Creating Static Routes for Routing of Traffic VPC to VPC
Packets to and from TGW VPCs, as well as on-premises, will be hairpinned off the LAN interface. As such, you need to configure appropriate route ranges that you expect traffic for packets that need to be forward back to TGW. For simplicity, you can configure the FW to send all RFC 1918 packets to LAN port, which sends the packets back to the TGW.
In this example, we configure all traffic for RFC 1918 to be sent out of the LAN interface.
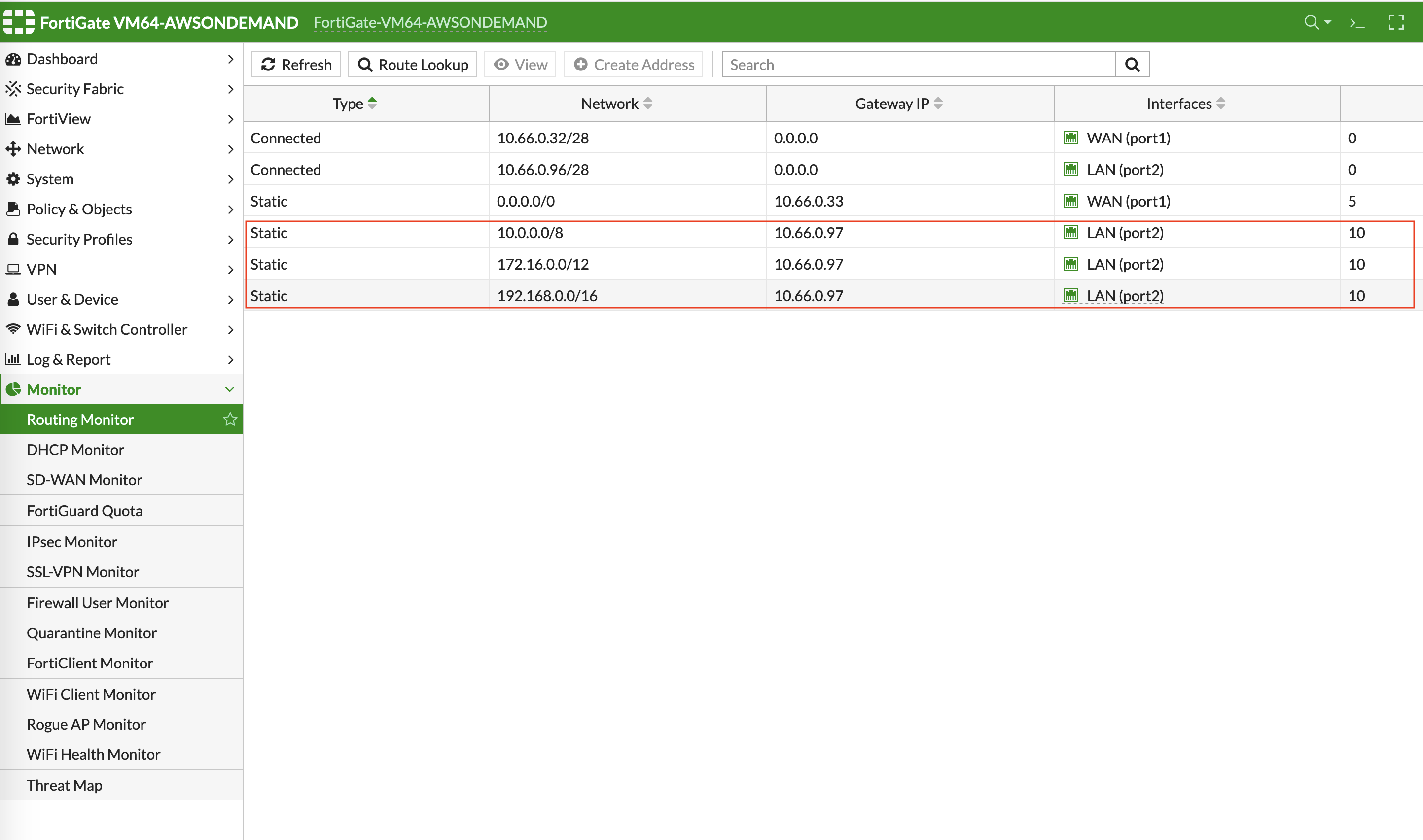
In the FortiGate UI, go to Network > Static Routes to create a Static Route as the following screenshot.
-
Click Create New.
-
Enter the destination route in Destination.
