Connecting Aviatrix Transit Gateway to External Devices
This document focuses on Aviatrix Transit Gateway connection to an external device.
There are three options to connect to the Aviatrix Transit Gateway:
-
AWS VGW
-
Azure VNG
-
External (or 3rd Party) Router/Firewall
What are the use cases for connecting to an external router?
-
Overcoming the AWS VGW 100 route limit Typically, an Aviatrix Transit GW connects to VGW over IPsec and runs a BGP session with VGW. VGW then connects to on-prem devices. By connecting directly to an external device, the VGW is bypassed.
-
Overcome AWS VGW performance reset VGW adjusts instance size based on network bandwidth consumption, leading to unexpected outage.
-
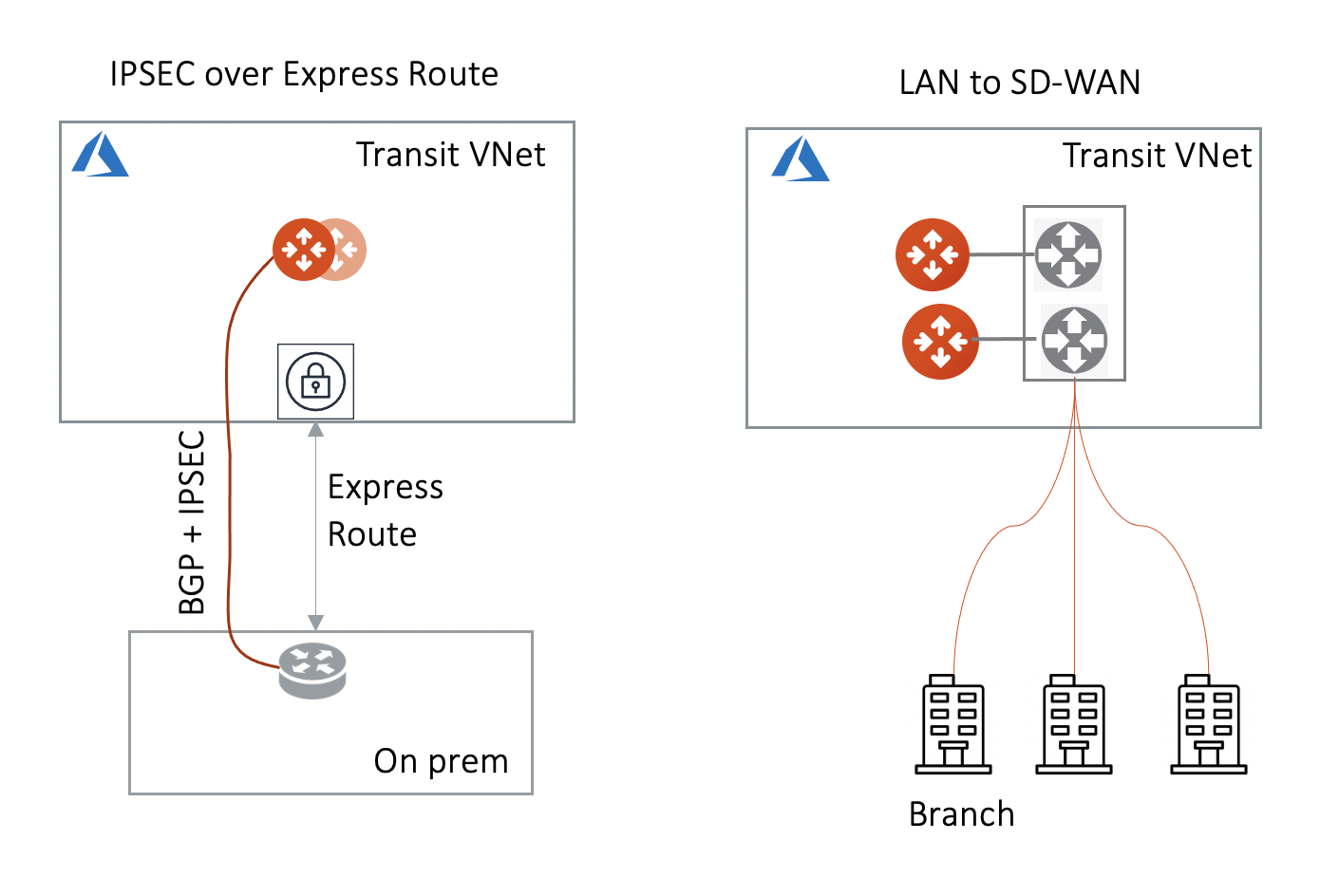
Azure Transit Network This feature allows an Aviatrix Transit GW to connect to on-prem over Azure Express Route or Internet.
-
High Performance with on-prem By using GRE tunneling protocol, Aviatrix Multicloud Transit Gateway builds multiple GRE tunnels to on-prem routers to achieve 10Gbps throughput.
-
Integrate with SD-WAN gateways deployed in the cloud BGP over LAN as part of the External Device option provides an efficient mechanism to connect to SD-WAN cloud gateways by interoperating with them over LAN in the same VPC/VNet while exchanging routes dynamically via BGP.
-
All Other Cloud Providers Use this feature to connect to network of cloud providers such as Alibaba Cloud, Tencent Cloud, VMware Cloud, IBM Cloud and others.
How does it work?
The Aviatrix Transit Gateway runs a BGP session to an external router to dynamically exchange routes. It also establishes an IPsec tunnel, GRE tunnel, or direct Ethernet to the router for packet forwarding. For IPsec tunneling, static routing option is also supported.
