Aviatrix NEXT GEN TRANSIT with customized SNAT and DNAT features
This technical note provides a step-by-step configuration on the Aviatrix controller that will address the following requirements:
-
Spoke VPCs in Cloud need to communicate with On-Prem
-
On-Prem is not able to route RFC 1918 traffic to Cloud
-
Perform Customized SNAT feature for the traffic from Cloud to On-Prem
-
Perform DNAT feature for the traffic from On-Prem to Cloud
-
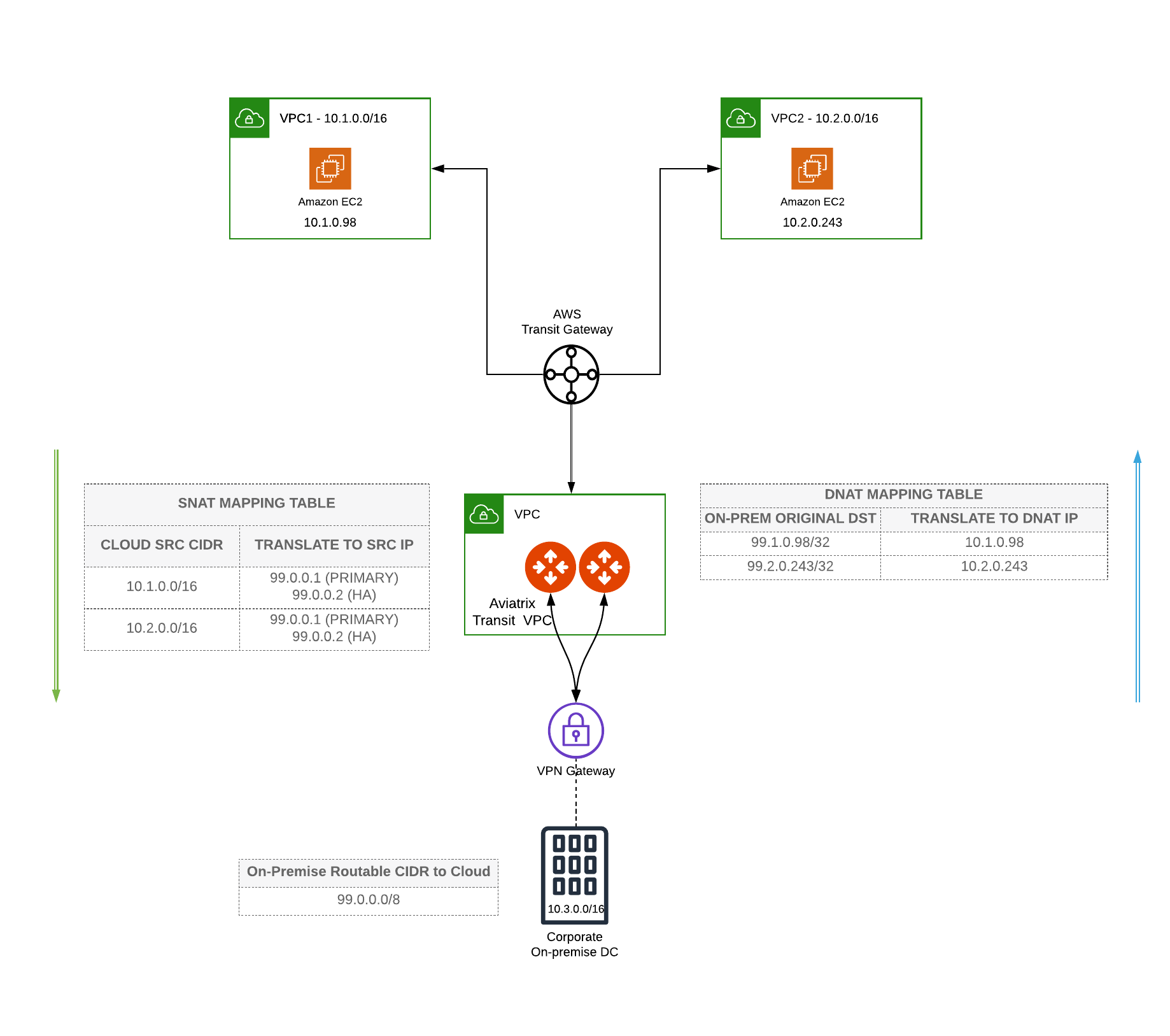
Topology:
-
Aviatrix NEXT GEN TRANSIT FOR AWS
-
Spoke VPCs * 2 (for example: 10.1.0.0/16, 10.2.0.0/16)
-
Transit VPC * 1 (for example: 192.168.100.0/24)
-
AWS VGW
-
-
On-Prem routable CIDR (for example: 99.0.0.0/8)
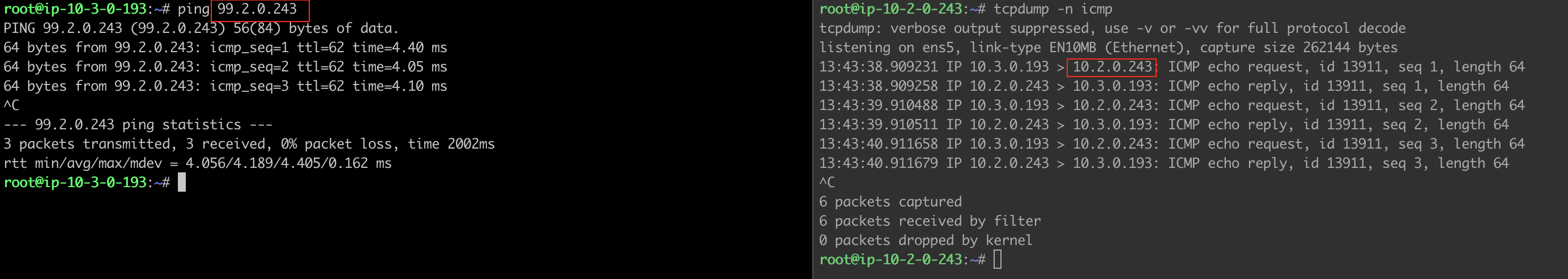
Scenario:
-
Traffic from Cloud to On-Prem: When a packet sent from Spoke VPCs in Cloud enters the Aviatrix Transit Gateway, the packet’s source address needs to be changed to an IP that On-Prem is routable. (Source address translation)
-
Traffic from On-Prem to Cloud: When a packet sent from On-Prem enters the Aviatrix Transit Gateway, the packet’s destination address needs to be changed from an IP within the On-Prem routable CIDR to an IP belonging to a service in Spoke VPCs in Cloud. (Destination address translation)
Follow the steps below to set up for the scenario.
Step 1. Prerequisite
-
Upgrade the Aviatrix Controller.
-
Prepare an IP mapping table for SNAT and DNAT configuration.
-
