Aviatrix Gateway to Check Point(R77.30)
This document describes how to build an IPsec tunnel based Site2Cloud connection between Aviatrix Gateway and Check Point Firewall. To simulate an on-prem Check Point Firewall, we use a Check Point CloudGuard IaaS firewall VM at AWS VPC.
|
If you do not have access to AWS, you can simulate an on-prem Firewall by deploying the Palo Alto Firewall in any other cloud (such as Microsoft Azure, Google Cloud Platform, or Oracle Cloud Infrastructure). |
The network setup is as follows:
VPC1 (with Aviatrix Gateway)
VPC1 CIDR: 10.0.0.0/16
VPC1 Public Subnet CIDR: 10.0.1.0/24
VPC1 Private Subnet CIDR: 10.0.2.0/24
VPC2 (with Check Point Security Gateway)
VPC2 CIDR: 10.10.0.0/16
VPC2 Public Subnet CIDR: 10.10.0.0/24
VPC2 Private Subnet CIDR: 10.10.1.0/24
Launching Check Point Security Gateway VM
Refer to the http:/supportcontent.checkpoint.com/documentation_download?ID=45816[vSEC Gateway for Amazon Web Services Getting Started Guide] to launch a CheckPoint VM with at least two network interfaces. One interface serves as a WAN port and is in VPC2’s public subnet. The other interface serves as a LAN port and is in VPC2’s private subnet. Collect the public IP address of the WAN port.
Creating a Site2Cloud Connection at Aviatrix Controller
-
Go to Gateway > New Gateway to launch an Aviatrix Gateway at VPC1’s public subnet. Collect both public and private IP addresses of the Gateway.
-
Go to Site2Cloud and click Add New to create a Site2Cloud connection:
Field Value VPC ID/VNet Name
Choose VPC ID of VPC1
Connection Type
Unmapped
Connection Name
Arbitrary (e.g. avx-cp-s2c)
Remote Gateway Type
Generic
Tunnel Type
UDP
Algorithms
Unmark this checkbox
Encryption over DirectConnect
Unmark this checkbox
Enable HA
Unmark this checkbox
Primary Cloud Gateway
Select Aviatrix Gateway created above
Remote Gateway IP Address
Public IP of CheckPoint-VM WAN port
Pre-shared Key
Optional (auto-generated if not entered)
Remote Subnet
10.10.1.0/24 (VPC2 private subnet)
Local Subnet
10.0.2.0/24 (VPC1 private subnet)
-
Go to the Site2Cloud page. From the Site2Cloud connection table, select the connection created above (e.g. avx-cp-s2c). Select Generic from the Vendor dropdown list and click Download Configuration to download the Site2Cloud configuration. Save the configuration file for configuring CheckPoint-VM.
Downloading and Installing SmartConsole
-
Using a browser, connect to the Gaia Portal of the CheckPoint-VM at https:/CheckPoint-VM_Public-IP:
-
Click Overview at the left navigation bar, and then click Download Now! to download SmartConsole.
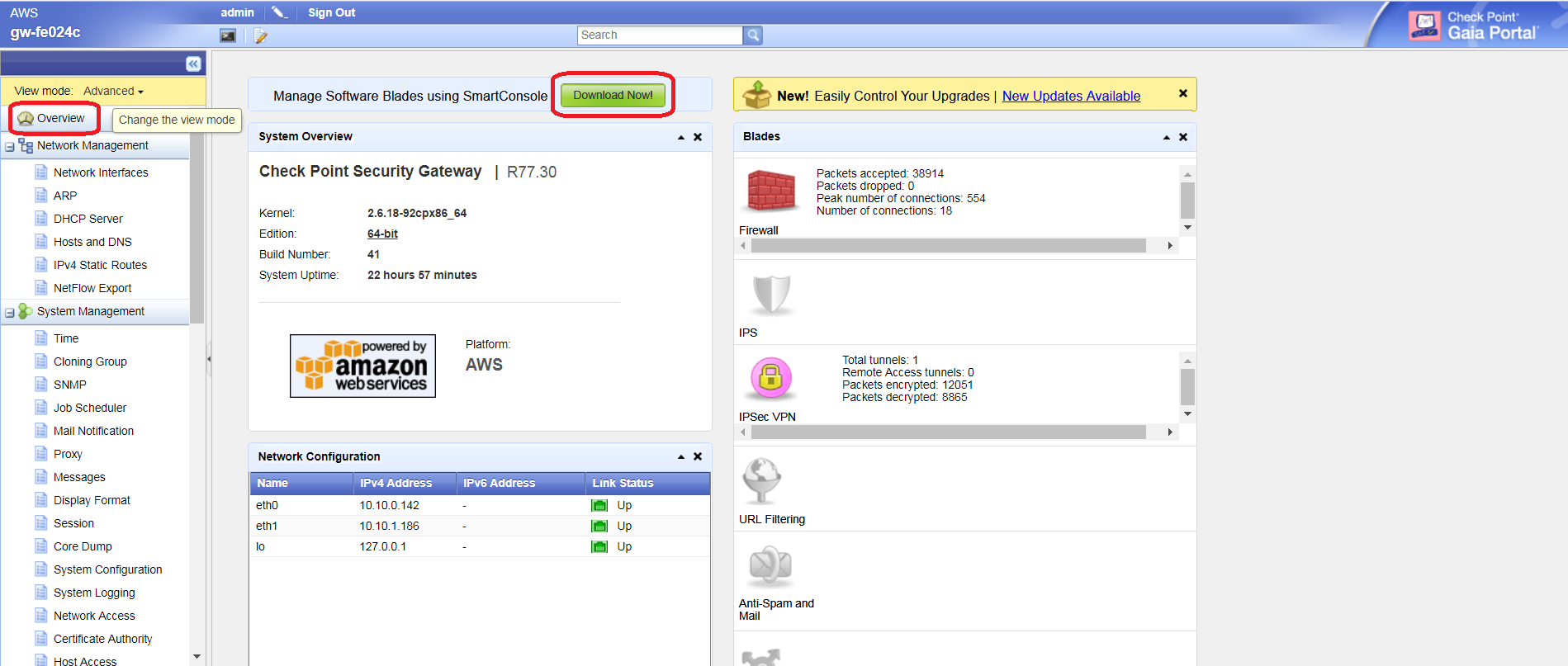
-
Install SmartConsole at your local machine and launch SmartDashboard.
Creating Network Objects at SmartConsole
-
At the Check Point SmartDashboard window, select the Desktop tab. Right click the Networks folder at the left navigation bar and select Network.
-
Create one network for private subnet of VPC2 (Check Point VPC).
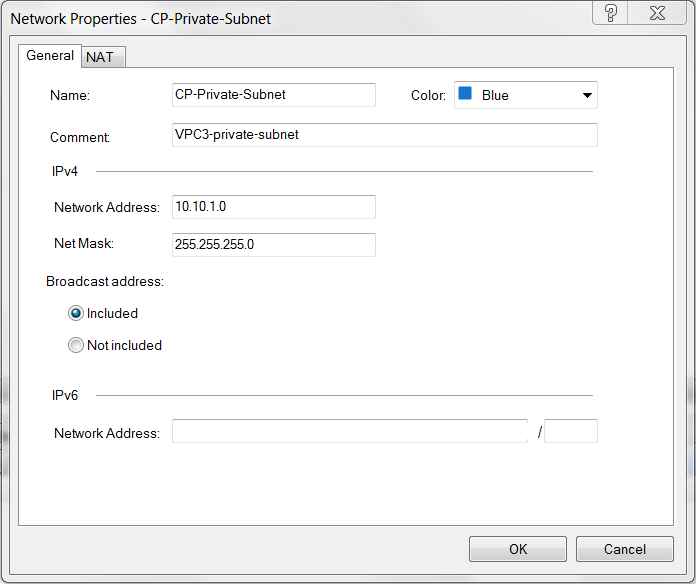
Field Value Name
Arbitrary (e.g. CP-Private-Subnet)
IPv4 Network Address
VPC2 private subnet CIDR
IPv4 Net mask
VPC2 private subnet mask
-
Create one network for private subnet of VPC1 (Aviatrix Gateway VPC).