-
In Gateway Address, you will need to enter the AWS default gateway IP on subnet -dmz-firewall.
|
The subnet CIDR for -dmz-firewall is 10.66.0.96/28, thus the AWS default gateway IP on this subnet is 10.66.0.97. |
-
The interface will be the LAN (port2).
-
Configure an appropriate admin distance if you expect overlapping routes that need to be prioritized.
-
Enter comments as necessary.
-
Repeat the steps above for RFC 1918 routes.
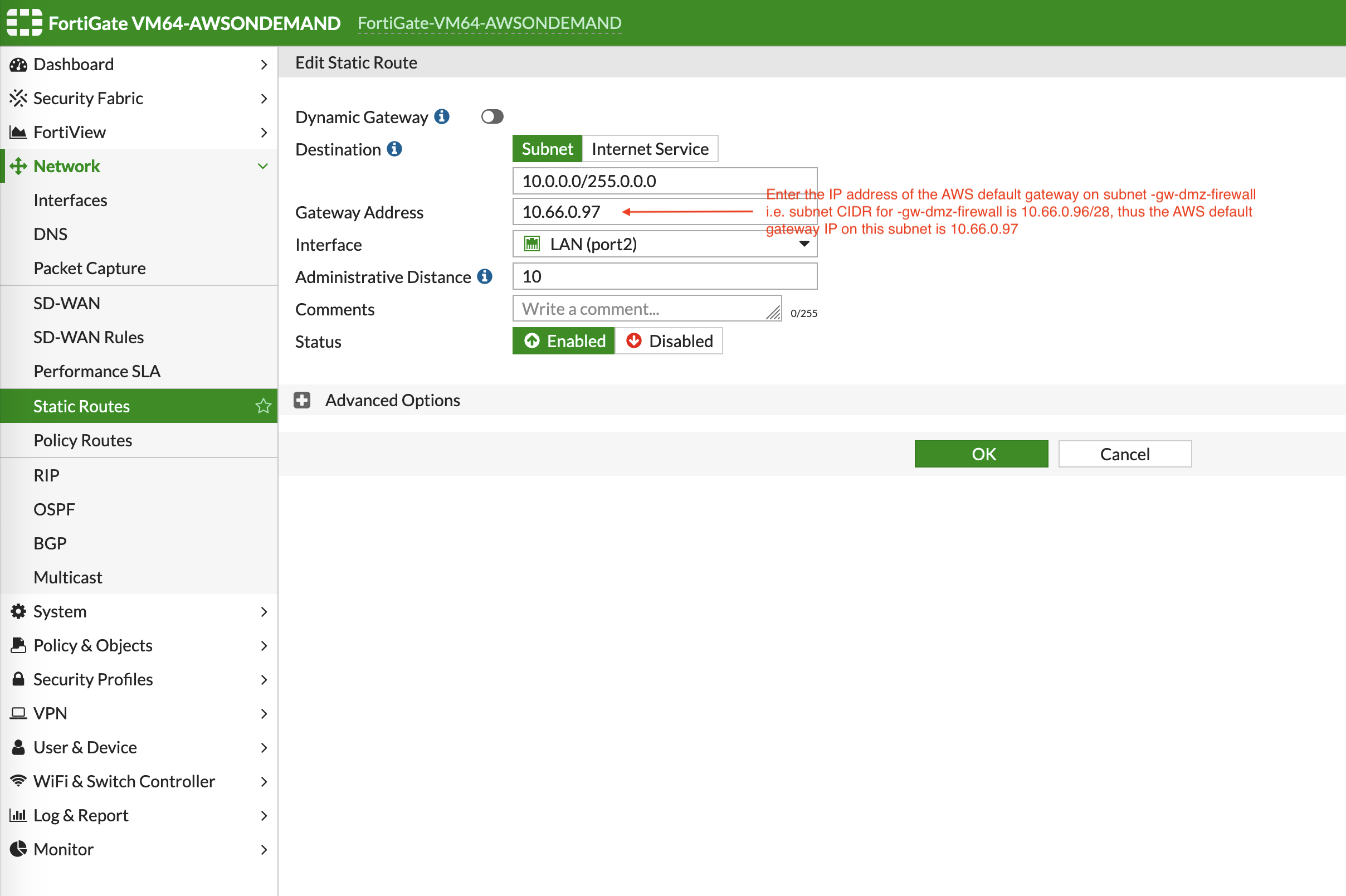
Those static routes can also be reviewed by navigating to Monitor > Routing Monitor.