Configuring Azure Multi-Peer BGP Over LAN Workflow
Introduction
This document provides step-by-step instructions for building BGP over LAN connections between an Aviatrix Transit Gateway and one or more External Devices in Azure.
Transit BGP over LAN allows Aviatrix Transit Gateways to communicate with multiple instances in different VNets in Azure without running any tunneling protocol such as IPsec or GRE. One use case is to interoperate with third-party virtual appliances such as SD-WAN cloud instances that do not have the capability to support BGP over any tunneling protocols. For example, integrating with SD-WAN gateways can be deployed as below, where Aviatrix Multi-Cloud Transit Gateways connect to third-party cloud instances in another VNet in Azure.
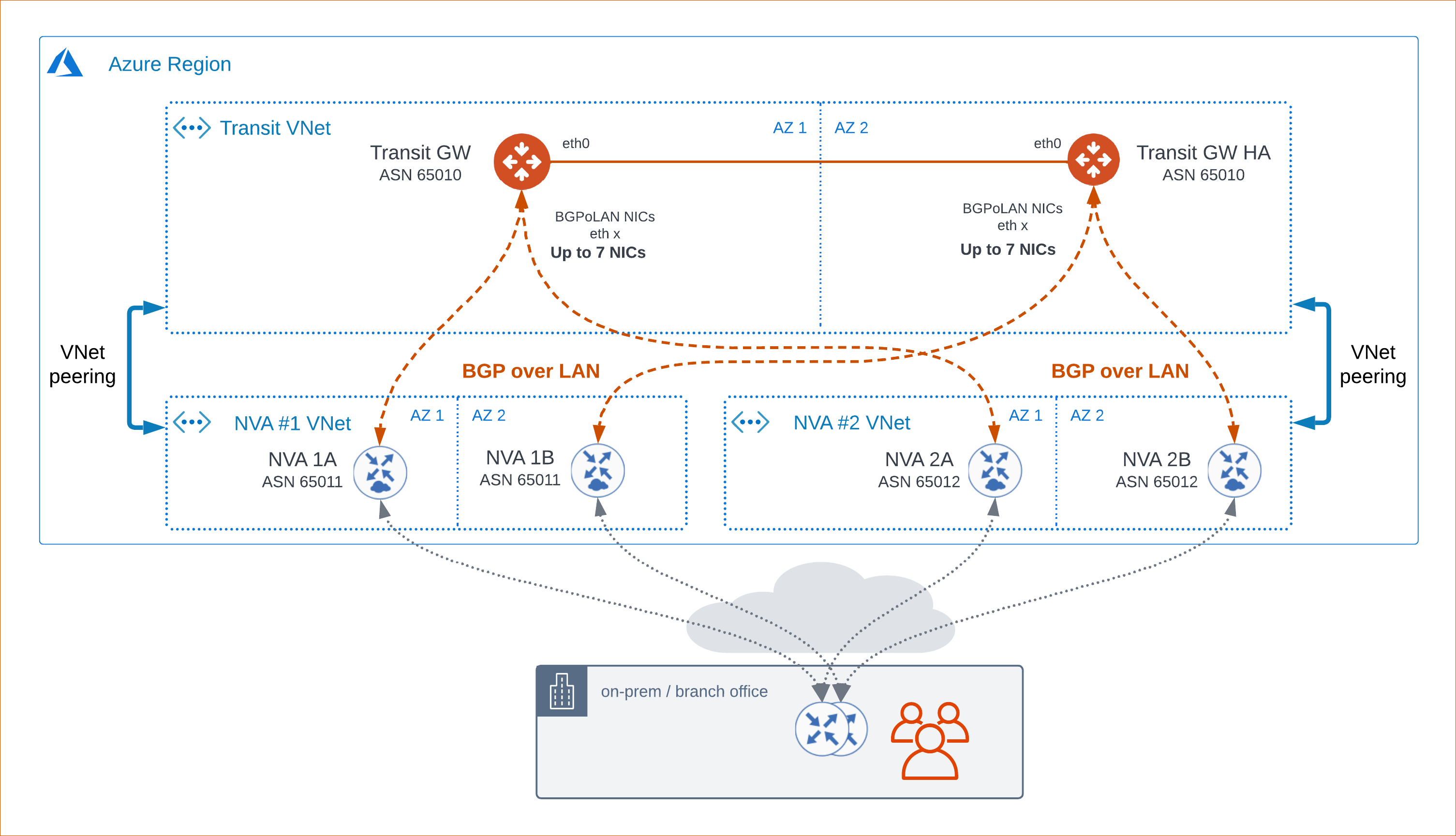
Prerequisites
-
Aviatrix Controller is updated to software version 6.8 or above.