SNAT configuration: Prepare two On-Prem routable IPs (one for the Aviatrix Transit Gateway; one for the Aviatrix Transit HA Gateway if needed)
-
Example: Transit Primary Gateway: 99.0.0.1/32 Transit HA Gateway: 99.0.0.2/32
DNAT configuration:
-
Prepare a list of IP mapping tables for the On-Prem routable CIDR to a service in Spoke VPCs corresponding to your topology
-
A service might be an IP belonging to Load Balancer or EIP
Example: 99.1.0.98 <--> 10.1.0.98 99.2.0.243 <--> 10.2.0.243
Step 2. Build Aviatrix Next Gen Transit for AWS
-
Follow steps 1, 2, 3, 4, 4.1, 5, and 6 here.
Step 3. Perform a Manual BGP Advertised Network List feature on the tunnel between Aviatrix Transit GW and AWS VGW
Follow these steps: Gateway Manual BGP Advertised CIDR List. This action will advertise the On-Prem routable CIDR to On-Prem via BGP session.
Example: On-Prem routable CIDR: 99.0.0.0/8
To configure:
-
Go to the Site2Cloud page and click on the tunnel between Aviatrix Transit Gateway and AWS VGW
-
Scroll down to the Manual BGP Advertised Network List
-
Enter the value of the On-Prem routable CIDR (for example: 99.0.0.0/8).
-
Click the button Change BGP Manual Spoke Advertisement.
Step 4. Configure Aviatrix Customized SNAT function on both Transit
Perform Customized SNAT on the main Transit and HA gateways. This action changes the packet’s source IP address from Spoke VPCs in the Cloud to an IP which belongs to an On-Prem routable CIDR.
