Building Site to Site IPsec VPN Connection
You can use Aviatrix gateways to connect one site to another. This solution requires one Aviatrix gateway in each location that needs to be connected. These on-premise gateways can be deployed as virtual machines on VMware, KVM or Hyper-V.
Environment Requirements
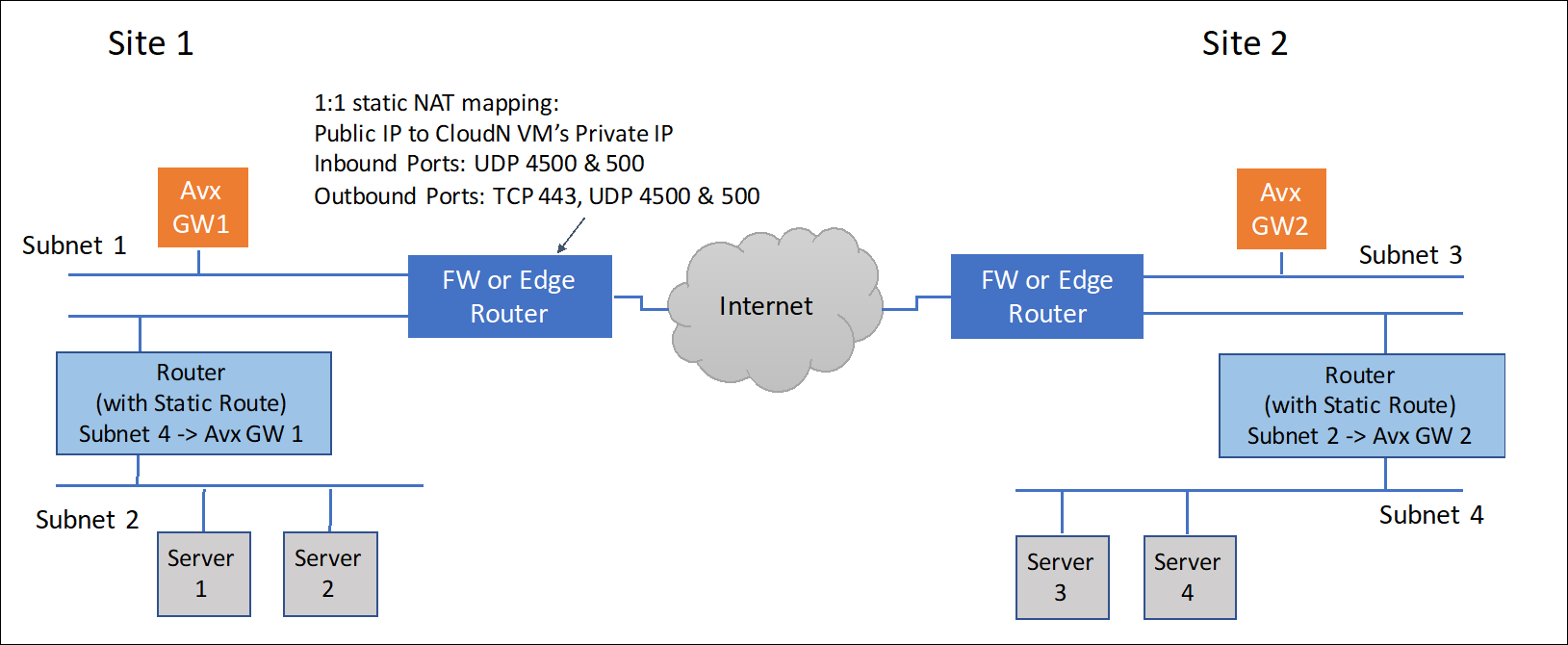
An Aviatrix Site to Site IPSEC tunnel is accomplished by one gateway initiating the session with the other gateway. For this to work at least one of the Aviatrix virtual appliances needs to be accessible via a public IP address. This can be accomplished by setting up the public IP address on the edge router in the on-premise network and configuring NAT from that public IP address to the Aviatrix VM with a 1-1 IP address NAT. The only ports that need to be forwarded from the edge router to the VM are UDP ports 500 and 4500.