-
Transit Gateways are deployed with BGPoLAN enabled with the required number of interfaces, which is based on the number of BGP over LAN connections you need.
-
In the single-attach use case, each BGP peer requires one BGPoLAN NIC on a single Aviatrix Transit Gateway.
-
In the dual-attach use case—that is, a scenario where the BGP peer needs to establish a BGP session to both Transit Gateways for high-availability reasons—a single BGP peer requires one BGPoLAN NIC on both Aviatrix Transit Gateways.
Deploying Aviatrix Multi-Cloud Transit Solution
Refer to Global Transit Network Workflow Instructions for more detailed instructions for the steps below. Adjust the topology depending on your requirements.
-
Deploy Aviatrix Multicloud Transit Gateway and HA with Insane Mode encryption enabled in the Transit VNet.
-
Deploy a Spoke Gateway. If desired, you can deploy this gateway with HA and enable Insane Mode encryption in the Spoke VNet(s). Note that HA and Insane Mode are not required.
Building BGP over LAN
Deploy the Aviatrix Transit Gateway with all the required BGP interfaces.
-
Log into the Aviatrix Controller.
-
Navigate to Multi-Cloud Transit > Setup > Transit.
-
Use the settings below to deploy the Aviatrix Transit Gateway.
| Setting | Value |
|---|---|
Cloud Type |
Azure ARM |
Gateway Name |
Provide a unique name to identify the Transit Gateway. |
