Encryption over Direct Connect/ExpressRoute
AWS Direct Connect and Azure ExpressRoute provide a private routed circuit to an AWS VPC and an Azure VNet.
The Aviatrix Site2Cloud feature provides encryption over Direct Connect or ExpressRoute. This document describes how to implement the feature over Express Route. The same method applies to AWS.
The VNet VPN gateway that terminates the ExpressRoute connects VNet virtual machines with the on-prem servers in a traditional routing domain. While Azure ExpressRoute provides a private link between a customer’s on-prem network and an Azure VNet without going through the Internet, packets between on-prem edge and VNet travel through exchange points and third party provider networks and are not encrypted.
Aviatrix Solution for Encryption over ExpressRoute
The Aviatrix Site2Cloud solution can be applied to encrypt traffic over ExpressRoute, as shown below.
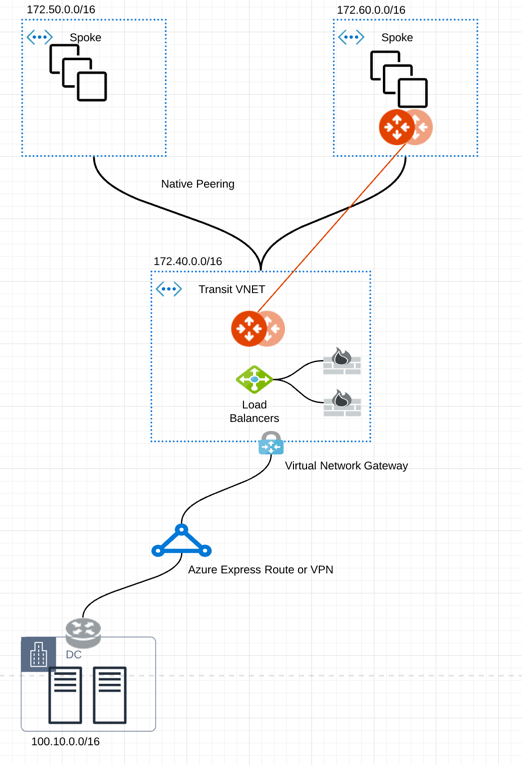
In the diagram above, an encrypted IPsec tunnel is established between an Aviatrix Gateway and the customer’s edge router.
An Aviatrix Gateway is deployed in a separate subnet from the subnets where the user virtual machines are launched. (The Controller is not drawn.) This is necessary as the Aviatrix Gateway is the router for user subnets to reach the enterprise data center.
An Aviatrix Gateway can be deployed in a 1:1 redundancy fashion where a backup gateway is ready to take over should the primary IPsec tunnel go down.
Configuration Workflow
Before beginning:
-
Make sure you have the latest Controller software by checking the Dashboard. If an alert message displays, click !New to download the latest software.
-
Decide if you want to enable HA for the gateway.
The configuration workflow is as follows, with major steps highlighted.
-
Create a gateway in a VNet where you like to connect to the enterprise datacenter. In the Controller, go to Gateway > Create and make sure the gateway is launched in a different subnet from the user subnets. In this example, the gateway is deployed on Subnet1.
The gateway can have VPN access disabled.
-
(Optional) If HA will be enabled, create a backup gateway in the same VNet. In the Controller, go to Gateway > Create and make sure the gateway is launched in a different subnet from the user subnets. In this example, the gateway is deployed on Subnet1.
The gateway can have VPN access disabled.
Create a connection to the Enterprise data center.
-
In the Controller, go to Site2Cloud > Setup > Add New.
-
Select the VPC ID/VNet Name where the Aviatrix Gateway for encryption is launched.
-
If you want to enable HA, select the Enable HA checkbox.
-
In the Primary Cloud Gateway field, select a gateway launched earlier as primary gateway.
-
(HA enabled only) In the Backup Gateway field, select a gateway launched earlier as the backup gateway.
-
In the Connection Name field, give the connection a unique name, such as "FirstExpressRoute".
-
In the Remote Gateway IP Address field, enter the private IP address of the edge router for Enterprise data center.
-
In the Remote Subnet (Real) field, enter the network CIDR of the Enterprise datacenter. If there are multiple subnets, enter each one separated with a comma.
-
Check the Over Private Network checkbox.
-
In the Route Table To Modify field (visible after the Over Private Network checkbox is selected), select the route table(s) associated with subnet2 and subnet3.
-
Click OK.
Downloading the Configuration Template
-
On the Site2Cloud > Setup page, select the connection you just created and click Edit.
-
In the Download Configuration area, select your remote site device from the Vendor menu, or use the Generic/Vendor Independent template (you select Generic for anything that is not an Aviatrix gateway. If you are connecting two Aviatrix gateways, you select Aviatrix as the vendor).
-
If you select a Generic vendor, the Platform field is populated as Generic, and the Software field is populated with Vendor Independent.
-
If you select the Aviatrix vendor, the Platform field is populated with UCC, and the Software version is 1.0.
-
If you select a specific hardware vendor (such as Cisco), available platforms belonging to that vendor are displayed in the Platform field, and the Software field is populated with related software versions.
-
-
Click Download Configuration to download a template file that contains the gateway public IP address, VPC/VNet CIDR, pre-shared secret and encryption algorithm (is this accurate?)
-
Incorporate the information to your remote router/firewall configuration.
-
At the enterprise data center or remote site, configure encryption on the edge device. Make sure your peer network is Subnet2 and Subnet3, as shown in this example.