Example: Transit Primary Gateway: traffic from spoke VPCs 10.1.0.0/16 and 10.2.0.0/16 translates to IP 99.0.0.1 Transit HA Gateway: traffic from spoke VPCs 10.1.0.0/16 and 10.2.0.0/16 translates to IP 99.0.0.2
To configure:
-
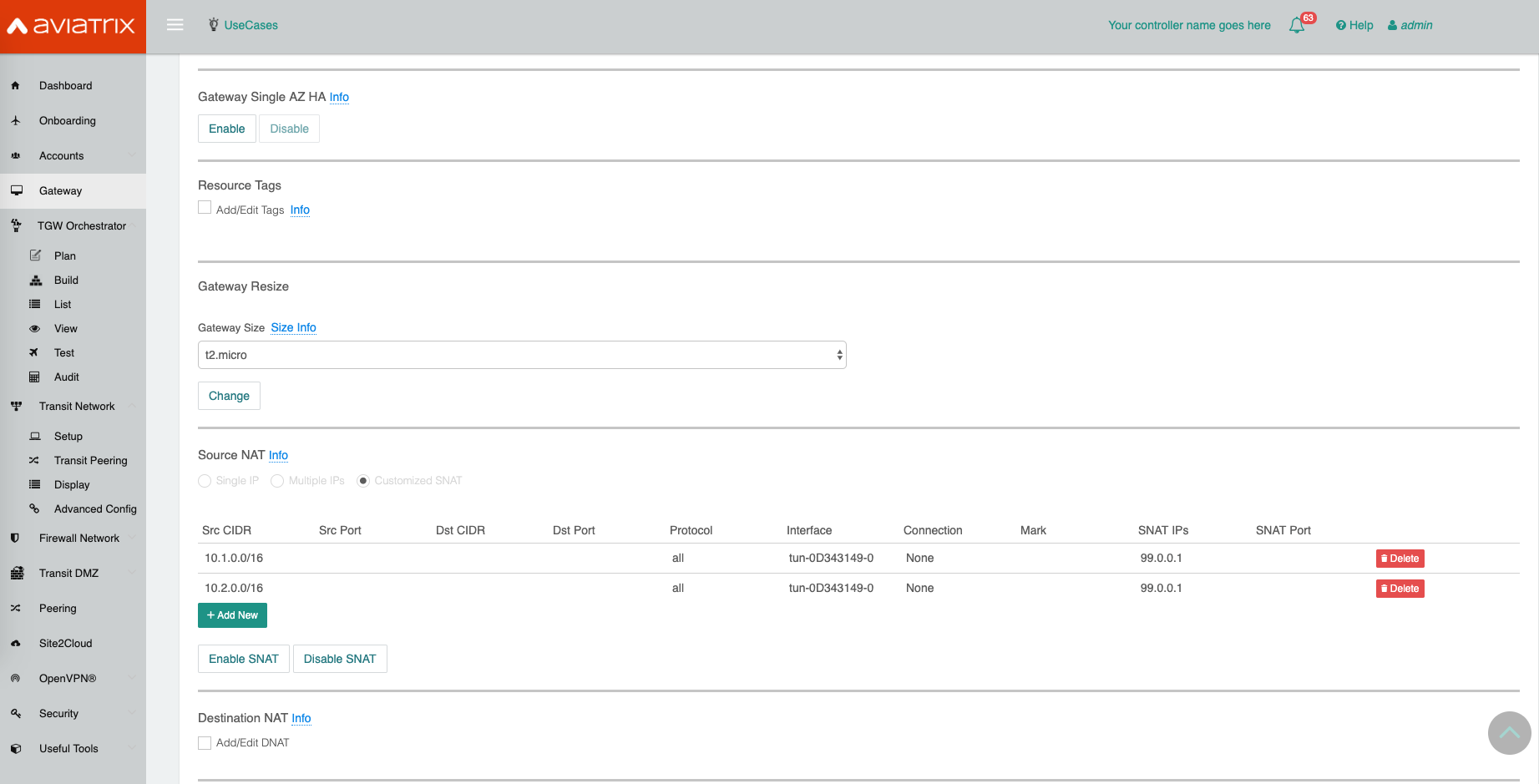
Go to the Gateway page, click on the Transit Primary Gateway first.
-
Click Edit.
-
Continue on to the Edit page, scroll to SNAT. Select Customized SNAT.
-
Select Customized SNAT.
-
Click Add New.
-
Enter fields for Src CIDR, protocol, Interface (select the one with VGW) and SNAT IPs as below example.
