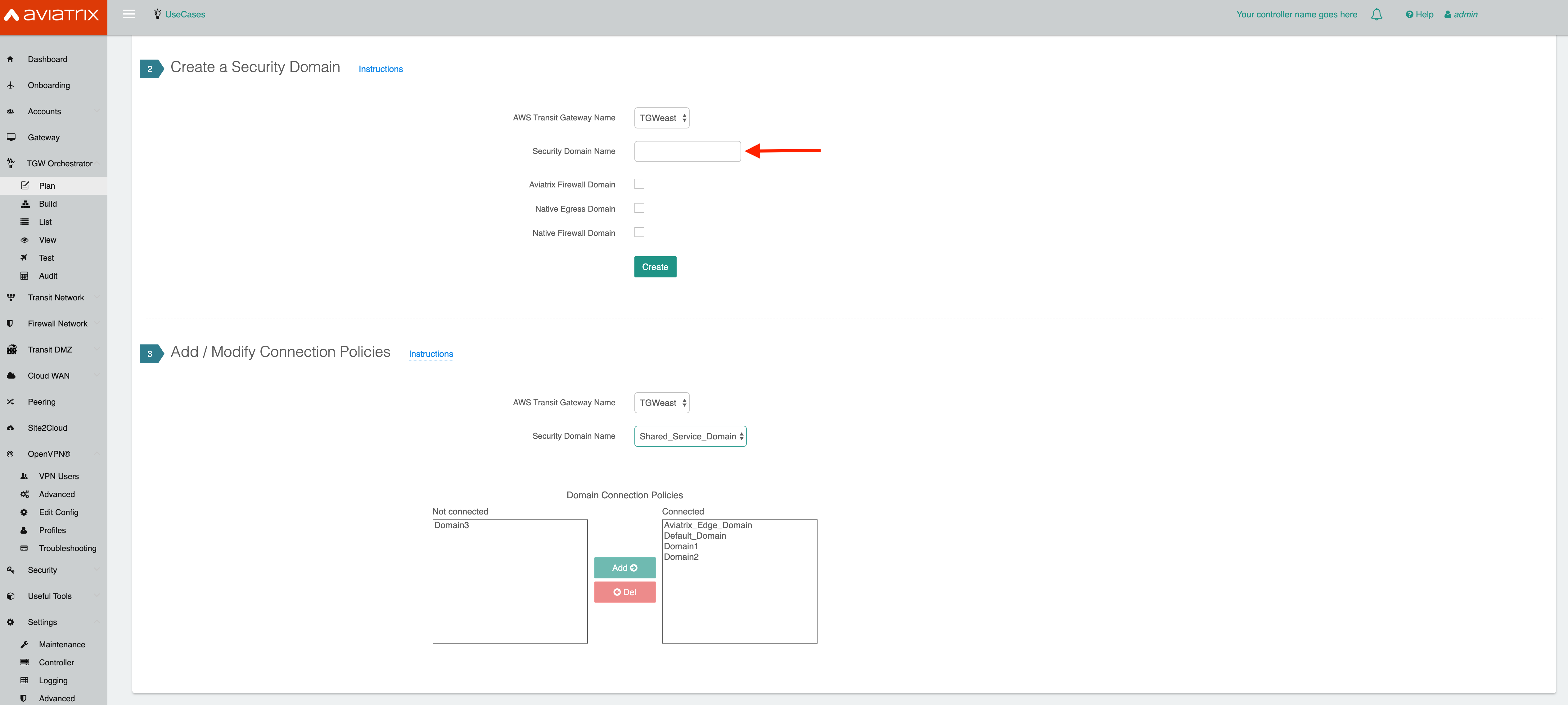
You have now created Security Domains. The next step is to use these domains to define the connection policies.
-
First, make sure you select the AWS Transit Gateway Name created above.
-
Next, for Security Domain Name, select Shared Services Domain.
-
Select the Dev domain from the Domain Connection Policy List under Not Connected and add it to the Connected list.
-
Repeat this step for the Prod domain.
Now, you have allowed both the Dev and Prod Domains to connect to the Shared Service Domain.
|
You can call these domains any name and use as many domains as needed. As seen in the images below Dev and Prod are simply called Domain 1 and Domain 2. |
Attaching VPCs to TGW
The next step is to attach your existing VPCs to the Transit Gateway (TGW) created above.