Access Account Name |
Select the appropriate Azure account. |
VNet Name: Resource Group |
Select the VNet where the Transit Gateway will be deployed. |
Public Subnet |
Select the subnet the Transit Gateway will use. |
Gateway Size |
Select an instance size that allows interfaces to be created for all BGP peers. |
Allocate New IP |
Select this checkbox if you want to allocate a new EIP. |
EIP |
If you choose to use an existing EIP, enter it here. |
Insane Mode Encryption |
Select this checkbox to enable HPE (High Throughput Encryption). HPE is mandatory when configuring BGP over LAN for a Transit Gateway deployed in Azure. |
Enable Transit FireNet Function |
Select this checkbox to enable Transit FireNet. |
BGP over LAN |
Select this checkbox to enable BGP over LAN functionality. |
Add/Edit Tags |
Select this checkbox to add additional tags. |
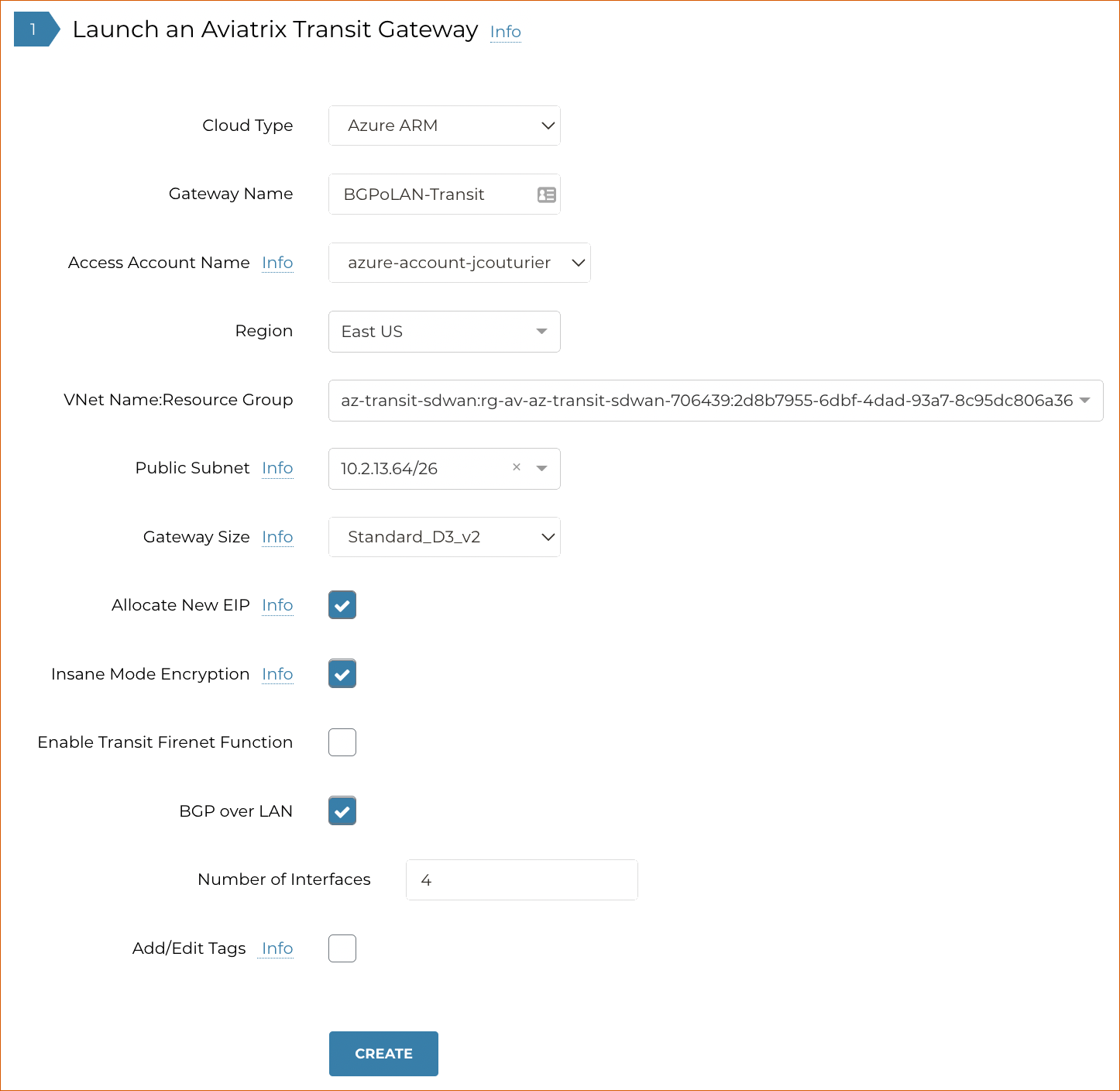
-
Click Create.
-
(Optional) If you want to enable HA to an Aviatrix Transit Gateway, complete Step 2 of the UI workflow - Enable/Disable HA to an Aviatrix Transit Gateway.
Configuring BGP over LAN on Aviatrix Transit Gateway
-
Log into the Aviatrix Controller.
-
Navigate to Multi-Cloud Transit > Setup > External Connection tab.
-
Select the following radio buttons: External Device > BGP > LAN.
-
Enter the following information in the fields provided.