-
Click Save.
-
Repeat the above steps for more entries.
-
Click Enable SNAT to commit.
-
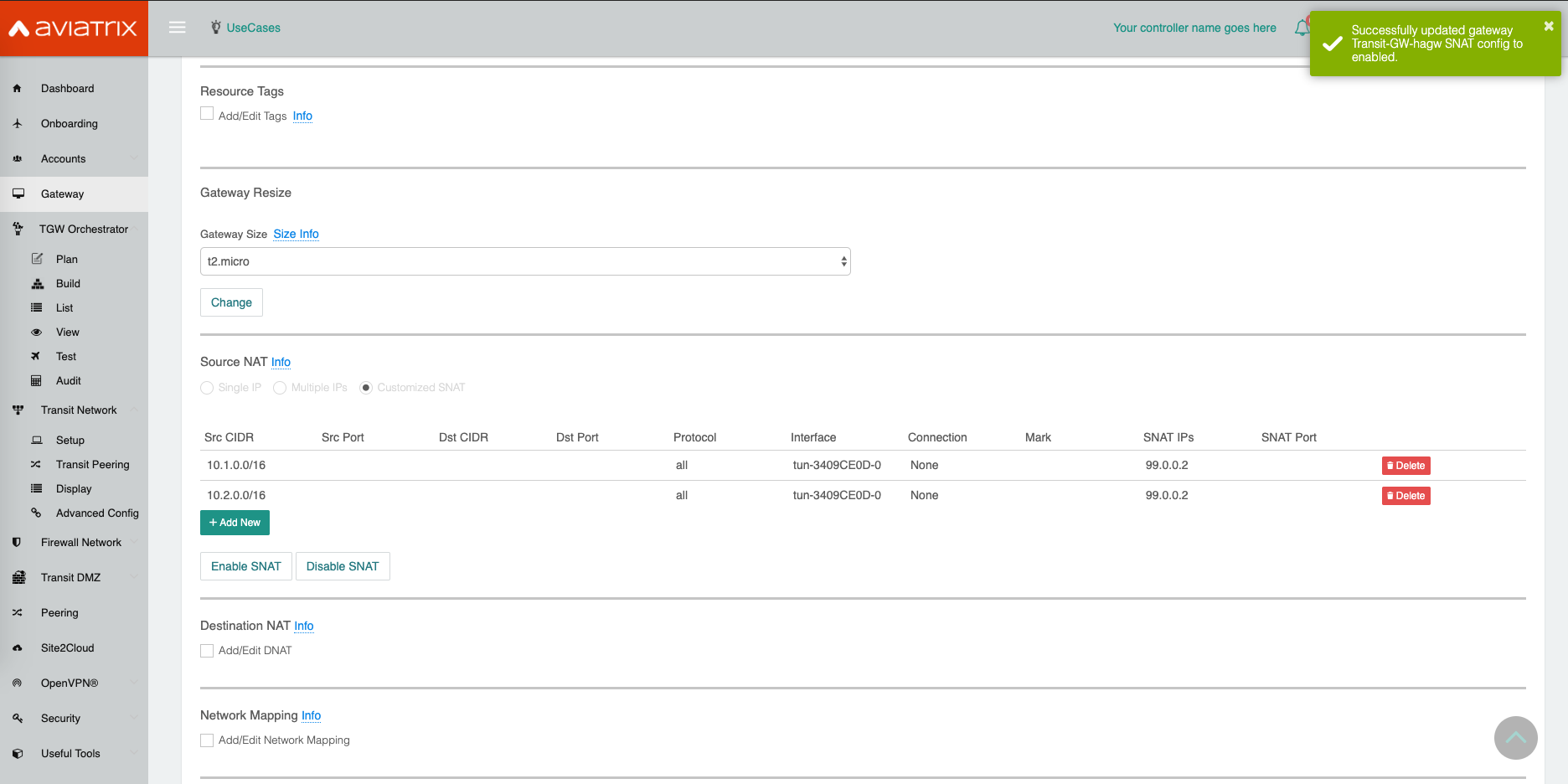
Go to Gateway page, click on the Transit HA Gateway. Click Edit.
-
Repeat the above steps to configure Customized SNAT for Transit HA Gateway as shown in the example below.