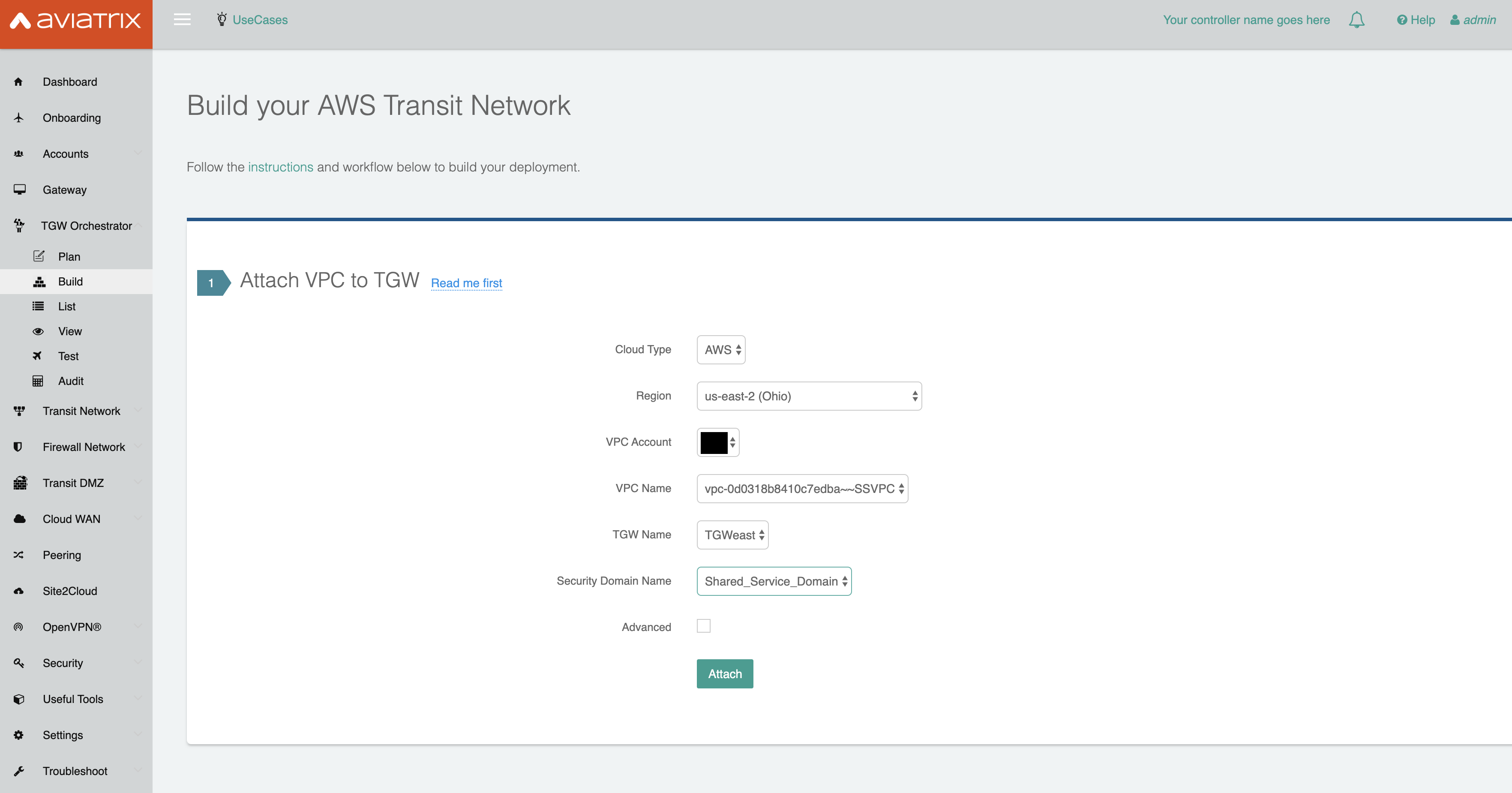
To perform this, navigate in the Aviatrix Controller to the "Build" section under the TGW Orchestrator tab. In section 1, "Attach VPC to TGW":
-
Select the region of the TGW and your account.
-
Choose your Shared Service VPC and TGW Name.
-
Select Shared Service Domain for the Security Domain Name.
-
Click Attach.
