GCP Multi-Peer BGP over LAN Workflow
Introduction
Transit BGP to LAN allows Aviatrix Transit Gateways to communicate with multiple instances in the same VPC in GCP without running any tunneling protocol such as IPsec or GRE. One use case is to interoperate with third-party virtual appliances such as SD-WAN cloud instances that do not have the capability to support BGP over any tunneling protocols.
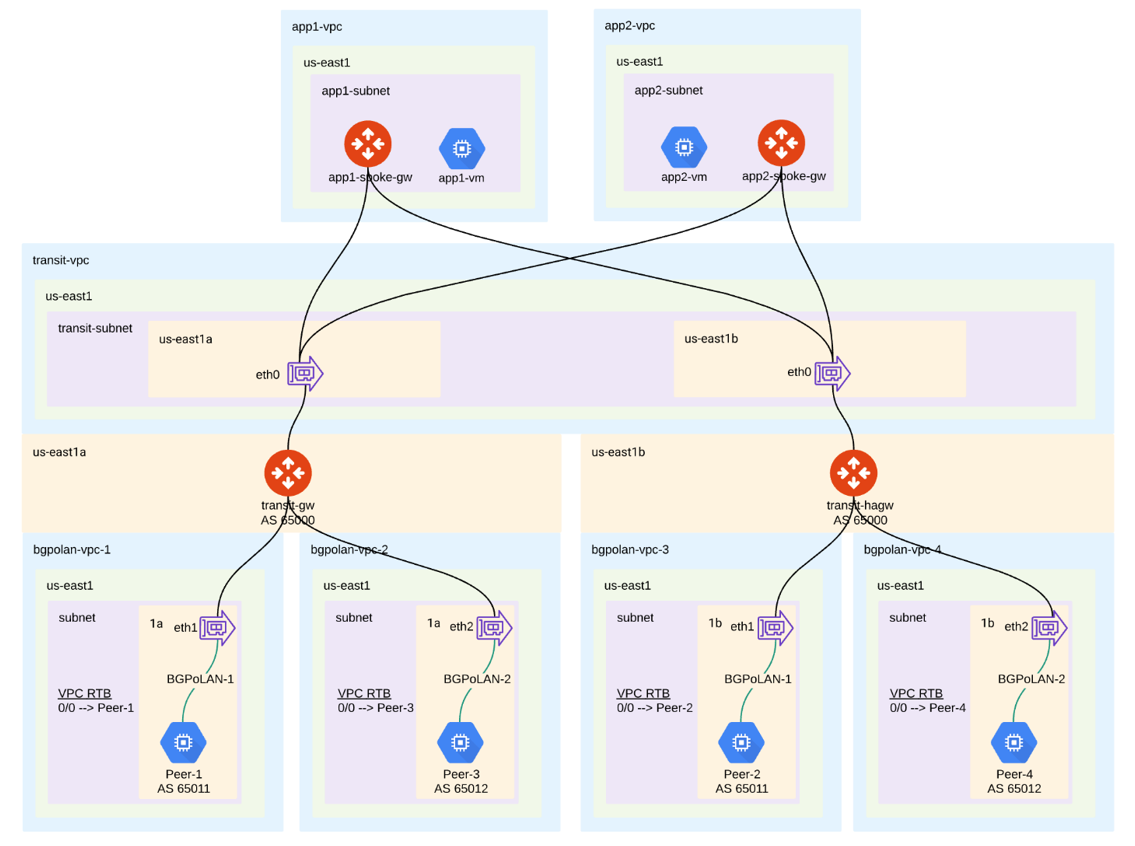
For example, integrating with SD-WAN gateways can be deployed as below, where Aviatrix Multicloud Transit Gateways connect to third-party cloud instances in the same VPC in GCP:
This document describes a step-by-step instruction on how to build Aviatrix Transit Gateway to External Device using BGP over LAN. In this Tech Note, you will learn the following:
-
Workflow on deploying Aviatrix Transit Solution
-
Workflow on launching third-party cloud instances
-
Workflow on building BGP over LAN
For other BGP over LAN workflows, see the documents below:
For more information about Multicloud Transit Network and External Device, see the documents below:
|
The key ideas for this solution are:
-
A BGP session establishes between third-party cloud instances and Aviatrix Transit Gateways via each LAN interface in the same VPC.