Step 5. Configure Aviatrix Customized DNAT function on the Transit
Run DNAT on the main Transit gateway. This action instructs the gateway to translate the destination address from an IP within the On-Prem routable CIDR to an IP belong to a service in Spoke VPCs in Cloud.
Example: 99.1.0.98/32 <--> 10.1.0.98 99.2.0.243/32 <--> 10.2.0.243
To configure:
-
Go to the Gateway page and click on the Transit Primary Gateway. Click Edit.
-
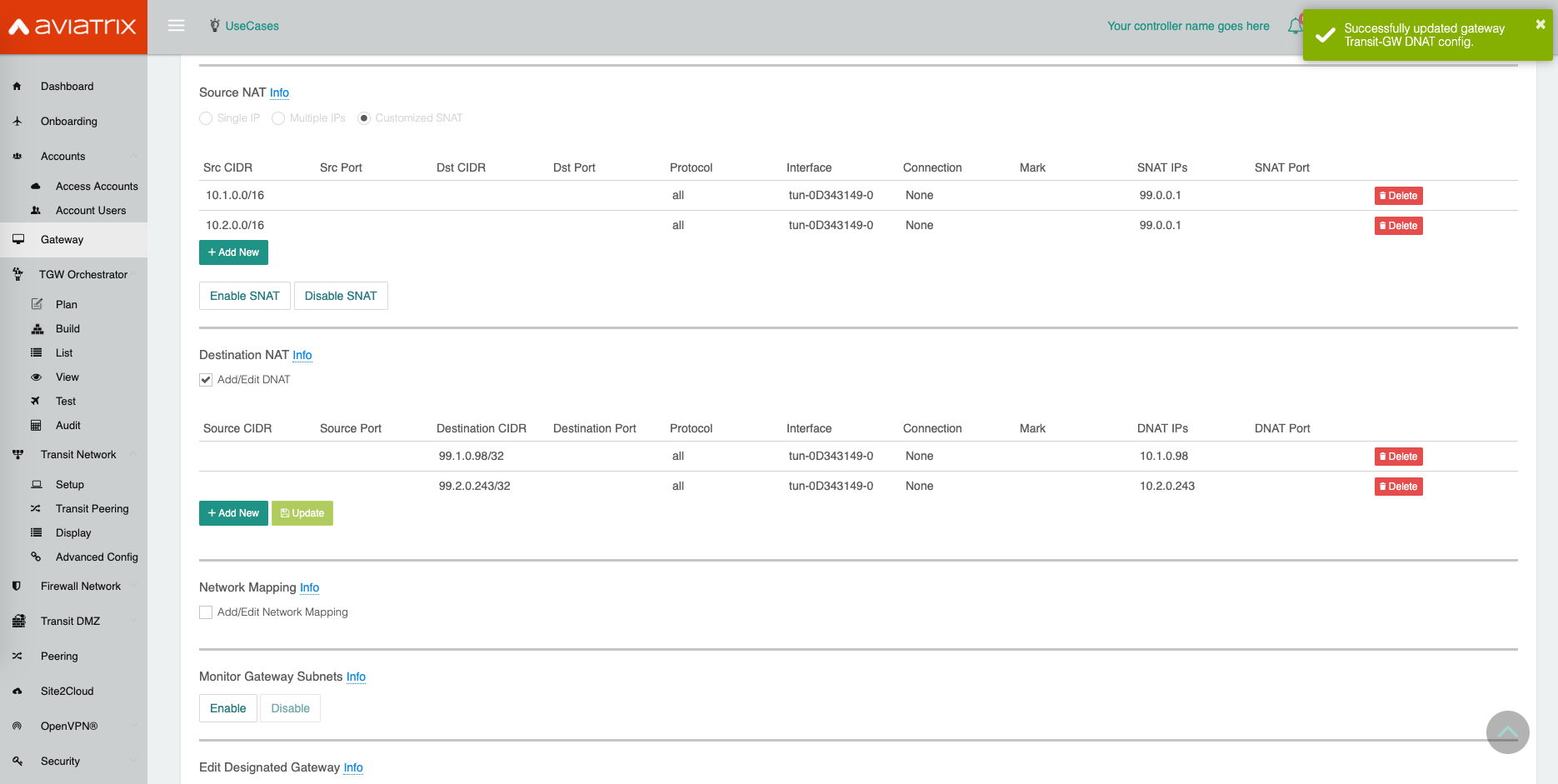
Scroll down to “Destination NAT”, click Add/Edit DNAT
-
Click Add/Edit DNAT.
