PingOne for Customers IdP for SAML Integration
Overview
This guide provides an example on how to configure PingOne for Customers as an IdP for an Aviatrix SAML SP (endpoint). When SAML client is used, your Aviatrix controller acts as the Identity Service Provider (ISP) that redirects browser traffic from client to IdP (e.g., PingOne for Customers) for authentication.
Before configuring SAML integration between Aviatrix and PingOne for Customers, make sure you have a valid PingOne for Customers account with administrator access.
Configuration Steps
Follow these steps to configure Aviatrix to authenticate against your PingOne for Customers IdP:
-
Step 1. Create an Aviatrix SP Endpoint in the Aviatrix Controller.
-
Step 2. Create a PingOne Web SAML App for Aviatrix in the PingOne for Customers Portal.
-
Step 4. Update Aviatrix SP Endpoint in the Aviatrix Controller.
-
Step 5. Test the Integration is set up correctly.
Step 1. Create an Aviatrix SP Endpoint
Visit one of the following links based on your use case and follow step 1 (Create temporary Aviatrix SP Endpoint for Aviatrix) from the link’s Configuration section:
-
If integrating PingOne IdP with Controller Login SAML Config
-
If integrating PingOne IdP with OpenVPN with SAML Authentication
Step 2. Create a PingOne Web SAML App for Aviatrix
| This step is usually done by the PingOne for Customers Admin. |
-
Login to the PingOne Admin portal.
-
Follow PingOne documentation to add a Web SAML application.
-