-
Dataplane traffic also runs between third-party cloud instances and Aviatrix Transit Gateways via each LAN interface without a tunnel protocol such as IPsec or GRE.
Prerequisite
-
This feature is available starting in Aviatrix software version 6.6. Upgrade Aviatrix Controller to at least version 6.6.
-
Third-party cloud instance has high throughput supported.
Deploying Aviatrix Multicloud Transit Solution
Refer to Global Transit Network Workflow Instructions for the below steps. Please adjust the topology depending on your requirements.
-
Deploy Aviatrix Multicloud Transit Gateway and HA with High Performance Encryption Mode encryption enabled in Transit VPC.
-
Deploy Spoke Gateway and HA with High Performance Encryption Mode encryption enabled in Spoke VPC(s).
Launching Third-Party Cloud Instances
Deploy third-party cloud instances with an interface in the same VPC as the Aviatrix Transit Gateway.
-
Create a third-party cloud instance and put MGMT interface in public gateway subnet.
-
Create a new WAN subnet and dedicated routing table for WAN interface if needed.
-
Create a new LAN subnet and a dedicated routing table for the LAN interface.
-
Make sure the IP forwarding function is enabled on the third-party cloud instances.
|
GCP allows a maximum of 8 interfaces per instance, and the max limit depends on the number of vCPUs. Due to this limitation, the solution supports 7 BGP peers without FireNet enabled and 6 BGP peers with FireNet enabled. |
Building BGP over LAN
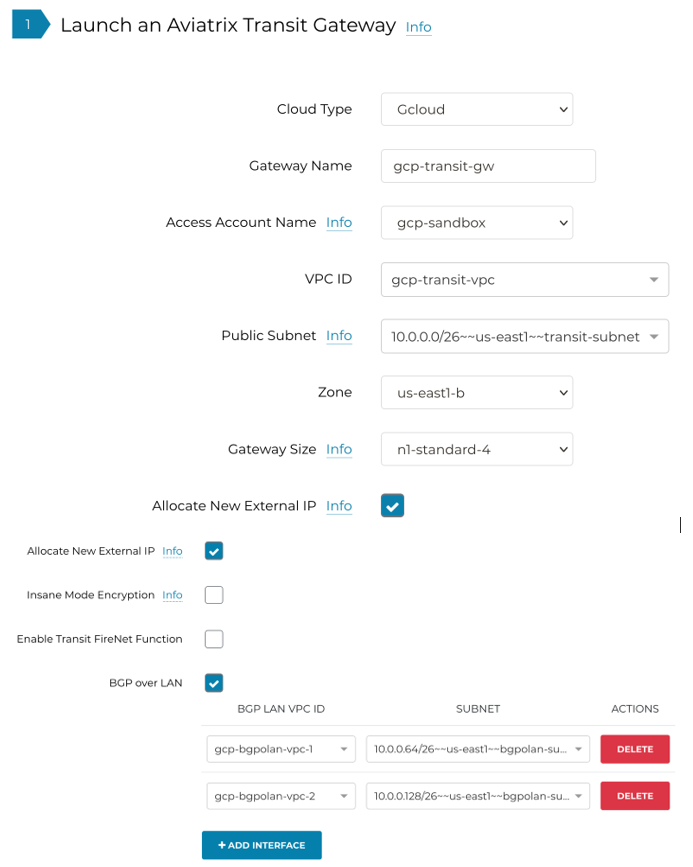
Deploy the Aviatrix Transit Gateway with all the required BGP interfaces.
-
Log in to the Aviatrix Controller.
-
Navigate to Multi-Cloud Transit > Setup > Transit tab.
-
Set the parameters to deploy the Aviatrix Transit Gateway.
| Cloud Type | GCloud |
|---|---|
Gateway Name |
Provide a unique name to identify the Transit Gateway |
Access Account Name |
Select the appropriate GCP account |
VPC ID |
Select the VPC where the Transit Gateway will be deployed |
Public Subnet |
Select the subnet the Transit Gateway interface will use |
Zone |
Select the Availability Zone where the Transit Gateway will be deployed |
Gateway Size |
Select an instance size that allows interfaces to be created for all BGP peers |
High Performance Encryption Mode |
Check this box to enable high throughput |
BGP over LAN |
Check this box and then Add Interface for all BGP peers |
Enable HA on the Aviatrix Transit Gateway, deploying the HA Gateway in a different Availability Zone.