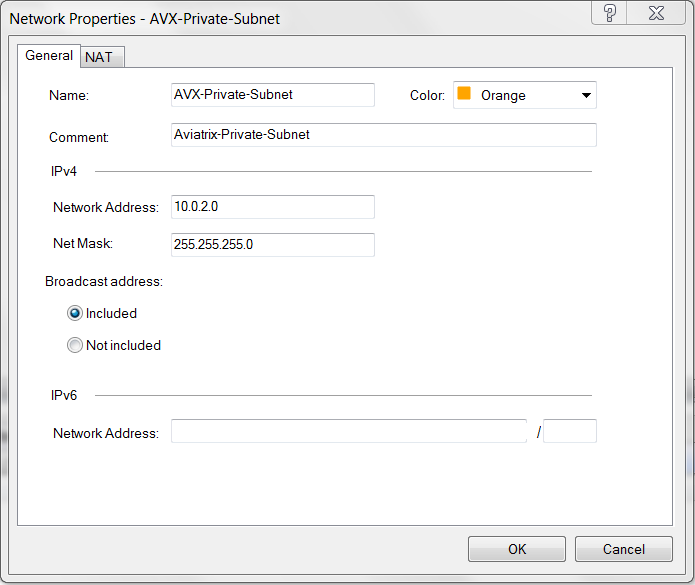
Field Value Name
Arbitrary (e.g. AVX-Private-Subnet)
IPv4 Network Address
VPC1 private subnet CIDR
IPv4 Net mask
VPC1 private subnet mask
Configuring Check Point Security Gateway with VPN
-
At the SmartDashboard window, select the Desktop tab and expand the Check Point folder at the left navigation bar. Note that your gateway VM with the name format "gw-xxxxxx" is automatically created.
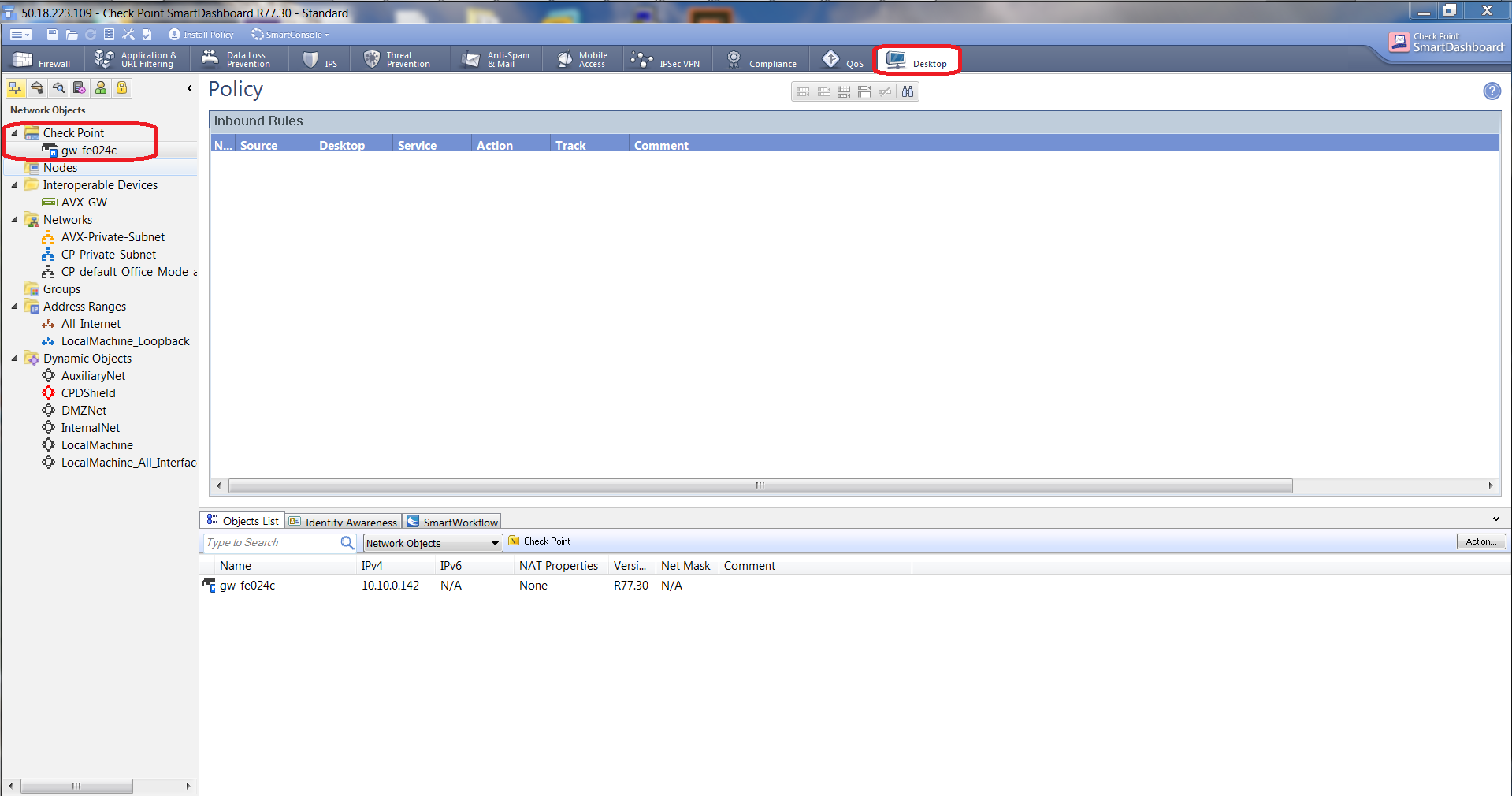
-
Right-click the gateway name and select Edit from the menu.
-
At the Check Point Gateway > General Properties window:
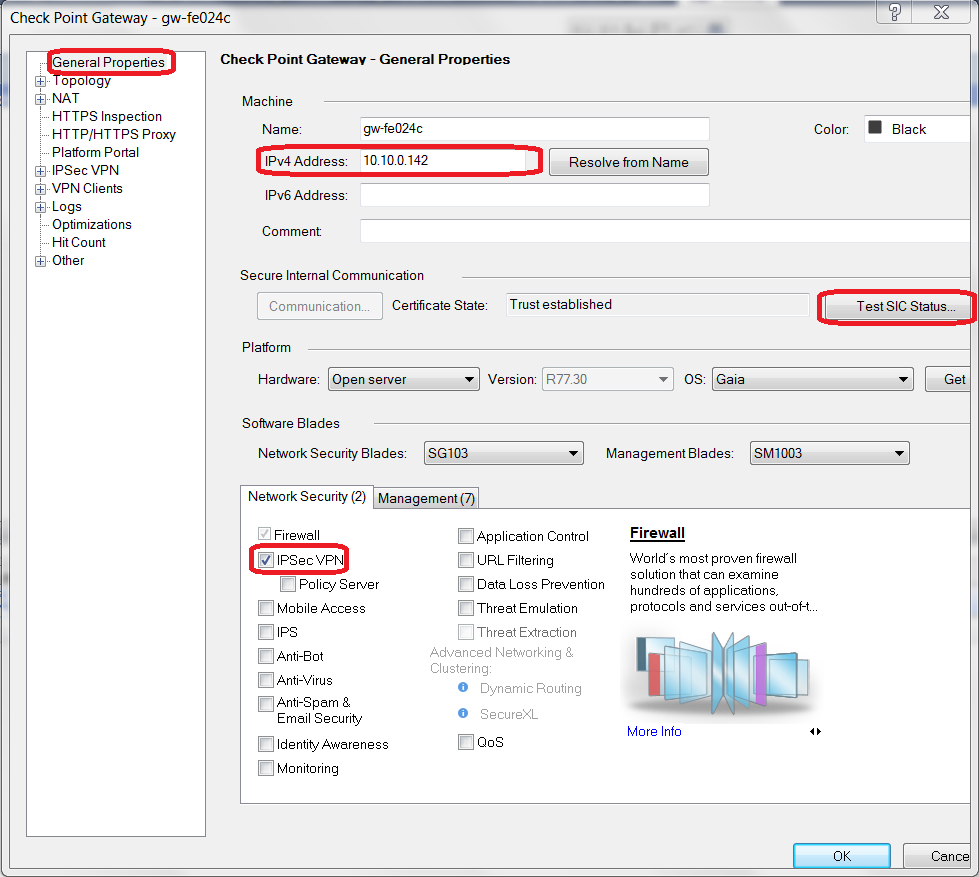
Field Value IPv4 Address
Private IP of CheckPoint VM WAN port
Test SIC Status
Make sure the status is "communicating"
Network Security
Select IPsec VPN
-
At Check Point Gateway - Topology window, select Manually defined for VPN Domain. Select the network created when you created a network for private subnet of VPC2 (Check Point VPC).