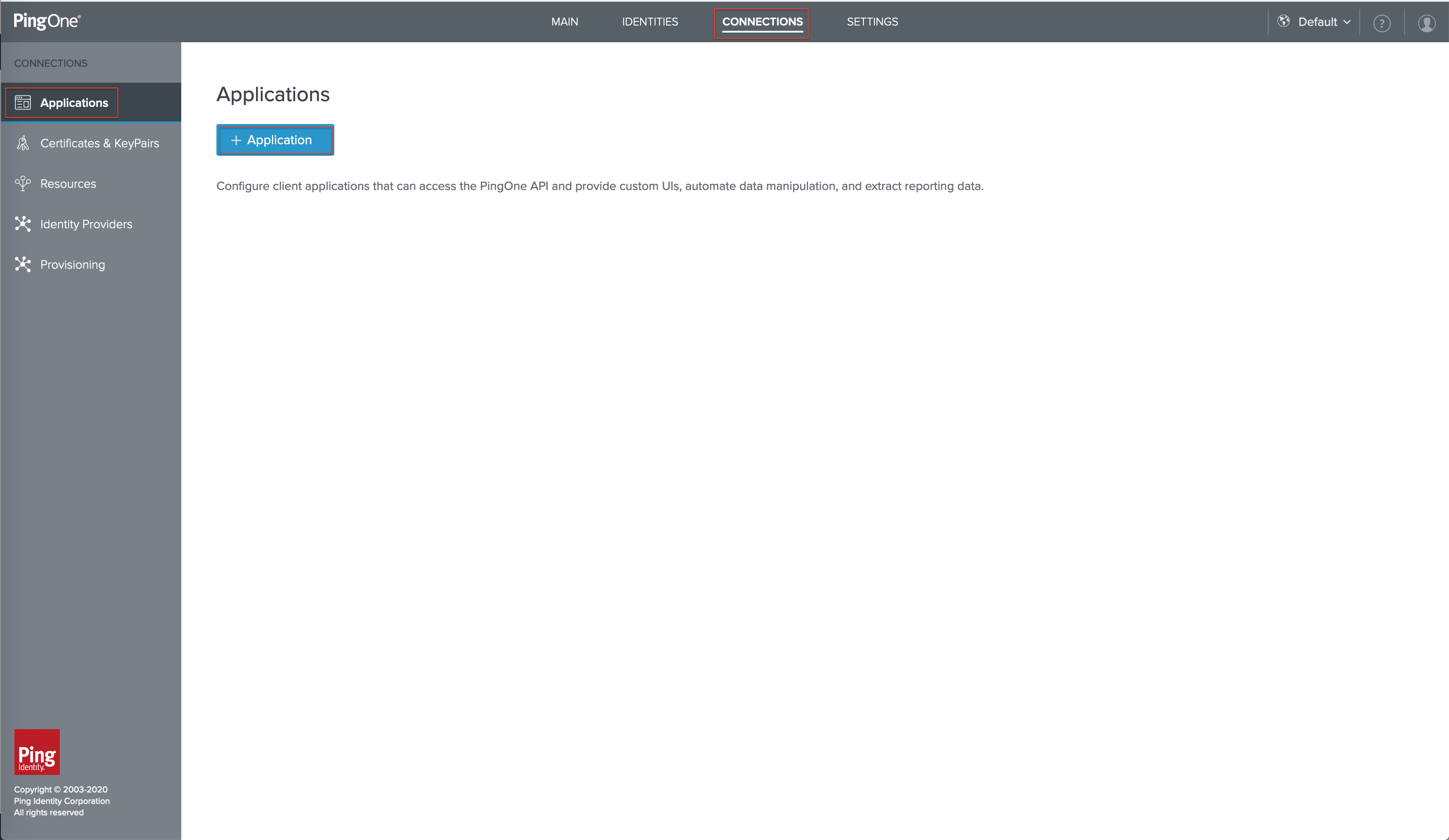
On the top of the page, click Connections.
-
On the left, click Applications and then + Application.
-
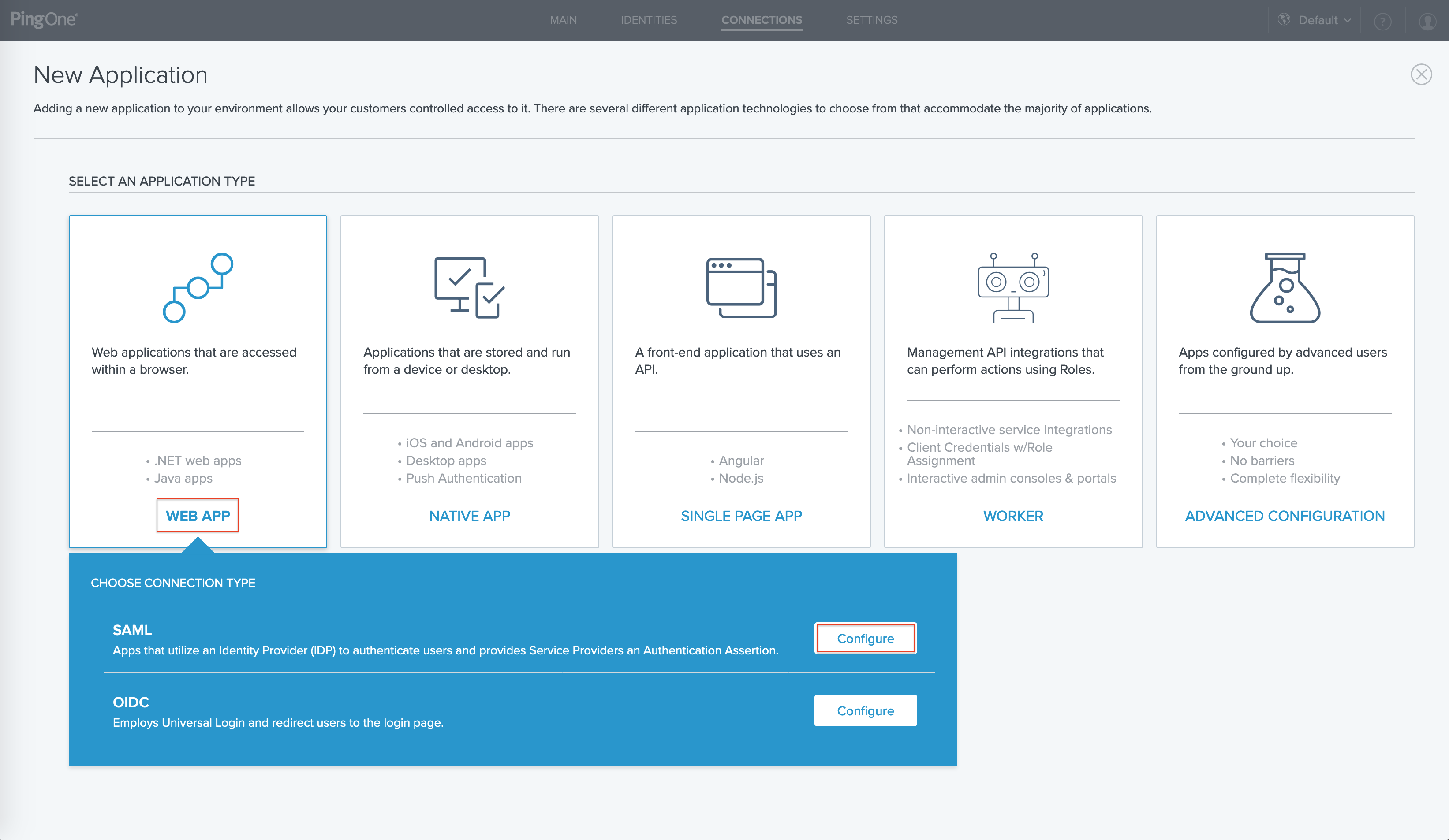
Click WEB APP, and then for SAML, click Configure.
-
Create the application profile by entering the following information:
Field Value Application name
A unique identifier for the application.
Description
(optional) A brief characterization of the application.
Icon
(optional) A pictorial representation of the application. The file can be up to 1MB in size in JPG, JPEG, GIF, or PNG format.
-
For Configure SAML Connection, enter the following:
Field Value ACS URLs
https://[host]/flask/saml/sso/[Endpoint Name]
Signing certificate
PingOne SSO Certificate for Default environment
