About Gateway High Availability
This document provides an overview of the high availability configuration options for Aviatrix Transit and Spoke Gateways.
About Highly Available Gateway Configuration
Aviatrix High Availability feature supports multiple gateway instances in a VPC or VNet for high availability and scalability, to minimize and reduce network downtime and improve network stability and performance to mitigate packet loss.
In this configuration, a Gateway can consist of multiple gateway instances. All gateway instances are in Active-Active mode. Network traffic flow is load balanced to all the gateway instances in that VPC or VNet.
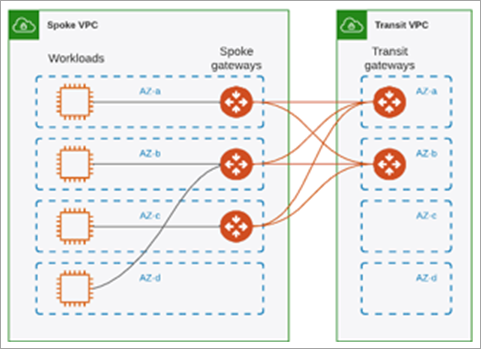
Aviatrix Gateways must have at least two gateway instances to be highly available.
-
Transit Gateways can have only 2 gateway instances.
-
Spoke Gateways can have up to 15 gateway instances.
A Spoke Gateway can have only one gateway instance in the following scenarios.
-
A Spoke Gateway with BGP connection(s).
-
A Spoke Gateway with Site2Cloud or customized SNAT and DNAT enabled.
-
About Active-Standby External Connection Configuration
Active-Standby high availability mode is supported for Aviatrix Transit and BGP-enabled Spoke Gateway external connections where the external device, such as an on-premises firewall, does not support asymmetric routing on two tunnels.
Active-Standby mode applies to both BGP and Static Remote Route Based external device connections and for each connection, only one tunnel is active in forwarding network traffic at any given time.
| Active-Standby mode can only be applied to external connections without HA enabled. |
In an Active-Standby configuration, a Gateway consists of two gateway instances, one with active peering and the other with standby peering connection to the external device. Only the active peering connection forwards and receives network traffic to and from the external device. The network switches to the standby peering connection when the active peering connection is down.
When Active-Standby is enabled for a Transit or BGP-enabled Spoke Gateway and the Gateway has multiple external connections, then the setting applies to all applicable connections.
You can set Active-Standby mode in the Gateway’s Settings.
See:
How Aviatrix Handles Automatic Failover
The Aviatrix Controller monitors your cloud network deployment and when it detects a gateway is down, it automatically handles failover.
When highly available gateway instances are deployed and the Aviatrix Controller detects a gateway instance is down, it automatically switches to and directs traffic flow to the other active gateway instances in that VPC or VNet.
When a Transit or BGP-enabled Spoke Gateway is deployed with Active-Standby external connection(s) and the Aviatrix Controller detects that the active peering connection is down, it automatically switches to and directs traffic flow to the standby peering connection.
Creating Highly Available Gateway Instances
Aviatrix Gateways must have at least two gateway instances to be highly available. By default, gateway instances are created in Active-Active mode.
-
Transit Gateways can have only 2 gateway instances.
-
Spoke Gateways can have up to 15 gateway instances.
A Spoke Gateway can have only one gateway instance in the following scenarios.
-
A Spoke Gateway with BGP connection(s).
-
A Spoke Gateway with Site2Cloud or customized SNAT and DNAT enabled.
-
At least one gateway instance must be deployed to create a Gateway. Additional gateway instances can be created during or after the Gateway is created.
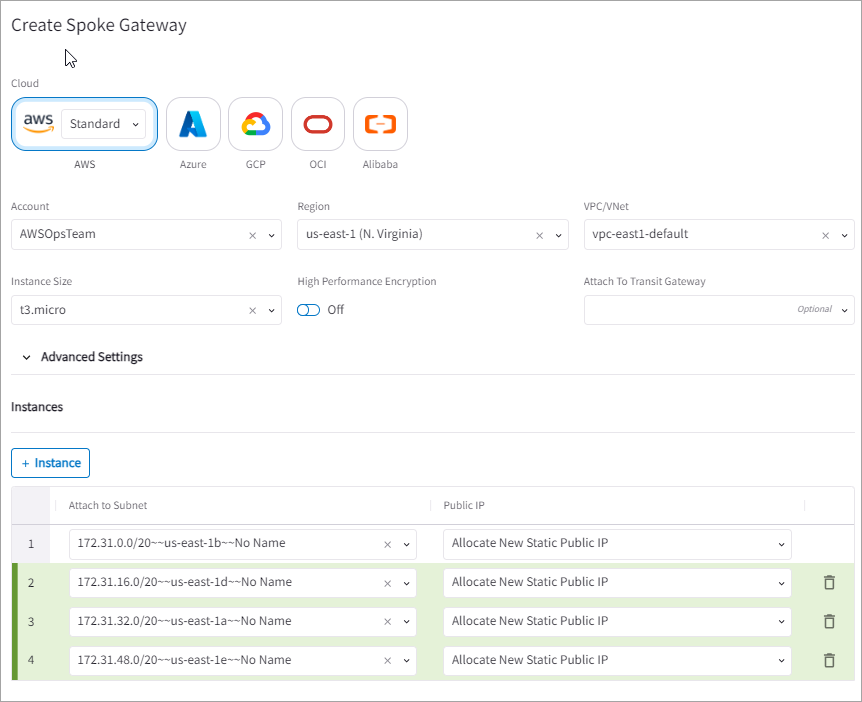
CoPilot auto-generates the name of the gateway instance. The first gateway instance name is the same as the Gateway, subsequent gateway instance names are generated in the format <_gateway-name_>-<_instance-number_>. The Aviatrix Controller automatically reprograms the CSP route tables to forward traffic across all gateway instances in that VPC or VNet.