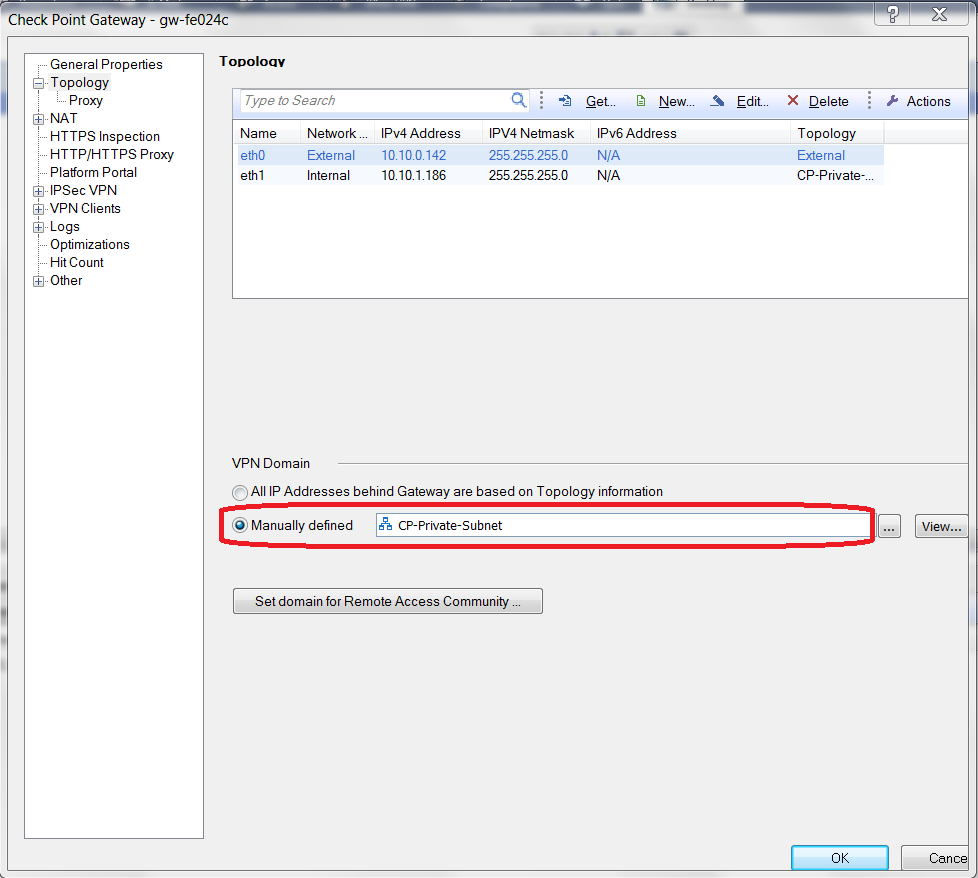
-
At Check Point Gateway - Topology window, double-click "eth0" (Check Point WAN port). Select External (leads out to the Internet).
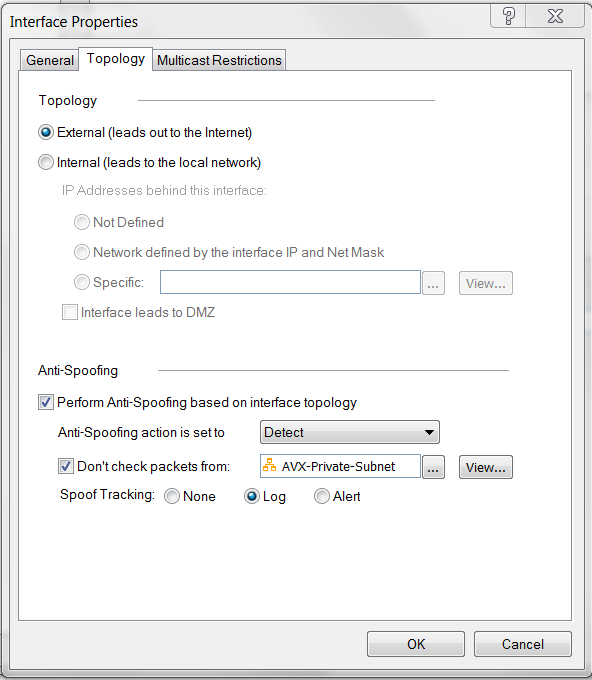
-
At Check Point Gateway - Topology window, double click "eth1" (Check Point LAN port). Select Internal (leads to the local network).
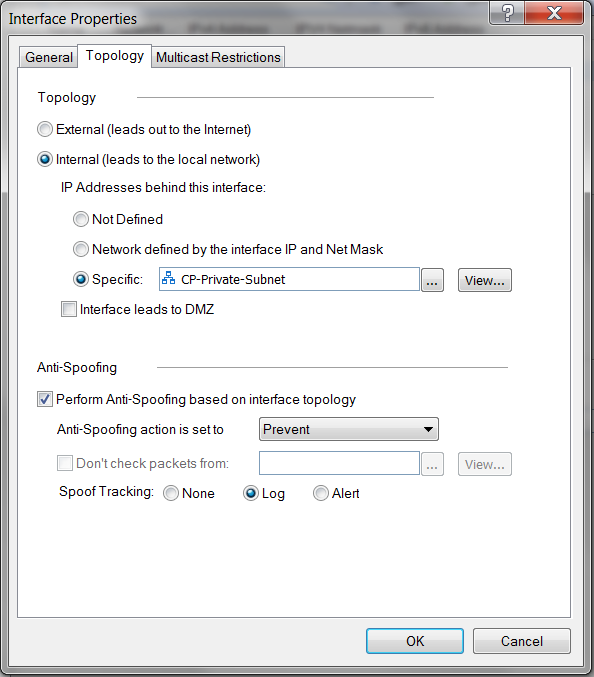
-
At the Check Point Gateway - IPsec VPN - Link Selection window, configure the parameters as follows:
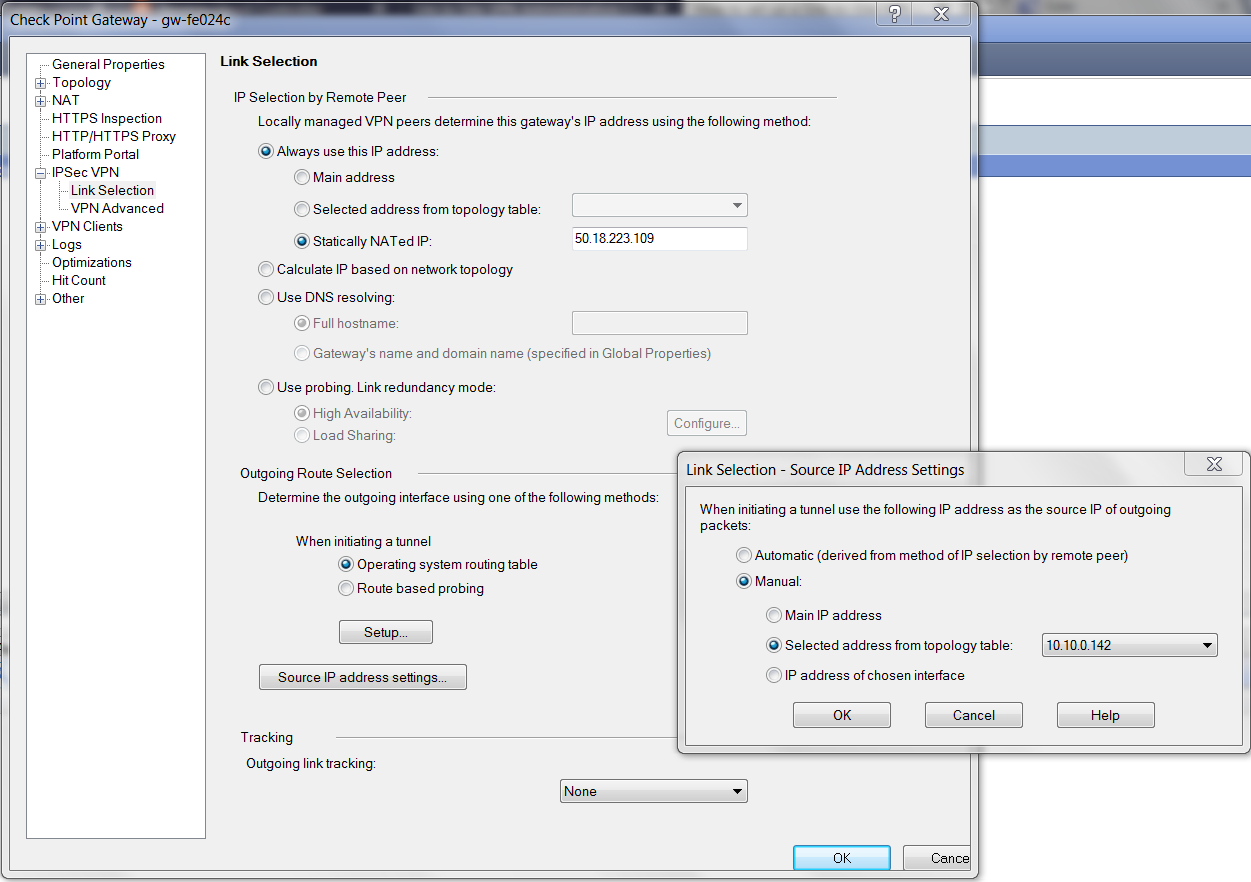
Field Value Statically NATed IP
Public IP of Check Point WAN port
Selected address from topology table
Private IP of Check Point WAN port
-
At the Check Point Gateway - IPsec VPN - VPN Advanced window, configure the parameters as follows:
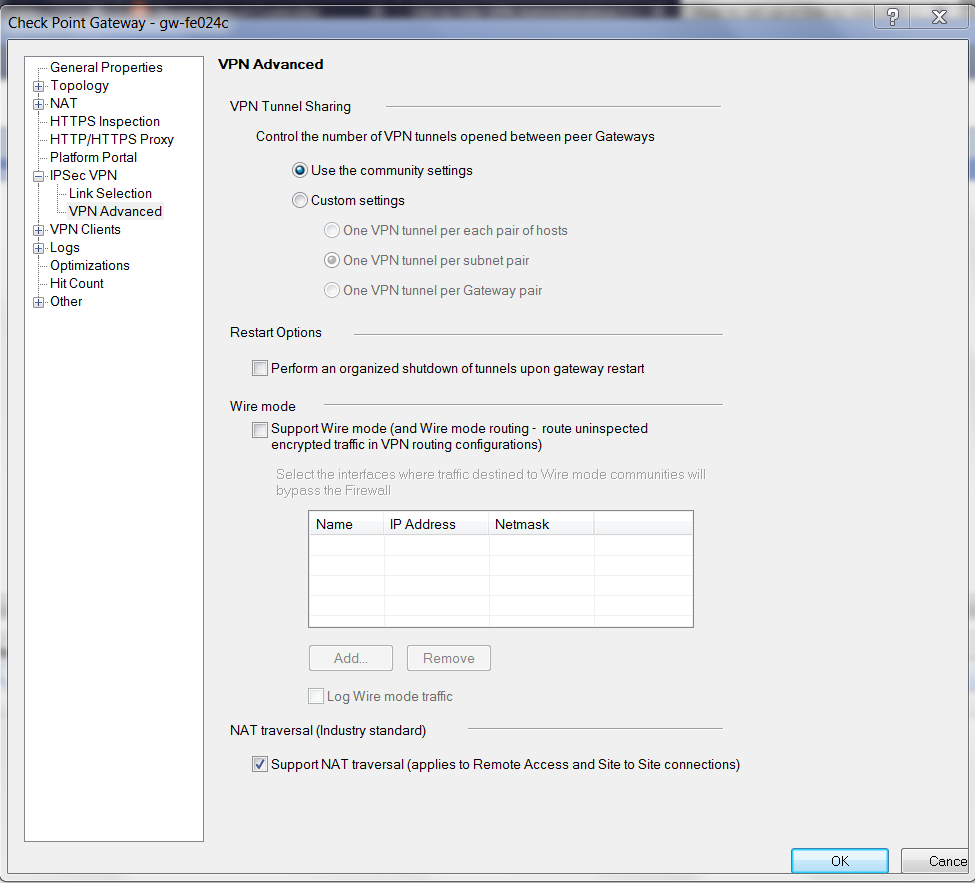
Configuring an Interoperable Device to Represent Aviatrix Gateway
-
At Check Point SmartDashboard window, select the Desktop tab. Right-click the Networks folder at the left navigation bar to create a new interoperable device.
-
At the Interoperable Device - General Properties window:
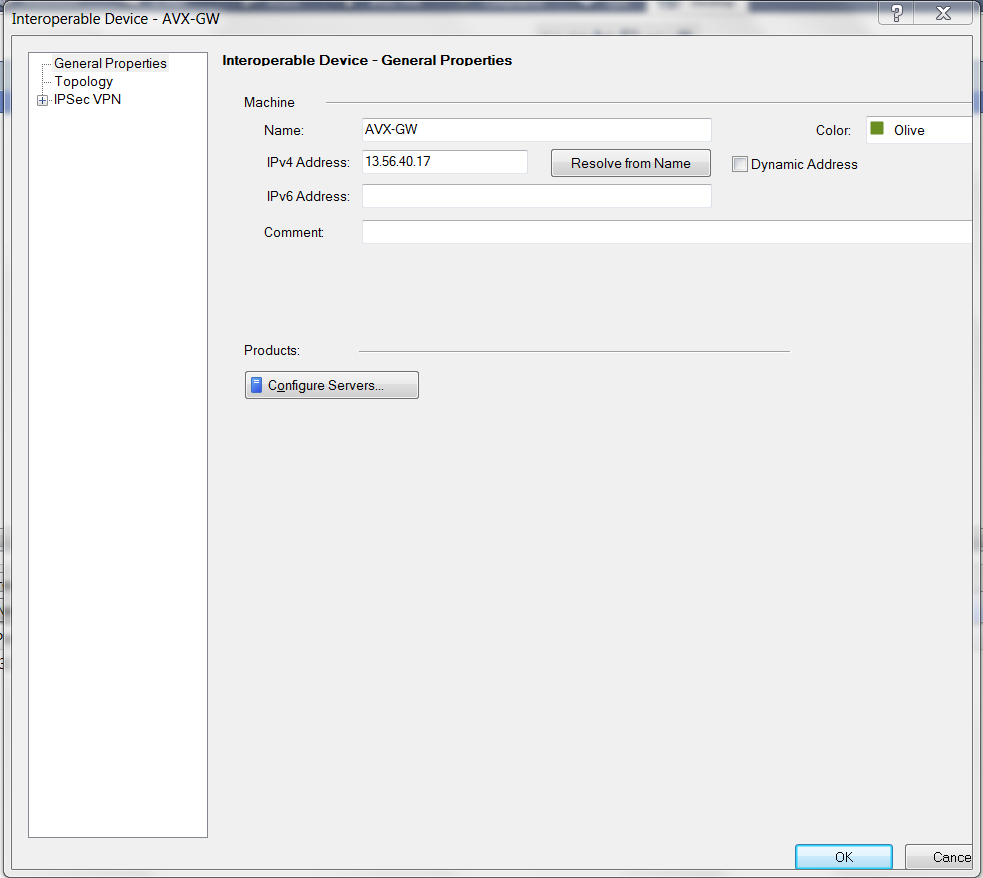
Field Value Name
Arbitrary (e.g. AVX-GW)
IPv4 Address
Public IP of Aviatrix Gateway
-
At the Interopable Device - Topology window, select Manually defined for VPN Domain. Select the network private subnet of VPC1 (Aviatrix Gateway VPC) you created above.
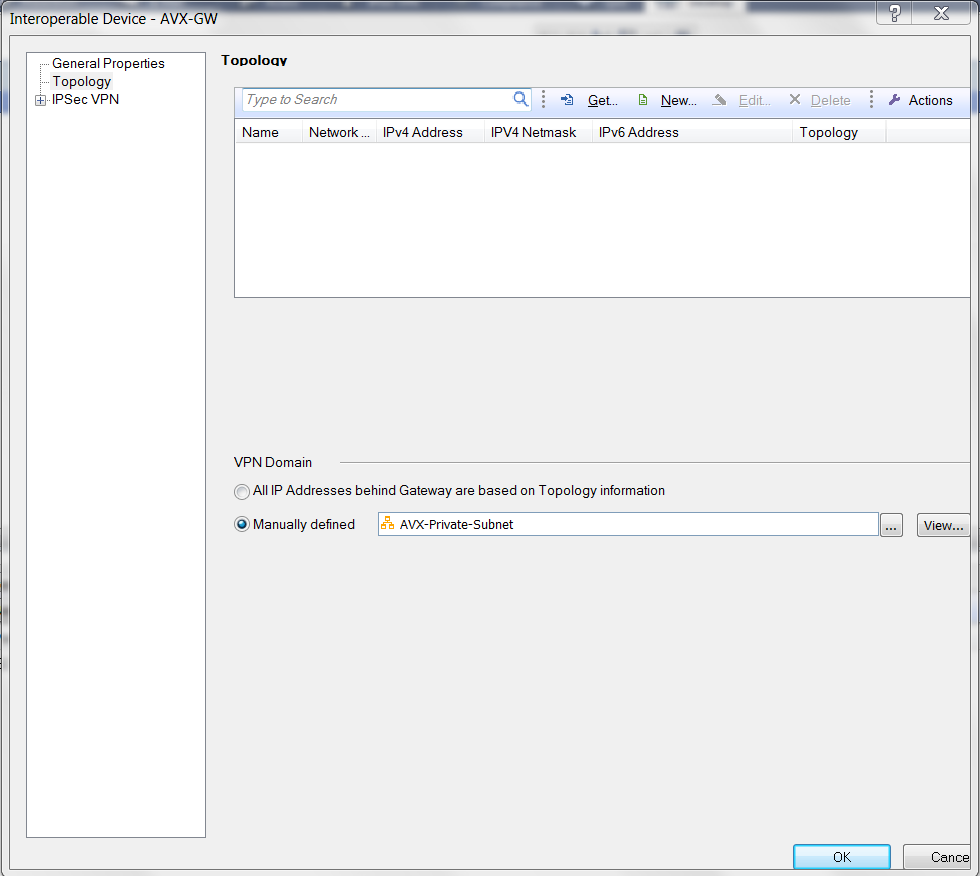
-
At the Interopable Device - IPsec VPN - Link Selection window, select Always use this IP address > Main Address.
