Multicloud Transit Integration with Azure VNG
Introduction
Currently, Aviatrix Multicloud Transit solution requires encryption over Azure ExpressRoute or External Device to on-prem directly. There are times where encryption is not required and native network connectivity on ExpressRoute is highly desirable. In such scenarios, Aviatrix Transit solution including Transit FireNet can only forward traffic between Spoke VNets or inspect east-west traffic only, as shown with these Azure Transit Network design patterns.
This feature allows Aviatrix Multicloud Transit solution to integrate with native Azure Virtual Network Gateway (VNG) and enables Aviatrix Transit Gateway to inspect traffic from on-prem to cloud in addition to east-west and egress traffic inspection. Both native Spoke VNet and Aviatrix Spoke Gateway based Spoke VNets are supported.
The key ideas for this solution are:
-
The edge (WAN) router runs a BGP session to Azure VNG via Azure ExpressRoute or VPN where the edge router advertises to the Azure VNG the on-prem routes and the VNG advertises the Spoke VNet CIDRs.
-
Aviatrix Controller periodically retrieves route entries from the Transit VNet VNG route table advertised from on-prem. The Controller then distributes these routes to Spoke VNet and Aviatrix Transit Gateway.
-
Azure native VNet Peering is configured between each Spoke VNet and Transit VNet VNG with Allow Remote Gateway attribute configured on the Spoke VNet to automatically advertise routes from Spoke VNet to VNG and to On-prem.
-
Traffic coming from on-prem to VNG is routed to the Azure Load Balancer which then forwards traffic to both Aviatrix Transit Gateways for Active-mesh deployment. The same Load Balancer is also used to distribute traffic to firewalls for inspection.
-
Traffic coming from Spoke VNet is routed to Aviatrix Transit Gateway directly which then forwards the traffic to the Azure Load Balancer. Future release will support ActiveMesh in this direction of traffic.
This document describes the configuration workflow for the following network diagram.
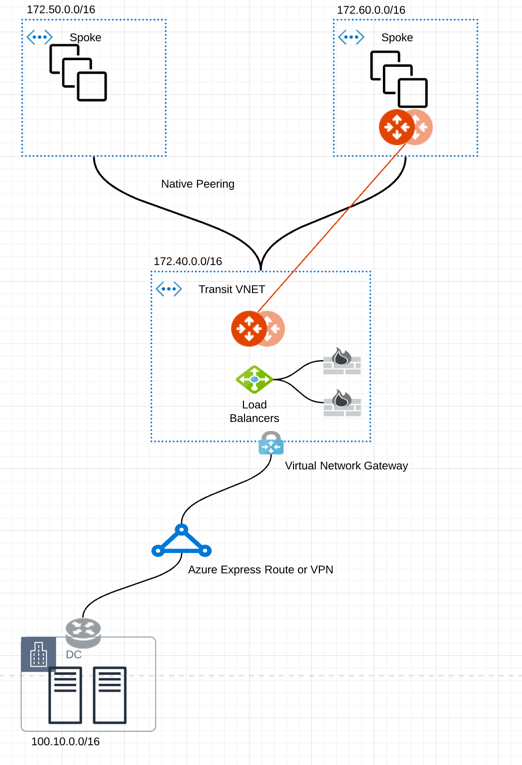
where there are two Spoke VNets, one with Aviatrix Spoke Gateway (172.60.0.0/16) and one native Spoke VNet (172.50.0.0/16).
Prerequisite
Upgrade Aviatrix Controller to the latest version.
| We highly recommend creating an Azure Transit VNET with Aviatrix FireNet VNet option enabled. Create a VNG in this Transit VNet. |
Connecting VNG on On-Prem
If you have already created VNG in Transit VNet, skip this section.
Building Azure ExpressRoute is customer’s responsibility. For more information about Azure ExpressRoute, please check out the below documents:
-
Refer to Azure ExpressRoute.
-
Refer to ExpressRoute documentation for more info.
-
Refer to Equinix ECX Fabric Microsoft Azure ExpressRoute if users select Equinix solution. This is just an example here.
Adjust the topology depending on your requirements.
Follow the steps below to set up this configuration workflow.
-
Create an ExpressRoute circuit. See Tutorial: Create and modify an ExpressRoute circuit.
-
Create Azure private network for an ExpressRoute circuit. See the private peering section in Create and modify peering for an ExpressRoute circuit.
-
Create a VNG in Transit VNet with Aviatrix FireNet VNet option enabled. Note that this step may take up to 45 minutes to complete. See Configure a virtual network gateway for ExpressRoute using the Azure portal for more information.