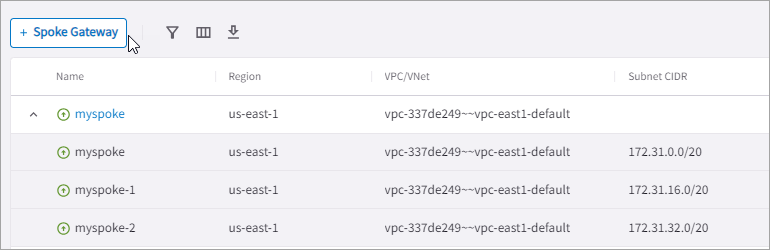
| All gateway instances are created in active-active state and will forward traffic in the event of tunnel failure between Spoke VPC or VNet and Transit VPC or VNet. For best practice, each gateway instance in a VPC or VNet should be created on a different public subnet in different availability zone, if available. |
Gateway instances share the same properties as the Gateway, such as instance size, high performance encryption, and attachment or peering. When the Gateway’s property is changed in CoPilot, instance size for example, the instance size for all gateway instances in that VPC or VNet is changed.
|
Creating Highly Available Spoke Gateway Instance Using Terraform
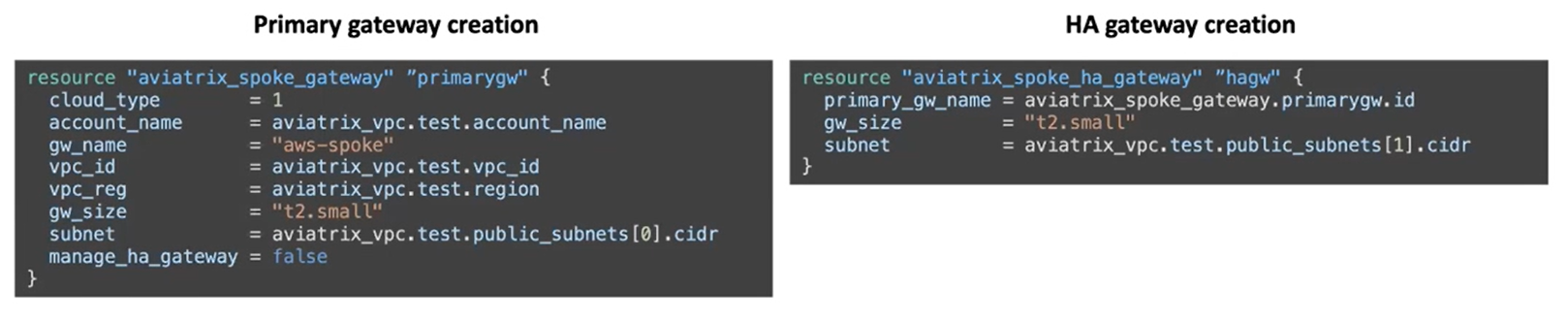
If you deploy your Aviatrix platform using Terraform, to create highly available Spoke gateway instance, you can use the Terraform resource, aviatrix_spoke_ha_gateway .
|
The highly available Spoke gateway instances are created sequentially (one by one).
For more information, see Aviatrix Provider.
Removing Highly Available Gateway Instances
You can remove one or more highly available gateway instances from a VPC or VNet.
When gateway instances are removed, the Aviatrix Controller automatically reprograms the CSP route tables pointing to the instances that are removed to forward network traffic to the remaining highly available gateway instances in that VPC or VNet.
| You cannot delete the first gateway instance. You can only delete the first gateway instance by deleting the Gateway itself. Before you can delete the Gateway, you must delete the other gateway instances in the VPC or VNet and detach all gateway peerings. |
Deleting a Spoke Gateway Instance
When a Spoke gateway instance is deleted and the gateway instance is attached (spoke-to-transit) or peered to another gateway (spoke-to-spoke), the Aviatrix Controller dynamically removes the gateway attachment or peering without affecting other gateway instances in that VPC or VNet.
| If a BGP-enabled Spoke Gateway has external connections, you must remove the connections before you can delete the Spoke gateway instance. |