Attaching VPCs to TGW
The next step is to attach your existing VPCs to the Transit Gateway (TGW) created above.
To perform this, navigate in the Aviatrix Controller to the "Build" section under the TGW Orchestrator tab. In section 1, "Attach VPC to TGW":
-
Select the region of the TGW and your account.
-
Choose your Shared Service VPC and TGW Name.
-
Select Shared Service Domain for the Security Domain Name.
-
Click Attach.

Launching a VPN Gateway
After attaching VPCs to the TGW, create a VPN Gateway so users can access the instances in the VPCs.
-
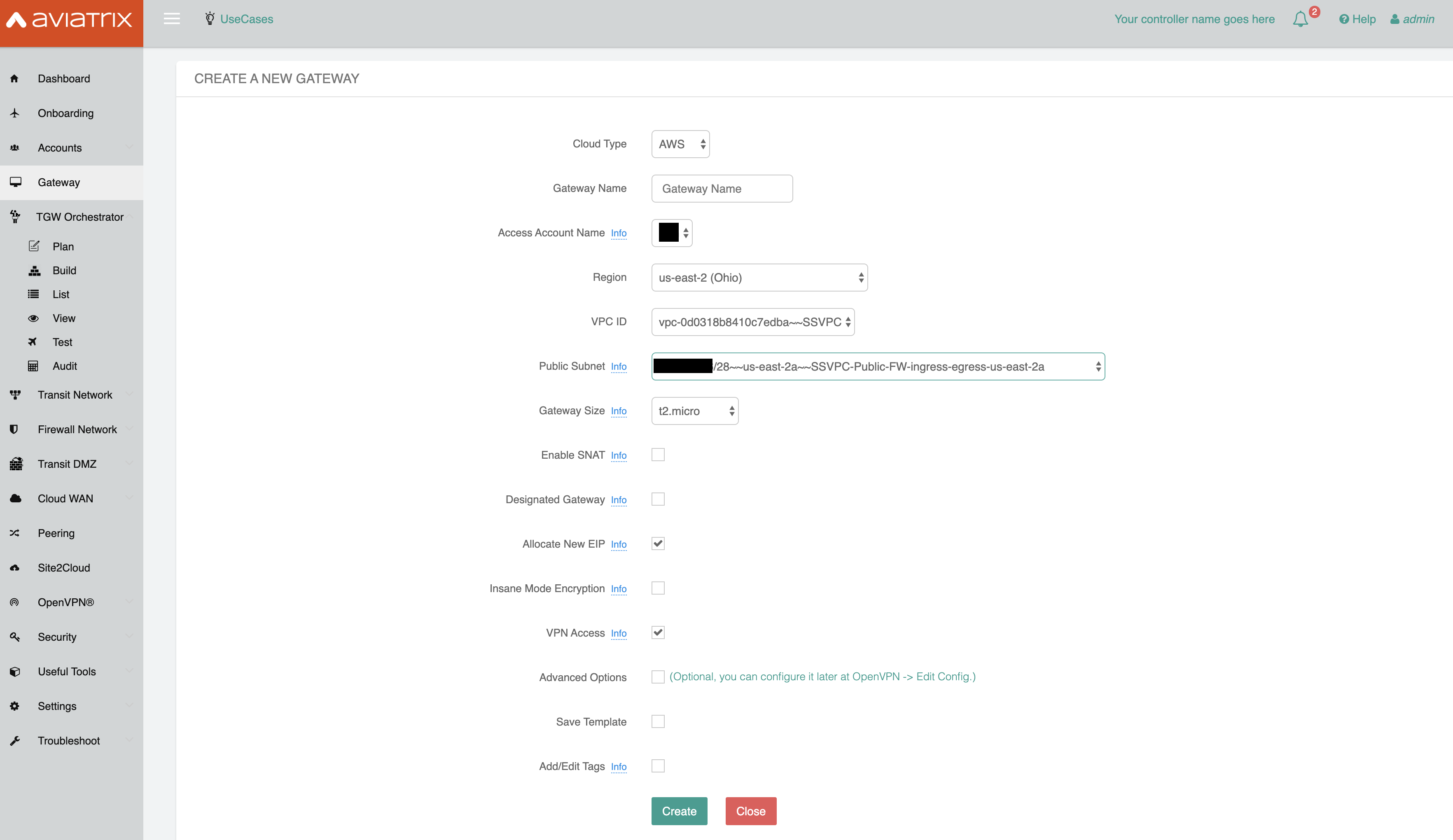
Navigate to the Gateway tab on the Aviatrix Controller and click New Gateway.