Signing
Sign Assertion
Signing Algorithm
RSA_SHA256
Encryption
DISABLED
Entity ID
https://[host]/
SLO endpoint
Not Specified
SLO response endpoint
Not Specified
SLO binding
HTTP POST
Assertion validity duration
300
Target Application URL
Not Specified
Enforce signed Authn request
Disabled
Verification certificate
No Verification Certificates Selected
[host] is the hostname or IP of your Aviatrix controller. For example, https://controller.demo.aviatrix.live.
[Endpoint Name] is an arbitrary identifier. This same value should be used when configuring SAML in the Aviatrix controller.
[Entity ID] is using https://[host]/ as default if you select the
Hostnameoption when configuring SAML in the Aviatrix Controller.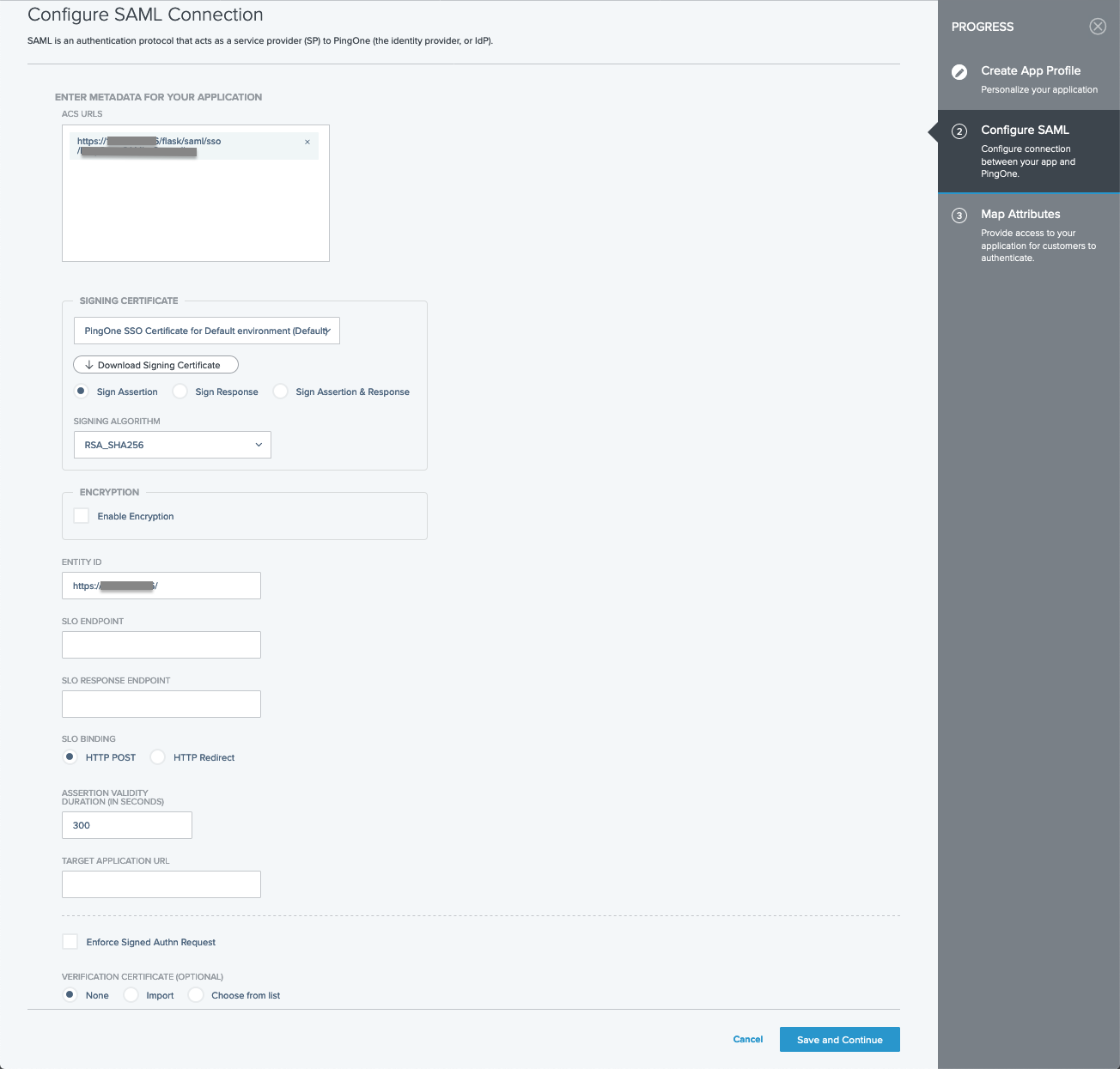
