Creating Distributed Cloud Firewall Rules
After creating your groups, you create Distributed Cloud Firewall (DCF) rules within one of the system-defined rulesets to define the access control to apply on the traffic between those groups.
|
If your SmartGroups contain Spoke Gateways, ensure that those Spoke Gateways have Egress enabled. |
| If you have upgraded to Controller 8.0, you can use the Policies tab to create and manage DCF rulesets. |
For example, in the workload isolation use case, all traffic (i.e., ports and protocols) between the ShoppingCart application and the Product Logging app must be blocked (Denied). You can decide which policies to enforce, and if you want to log the actions related to a rule. These rules are enforced (if enabled) on your Spoke gateways, and are executed against the Spoke gateways in the order that they are shown in the rule list.
Creating a rule for the workload isolation use case would resemble the following:
-
Source Group: Shopping Cart application
-
Destination Group: Product Logging app
-
Action: Deny
-
Protocol: Any
-
Ports: 0-65535 (Any)
-
Logging: Off
-
Enforcement: On
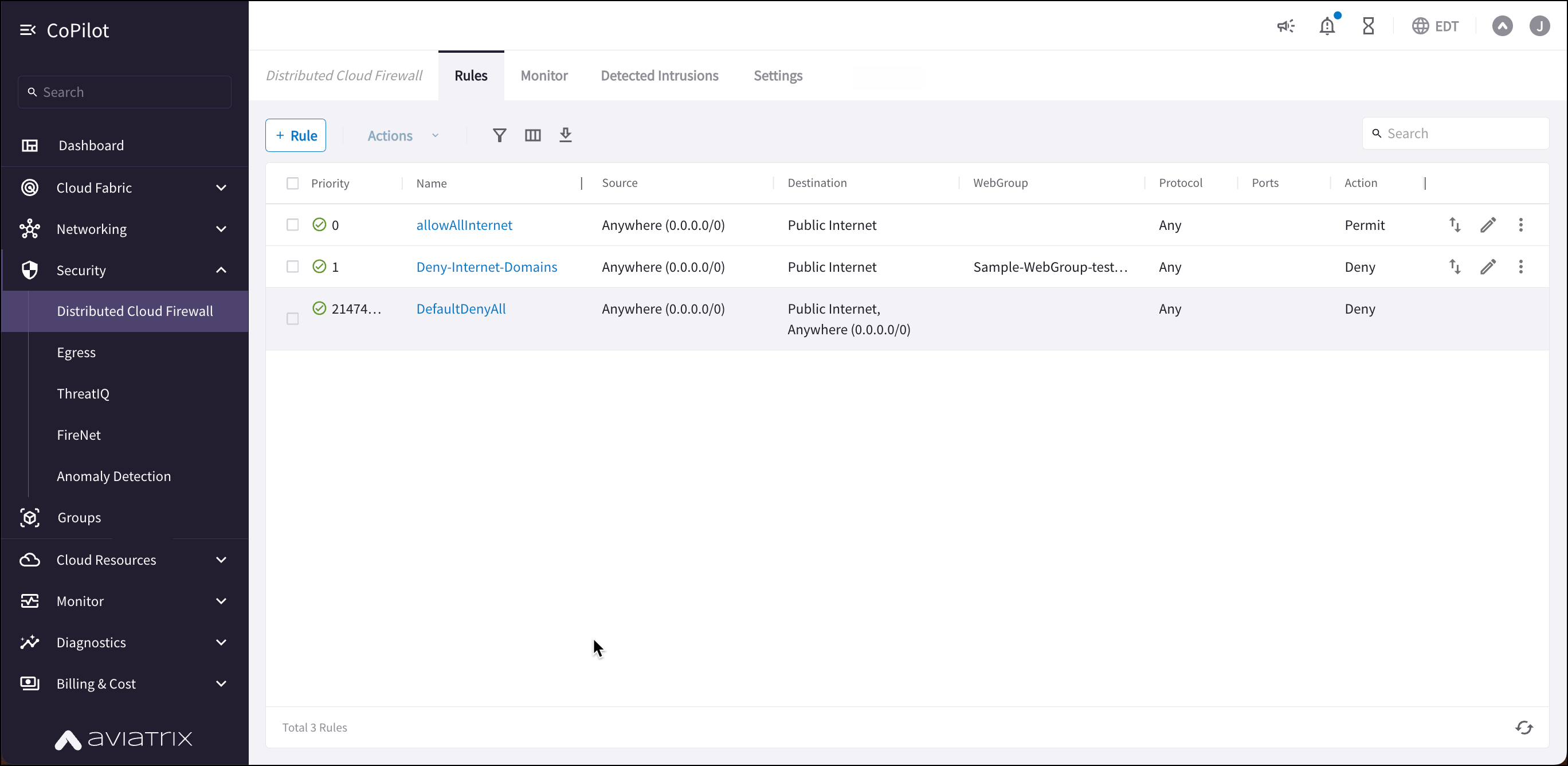
To create a new Distributed Cloud Firewall rule:
-
In CoPilot, navigate to Security > Distributed Cloud Firewall > Policies.
-
Select a ruleset from the Ruleset list.
-
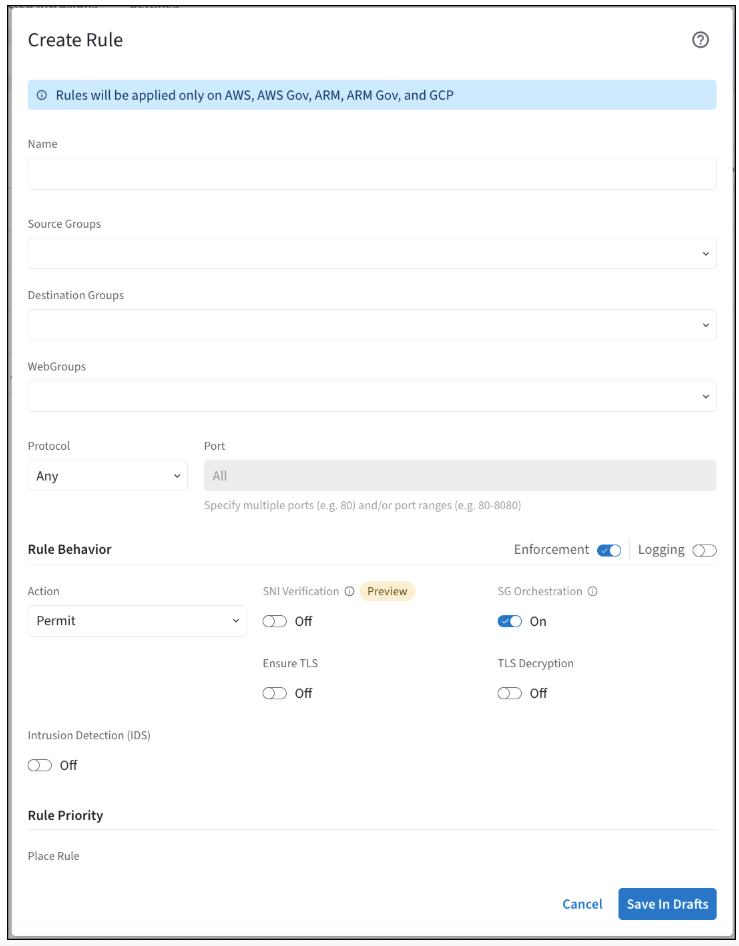
Click + Rule. The Create Rule dialog displays.
-
Use the Distributed Cloud Firewall Field Reference to create your rule.
|
If the Rule Behavior Action is Deny, the SNI Verification toggle is not displayed. The SNI Verification feature is only available with Controller 8.0. |
Tips for Rule Creation
-
Always specify the port and protocol for HTTP/TLS or non-HTTP/TLS when the domain names overlap.
