Multicloud Transit Gateway Peering over Private Network Workflow
Aviatrix Transit Gateway Peering over Private Network feature expands Transit Gateway peering to across multiclouds where there is a private network connectivity between the cloud providers via on-prem or a co-location. This enables customers to build high performance data networks while ensuring data privacy by encrypting data in motion.
The solution applies to AWS Direct Connect, Azure ExpressRoute, and Google Cloud Interconnect for the cloud to on-prem connectivity.
This document describes a step-by-step instruction on how to build Aviatrix Transit Gateway Peering with Private Network over AWS Direct Connect and Azure ExpressRoute for R6.2 and later releases. In this note, you learn the following:
-
Workflow on building underlay connectivity for private network with AWS Direct Connect
-
Workflow on building underlay connectivity for private network with Azure ExpressRoute
-
Workflow on Aviatrix Transit Gateway Peering with private network
|
Topology
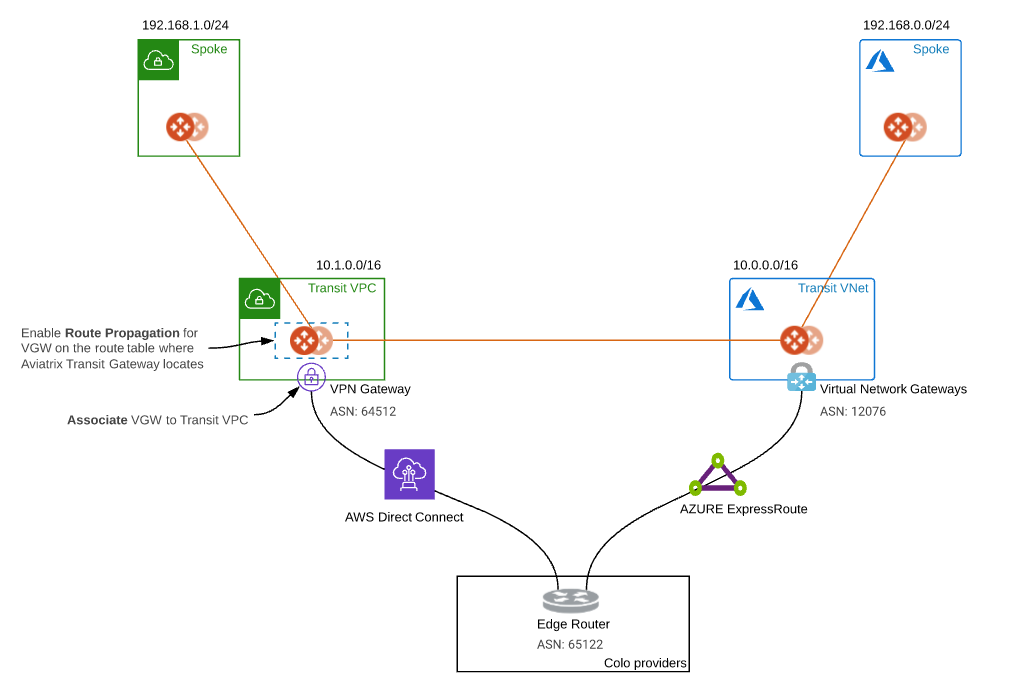
The key ideas for this solution are:
-
The edge (WAN) router runs a BGP session to AWS VGW via AWS Direct Connect where the edge router advertises the Azure Transit VNET CIDR and the AWS VGW advertises the AWS Transit VPC CIDR.
-
The edge (WAN) router runs a BGP session to Azure VNG via Azure ExpressRoute where the edge router advertises the AWS Transit VPC CIDR and the Azure VNG advertises the AZURE Transit VNET CIDR.
-
The edge (WAN) router redistributes AWS Transit VPC CIDR and AZURE Transit VNET CIDR.
-
Once the reachability between two cloud transits over private network is there, user is able to deploy Aviatrix Multi Cloud Global Transit Gateway Encrypted Peering over Private Network
|
Prerequisite
Upgrade Aviatrix Controller to the latest version.