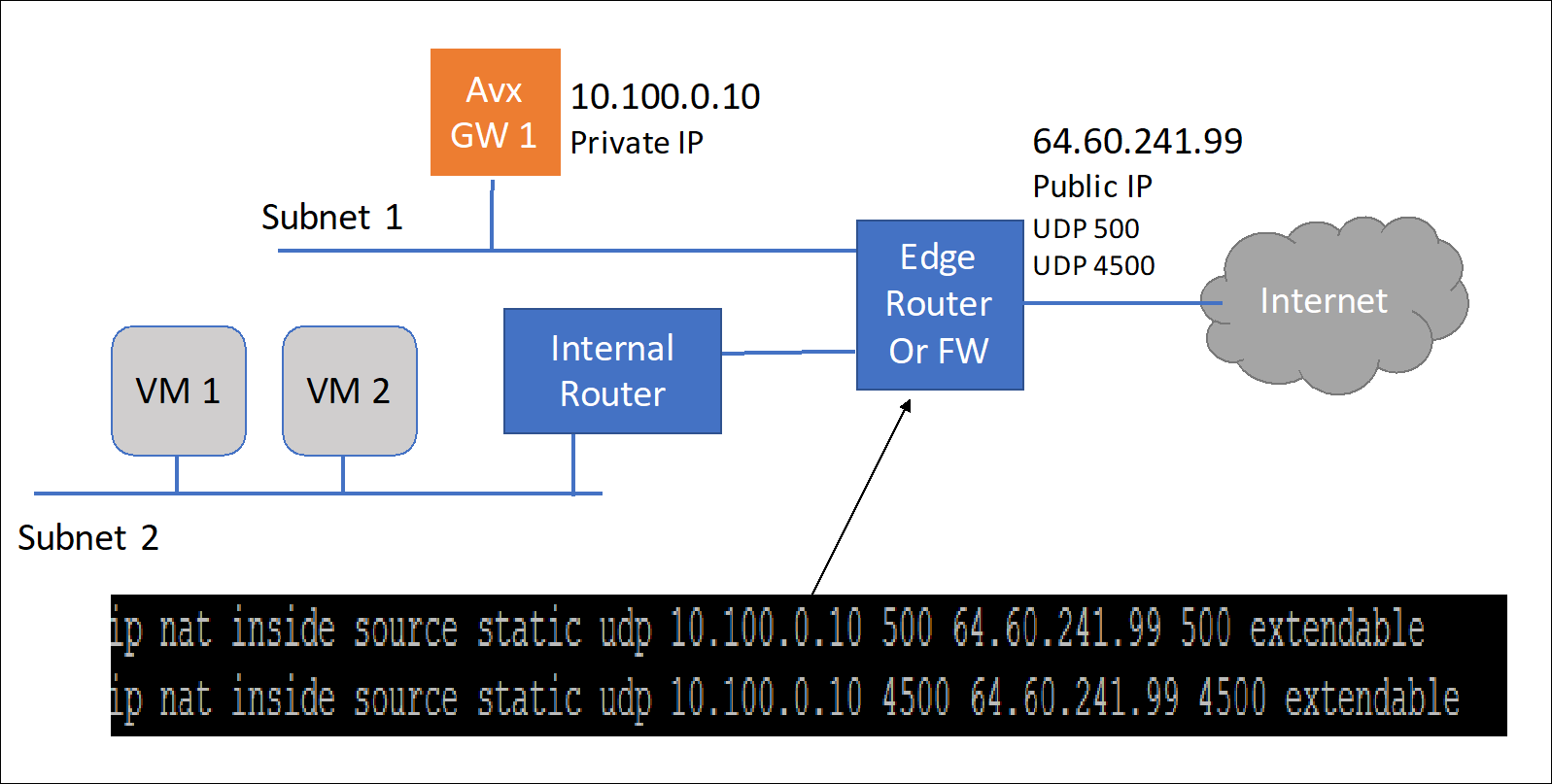
On the other site, the second gateway does not need a public IP assigned to the Aviatrix gateway. This second gateway will reach outbound to the first Aviatrix GW (GW1).
The last requirement is to configure static routes in the internal routers (default gateway of the Aviatrix VM) in both sites. This static route should send traffic destined for the other site to the Aviatrix GW as the next hop.
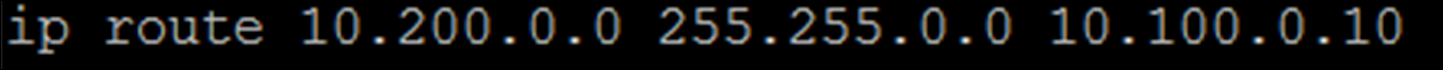
Steps to Configure IPSec connectivity
-
Install an Aviatrix gateway in each site.
-
Configure an external connection (Site2Cloud) in Gateway 1.
|
In the Aviatrix terminology, Site2Cloud is the name of the feature that enables connections from one site (or datacenter) to other sites (including cloud environments). |
-
In CoPilot, go to Networking > Connectivity > External Connections (S2C) and click +External Connection to create a Site2Cloud connection using the values for one of the below options (for either you can select either PSK or certificate-based authentication).
-
Use these table values:
Field Description Connect Public Cloud to
External Device: Static Route-Based (Unmapped) or Static Policy-Based (Unmapped)
Local Gateway
The Gateway 1 gateway created above
Local Subnet CIDR(s)
The CIDR(s) in the local site
Remote Gateway Type
Aviatrix
Remote Subnet CIDR(s)
The CIDR(s) of the other site
Pre-Shared Key
Can leave blank; will be pre-populated
Remote Gateway IP
The public IP of the other site
-
Click Save. The connection is listed on the External Connections (S2C) tab.
-
Log in to Gateway 2’s CoPilot on the other site (GW2).
-
On the Networking > Connectivity > External Connections (S2C) tab, add a new connection using the downloaded configuration information above. This will start the IPsec negotiations between both gateways.
You can check the status of the connection at Diagnostics > Cloud Routes > External Connections.