-
Connect a virtual network to an ExpressRoute circuit. See Connect a virtual network to an ExpressRoute circuit using the portal.
-
Check ExpressRoute Circuits - List Routes Table on the Azure portal.
Connect Aviatrix Transit Gateway with VNG
Refer to Global Transit Network Workflow Instructions for the below steps. Please adjust the topology depending on your requirements.
Deploying an Aviatrix Multicloud Transit Gateway and HA in Azure
-
Deploy the Transit Aviatrix Gateway and enable HA with High Performance Encryption (HPE) mode enabled in Azure Transit VNET. HPE mode is not required but an optional feature to increase throughput.
-
Instance size of at least Standard_D5_v2 will be required for High Performance Mode Encryption for higher throughput. Please refer to ActiveMesh HPE Performance Benchmark for performance details.
-
Enable Transit FireNet Function.
Connecting Transit FireNet Gateway to VNG
This step assumes VNG is already deployed in the Transit VNet.
-
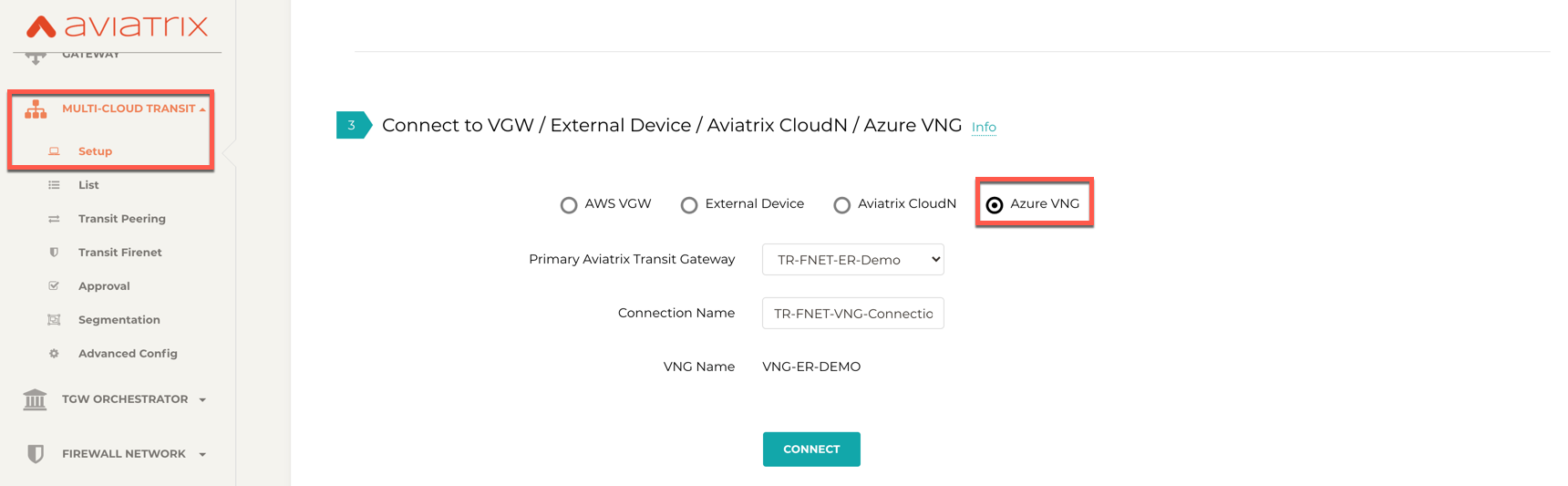
Go to Multi-Cloud Transit > External Device tab.
-
Select Azure VNG radio button.
-
Select Primary Aviatrix Transit Gateway in the dropdown menu. Note if VNG has not been deployed in the Transit VNet, this step cannot complete.
-
VNG Name will populate automatically. Click Connect.
