Site2Cloud Configuration Workflow
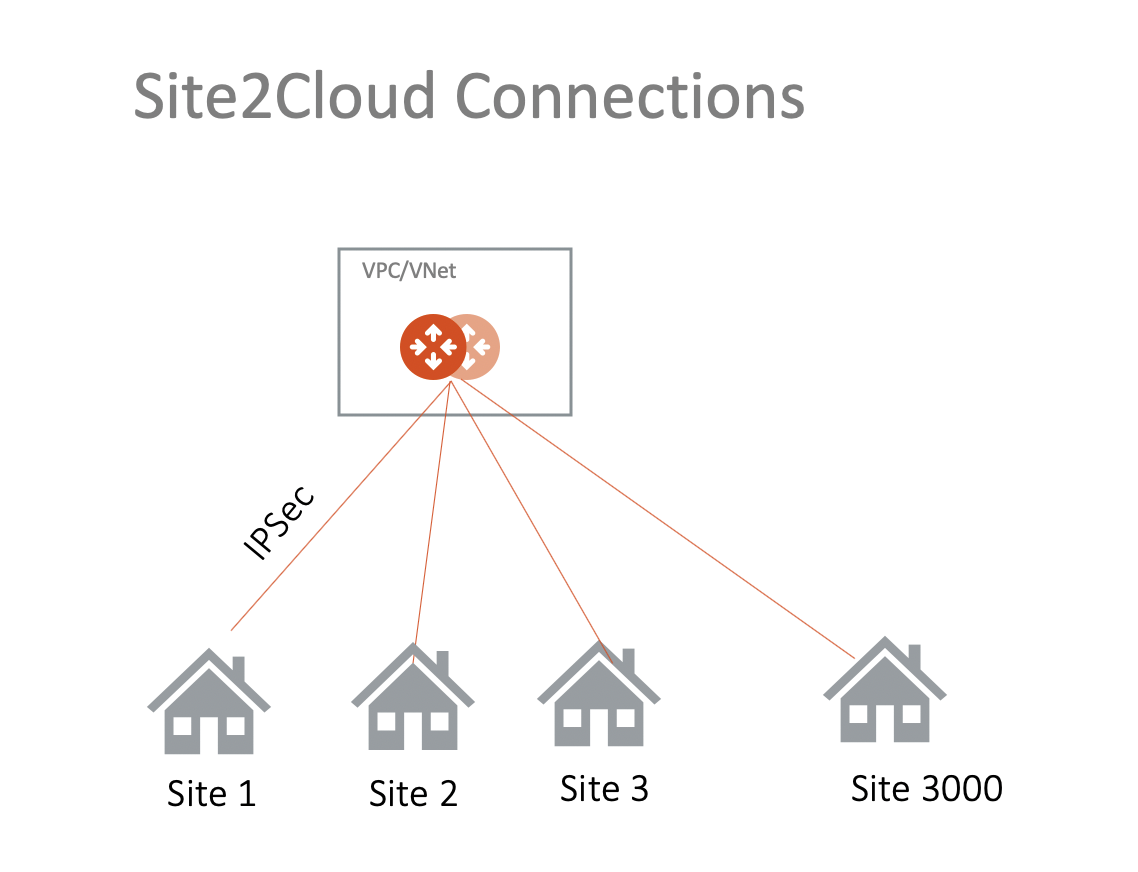
In this document, learn how to establish connectivity between an Aviatrix gateway in AWS, Azure, or GCP and your on-premise router or firewall.
|
If you are planning to use certificate-based authentication for your Site2Cloud connection, ensure that you have already generated and exported the external device CA certificate. |
Create Site2Cloud Connection
-
Log in to your Aviatrix Controller.
-
Select Site2Cloud > Setup on the left navigation bar.
-
In Create a New Site2Cloud Connection, click on + Add New.
-
Under Add a new connection, select the VPC ID where this tunnel will terminate in the cloud.
-
Refer to the sections below for information on configuring the connection.
Connection Type
Select Mapped or Unmapped as the Connection Type. You should select Unmapped unless the Local Subnet and the Remote Subnet overlap.