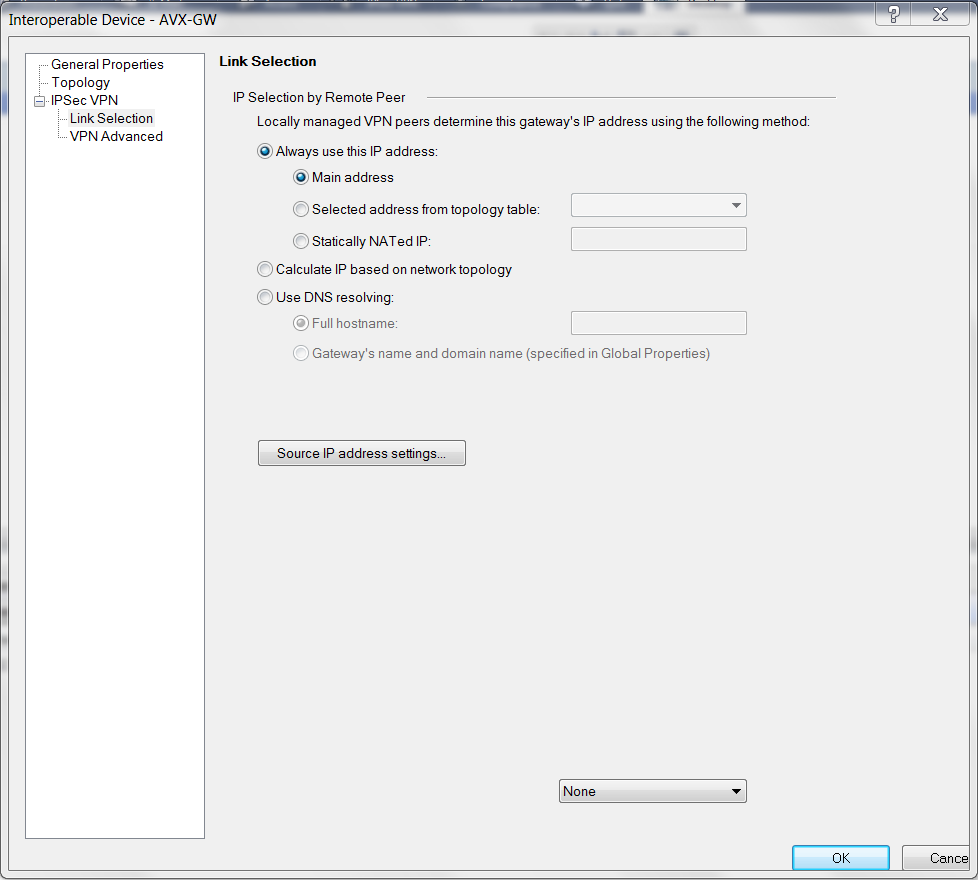
-
At the Interopable Device - IPsec VPN - VPN Advanced window, select Use the community settings.
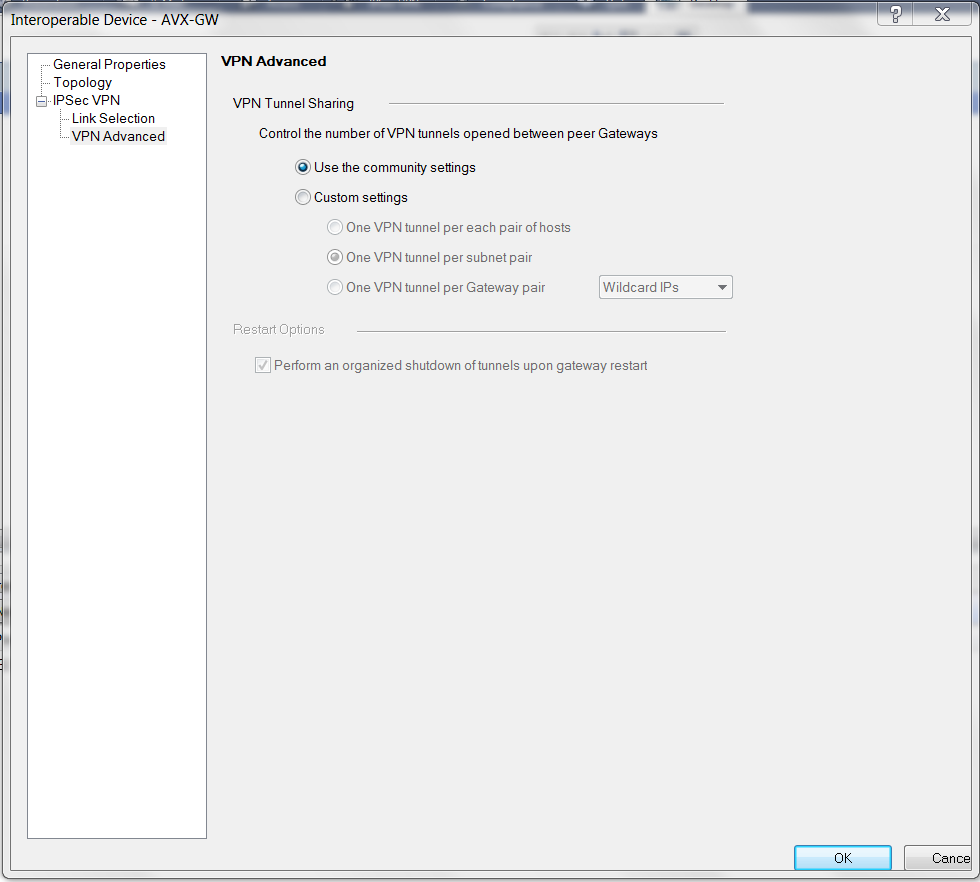
Creating a VPN Community
-
At SmartDashboard IPsec VPN tab, select Overview from left navigation bar. Click New to create a Meshed Community.
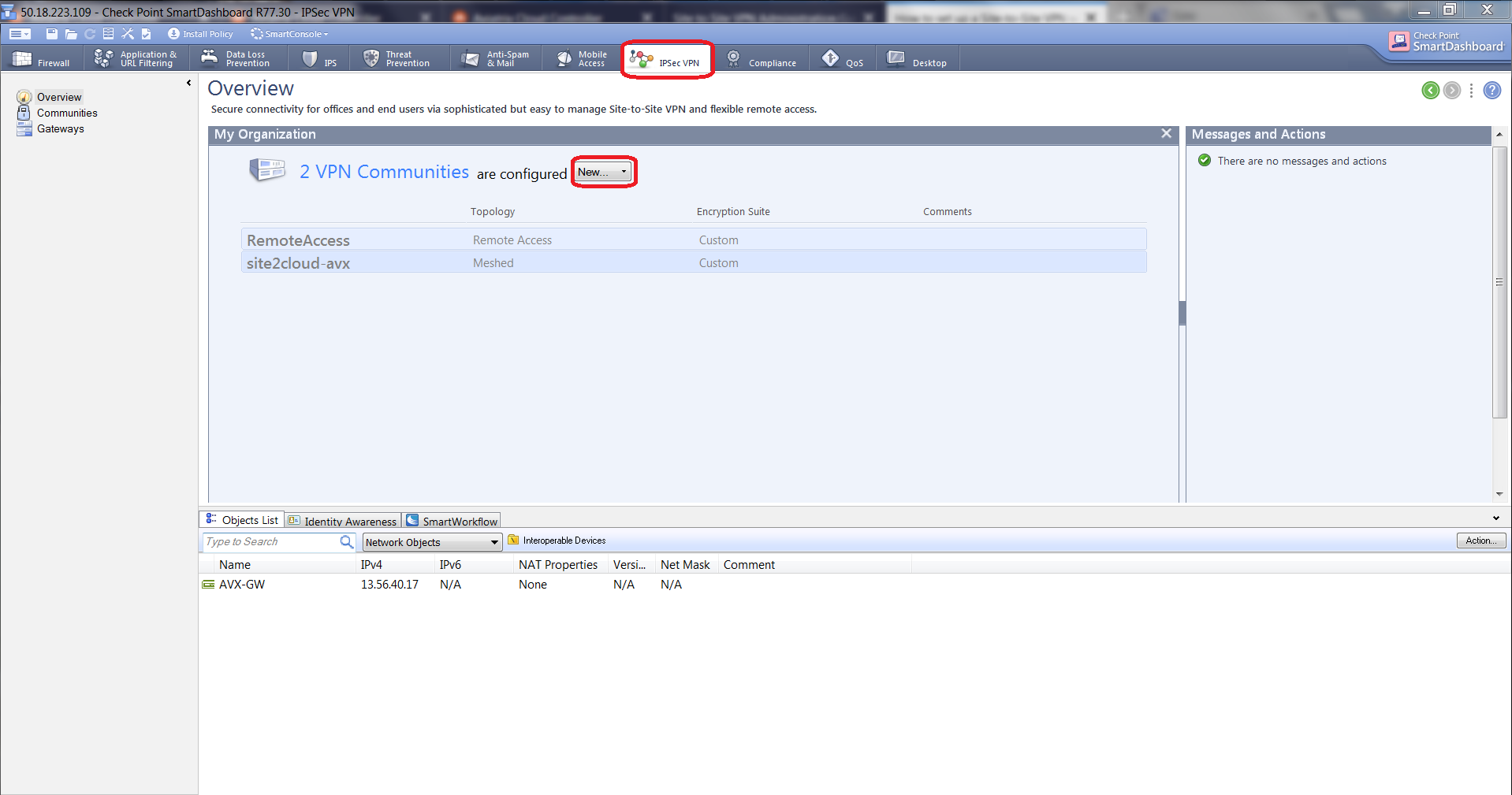
-
At Meshed Community Properties - General window, create one community with a name (e.g. Site2Cloud-avx).