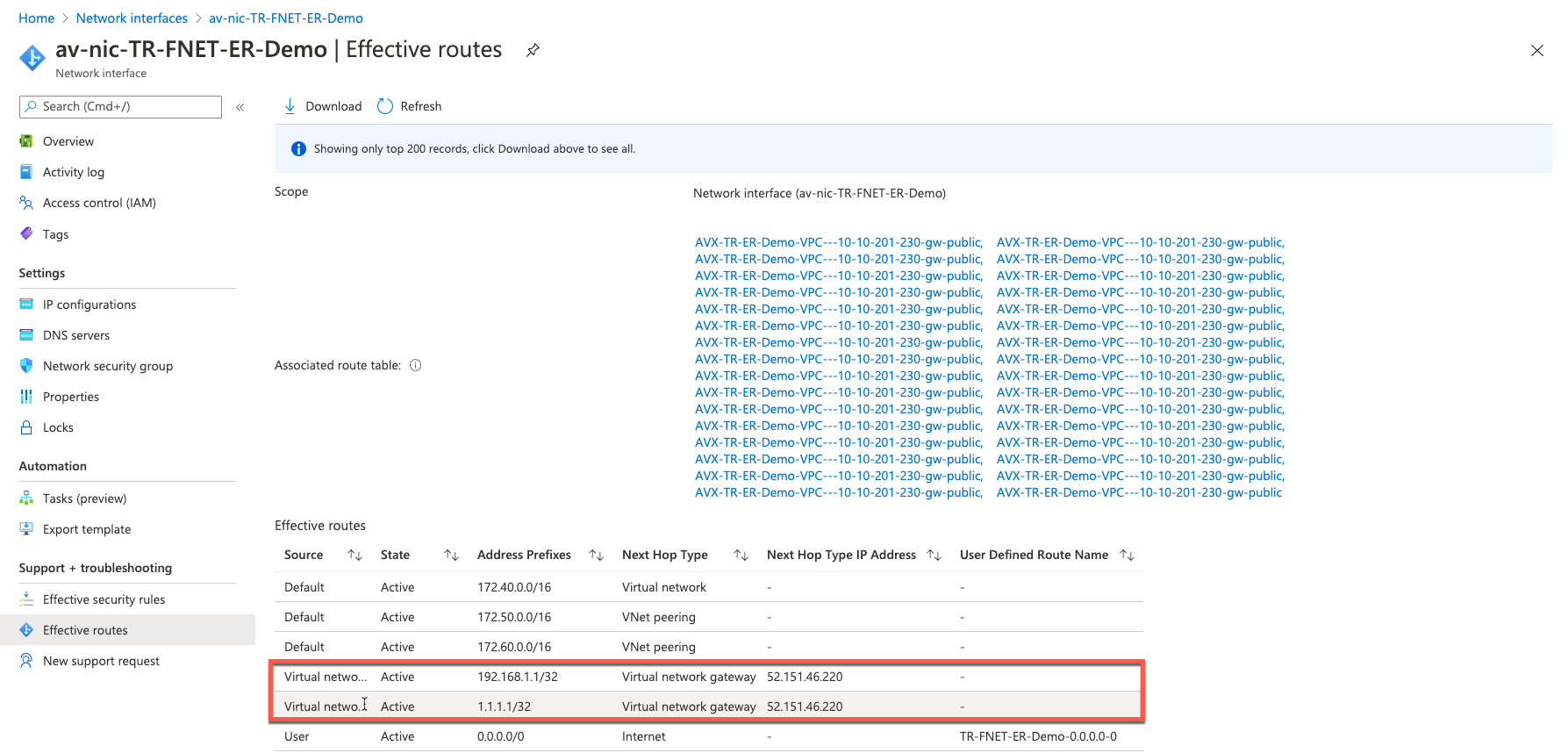
Checking Effective Routes Info on Azure Portal
-
Log in to the Azure portal and search for "Network interfaces" on the search bar.
-
Select Aviatrix Transit Gateway’s interface.
-
Navigate to the "Effective routes" page by selecting Effective routes under the Support + troubleshooting section.
-
Check route entry for On-prem pointing Next Hop Type Virtual network gateway.
Attach Spoke VNet to Aviatrix Transit Gateway
-
Deploy Aviatrix Spoke Gateway in Spoke VNet. Create an Azure VNET for Aviatrix Spoke Gateway by using the Aviatrix feature Create a VNG in Transit VNet or manually deploy it in cloud portal or feel free to use existing virtual network.
-
Follow this step Deploy Spoke Gateways to launch Aviatrix Spoke Gateway and enable HA with insane mode enabled in Azure Spoke VNET. Insane mode is optional. An instance size of at least Standard_D5_v2 will be required for High Performance Encryption Mode Encryption for higher throughput. Please refer to ActiveMesh HPE Performance Benchmark for performance details.
-
Attach Spoke Gateways to Transit Network.
-
Follow this step Attach Spoke Gateways to Transit Network to attach Aviatrix Spoke Gateways to Aviatrix Transit Gateways in Azure
-
Follow step Attach Native Azure VNET to Transit Network to attach Azure Native VNET Spoke to Aviatrix Transit Gateway.
-
Ready to Go
Now you should be able to send traffic from cloud to on-prem as well as on-prem to cloud over Azure Express Route.
For FireNet deployment, follow the Transit FireNet workflow.