If you select the Mapped option in conjunction with the Forward Traffic to Transit Gateway option (possible after you configure your Site2Cloud connection, under the Edit options), bi-directional traffic flow occurs.
Mapped
If you select Mapped, configure the following:
-
Remote Subnet (real): Specify a list of the destination network CIDRs, separated by comma, that will be encrypted (for example, 10.10.1.0/24, 10.10.2.0/24).
-
Remote Subnet (virtual): Specify a list of virtual remote network CIDRs that are mapped to the real remote subnet (for example, for the real CIDRs listed above, you can have these virtual remote subnets: 192.168.1.0/24, 192.168.2.0/24).
-
Local Subnet (real): Specify a list of the source network CIDRs, separated by comma, that will be encrypted. If left blank, the full CIDR is used. If you enter a value, make sure you include the VPC/VNet as well. These Local Subnets are advertised to Remote Subnets that the Site2Cloud connection can reach. Examples of real local subnets are 172.16.1.0/24, 172.16.2.0/24.
-
Local Subnet (virtual): Specify a list of virtual local network CIDRs that are mapped to the real local subnet (for example, for the real CIDRs listed above for the real local subnet, you can have these virtual local subnets: 192.168.7.0/24, 192.168.8.0/24).
|
If the Local Subnet field is outside of gateway VPC/VNet, you need to open the gateway inbound security groups to allow the Local Subnet network CIDR ranges. |
|
Here is an example of one-to-one mapping:
Remote Subnet (Real): 10.1.7.10/32
Remote Subnet (Virtual): 172.16.7.10/32
Local Subnet (Real): 10.1.7.15/32
Local Subnet (Virtual): 192.168.7.45/32
Unmapped
For unmapped connections, the following two fields will be displayed:
| Field | Description |
|---|---|
Remote Subnet |
Enter the CIDR representing the remote network. |
Local Subnet |
The CIDR block of the local VPC/VNet subnet. If left blank, Aviatrix will use the full VPC/VNet CIDR. |
Custom Mapping
If you select the Custom Mapped checkbox after selecting the Mapped option, more complex Site2Cloud configurations are possible. You can have locally initiated traffic flows only; remotely initiated traffic flows only; and differing NAT translation based on these local/remote initiated flows.
Remote Gateway Type
| Type | Description |
|---|---|
Generic |
Use this option for most third-party routers and firewalls. |
AWS VGW |
For terminating on an AWS Virtual Private Gateway, select this option. |
Azure VPN |
For terminating on Azure VPN Services |
Aviatrix |
When terminating on an Aviatrix CloudN on-premise gateway. |
SonicWall |
Authentication Type
You can authenticate the connection using Pre-Shared Key (PSK) or certificate-based authentication.
PSK-Based
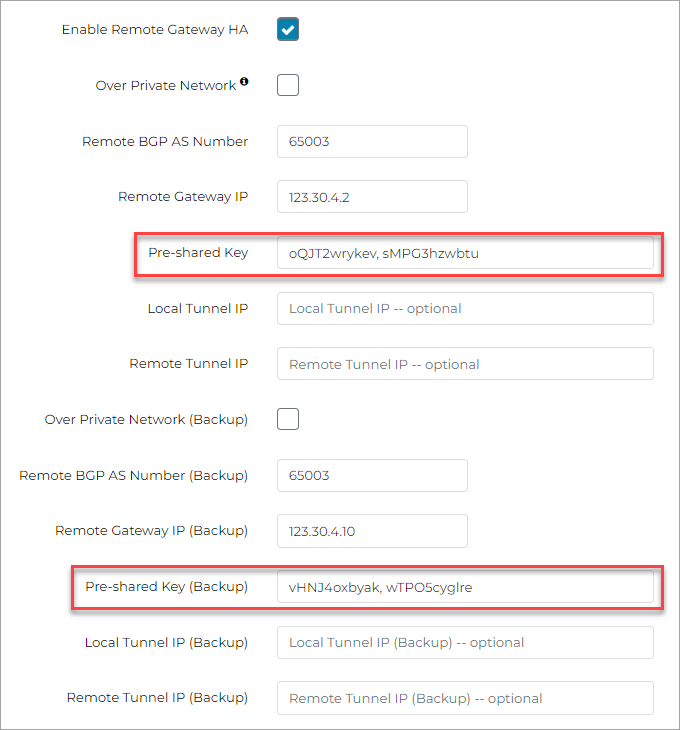
If you select PSK-based authentication, you can provide the Pre-Shared Key. A Pre-Shared Key is a string of random characters that is used to authenticate the IPsec tunnel connection between the Aviatrix Gateway and your on-premise router or firewall. You must ensure that this key is the same as the Pre-Shared Key that is configured for your on-premise firewall or router.