-
Click Save and Continue.
-
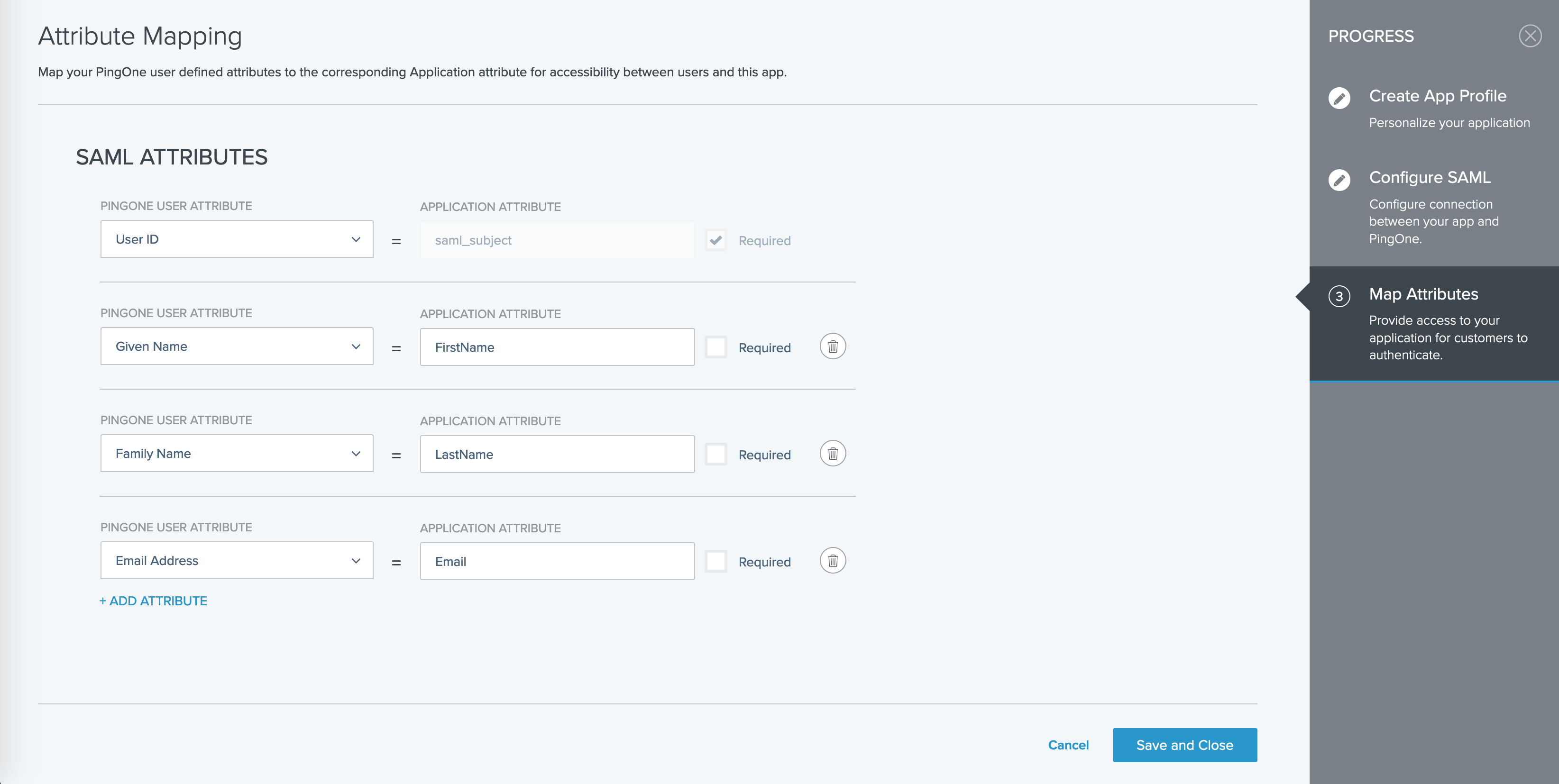
For attribute mapping, click the button "+ADD ATTRIBUTE" and then select "PingOne Attribute" to map PingOne user attribute to an attribute in this application as below.
PingOne User Attribute Application Attribute User ID (required)
saml_subject
Given Name
FirstName
Family Name
LastName
Email Address
Email
-
Click Save and Close.
-
Enable the WEB SAML APP.
Step 3. Retrieve PingOne IdP metadata
| This step is usually completed by the PingOne for Customers admin. |
-
After the application is created in PingOne, click Connections on the top of the page and then click Applications on the left.
-
Locate the Web SAML application that we just created.