The mechanism works for AWS Direct Connect, Azure ExpressRoute, or the Internet.
Over Private Network in AWS
When the underlying infrastructure is AWS Direct Connect, the diagram is shown as below.
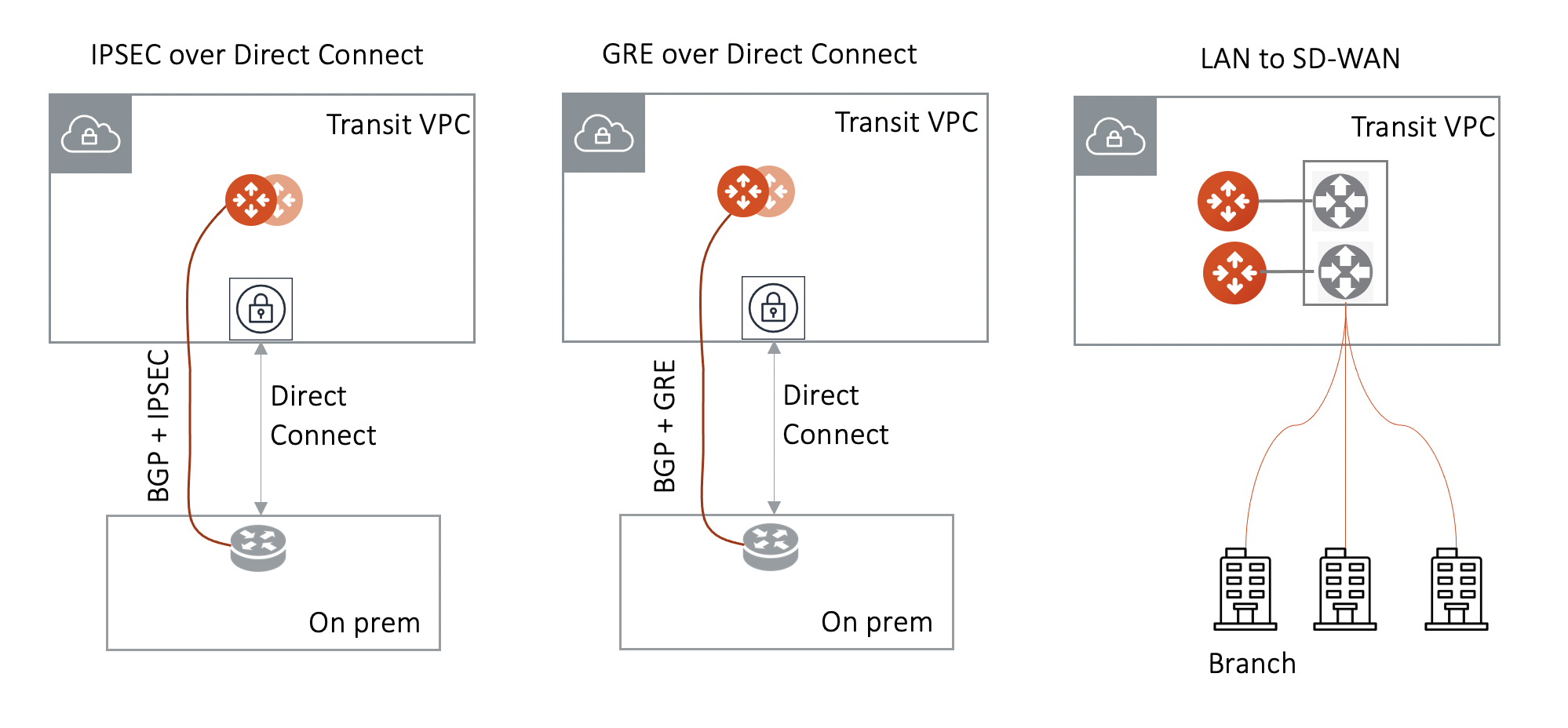
Make sure:
-
The VGW is attached to the Transit VPC for IPsec over Direct Connect and GRE over Direct Connect.
-
The external device advertises its IP address to VGW.
-
The external device advertises the on-prem network CIDR list to Aviatrix Transit GW.
How do I configure it?
Follow the instructions in Aviatrix Transit Gateway to External Devices.
If I already have a Transit to External Device connection using IKEv1, could I create another one using IKEv2?
The prerequisite for IKEv2 is that you need to create the first Transit to External Device connection with IKEv2 enabled. If your current Transit gateway already has a connection using IKEv1 either is created by attaching the Spoke Gateway or is built in Multi-Cloud Transit > Attach/Detach tab, you need to delete it first before creating the Transit to External Device connection with IKEv2.
How do I find out what routes being propagated from on-prem?
On-prem routes are propagated to the VGW which in turn propagates to the Transit GW. There are two ways to see what learned routes are by the Transit GW:
-
Go to Site2Cloud, select the connection you specified at Step 3 during the Transit Network Workflow. Scroll down, you will see the Learned Network. Search for a learned route by typing a specific CIDR.
-
Go to Peering > Transitive Peering. Click the box next to Destination CIDR column for a specific Spoke VPC/VNet GW. The Learned Routes are displayed and searchable.
-
Go to Multi-Cloud transit > BGP > select a Transit GW, and click Detail.
How do I know if the tunnel between the VGW and the Transit GW is up?
Go to Site2Cloud on the left sidebar. The tunnel status is displayed for each connection.