Transit FireNet Workflow for AWS, Azure, GCP, and OCI
If you want to deploy firewall networks in an AWS TGW environment, your starting point is AWS TGW FireNet Workflow.
-
For a complete step-by-step guide on AWS for Transit FireNet, refer to Transit FireNet on AWS Configuration Example Guide.
-
For a complete step-by-step guide on AWS for Transit FireNet with AWS Gateway Load Balancer (GWLB), refer to Transit FireNet Workflow with AWS Gateway Load Balancer (GWLB).
-
For a complete step-by-step guide on Azure for Transit FireNet, refer to Transit FireNet on Azure Configuration Example Guide.
-
For a complete step-by-step guide on GCP for Transit FireNet, refer to Transit FireNet on GCP Configuration Example Guide.
-
For a complete step-by-step guide on OCI for Transit FireNet, refer to Transit FireNet on OCI Configuration Example Guide.
Prerequisite for AWS
Transit FireNet builds on the Aviatrix Transit Network where Aviatrix Gateways are deployed in both the transit VPC and the spoke VPCs in AWS. Make sure the deployment meets the following specifications.
-
ActiveMesh 2.0 is required (enabled by default from release 6.0 onward). To migrate to ActiveMesh 2.0, see Migrating from Classic Aviatrix Encrypted Transit Network to Aviatrix ActiveMesh Transit Network.
-
The minimum size of the Aviatrix Transit Gateway is c5.xlarge.
-
Aviatrix Transit Network must be in Connected mode. Go to Transit Network > Advanced Config > Connected Transit. Click Enable.
Follow the Aviatrix Transit Network workflow to deploy Aviatrix Transit Gateways and at least one Spoke Gateway. When complete, proceed to Step 1.
Prerequisites for Azure
Transit FireNet builds on the Aviatrix Transit Network solution where Aviatrix Gateways are deployed in Transit VNet and/or in Spoke VNet in Azure. Make sure the deployment meets the following specifications.
-
ActiveMesh 2.0 is required (enabled by default in release 6.0 onward). To migrate to ActiveMesh 2.0, see Migrating from Classic Aviatrix Encrypted Transit Network to Aviatrix ActiveMesh Transit Network.
-
The minimum size of the Aviatrix Transit Gateway instance size is Standard_B2ms.
-
Select the Enable Transit FireNet option when launching the Aviatrix Transit Gateway.
-
Aviatrix Transit Network must be in Connected mode. Go to Transit Network > Advanced Config > Connected Transit. Click Enable.
Follow the Aviatrix Transit Network workflow to deploy Aviatrix Transit Gateways and attach at least one Spoke Gateway or one Spoke VNet. When you are done, proceed to Enabling Transit FireNet Function below.
Prerequisites for GCP
Transit FireNet builds on the Aviatrix Transit Network solution where Aviatrix Gateways are deployed in Transit VPC and/or in Spoke VPC in GCP. Make sure the deployment meets the following specifications.
-
A minimum of four VPCs will be required for the GCP FireNet solution with Palo Alto VM-series and all VPCs should be in same region.
-
The minimum size of the Aviatrix Transit Gateway instance size is n1-standard_1.
-
Select the Enable Transit FireNet option when launching the Aviatrix Transit Gateway.
-
Aviatrix Transit Network must be in Connected mode. Go to Multi-Cloud Transit > Advanced Config > Connected Transit. Slide the toggle to Enabled.
Follow the Aviatrix Transit Network workflow to deploy Aviatrix Transit Gateways and attach at least one Spoke Gateway or one Spoke VNet. When you are done, proceed to Enabling Transit FireNet Function below.
Prerequisites for OCI
Transit FireNet builds on the Aviatrix Transit Network solution where Aviatrix Gateways are deployed in Transit VCN and/or in Spoke VCN in OCI.
Make sure the deployment meets the following specifications:
-
Select the Enable Transit FireNet option when launching the Aviatrix Transit Gateway.
-
Aviatrix Transit Gateway minimum instance size should be VM.Standard2.4 or more.
Follow the Aviatrix Transit Network workflow to deploy Aviatrix Transit Gateways and attach at least one Spoke Gateway. When you are done, proceed to Enabling Transit FireNet Function below.
|
Transit FireNet High Performance Encryption mode is not supported in Release 6.4. |
Enabling Transit FireNet Function
A Transit FireNet Gateway is an Aviatrix Transit Gateway with FireNet service enabled.