-
Click Add New.
-
Enter fields for Destination CIDR, protocol, Interface (select the one with VGW) and DNAT IPs as per the below example.
-
Click Save.
-
Repeat steps 5.4, 5.5, and 5.6 for multiple entries.
-
Click Update to commit.
Step 6. Attach spoke VPCs to an AWS Transit Gateway (TGW)
Use the steps in TGW Build.
Step 7. Verify traffic flow
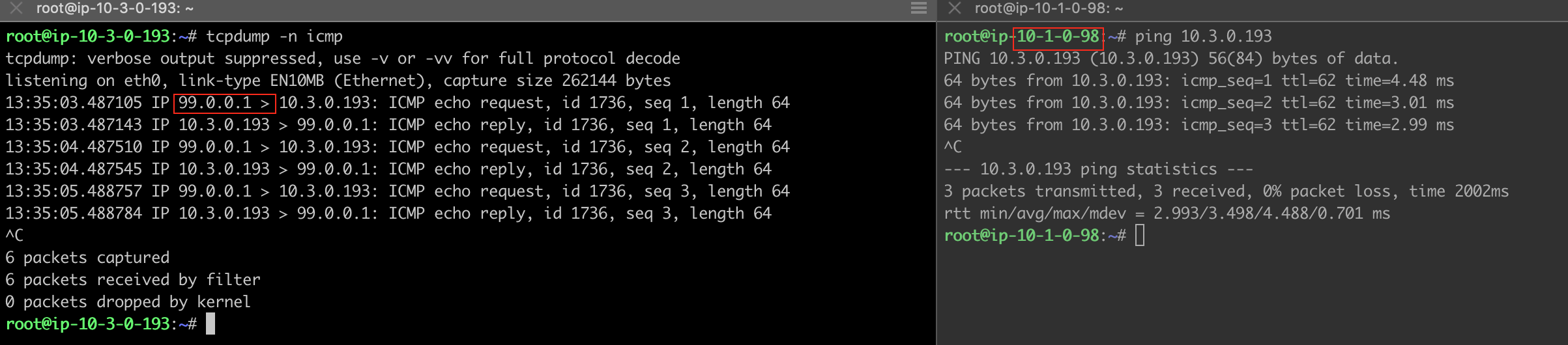