In this example, we are going to deploy the below VPCs in AWS and Azure
-
AWS Aviatrix Transit VPC (i.e. 10.1.0.0/16)
-
AWS Aviatrix Spoke VPC (i.e. 192.168.1.0/24)
-
Azure Aviatrix Transit VNET (i.e. 10.0.0.0/16)
-
Azure Aviatrix Spoke VNET (i.e. 192.168.0.0/24)
Workflow on building underlay connectivity for private network with AWS Direct Connect
Building AWS Direct Connect is customer’s responsibility. For more information about AWS Direct Connect, please check out the below documents:
-
Refer to Connect Your Data Center to AWS
Please adjust the topology depending on your requirements.
Step 1.1. Build AWS Direct Connect
-
Refer to Equinix ECX Fabric AWS Direct Connect if users select Equinix solution. This is just an example here.
Step 1.2. Associate AWS VGW to AWS Transit VPC
-
Login AWS VPC Portal
-
Click the hyperlink "Virtual Private Gateways" under sidebar "VIRTUAL PRIVATE NETWORK (VPN)"
-
Select the Virtual Private Gateway that you have the private virtual interface to AWS Direct Connect
-
Click the button "Actions"
-
Click the hyperlink "Attach to VPC"
-
Select the AWS Transit VPC and click the button "Yes, Attach"
Workflow on building underlay connectivity for private network with Azure ExpressRoute
Building Azure ExpressRoute is customer’s responsibility. For more information about Azure ExpressRoute, please check out the below documents:
-
Refer to Azure ExpressRoute
-
Refer to ExpressRoute documentation for more info
-
Refer to Equinix ECX Fabric Microsoft Azure ExpressRoute if users select Equinix solution. This is just an example here.
Please adjust the topology depending on your requirements.
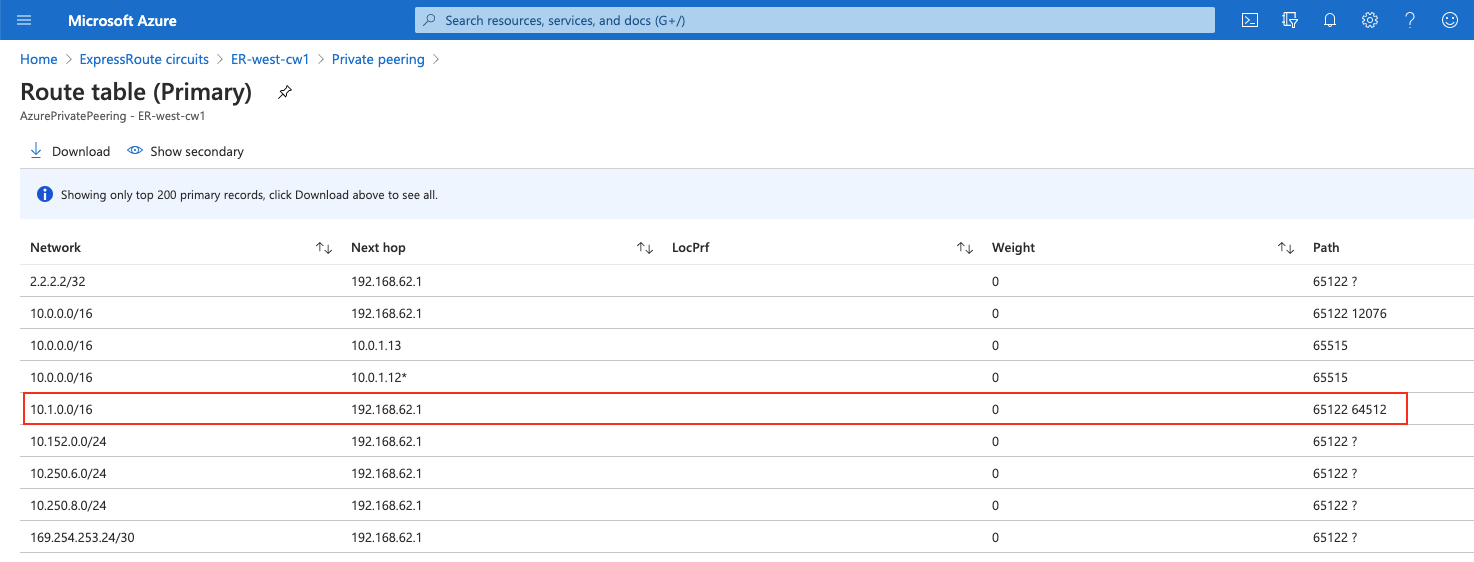
Step 2.5. Check Express Route Circuits - List Routes Table on Azure portal
-
Login Azure Portal
-
Search for "ExpressRoute circuits" on the search bar
-
Select the "ExpressRoute circuits" that you created
-
Select the Azure private peering row
-
Click on the hyperlink "Get route table"
-
Check whether AWS Transit VPC’s CIDR with the ASN Path of edge router and AWS VGW
Workflow on Aviatrix Transit Gateway Peering with private network