-
The cloud type is AWS. Enter a Gateway name.
-
Next, pick the region deployed in above and select the Shared Service VPC.
-
Mark the Allocate New EIP and VPN Access checkboxes.
-
Click Create.
A new VPN Gateway will be created in the Shared Service VPC.
More detailed options for deploying an Aviatrix Gateway are available here Gateway Options.
Configuring VPN Gateway
Now, in order to segment the Development and Production VPCs, enable Split Tunnel Mode on the VPN Gateway.
-
In your Aviatrix Controller, select OpenVPN® > Edit Config.
-
In "VPC ID/VNet Name" section, select the Shared Service VPC created earlier.
-
Confirm the proper LB/Gateway Name is selected.
-
In the "Modify Split Tunnel" section, add the IPv4 CIDR ranges for the Dev and Prod VPCs.
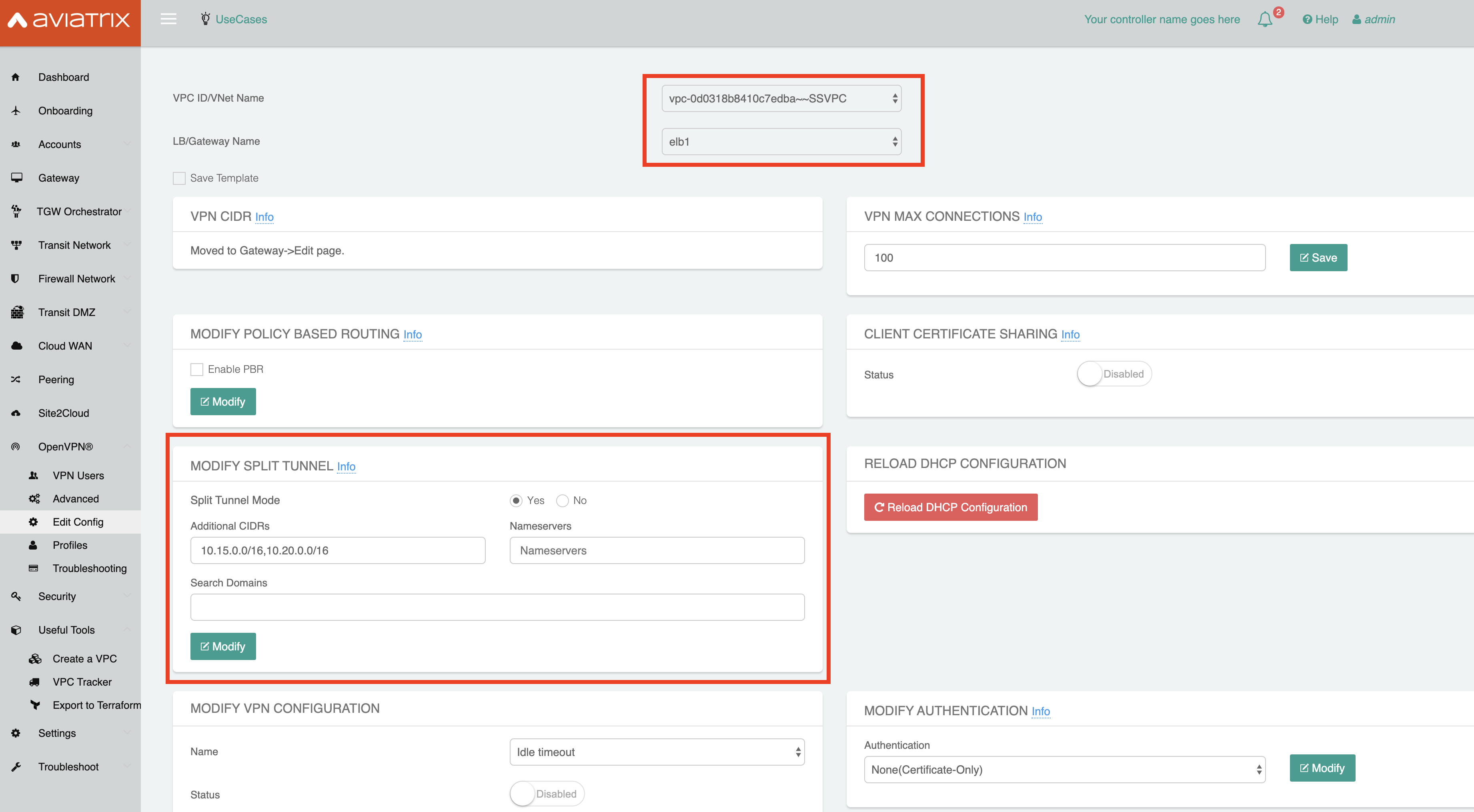
These ranges can be found by logging-into AWS and navigating to the VPC section. In your Aviatrix Controller, you can navigate to Useful Tools > VPC Tracker. There, you can view all the CIDR ranges for your VPCs. You will see your Prod and Dev VPCs there.