For SNAT, verify the following:
-
Traffic from Spoke VPC 10.1.0.0/16 to On-Prem
-
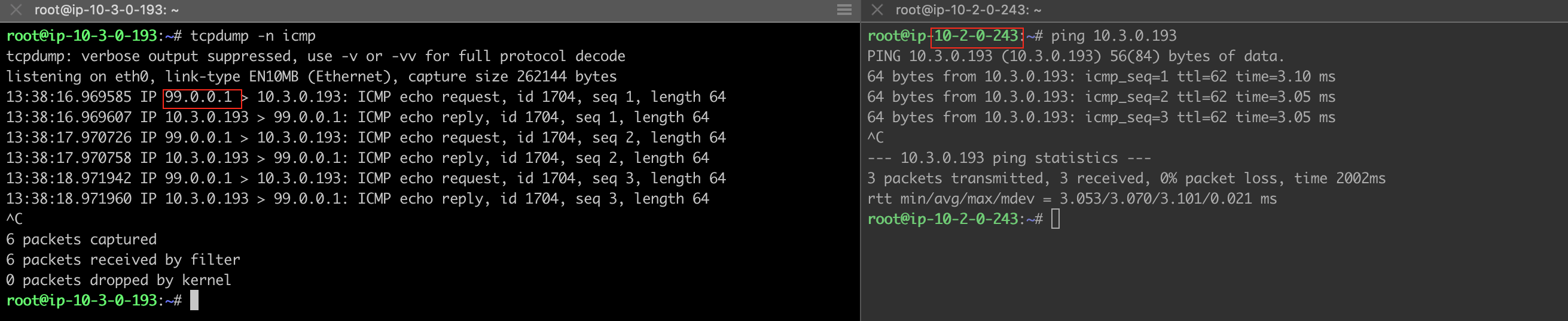
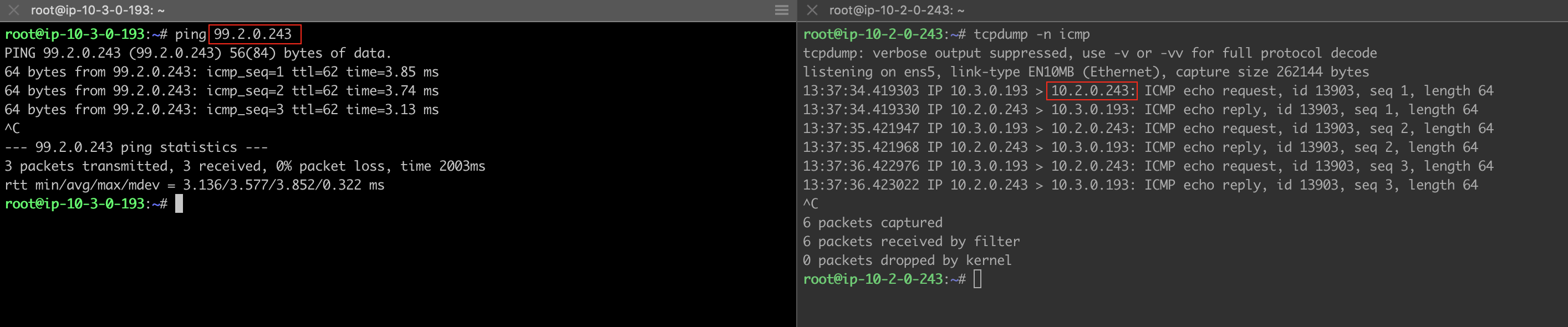
Traffic from Spoke VPC 10.2.0.0/16 to On-Prem
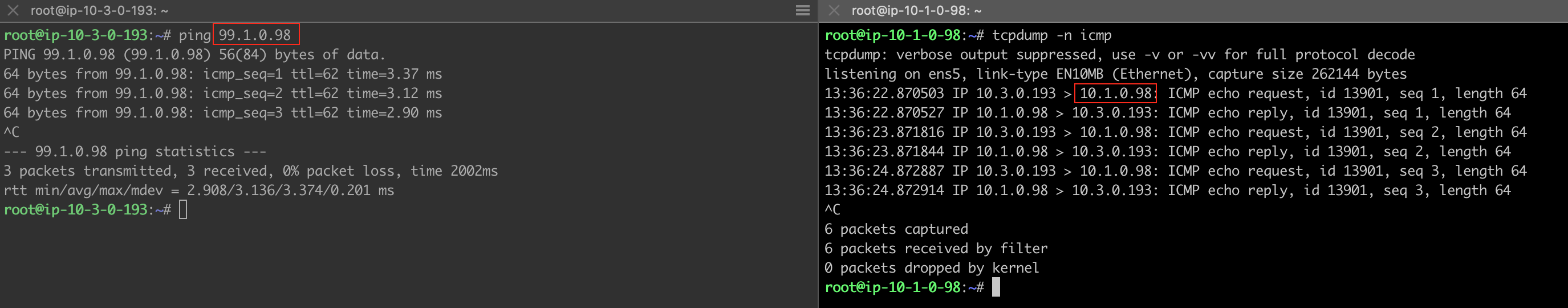
For DNAT, verify the following:
-
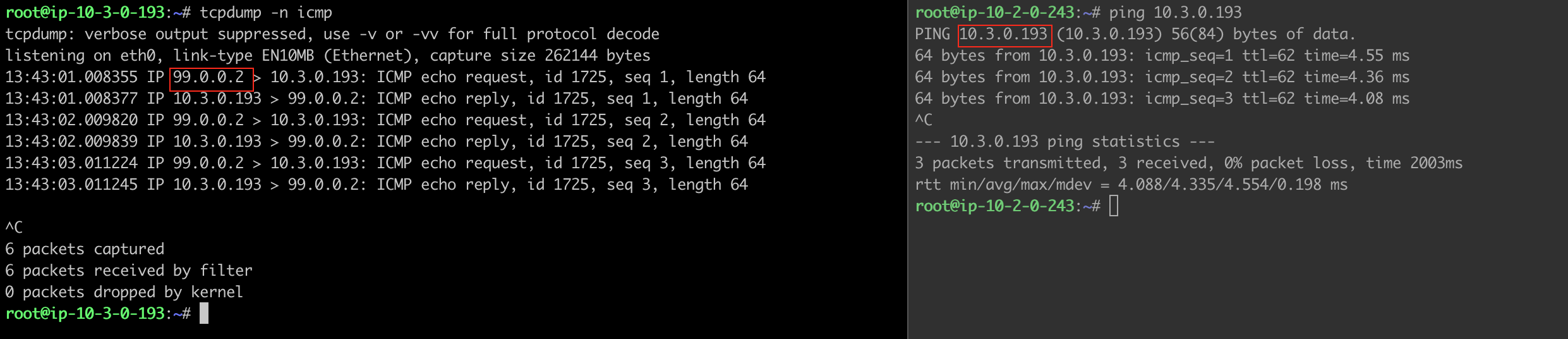
Traffic from On-Prem to Spoke VPC 10.1.0.0/16
-
Traffic from On-Prem to Spoke VPC 10.2.0.0/16