Starting from Release 6.0, an Aviatrix Spoke can be optionally attached to two Transit FireNet Gateways, one for east-west and north-south traffic inspection, and another for ingress/egress inspections.
Enabling Transit FireNet on Aviatrix Transit Gateway
This step defines a set of Aviatrix Transit FireNet Gateways.
In the Aviatrix Controller, navigate to Firewall Network > Setup > Transit Firenet. In the 3a dropdown menu, select one Aviatrix Transit Gateway and click Enable.
|
For Azure and GCP deployment, Transit FireNet function is enabled when launching the gateway, skip this step. |
By default, east-west and north-south traffic inspections are enabled on Transit FireNet Gateways, you can also enable Ingress/Egress inspection on the Transit FireNet Gateways. To do so, go to Firewall Network > Advanced > click the 3 dots skewer of one FireNet Gateway, enable Egress through firewall option.
A deployment diagram in this option is shown as below:
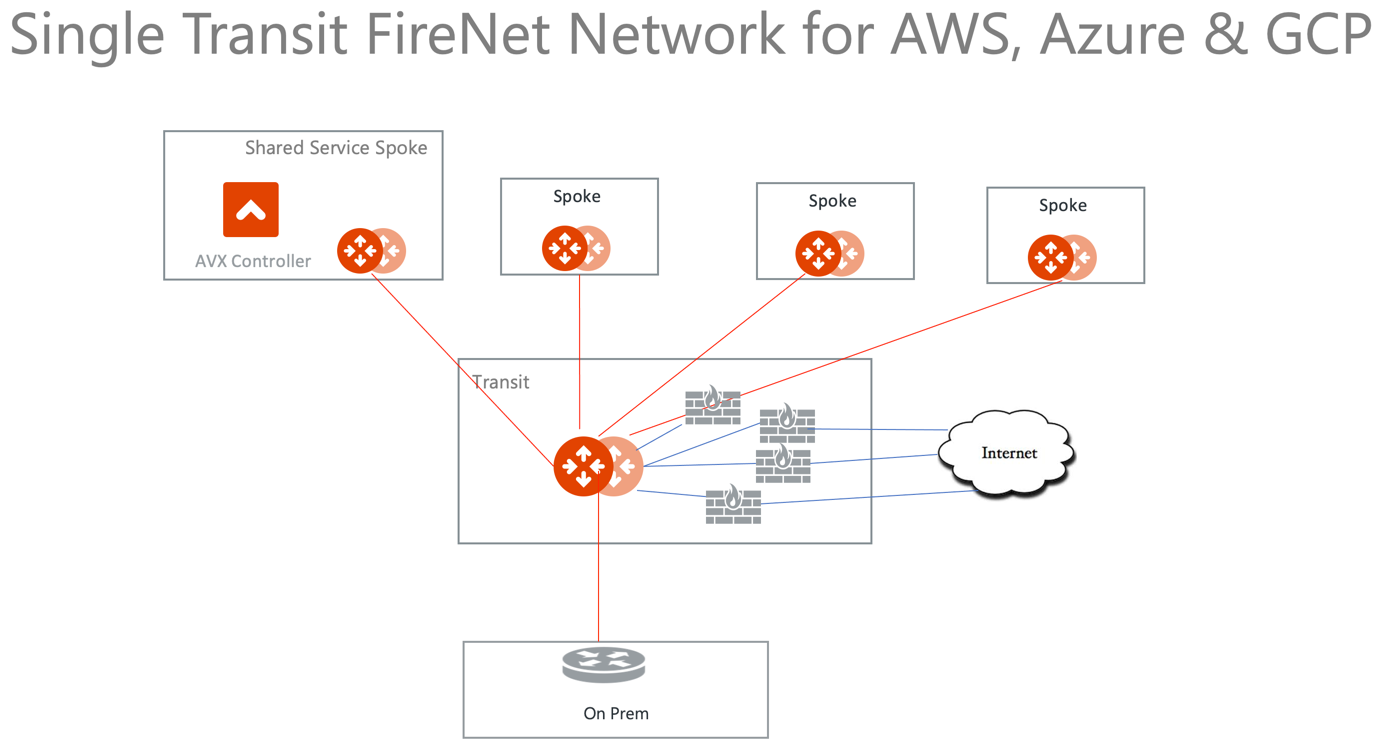
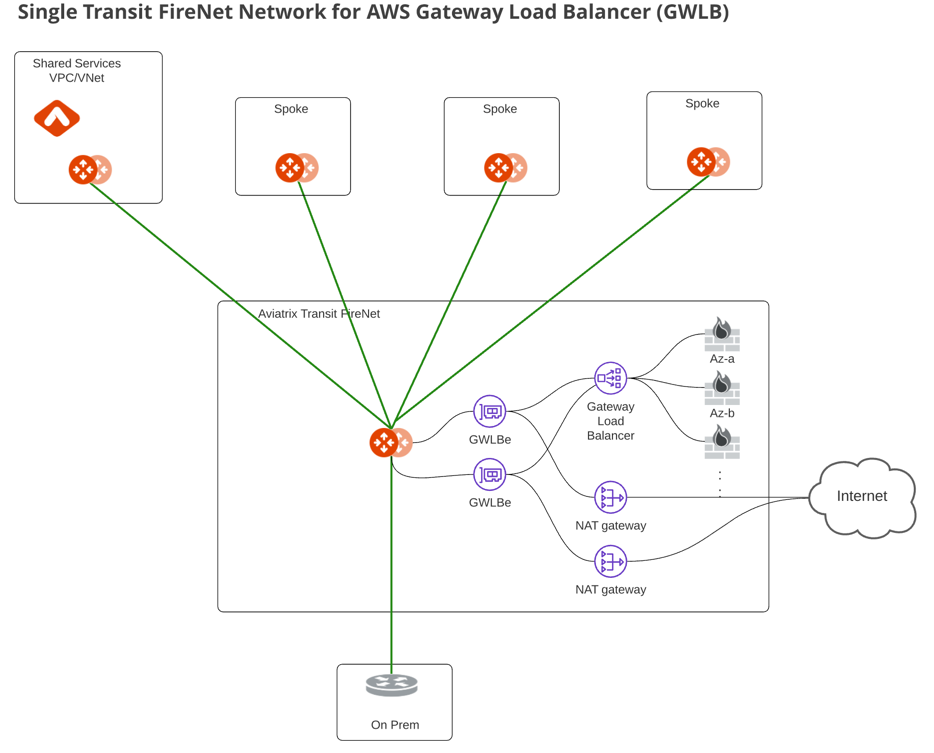
Aviatrix Transit FireNet also supports the AWS Gateway Load Balancer (AWS GWLB).
In order to use the Aviatrix Transit FireNet solution with AWS GWLB, select one Aviatrix Transit Gateway deployed in AWS from the dropdown menu, select the Use AWS GWLB checkbox and click Enable.
|
IAM policies need to be updated for ingress/egress traffic. Go to Aviatrix Controller > Accounts > Access Accounts > Select AWS Account and click Update Policy. |
|
Transit FireNet solution with GWLB also requires HTTPS port enabled on the firewall appliance to check the firewall health status at regular intervals. Click Enable Health Check Policy in Firewall for more information. |
By default, east-west and north-south traffic inspections are enabled on Transit FireNet Gateways.
You can also enable Ingress/Egress inspection on the Transit FireNet Gateways:
-
In the Aviatrix Controller, navigate to Firewall Network > List > Firenet.
-
Select a Transit FireNet and click Details. You can then enable the Egress through Firewall option.
A deployment diagram in this option is shown as below:
Enabling Transit FireNet on Aviatrix Egress Transit Gateway
If you plan to use one set of Transit FireNet Gateways for all traffic types' inspection, skip this step.
If a separate group of firewalls for Ingress/Egress traffic inspection is required, you need to deploy a second set of Aviatrix Transit Gateways called Aviatrix Egress Transit Gateway, shown as the diagram below.