Refer to Global Transit Network Workflow Instructions and Aviatrix Transit Gateway Encrypted Peering for the below steps. Please adjust the topology depending on your requirements.
Step 3.1. Deploy VPCs for Transit FireNet
-
Create AWS Transit VPC and Azure Transit VNET by utilizing Aviatrix feature Create a VPC with Aviatrix FireNet VPC option enabled
-
Create AWS Spoke VPC and Azure Spoke VNET by utilizing Aviatrix feature Create a VPC as the previous step or manually deploying it in each cloud portal. Moreover, feel free to use your existing cloud network.
Step 3.2. Deploy Aviatrix Multicloud Transit Gateway and HA in AWS
-
Follow this step Deploy the Transit Aviatrix Gateway to launch Aviatrix Transit gateway and enable HA with High Performance Encryption (HPE) mode enabled in AWS Transit VPC
-
Instance size of at least c5.xlarge will be required for High Performance Mode Encryption for higher throughput. Recommended minimum size for Transit in AWS is c5n.4xlarge. Please refer to this ActiveMesh HPE Performance Benchmark for performance detail.
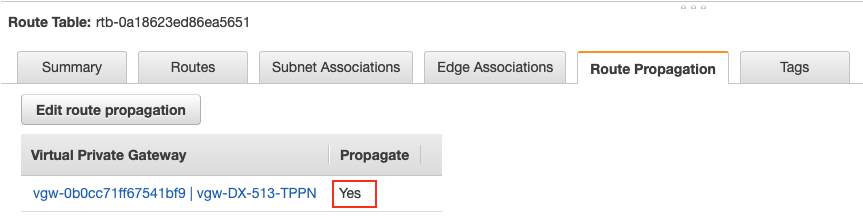
Step 3.3. Enable Route Propagation on the subnet route table where Aviatrix Transit Gateway locates on AWS portal
-
Login AWS VPC portal
-
Locate the subnet route table where Aviatrix Transit Gateway locates
-
Select the tab "Route Propagation"
-
Click the button "Edit route propagation"
-
Locate the AWS VGW that is associated with this Transit VPC and check the checkbox "Propagate"
-
Click the button "Save"
-
Check whether the Propagate status is Yes
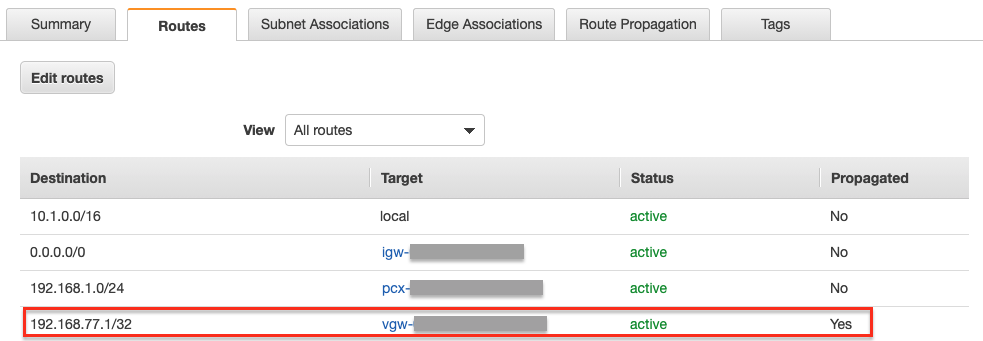
Step 3.4. Check route propagation info on AWS portal
-
Login AWS VPC portal
-
Locate the subnet route table where Aviatrix Transit Gateway locates
-
Select the tab "Routes"
-
Check whether there is a route entry "Azure Transit VNET’s CIDR pointing to AWS VGW"
Step 3.5. Deploy Aviatrix Multicloud Transit Gateway and HA in Azure
-
Follow this step Deploy the Transit Aviatrix Gateway to launch Aviatrix Transit gateway and enable HA with insane mode enabled in Azure Transit VNET
-
Instance size of at least Standard_D5_v2 will be required for High Performance Encryption Mode Encryption for higher throughput. Please refer to this ActiveMesh HPE Performance Benchmark for performance detail.