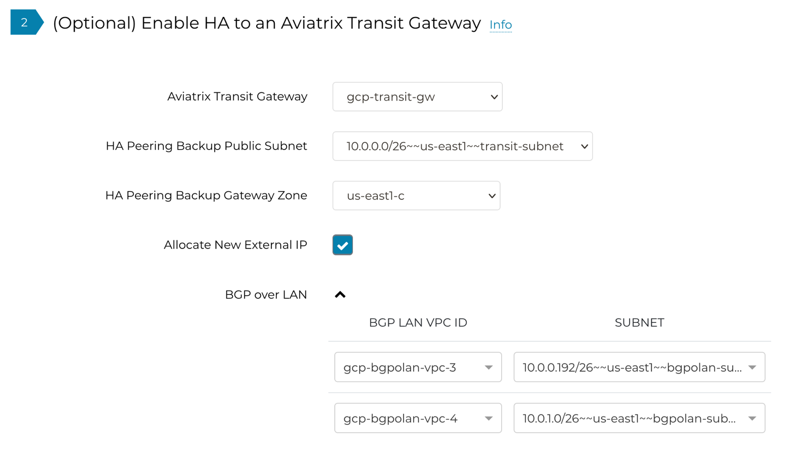
Configuring BGP over LAN on Aviatrix Transit Gateway
-
Log in to the Aviatrix Controller.
-
Navigate to Multi-Cloud Transit > Setup > External Connection tab > Connect to VGW / External Device / Azure VNG section.
-
Select the options External Device > BGP > LAN.
-
Enter the following information in the fields below.
VPC Name / Site ID |
Select the Transit VPC ID where the Transit Gateway was deployed. |
Connection Name |
Provide a unique name to identify the connection to external device. |
Aviatrix Gateway BGP ASN |
Configure a BGP AS number that the Transit Gateway will use to exchange routes with the external device. |
Primary Aviatrix Gateway |
Select the Transit Gateway. |
Enable Remote Gateway HA |
Check this box to connect two external devices. |
BGP Activemesh |
Check this box to enable full mesh BGP connections to the external devices. |
Remote BGP AS Number |
Configure the BGP AS number that the third-party cloud instance will use to exchange routes with the Aviatrix Transit Gateway. |
Remote LAN IP |
Use the private IP of the LAN interface of the third-party cloud primary instance. |
Local LAN IP |
If blank, the controller will assign an IP in the same subnet as the Remote LAN IP. Optionally, configure a specific IP within the same subnet as the Remote LAN IP. |
Remote BGP AS Number (Backup) |
Configure the BGP AS number that the third-party HA cloud instance will use to exchange routes with the Aviatrix HA Transit Gateway. |
Remote LAN IP (Backup) |
Use the private IP of the LAN interface of the third-party HA cloud instance. |
Local LAN IP (Backup) |
If blank, the controller will assign an IP in the same subnet as the Remote LAN IP (Backup). Optionally, configure a specific IP within the same subnet as the Remote LAN IP (Backup). |
-
Click Connect to generate the BGP sessions.