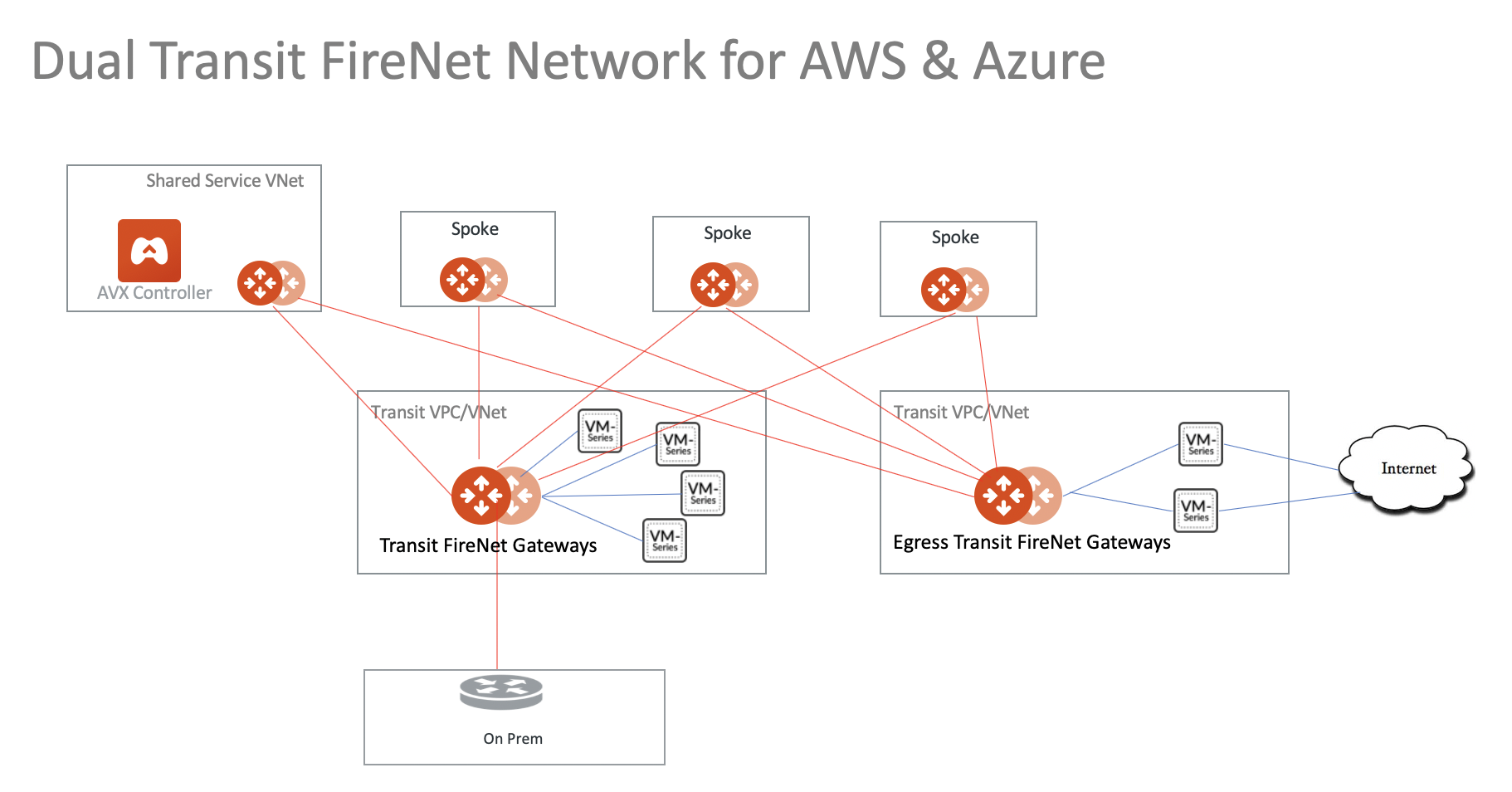
This step defines a set of Aviatrix Egress Transit FireNet Gateways. The HA Aviatrix Egress Transit FireNet Gateway is automatically enabled in this step.
Managing Transit FireNet Policy
Select an Aviatrix Transit Gateway that you enabled for FireNet function in the previous step.
On the left side of the Manage Transit Firenet Policy page (Firewall Network > Policy), highlight one Spoke VPC/VNet for inspection and click Add. The selected Spoke VPC/VNet is moved to the right panel.
For example, if traffic going in and out of VPC/VNet PROD1 where gcp-spkgw-1 is deployed should be inspected, move the gcp-spkgw-1 to the right, as shown below.