-
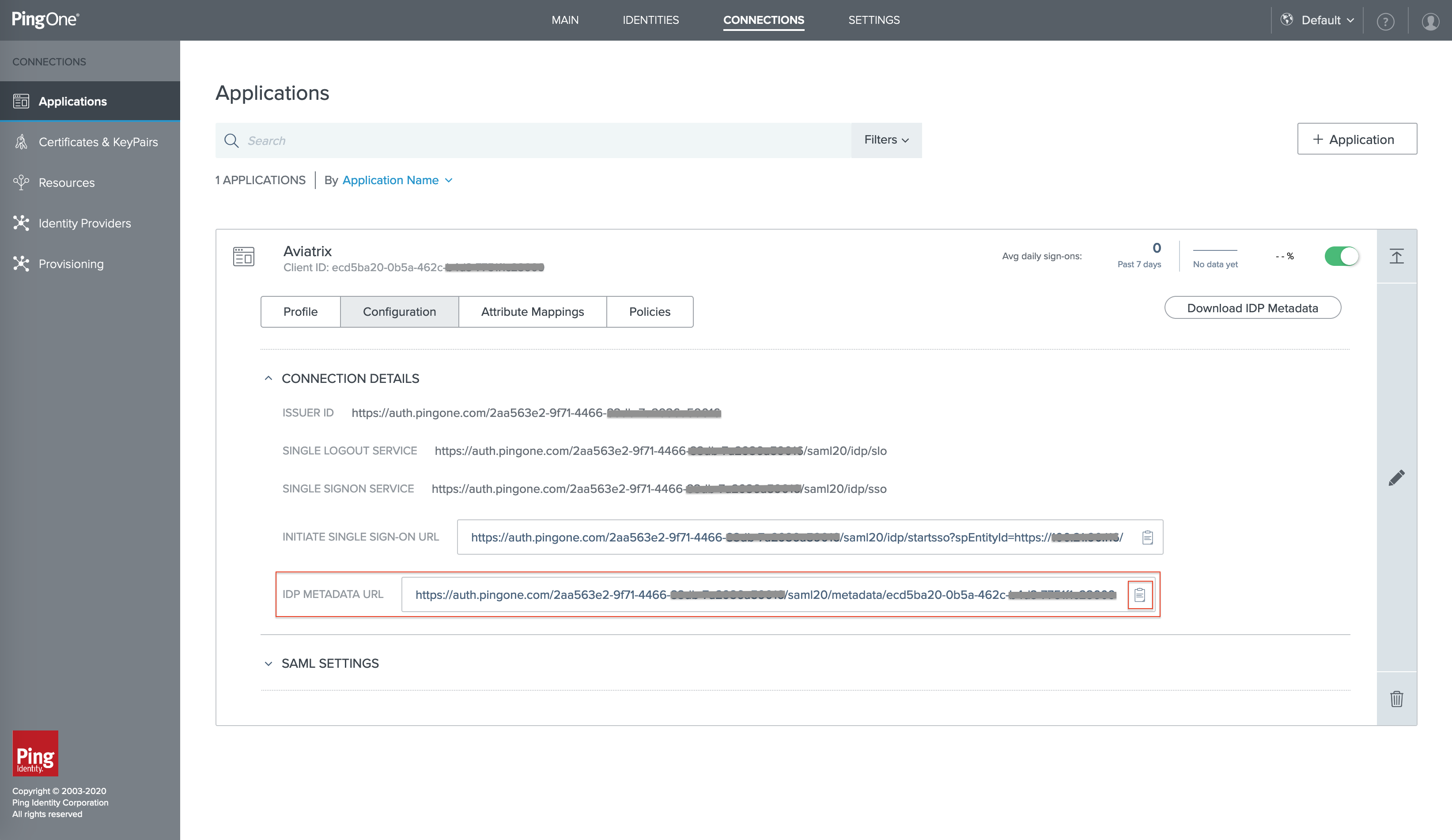
Click the details icon to expand the Web SAML application and then click the button "Configuration".
-
Copy the URL from the IDP Metadata URL from the CONNECTION DETAILS. This value will be used to configure the Aviatrix SP Endpoint.
Step 4. Update Aviatrix SP Endpoint
| This step is usually completed by the Aviatrix admin. PineOne IdP provides IdP Metadata through URL obtained in Retrieve `PingOne IdP metadata URL <#pingone-idp-metadata>`__ step. PingOne for Customers IdP requires a custom SAML request template. |
Continue with updating Aviatrix SAML Endpoint by visiting one of the following links based on your use case:
-
If integrating PineOne IdP with Controller Login SAML Config.