Configuring Aviatrix VPN Client
The first step is to add a new VPN User.
-
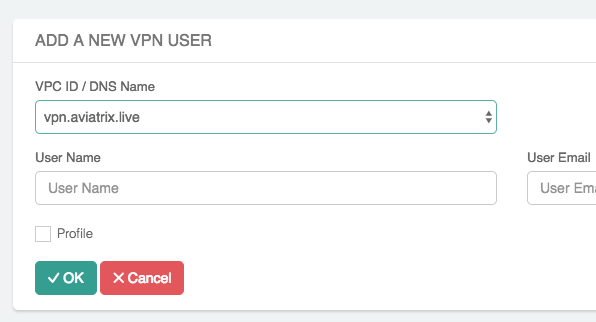
Navigate to OpenVPN® > VPN Users.
-
Click Add New and fill out the information in the fields provided. For the VPC ID, use the Shared Service VPC ID.
-
Next, download your OpenVPN® configuration file.
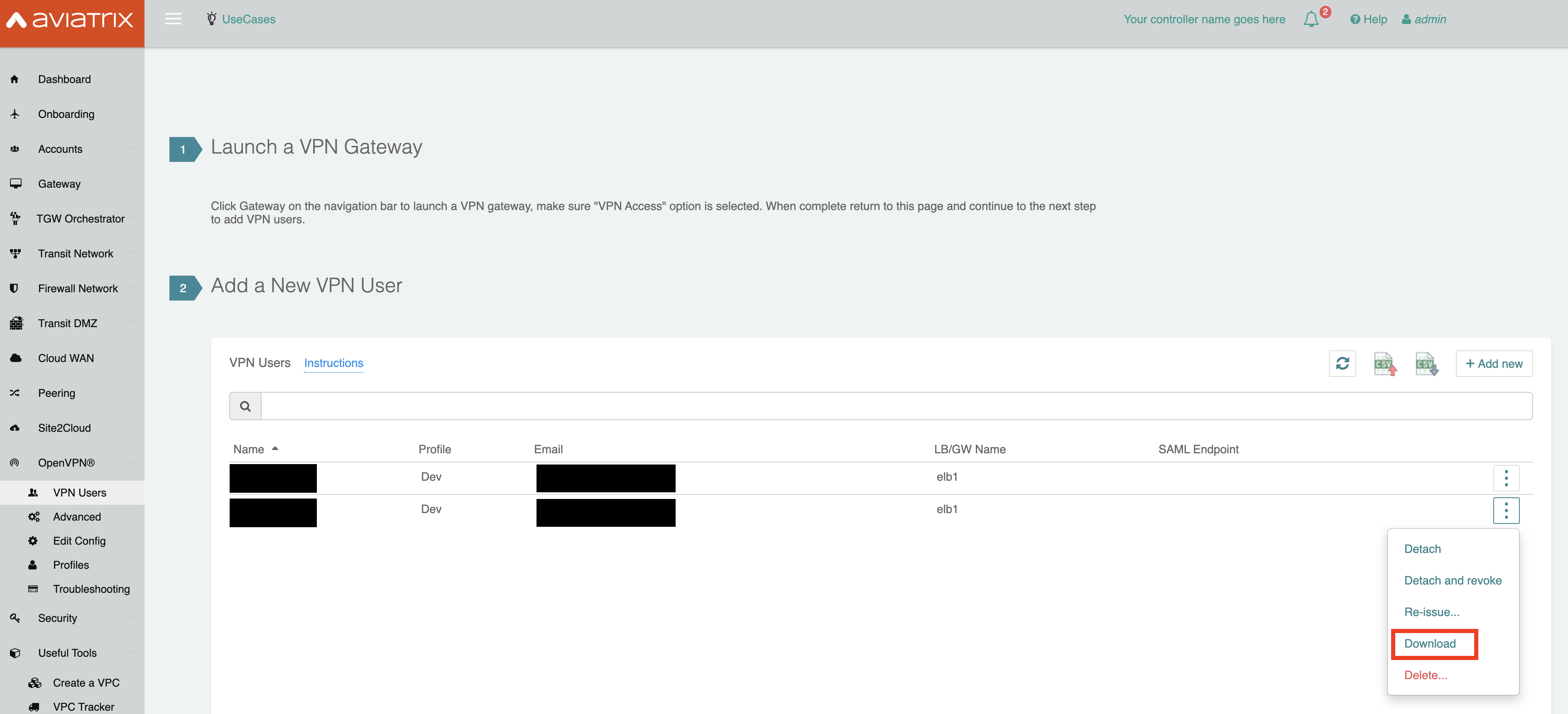
-
Download the latest Aviatrix VPN Client from the Docs page here: Aviatrix VPN Client.