| Setting | Value |
|---|---|
VPC Name/Site ID |
Select the Transit VNet ID where the Transit Gateway was deployed. |
Connection Name |
Provide a unique name to identify the connection to the external device. |
Aviatrix Gateway BGP ASN |
Provide the BGP AS Number that is configured on the Transit Gateway that will be used to exchange routes with the external device. |
Primary Aviatrix Gateway |
Select the Transit Gateway. |
Enable Remote Gateway HA |
Select this checkbox to connect two external devices configured as an HA pair. |
BGP ActiveMesh |
Select this checkbox to enable full mesh BGP connections to the external devices from the primary and HA Transit gateways. Only to be used for Azure Route Server Integration. |
Remote BGP AS Number |
Configure the BGP AS Number that the third-party Cloud instance will use to exchange routes with the Aviatrix HA Transit gateway. |
Remote LAN IP |
Enter the private IP of the LAN interface of the third-party Cloud primary instance. |
Local LAN IP |
The Controller will automatically show the IP assigned to the BGPoLAN interface that will be used for this specific peering. |
Remote BGP AS Number (Backup) |
Enter the BGP AS Number that the third-party HA Cloud instance will use to exchange routes with the Aviatrix HA Transit Gateway. |
Remote LAN IP (Backup) |
Enter the private IP of the LAN interface of the third-party HA Cloud instance |
Local LAN IP (Backup) |
The Controller will automatically show the IP assigned to the BGPoLAN interface that will be used for this specific peering. |
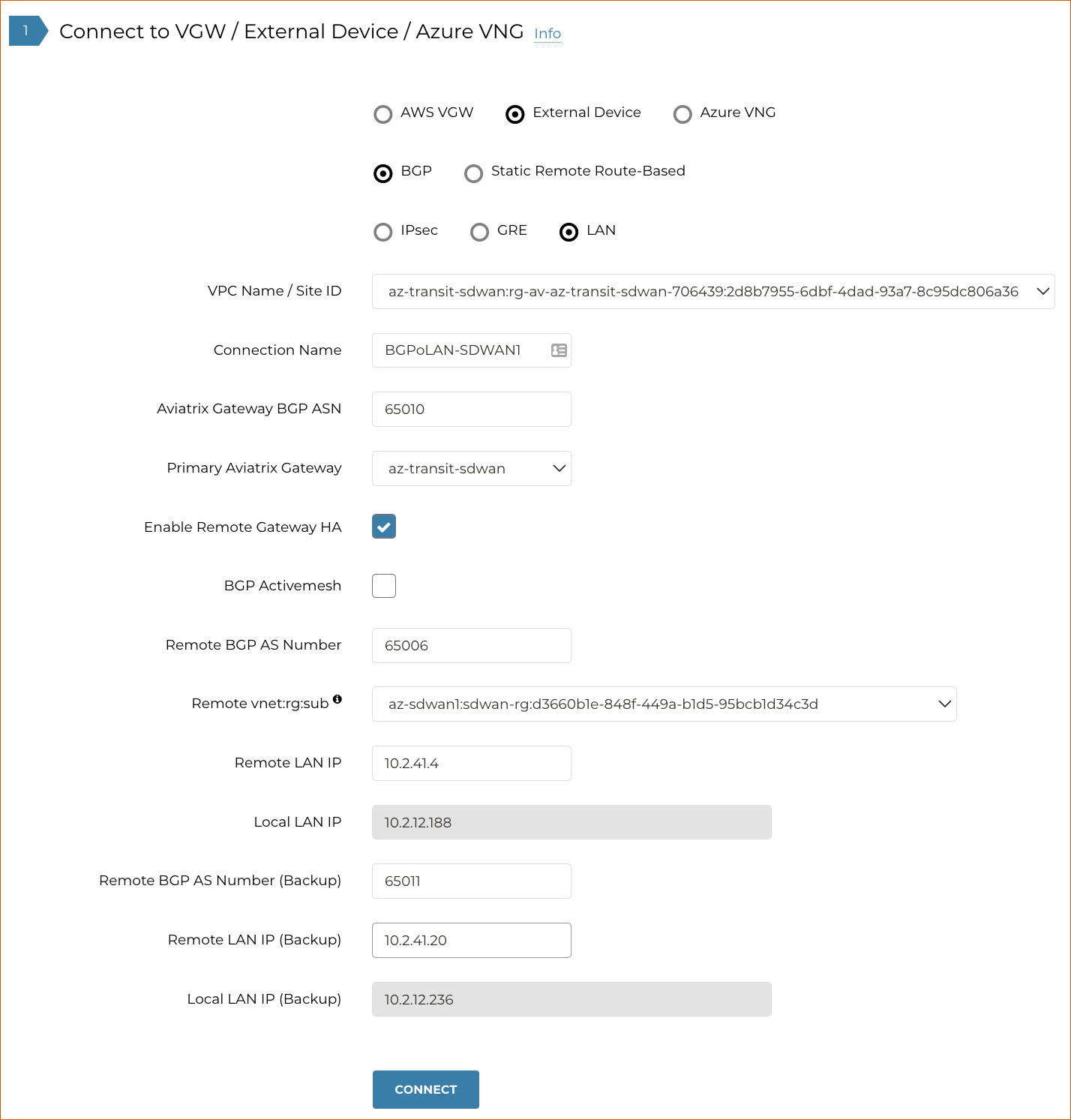
-
Click Connect to generate the BGP sessions.