For Site2Cloud ActiveMesh connections, where both the local Aviatrix Gateway and remote on-premise router or firewall have high availability (HA) enabled, four IPsec tunnels are created (Local gateway to remote router/firewall, local HA gateway to remote router/firewall, local gateway to remote HA router/firewall, local HA gateway to remote HA router/firewall). If you want the tunnels that are created to have different PSK values, you will need to enter the PSKs separated by a comma.
|
Certificate-Based
If you select certificate-based authentication:
-
In the Remote CA Certificate field select the certificate you uploaded from your Palo Alto VM-Series firewall.
Tunnel Type
Select Policy-Based or Route-Based. If you select the latter, you must enter the local and remote tunnel IP. If you selected the Mapped Connection Type, only Route-based is supported.
Remote CA Certificate
Click on the dropdown menu and select a Remote CA certificate for this connection.
Algorithms
If the Algorithms checkbox is unmarked, the default values will be used. If it is checked, you can set any of the fields defined below.
| Field |
|---|
Phase 1 Authentication |
Phase 1 DH Groups |
Phase 1 Encryption |
Phase 2 Authentication |
Phase 2 DH Groups |
Phase 2 Encryption |
IKEv2
Select the option to connect to the remote site using the IKEv2 protocol. This is the recommended protocol.
|
If you configure IKEv1 in a Site2Cloud connection that uses certificate-based authentication and is connecting to another Aviatrix device, you must add the intermediate CAs in addition to the root CA. When an intermediate CA is renewed and re-authentication is attempted, the Site2Cloud connection will go down until you add the new certificate. |
Enabling HA
Select this option to create a backup/failover connection in case the primary connection fails. If you select this option you can also select the Enable Single IP HA checkbox, which allows you to use the same EIP to bring up the backup tunnel (supported for AWS and Azure only).
If mapped NAT is enabled, HA in Site2Cloud is not supported.
If you have the following configuration you can select the Same Pre-shared Key as primary check box, which means the backup tunnel uses the same pre-shared key as the primary.
-
Enable HA check box selected
-
Enable Single IP HA checkbox not selected
-
PSK-based authentication selected
If the Enable HA checkbox is selected, you can enter a Pre-shared Key for the backup (HA) gateway. Also, if this checkbox is selected, you must enter the Remote Gateway IP address of the backup gateway.
Enable Single IP HA
When you select Enable Single IP HA check box, you also need to select the Backup Gateway. The backup gateway should be created at Gateway > Edit > Gateway for High Availability Peering.
Editing the Site2Cloud Connection
Once a connection is created, you can download the configuration or edit parameters. To do this, select Site2Cloud in the left pane and select the connection you just created. Make sure the values you entered for all the parameters are valid.
Local Identifier
By default, Aviatrix configures gateway’s public IP as the Local Identifier. You can adjust these settings to your gateway’s private IP.
Remote Identifier
Aviatrix only supports IP_ADDRESS and KEY_ID as the IKE identity type for the remote identifier in the pre-shared key authentication. The IP_ADDRESS must be a valid IPv4 IP address. The KEY_ID is a remote device ID during the key authentication.
By default, Aviatrix configures the public IPv4 address of the peer device as the Remote Identifier for pre-shared key authentication. You can adjust this setting to the private IPv4 address of the peer device.
If you enter string(s) other than an IPv4 address or empty string(""), the string(s) you entered is treated as Key_ID. If KEY_ID value is not correct, this field validation will fail.
If you are unsure about this field’s value, enter an empty string("") to skip the validation of this field.