-
Enable Transit FireNet Function (optional)
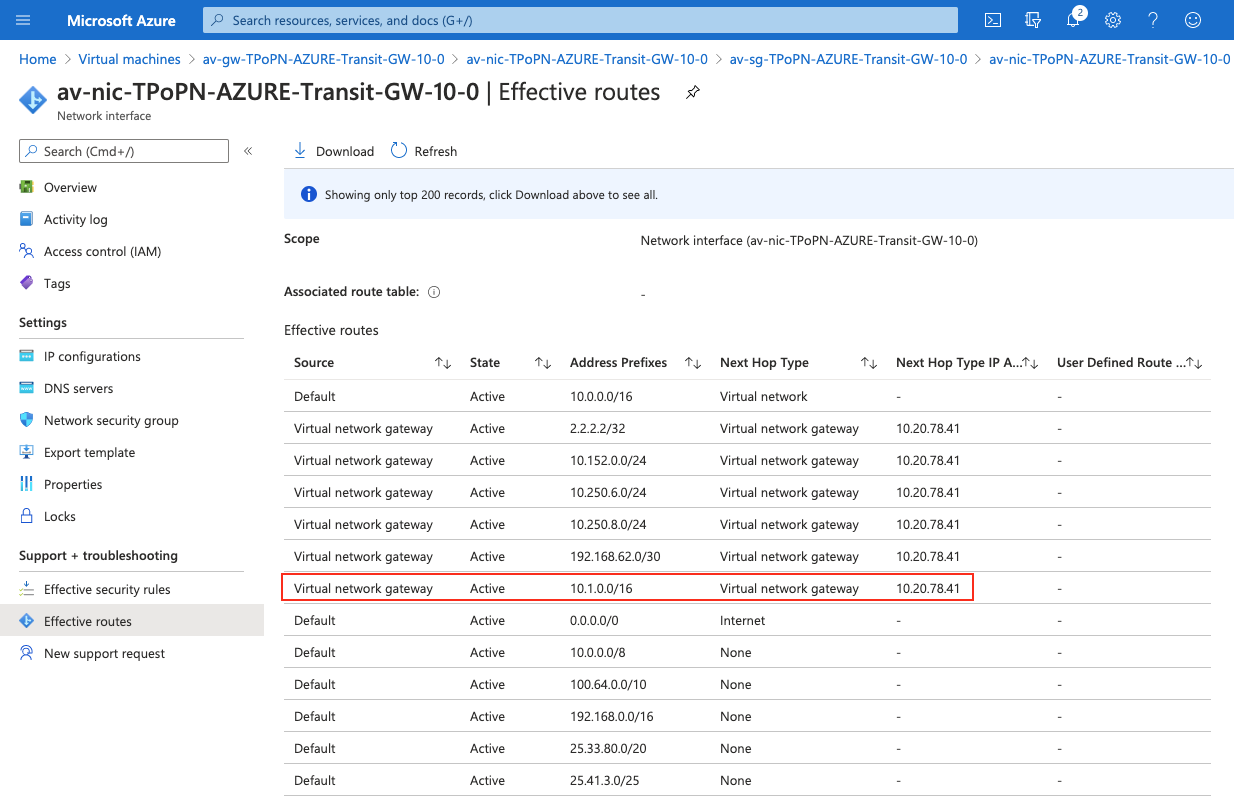
Step 3.6. Check Effective routes info on Azure portal
-
Login Azure Portal
-
Search for "Network interfaces" on the search bar
-
Select Aviatrix Transit Gateway’s interface
-
Navigate to the page "Effective routes" by clicking the link "Effective routes" under the section "Support + troubleshooting"
-
Check whether there is a route entry "AWS Transit VPC’s CIDR pointing to Next Hop Type Virtual network gateway"
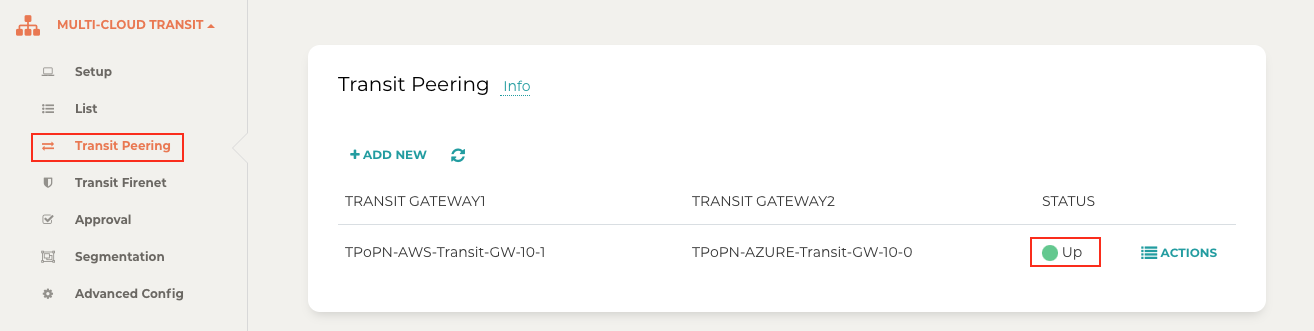
Step 3.7. Establish Transit Gateway Peering over Private Network
-
Navigate back to Aviatrix Controller
-
Go to MULTI-CLOUD TRANSIT → Transit Peering
-
Click the button "+ADD NEW"
-
Select "AWS Transit Gateway" as Transit Gateway1
-
Select "Azure Transit Gateway" as Transit Gateway2
-
Under Advanced options, check the option "Peering over Private Network"
-
(Optional) Under Advanced options, check the option Single-Tunnel mode if the underlying network is low speed (up to 4Gbps)
-
-
Click the button "OK"
-
Wait for a couple of minutes
-
Confirm the transit peering status is Up
Step 3.8. Deploy Spoke Gateway and HA
-
Follow this step Deploy Spoke Gateways to launch Aviatrix Spoke gateway and enable HA with High Performance Encryption Mode enabled in AWS Spoke VPC
-
Instance size of at least c5.xlarge will be required for High Performance Encryption Mode Encryption for higher throughput.
-
Follow this step Deploy Spoke Gateways to launch Aviatrix Spoke gateway and enable HA with insane mode enabled in Azure Spoke VNET
-
Instance size of at least Standard_D5_v2 will be required for High Performance Encryption Mode Encryption for higher throughput. Please refer to this ActiveMesh HPE Performance Benchmark for performance detail.
Step 3.9. Attach Spoke Gateways to Transit Network
-
Follow this step Attach Spoke Gateways to Transit Network to attach Aviatrix Spoke Gateways to Aviatrix Transit Gateways in AWS
-
Follow this step Attach Spoke Gateways to Transit Network to attach Aviatrix Spoke Gateways to Aviatrix Transit Gateways in Azure