5. After installing the client, import your OpenVPN® configuration file to the Aviatrix VPN Client. Once the client is open, click + and choose your .ovpn file. 6. After the configuration file is imported, click Connect.
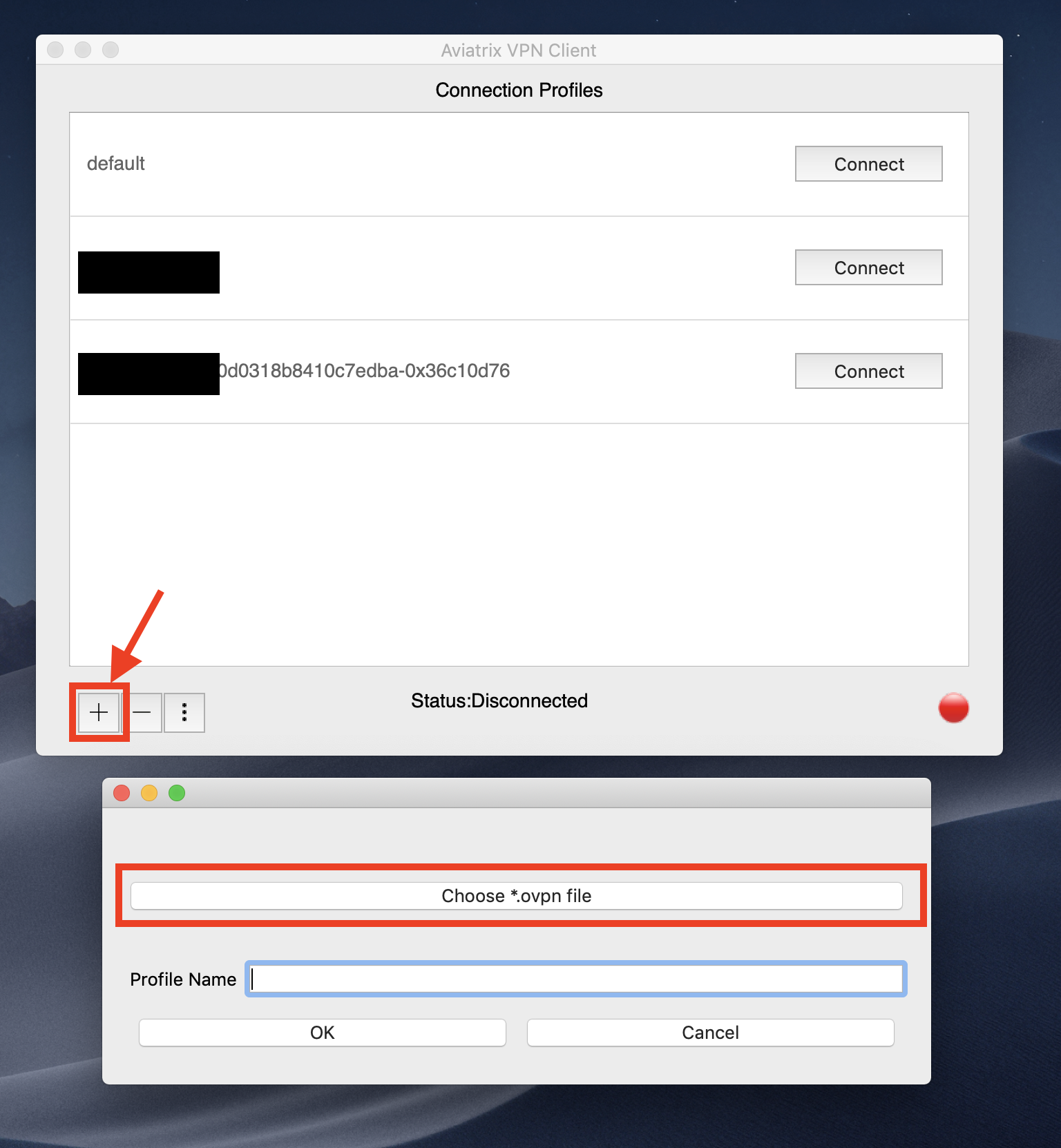
You are now connected via the Aviatrix VPN Client. Test that everything has been correctly configured.