-
If integrating PineOne IdP with OpenVPN with SAML Authentication.
| Field | Value |
|---|---|
Endpoint Name |
[Endpoint Name]: use the same name you previously entered in the PingOne application |
IdP Metadata Type |
URL |
IdP Metadata URL |
URL copied from PingOne (IdP metadata URL) |
Entity ID |
Select Hostname |
Custom SAML Request Template |
Check the box and either copy the below format into the prompt text box or modify it |
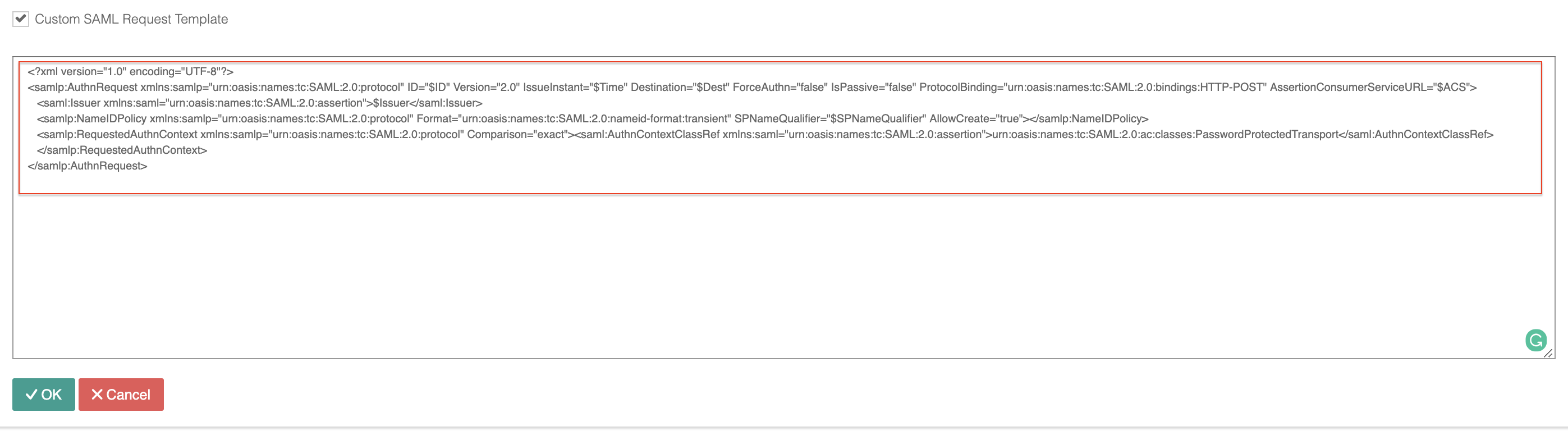
<?xml version="1.0" encoding="UTF-8"?> <samlp:AuthnRequest xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol" ID="$ID" Version="2.0" IssueInstant="$Time" Destination="$Dest" ForceAuthn="false" IsPassive="false" ProtocolBinding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" AssertionConsumerServiceURL="$ACS"> <saml:Issuer xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion">$Issuer</saml:Issuer> <samlp:NameIDPolicy xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol" Format="urn:oasis:names:tc:SAML:2.0:nameid-format:transient" SPNameQualifier="$SPNameQualifier" AllowCreate="true"></samlp:NameIDPolicy> <samlp:RequestedAuthnContext xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol" Comparison="exact"><saml:AuthnContextClassRef xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion">urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport</saml:AuthnContextClassRef> </samlp:RequestedAuthnContext> </samlp:AuthnRequest>
Step 5. Test the Integration
Continue with testing the integration by visiting one of the following links based on your use case:
-
If integrating PingOne IdP with Controller Login SAML Config:
-
Click Settings in the left navigation menu.
-
Select Controller.
-
Click on the SAML Login tab.
-
-
If integrating PingOne IdP with OpenVPN with SAML Authentication:
-
Expand
OpenVPN®in the navigation menu and click Advanced. -
Stay on the SAML tab.
-
You can quickly validate that the configuration is complete by clicking on the Test button next to the SAML endpoint.
OpenVPN is a registered trademark of OpenVPN Inc.