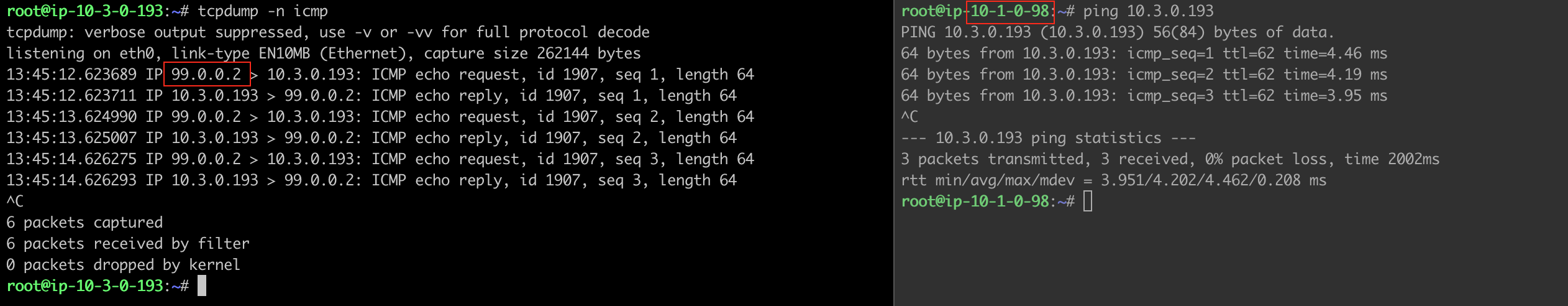
To verify SNAT failover to Transit HA gateway:
-
Traffic from Spoke VPC 10.1.0.0/16 to On-Prem
-
Traffic from Spoke VPC 10.2.0.0/16 to On-Prem
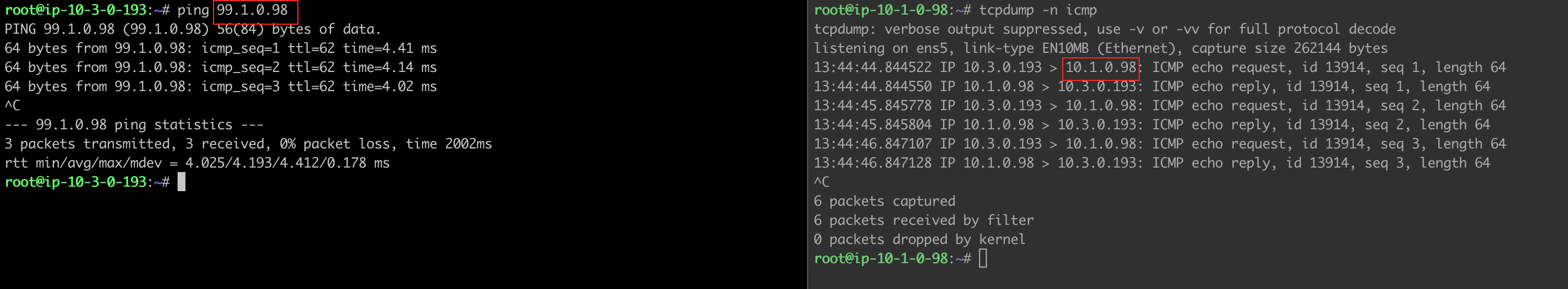
To verify DNAT failover to the Transit HA gateway:
-
Traffic from On-Prem to Spoke VPC 10.1.0.0/16
-
Traffic from On-Prem to Spoke VPC 10.2.0.0/16