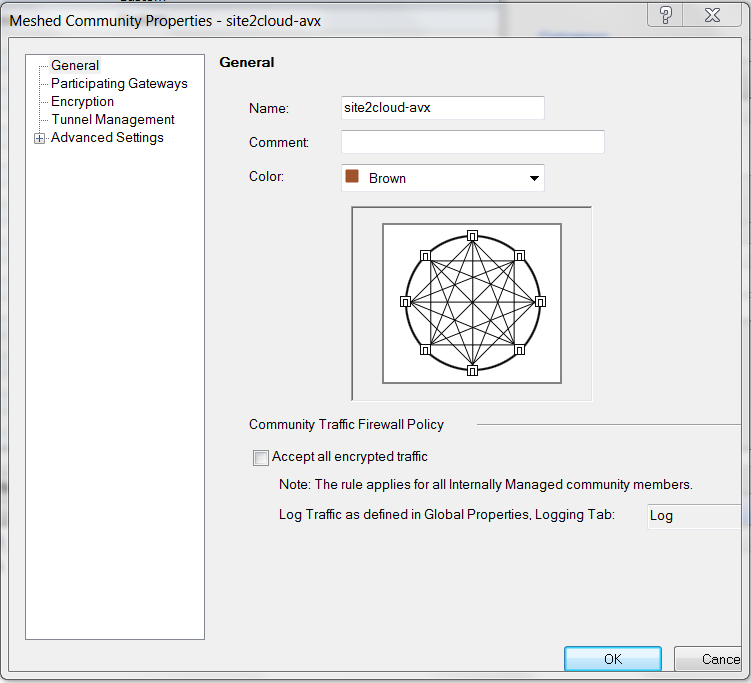
-
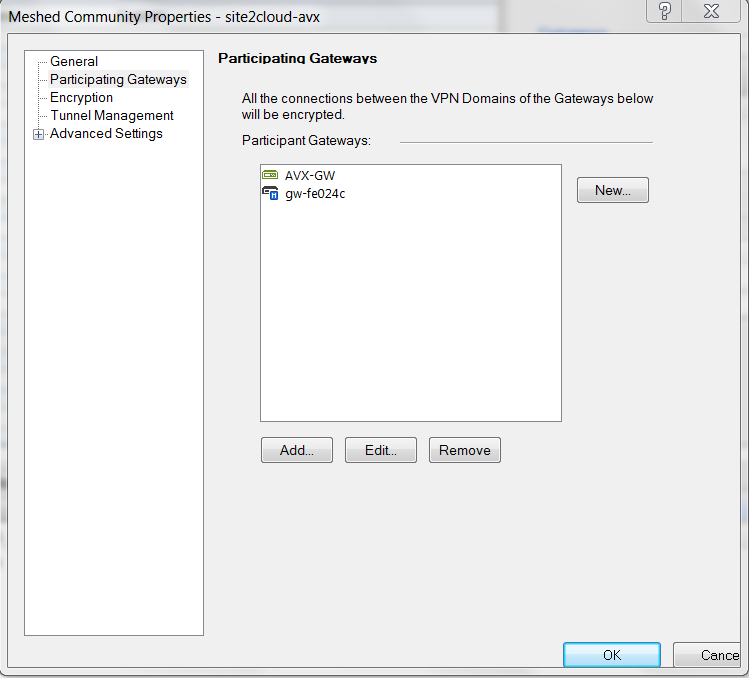
At Meshed Community Properties - Participating Gateways window, add both Check Point Security Gateway (e.g. gw-fe024c) and the interopable device created when you configured an interoperable device to represent the Aviatrix Gateway (e.g. AVX-GW) to this community.
-
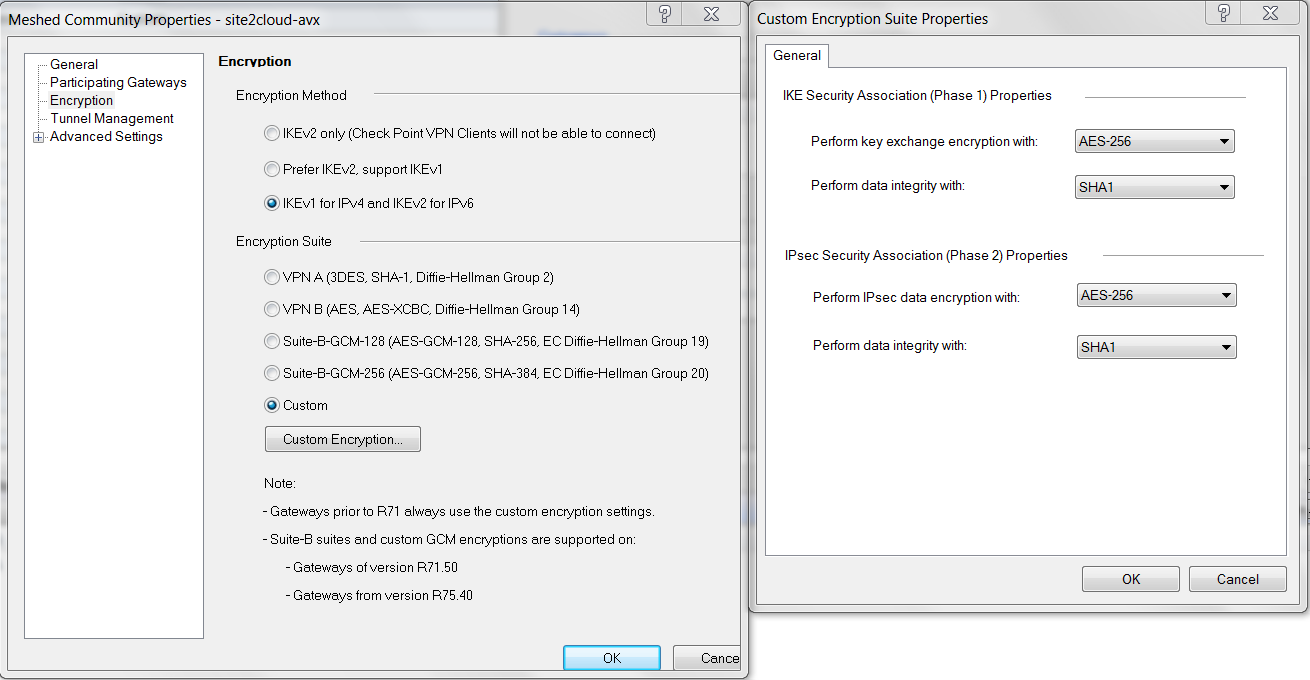
At Meshed Community Properties - Encryption window, select the options according to the Site2Cloud configuration for configuring CheckPoint-VM you saved and downloaded above.
-
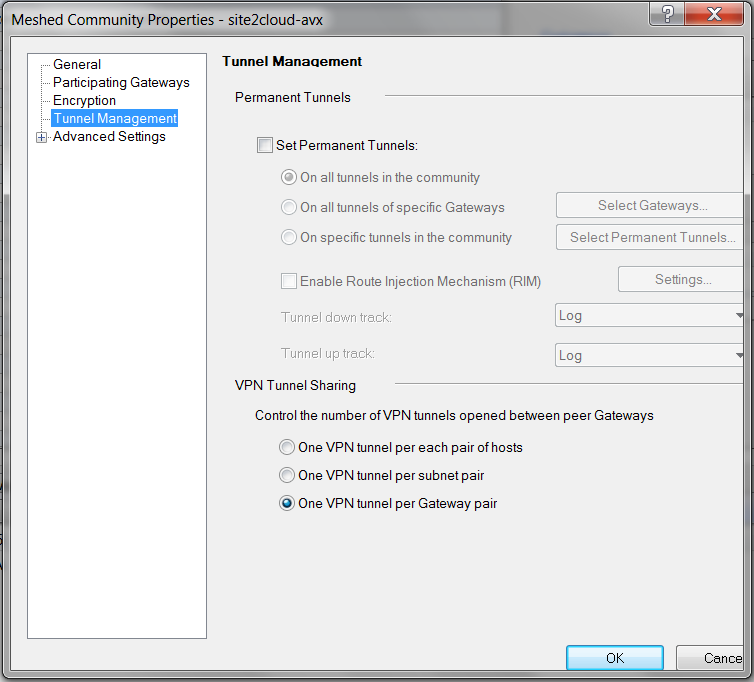
At Meshed Community Properties - Tunnel Management window, select One VPN tunnel per Gateway pair for VPN Tunnel Sharing.
