About External Connection Settings
The following are configuration settings for creating a Site2Cloud external connection, and general settings that you can configure after the Site2Cloud external connection is created.
About External Device Connection Settings
Connect Public Cloud to
Create a Site2Cloud external device Connection that uses BGP; a Static Route-Based or Static Policy-Based (Mapped or Unmapped) connection; or an AWS VGW/Azure VNG connection.
For the Static options, you should select Unmapped (any Static option not marked as Mapped) unless the Local Subnet and the Remote Subnet overlap. Then you must select a Mapped connection.
Local Subnet CIDR(s)
The CIDR(s) of the Local Gateway selected in this Site2Cloud external connection (the name changes to Real Local Subnet CIDR(s) if a Mapped connection is selected).
Remote Gateway Type
Select the gateway type of the Site2Cloud external connection.
You should select 'Generic' for most connections (used for most third-party routers and firewalls). Select 'Aviatrix' if you are terminating on an Aviatrix CloudN on-premise gateway.
Any other Remote Gateways listed here are only valid with Controller version 6.7 or lower. These other Remote Gateway types are:
| Field | Description |
|---|---|
AWS VGW |
For terminating on an AWS Virtual Private Gateway. |
Azure VPN |
For terminating on Azure VPN Services. |
SonicWall |
For terminating on a SonicWall firewall. |
Remote Subnet CIDR(s)
The CIDR(s) of the remote gateway selected in this Site2Cloud external connection (the name changes to Real Remote Subnet CIDR(s) if a mapped connection is selected).
Virtual Local Subnet CIDR(s) (Mapped connections only)
Virtual local network CIDRs that are mapped to the real local subnet.
Virtual Remote Subnet CIDR(s) (Mapped connections only)
Virtual remote network CIDR(s) that are mapped to the real remote subnet.
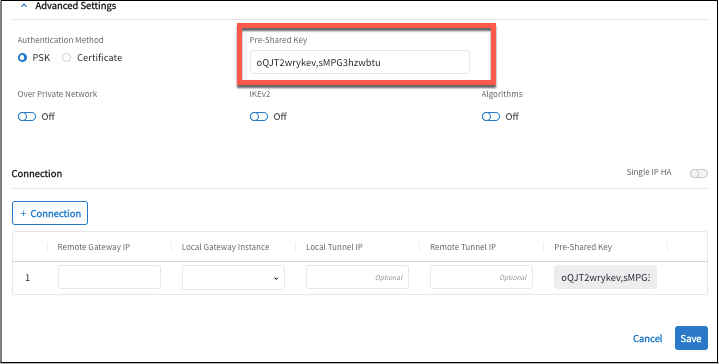
Authentication Method
You can authenticate the connection using Pre-Shared Key (PSK) or certificate-based authentication. This is applicable for Static Route-Based and Static Policy-Based Mapped and Unmapped external connections.
Certificate-Based
You can only select this option if a remote CA certificate has been uploaded or imported.
Do the following after uploading or importing a remote CA certificate:
-
In the first Connection row in the Add External Connection dialog, enter the SAN of the certificate in the first Remote Identifier SAN field
-
(if HA is enabled on the remote gateway) Add a second Connection row and enter the SAN of the remote HA gateway in the second Remote Identifier SAN field
Then, when creating your external connection, you enter the SAN of the certificate in the first Remote Identifier SAN field (under Connection in the Add External Connection dialog). If HA is enabled for the selected remote gateway (click +Connection to add another row) you also enter the SAN of the HA remote gateway in the second Remote Identifier SAN field.
The SAN (Subject Alternative Name) is a way to indicate that multiple domains can be secured by the same certificate.
Pre-Shared Key
A string of random characters that is used to authenticate the IPsec tunnel connection between the Aviatrix Gateway and your on-premise router or firewall. You must ensure that this key is the same as the Pre-Shared Key that is configured for your on-premise firewall or router. If you do not specify one, it is auto-generated. You can view the auto-generated PSK value when you download the external connection’s configuration, and copy it to use when configuring your on-premise router or firewall. See Aviatrix Gateway to FortiGate for an example.
