Firewall Overview
FireNet supports three types of firewall vendors: Check Point CloudGuard, Fortinet FortiGate, and Palo Alto VM-Series. Panorama (firewall manager) is also supported for Palo Alto VM-Series firewalls. After you deploy firewalls you can view them on the Security > FireNet > Firewall tab. You can deploy firewalls from the Firewall tab, or you can import an existing cloud-deployed firewall.
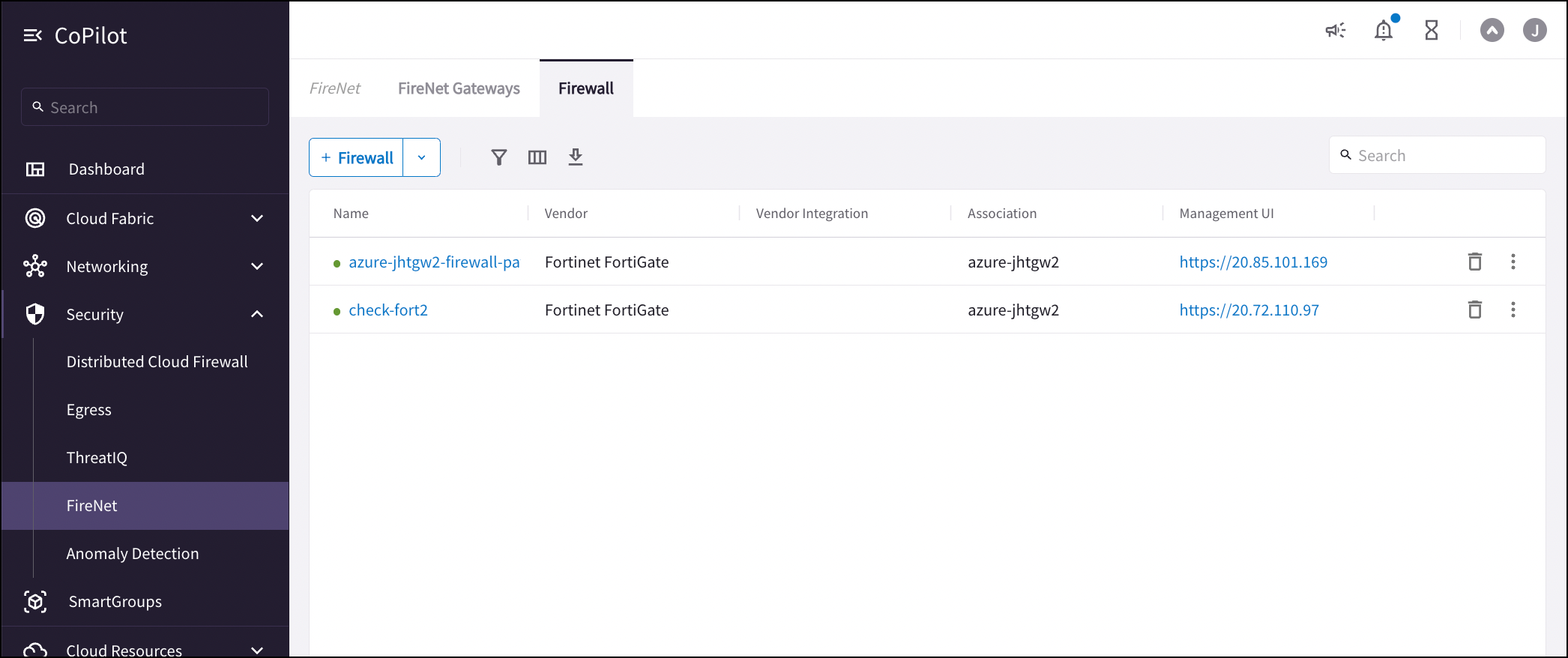
From here you can also:
-
Click the Management UI link to access the firewall UI and configure the firewall to check that FireNet traffic is flowing as expected. See the below examples for suggested configurations.
-
Click the name of the firewall to view firewall details.
| Any firewalls configured with password authentication do not allow for the downloading of the firewall access key. |
Palo Alto
| When configuring Palo Alto for AWS, you must download the access key to SSH into the firewall and change the password. |
You can use these example configuration documents to configure your Palo Alto VM-Series firewall in the following clouds.
| The Controller periodically issues Palo Alto API calls to find out if API can be issued successfully. This is used for route updating purposes, as firewall route updates requires API to work. If the Palo Alto API fails twice consecutively, the Controller declares the firewall is in Inaccessible state, but the firewall should still be attached and be able to forward traffic as long as its health checks pass. |
Fortinet FortiGate
You can use these example configuration documents to configure your Fortinet FortiGate firewall in the following clouds.