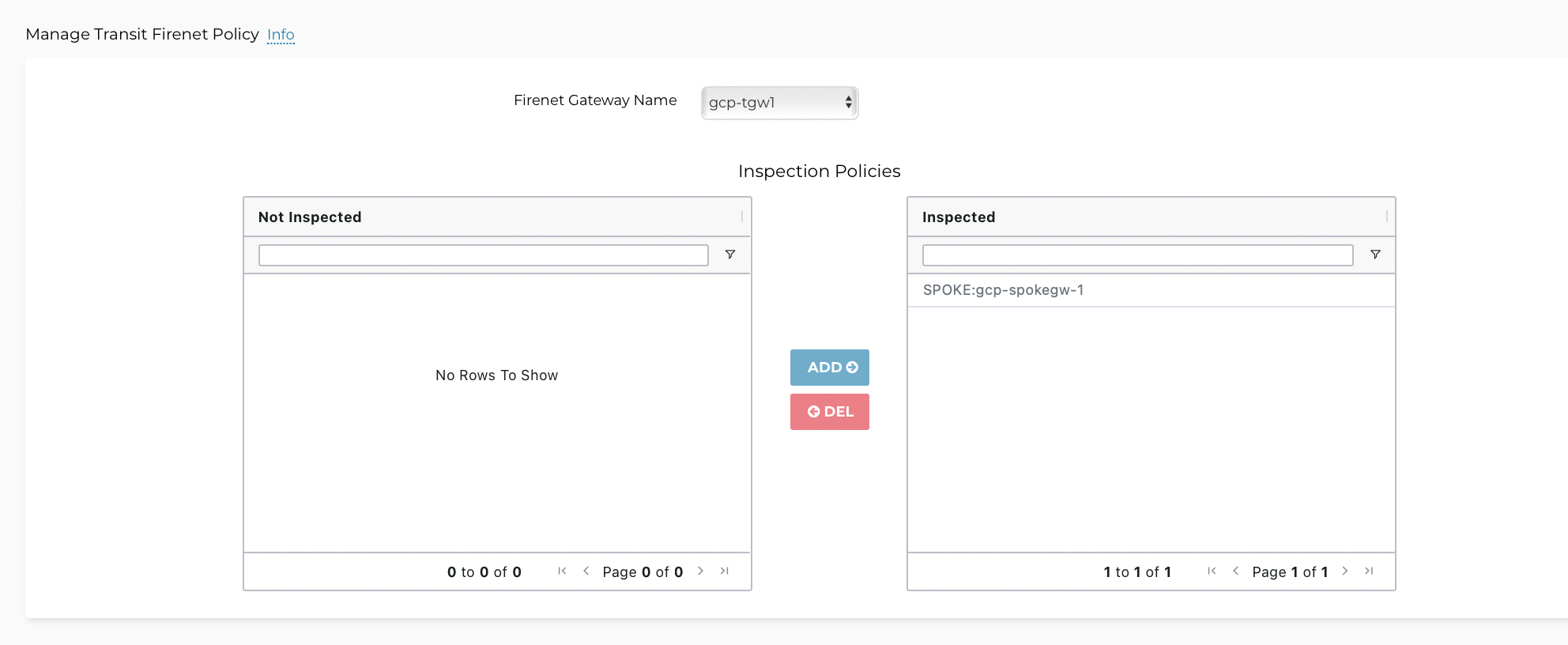
To add more VPC/VNets for inspection, repeat this step.
Centralized FireNet for AWS
If you have configured Centralized FireNet for AWS, when you select a Transit FireNet that functions as a Primary FireNet, the Select Secondary FireNet checkbox displays if there are Secondary FireNets attached to the Primary.
Select a Secondary FireNet from the Secondary FireNet list and configure the inspection policies accordingly for the Secondary FireNet. These inspection policies are then propagated to the Primary FireNet. For more information see this section under "Configure Transit Firewall Network".
Deploying Firewall Instances
Go to Firewall Network > Setup > Deploy Firewall Network and follow the deployment instructions to launch one or more firewall instances.
Enabling Firewall Management Access
When this option is configured, Aviatrix Transit Gateway advertises the transit VPC/VNet CIDR to on-prem.
The use case is if a firewall management console, such as Palo Alto Networks Panorama is deployed on-prem, the Panorama can access the firewalls of their private IP addresses with this option configured.
Disable and Detach Function
In the dropdown menu, select one Aviatrix Transit Gateway with FireNet function to disable it. All of these functions are performed from the Firewall Network > Setup > Detach tab.
Disabling Transit FireNet on an Aviatrix Transit Gateway
Select a Transit FireNet Gateway and click Disable.
Disabling Transit FireNet on an Aviatrix Egress Transit Gateway
If an Aviatrix Egress Transit Gateway has been configured, select one and click Disable.
Detaching Secondary FireNet from Primary
Select the Primary FireNet from the Primary FireNet list and a Secondary FireNet from the Secondary FireNet list and click Detach. This will detach the selected Secondary FireNet from the Primary FireNet. If at least one Secondary FireNet is still attached to the Primary FireNet, the Centralized FireNet architecture still exists.