For Site2Cloud ActiveMesh connections, where both the local Aviatrix Gateway and remote on-premise router or firewall have high availability (HA) enabled, four IPsec tunnels are created (Local gateway to remote router/firewall, local HA gateway to remote router/firewall, local gateway to remote HA router/firewall, local HA gateway to remote HA router/firewall). If you want the tunnels that are created to have different PSK values, you will need to enter the PSKs separated by a comma.
|
Local ASN (BGP connections only)
The BGP AS number the Transit GW will use to exchange routes with the external device.
Remote ASN
When BGP is selected, the BGP AS number the external device will use to exchange routes Aviatrix Transit GW.
Over Private Network (all connections except BGP over LAN)
Select this option if your underlying infrastructure is a private network, such as AWS Direct Connect or Azure ExpressRoute. See the "How does it work" section for more details. When this option is selected, BGP and IPsec run over private IP addresses.
IKEv2 (all connections except BGP over GRE and BGP over LAN)
Select the option to connect to the remote site using IKEv2 protocol.
| If you configure IKEv1 in a Site2Cloud connection that uses certificate-based authentication and is connecting to another Aviatrix device, you must add the intermediate CAs in addition to the root CA. When an intermediate CA is renewed and re-authentication is attempted, the Site2Cloud connection will go down until you add the new certficate. |
Algorithms (not applicable for BGP over GRE, BGP over LAN)
Aviatrix-supported encryption algorithms. If this is turned on, you can configure the following algorithms:
-
Phase 1 Authentication: default is SHA-256
-
Phase 1 DH Groups: default is 14
-
Phase 1 Encryption: default is AES-256-CBC
-
Phase 2 Authentication: default is HMAC-SHA-256
-
Phase 2 DH Groups: default is 14
-
Phase 2 Encryption: default is AES-256-CBC
Single IP HA
Enable this setting to set up High Availability (HA) instances for each new connection that can go up if the primary instance goes down. When active, each standby instance will use the same IP address as the remote connection.
Gateway Learned CIDR Approval
An approval process for gateway-learned CIDRs. When this is On:
-
An email notification is sent to the administrator to approve the learned CIDRs before they are propagated to the Spoke VPC/VNet route table.
-
You can also add pre-approved CIDRs on the Approval tab.
Local Gateway Instance (not applicable for BGP connections or Static Route-Based ActiveMesh)
The instance on the local gateway.
Local Tunnel IP
Optional parameter. This field is for the tunnel inside IP address of the Transit Gateway. Leave it blank.
About External Connection General Settings
You access a Site2Cloud connection’s settings in CoPilot by going to CoPilot > Networking > Connectivity > External Connections (S2C) tab, then select the connection and go to the connections’s Settings tab.
Active-Active HA
Allow gateways to support Active-Active mode where both tunnels are up and packets are routed to both gateways via respective VPC/VNet route tables.
To enable this, slide the toggle switch to turn it On.
Forward Traffic to Transit Gateway (Static Route-Based Mapped Only)
Typically you enable the Forward Traffic to Transit Gateway option when you have a connection that has overlapping CIDRs. This forwarding ensures that traffic is sent between on-prem routers and local Spoke and Transit gateways.
In most cases you will enable this so that your on-premise traffic is forwarded.
Jumbo Frame
Jumbo Frame improves Aviatrix Gateway throughput performance.
|
Dead Peer Connection
Dead Peer Detection (DPD) is a standard mechanism (RFC 3706) between IPsec tunnels to send periodic messages to ensure the remote site is up.
By default DPD detection is enabled.
Field |
Value |
Description |
Delay |
>= 1 |
Keepalive timer (in seconds) |
Retry Delay |
>= 1 |
How long should the tunnel wait before declaring keep alive failed. (in seconds) |
Maxfail |
>= 1 |
Number of tries before considering the peer is dead. |
Local Gateway Identifier
By default, Aviatrix configures gateway’s public IP as the Local Identifier. You can adjust these settings to your gateway’s private IP.
Remote Identifier SAN
Aviatrix only supports IP_ADDRESS and KEY_ID as the IKE identity type for the remote identifier in the pre-shared key authentication. The IP_ADDRESS must be a valid IPv4 IP address. The KEY_ID is a remote device ID during the key authentication. <should this be in the description for Remote Gateway IP?>
By default, Aviatrix configures the public IPv4 address of the peer device as the Remote Identifier for pre-shared key authentication. You can adjust this setting to the private IPv4 address of the peer device.