Download Configuration
You can generate a remote site configuration template. This template file contains the gateway public IP address, VPC CIDR, pre-shared secret and encryption algorithm. You can import the information to your remote router/firewall configuration.
| If the remote gateway is an Aviatrix CloudN, go to the Site2Cloud Setup page in the Controller, import the downloaded configuration file, and click OK. |
To download a configuration:
-
After creating a Site2Cloud connection, select the remote site device from the table on the Setup Site2Cloud Connection page and click Edit.
-
In the Download Configuration area, select your remote site device from the Vendor menu, or use the Generic/Vendor Independent template (you select Generic for anything that is not an Aviatrix gateway. If you are connecting two Aviatrix gateways, you select Aviatrix as the vendor).
-
If you select a Generic vendor, the Platform field is populated as Generic, and the Software field is populated with Vendor Independent.
-
If you select the Aviatrix vendor, the Platform is populated with UCC, and the Software version is 1.0.
-
If you select a specific hardware vendor (such as Cisco), available platforms belonging to that vendor are displayed in the Platform field, and the Software field is populated with related software versions.
-
How to use this downloaded configuration:
-
If connecting two Aviatrix gateways, you import the downloaded configuration when creating the other side of the tunnel. Gateways can be in different Controllers or the same Controller. See Aviatrix Gateway to Aviatrix Gateway for more information.
-
If connecting an Aviatrix gateway to a firewall or other on-prem vendor, use the downloaded configuration information to populate the necessary information in your firewall UI.
Dead Peer Detection
This field is not applicable to a Site2Cloud connection established by the Transit Network workflow.
Dead Peer Detection (DPD) is a standard mechanism (RFC 3706) between IPsec tunnels to send periodic messages to ensure the remote site is up.
By default DPD detection is enabled.
| Field | Value | Description |
|---|---|---|
Delay |
>= 1 |
Keepalive timer (in seconds) |
Retry Delay |
>= 1 |
How long should the tunnel wait before declaring keep alive failed. (in seconds) |
Maxfail |
>= 1 |
Number of tries before considering the peer is dead. |
Active Active HA
Allow Site2Cloud gateways to support Active-Active mode where both tunnels are up and packets are routed to both gateways via respective VPC/VNet route tables.
To enable this:
-
In the Aviatrix Controller navigate to Site2Cloud > Setup.
-
Select the relevant connection and click Edit.
-
Scroll to Active Active HA and click Enable.
Forward Traffic to Transit Gateway
Typically, you enable the Forward Traffic to Transit Gateway option when you have a Site2Cloud connection that has overlapping CIDRs. This forwarding ensures that traffic is sent between on-prem routers and local Spoke and Transit gateways.
In most cases you will enable this so that your on-premise traffic is forwarded.
For more information view the explanation in this scenario.
This option is only available for route-based IPSec paired with Mapped NAT.
Event Triggered HA
Event Trigger HA reduces convergence time. To configure:
-
Navigate to Site2Cloud > Setup and select a connection.
-
Click Edit.
-
Scroll down to Event Triggered HA and click Enable.
Jumbo Frame
Jumbo Frame improves the performance between an Aviatrix Transit gateway and CloudN or an Aviatrix Edge Gateway.
|
To configure:
-
Navigate to Site2Cloud > Setup and select a connection.
-
Click Edit.
-
Scroll down to Jumbo Frame and click Enable.
Clear Sessions
Clear Session allows you to reset all the active sessions on a selected Site2Cloud connection.
-
Navigate to Site2Cloud > Setup and select a connection.
-
Click Edit.
-
Scroll down to Clear Sessions and click Clear.
Periodic Ping
In very rare cases Site2Cloud tunnels may fail to pass traffic if the tunnel is dormant for a long period of time. This is not an issue with the Aviatrix Gateways and can usually be traced to misconfigurations on the remote device. To compensate for this Periodic Ping maintains a steady flow of traffic across the tunnel.
You can configure Periodic Ping by selecting a gateway, clicking Edit, and scrolling down to the Periodic Ping option.
Network Device Support
Aviatrix Site2Cloud supports all types of on-prem firewall and router devices that terminate VPN connections.