Configuring FireNet Inspection Policies
| By default, FireNet inspects ingress and east-west traffic only. |
On the FireNet Gateways Policy tab you can add or remove inspection policies for the selected FireNet. When an inspection policy is added the traffic related to the Transit FireNet’s attachment (Spoke/Edge gateway, peered Transit, Site2Cloud external connection) is inspected by the firewall within the selected Transit FireNet.
|
You can add inspection policies for a FireNet if you have already attached one of the following to the Transit FireNet:
See Azure Spoke Subnet Groups to synchronize and add subnet groups for Spoke Gateways attached to Azure Transit FireNets. You cannot add subnet groups to a Spoke Gateway if it has inspection enabled. |
-
Navigate to Security > FireNet > FireNet Gateways and click a FireNet in the list.
-
Click the Policy tab. The list of attachments for that FireNet displays.
-
Select the attachments that you want to add for inspection.
-
From the Actions menu, select Add. The selected attachments now show On in the Inspection column.
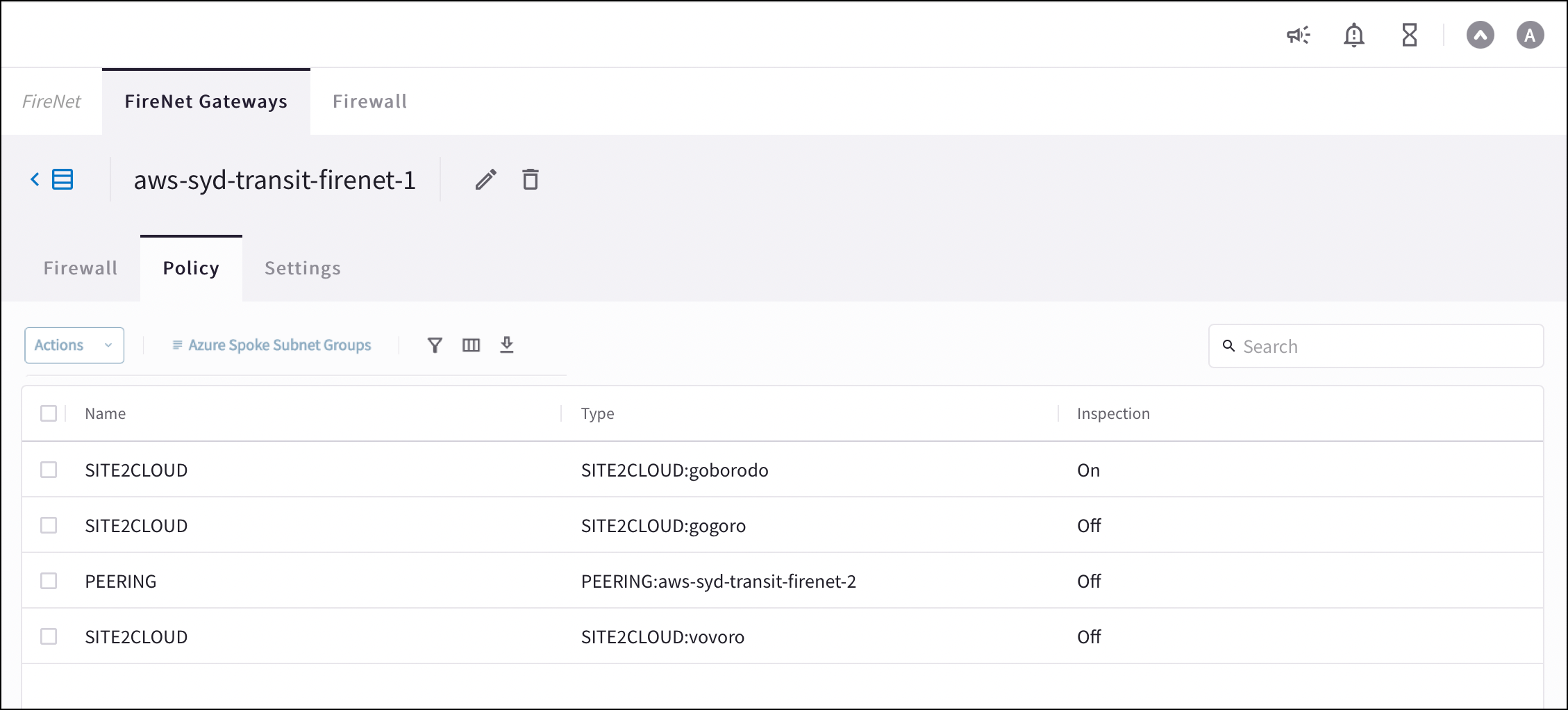
To remove an inspection policy, select the checkbox next to the attachment name, and then select Remove from the Actions menu.