-
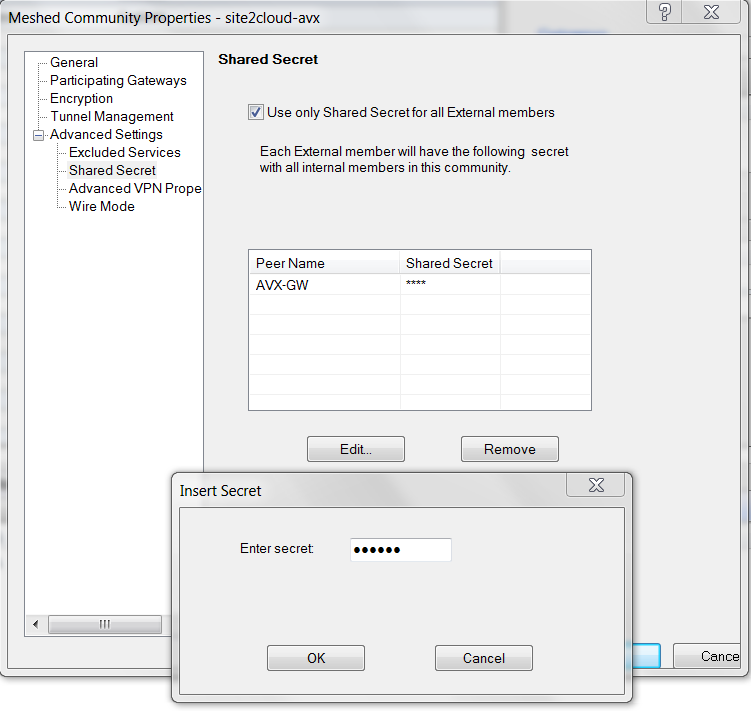
At the Meshed Community Properties - Advanced Settings - Shared Secret window, enter Shared Secret by copying the Pre-Shared Key from the Site2Cloud configuration downloaded above.
-
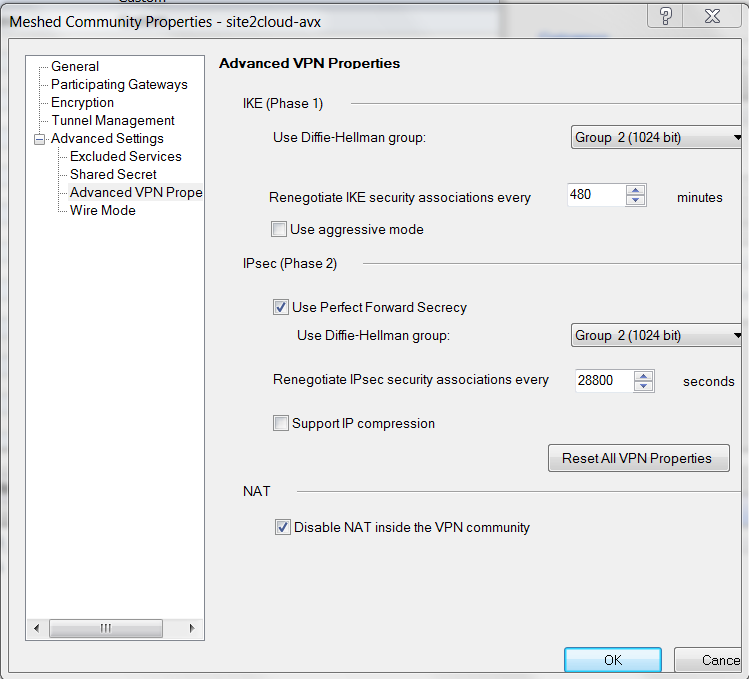
At the Meshed Community Properties - Advanced Settings - Advanced VPN Properties window, enter the Phase1 and Phase2 parameters according to the Site2Cloud configuration downloaded above.
Creating Firewall Rule for VPN Traffic
-
At SmartDashboard window, select the Firewall tab.
-
Select Policy to add a new rule.
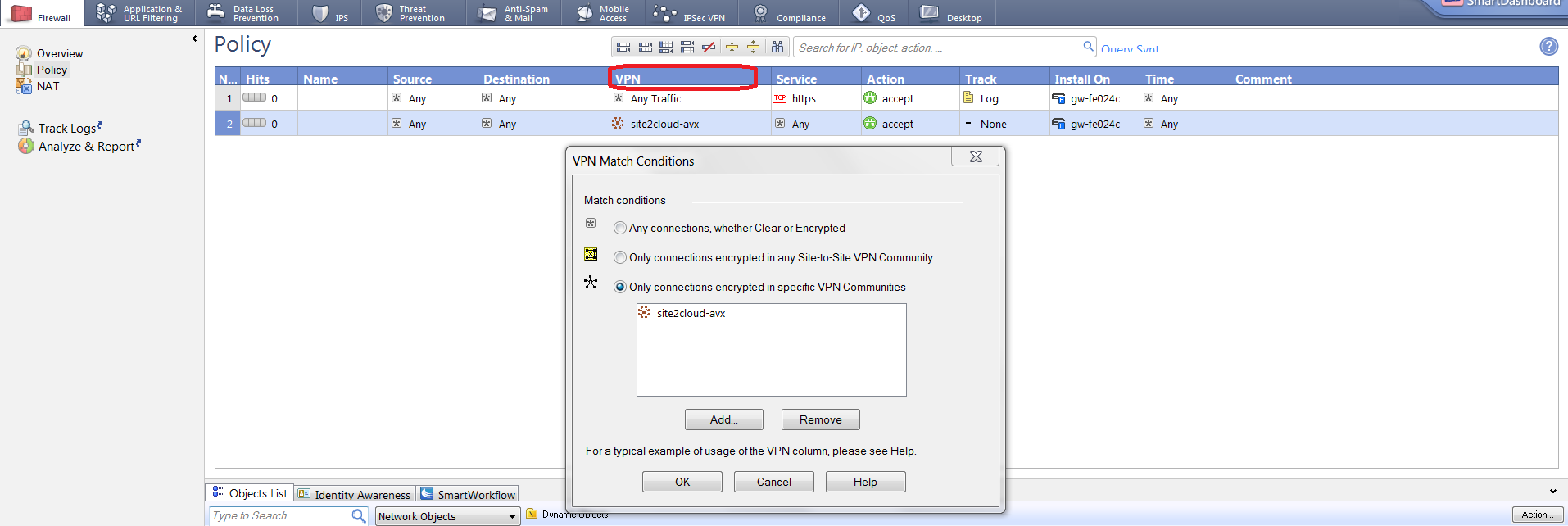
Field Value VPN
Select the Meshed VPN Community created above
Install On Sele
ct Check Point Security Gateway
-
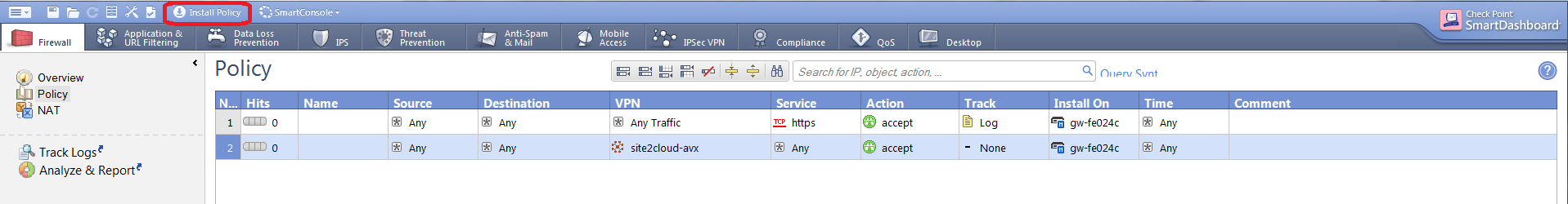
Click Install Policy button to push the firewall policy to the Check Point Security Gateway.