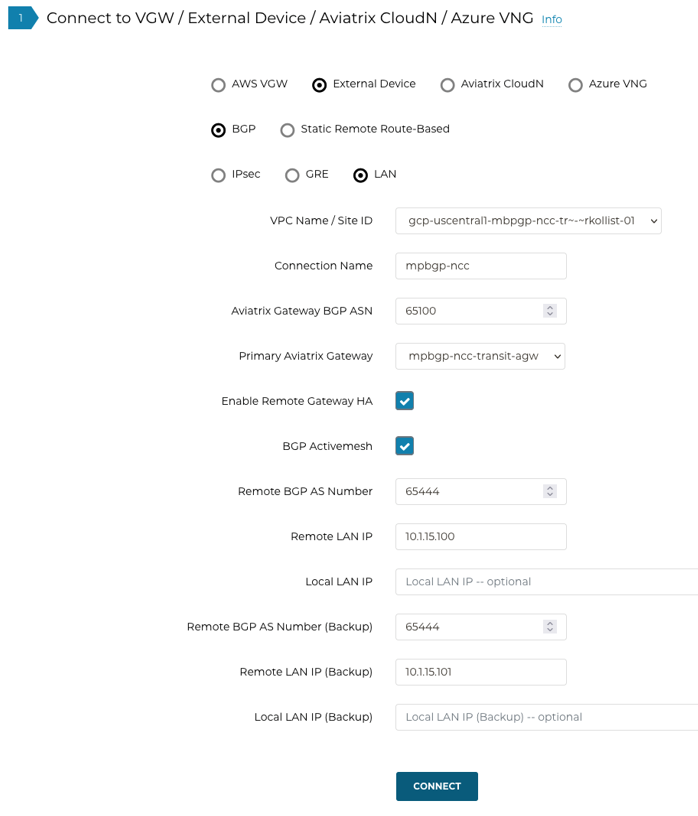
-
Create a Site2Cloud connection for each BGP peer.
(Optional) Downloading the BGP over LAN configuration sample from Aviatrix Controller
-
Navigate to Site2Cloud > Setup.
-
Select the previously created connection(s).
-
Click Edit.
-
Select the Vendor, Platform and Software that correspond to the third-party device.
-
Click Download Configuration.
Configuring BGP over LAN on the Third-Party Cloud Instance(s)
-
(Optional) Open the downloaded BGP over LAN configuration file.
-
Configure the relevant BGP over LAN information on the third-party cloud instance(s).
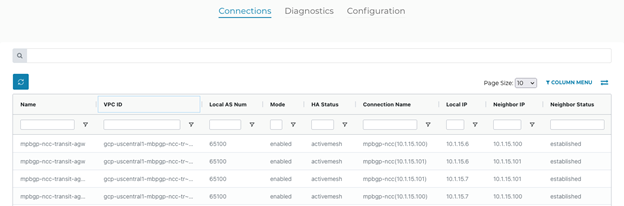
Verifying the Connection Status on Aviatrix Controller
-
Navigate to Site2Cloud > Setup.
-
Find the previously created connection(s).
-
Check the tunnel status.
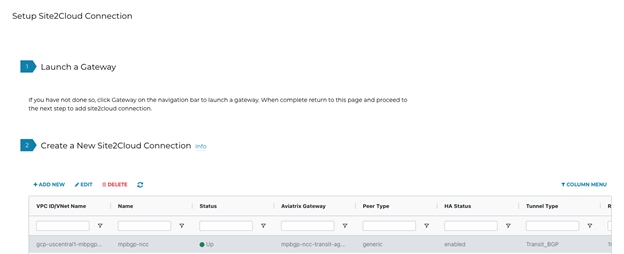
-
Navigate to Multi-Cloud Transit → List.
-
Select the previously created Aviatrix Transit Gateway.
-
Click Details/Diag.
-
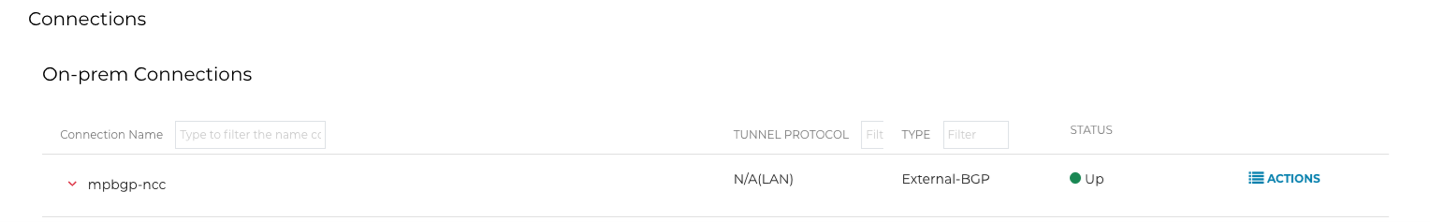
Scroll down to the Connections > On-prem Connections section.
-
Under On-prem Connections, find the previously created connection(s).
-
Check the tunnel status in the Status column.