-
Or, you can prioritize HTTP/TLS rules in the DCF Rules list (but this means that non-TLS/HTTP traffic will always be pulled through the web proxy).
-
Save any changes on the Policies tab (changes to logging or enforcement) before switching to another ruleset.
-
When configuring TLS Decryption in DCF, note that while the configuration is applied per rule, its operation is global. Once a connection is decrypted to check a URL filter, it remains decrypted even if it does not match that rule’s filter. The connection may match a later rule without decryption requirements, but it will already be decrypted due to the earlier rule. Therefore, carefully consider the placement of rules requiring decryption.
Viewing DCF Rule Details
You can click a DCF rule on the Security > Distributed Cloud Firewall > Policies tab to view its configuration details, source and destination entities, and statistics in the right-hand pane.
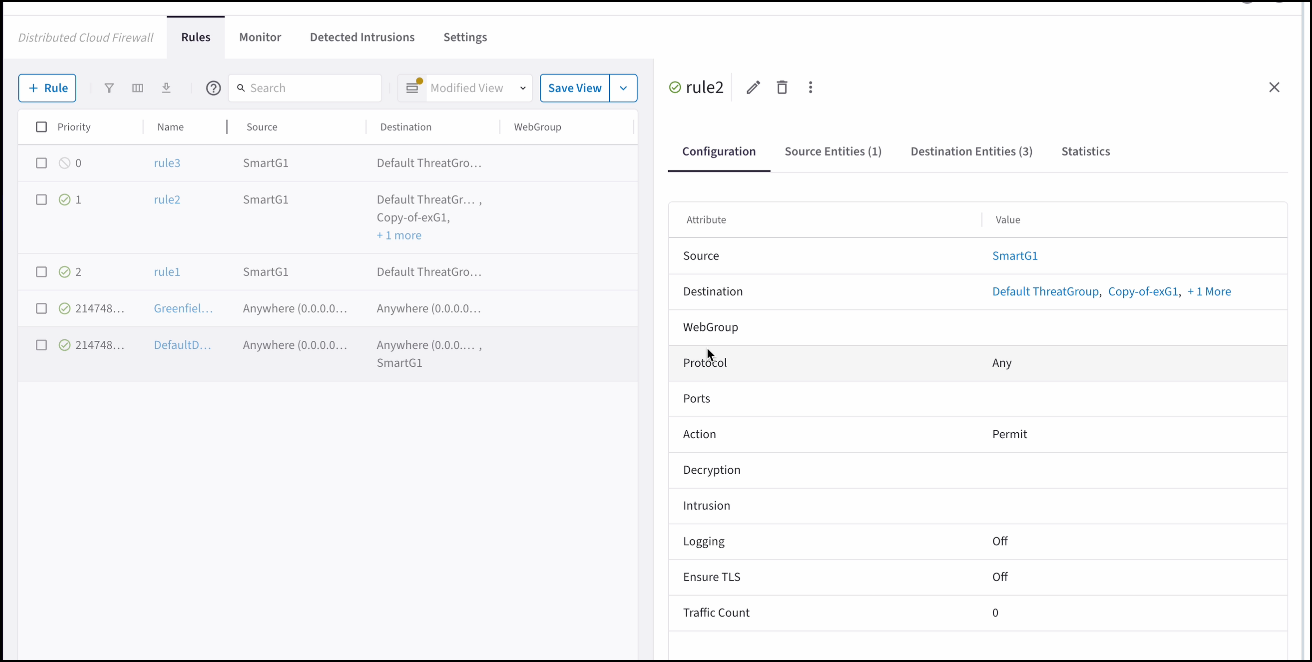
The Groups tab in the details pane shows the Source Entities, Destination Entities, and WebGroups used in the rule. The Statistics tab shows the number of hits for the rule, and the last time it was hit.