1. First, find and save the Private IP address of the EC2 instance running in either Dev or Prod VPCs. These IPs can be found in the AWS Console page under the EC2 banner.
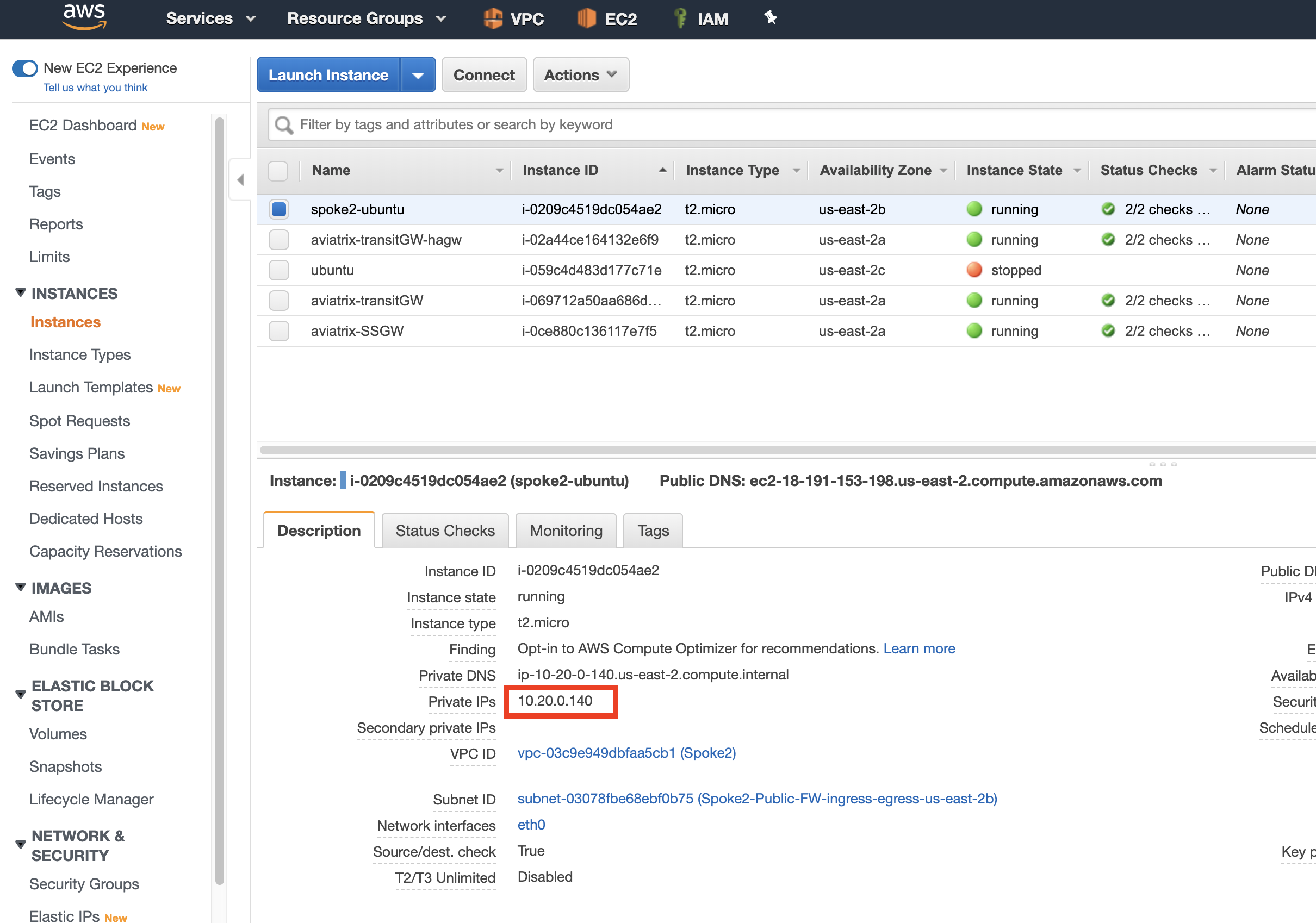
-
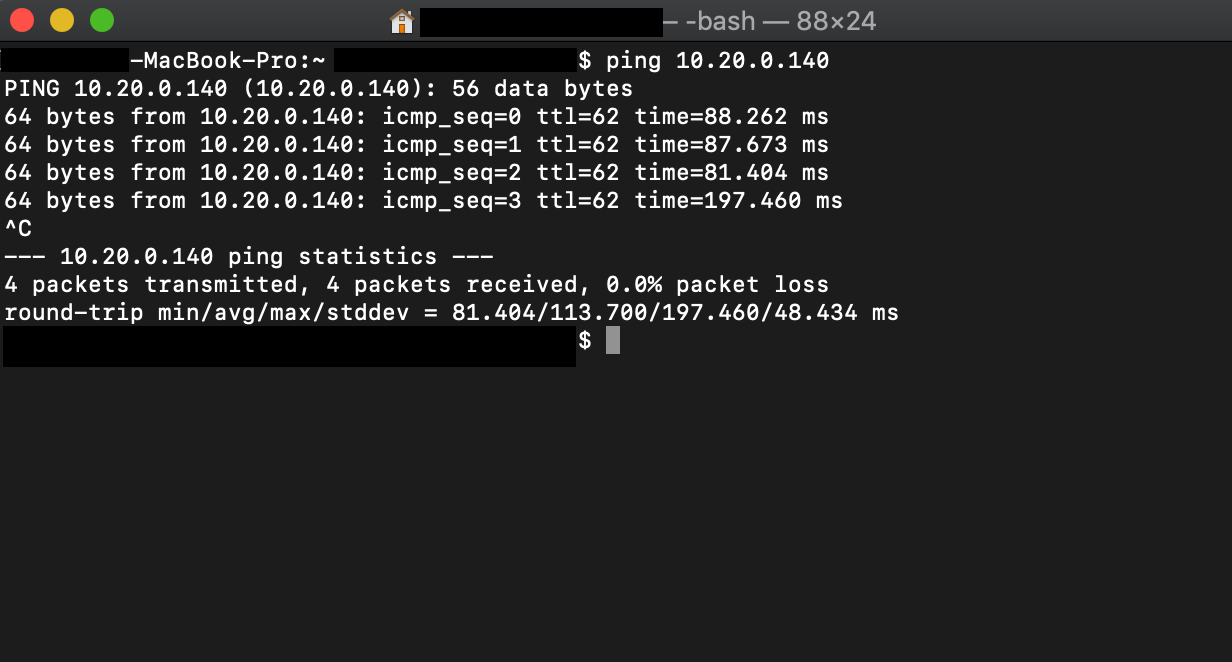
Now, open a terminal on your computer and see if you can ping the EC2 instance using its private IP address. If you are connected to the Aviatrix VPN Client, you should see a response.
-
To check, disconnect from the Aviatrix VPN Client. You should not see a response.
See below for an example of a proper ping response.
Last Steps
One last option for configuration is under Step 3 of this guide, "Connection Policies".
-
As a test, remove either the Dev or Prod Domain from the "Connected" list.
-
Remove Dev from the "Connected" list for the Shared Service Policy and run a Ping test. You should receive no response from the EC2 instance in the Development VPC.
OpenVPN is a registered trademark of OpenVPN Inc.