Troubleshooting and Verifying at Check Point Security Gateway
-
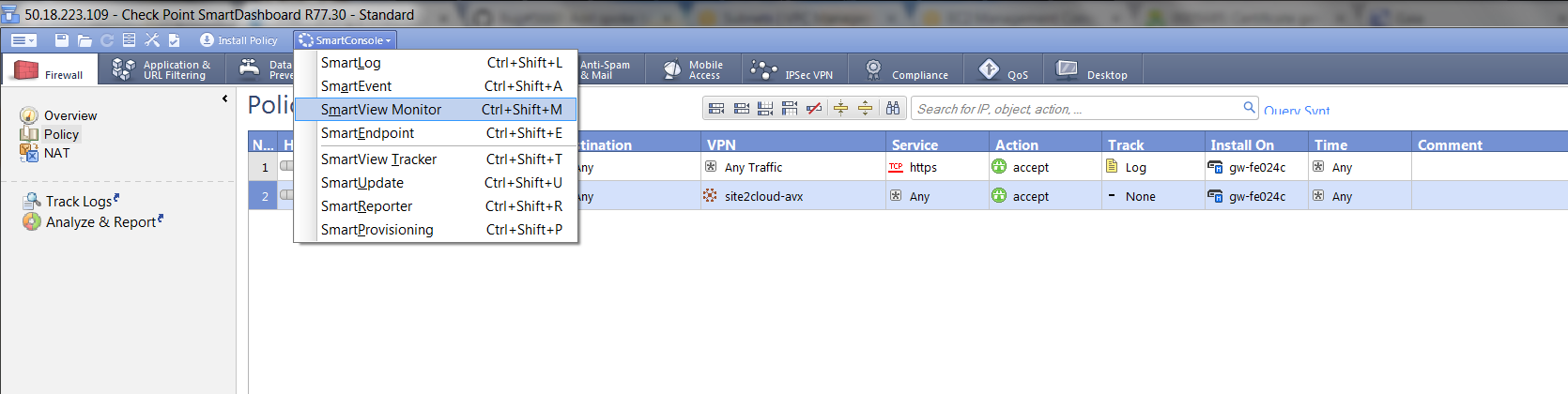
At SmartDashboard window, from SmartConsole dropdown list, select SmartView Monitor.
-
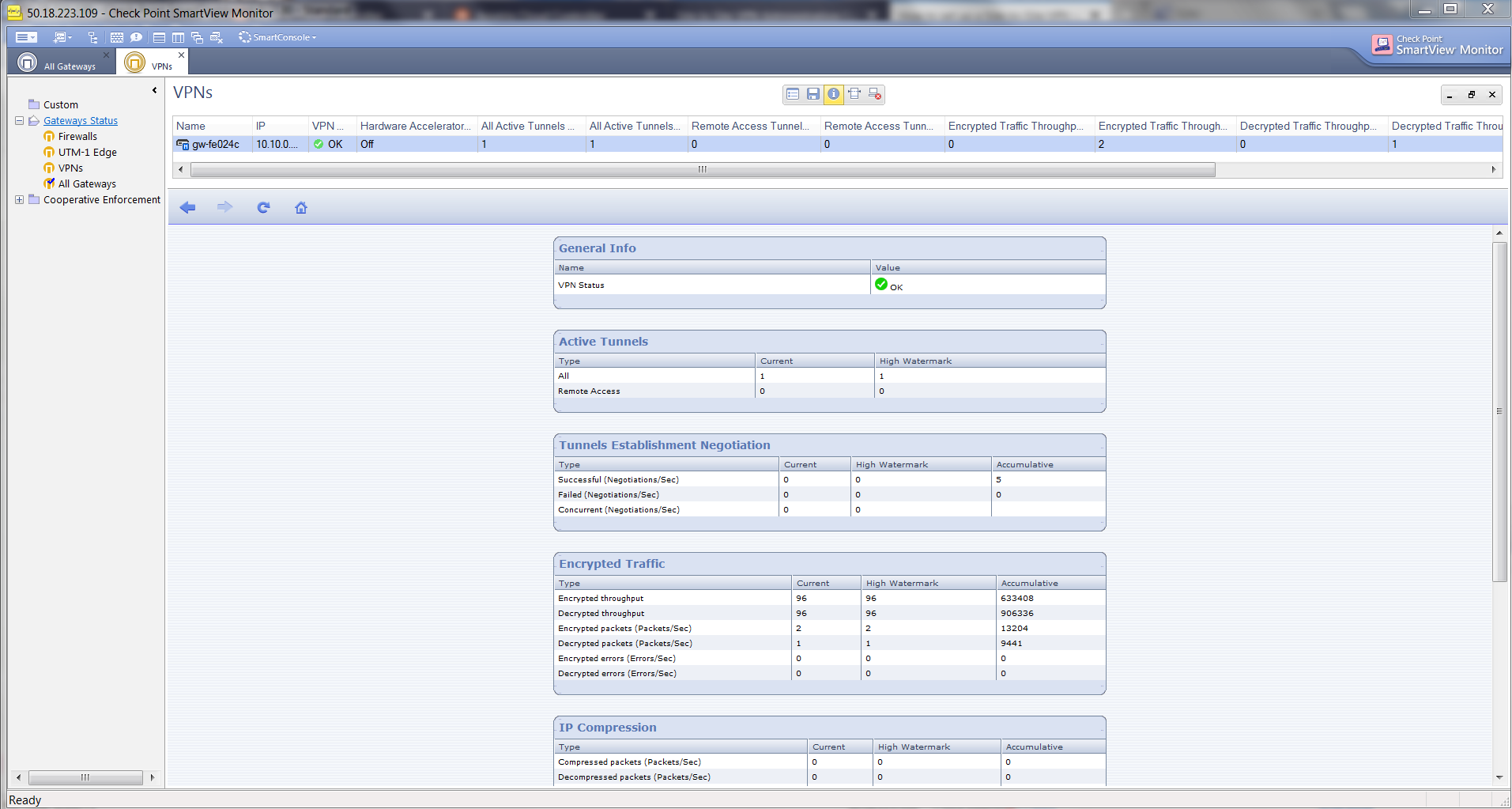
At the SmartView Monitor window, select VPNs from Gateway Status and verify Encrypted Traffic.
Troubleshooting and Verifying at Aviatrix Controller
-
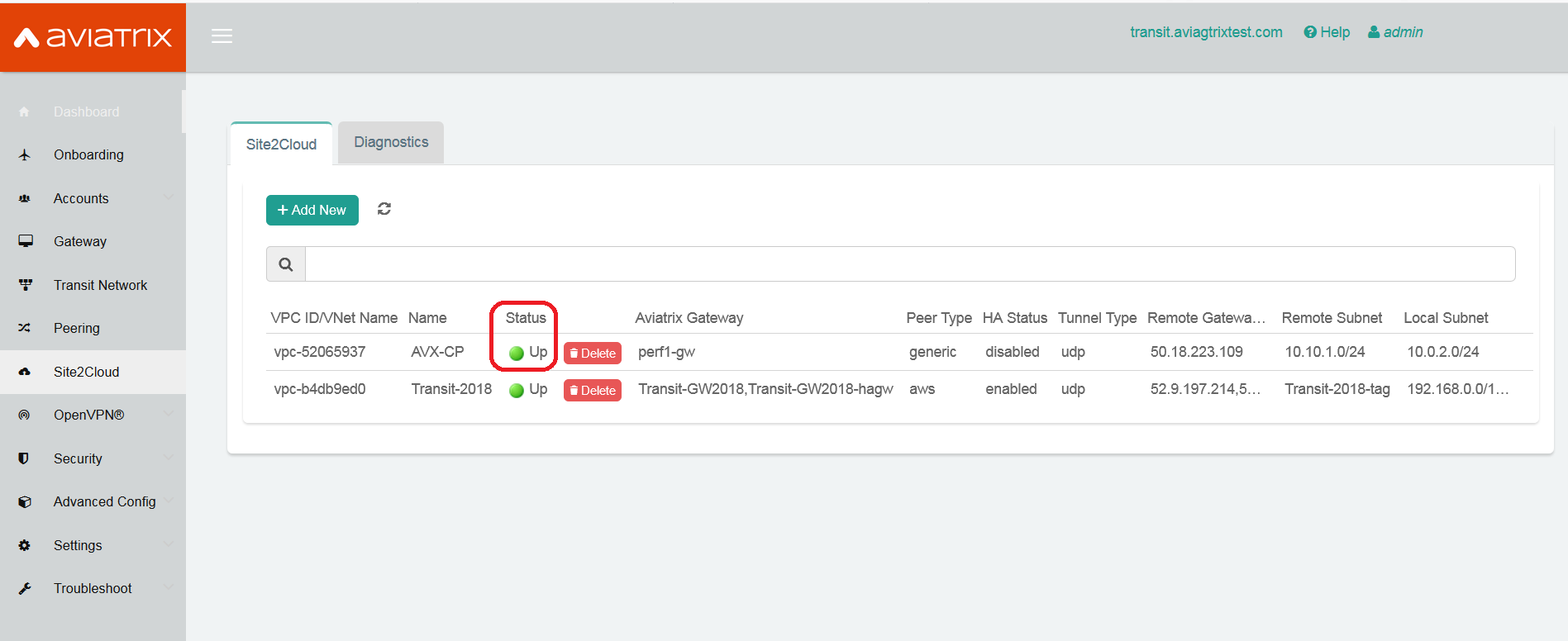
At the Aviatrix Controller, go to the Site2Cloud page. Verify that the status of the Site2Cloud connection is up.
-
At the Site2Cloud - Diagnostics page, run various diagnostics commands.
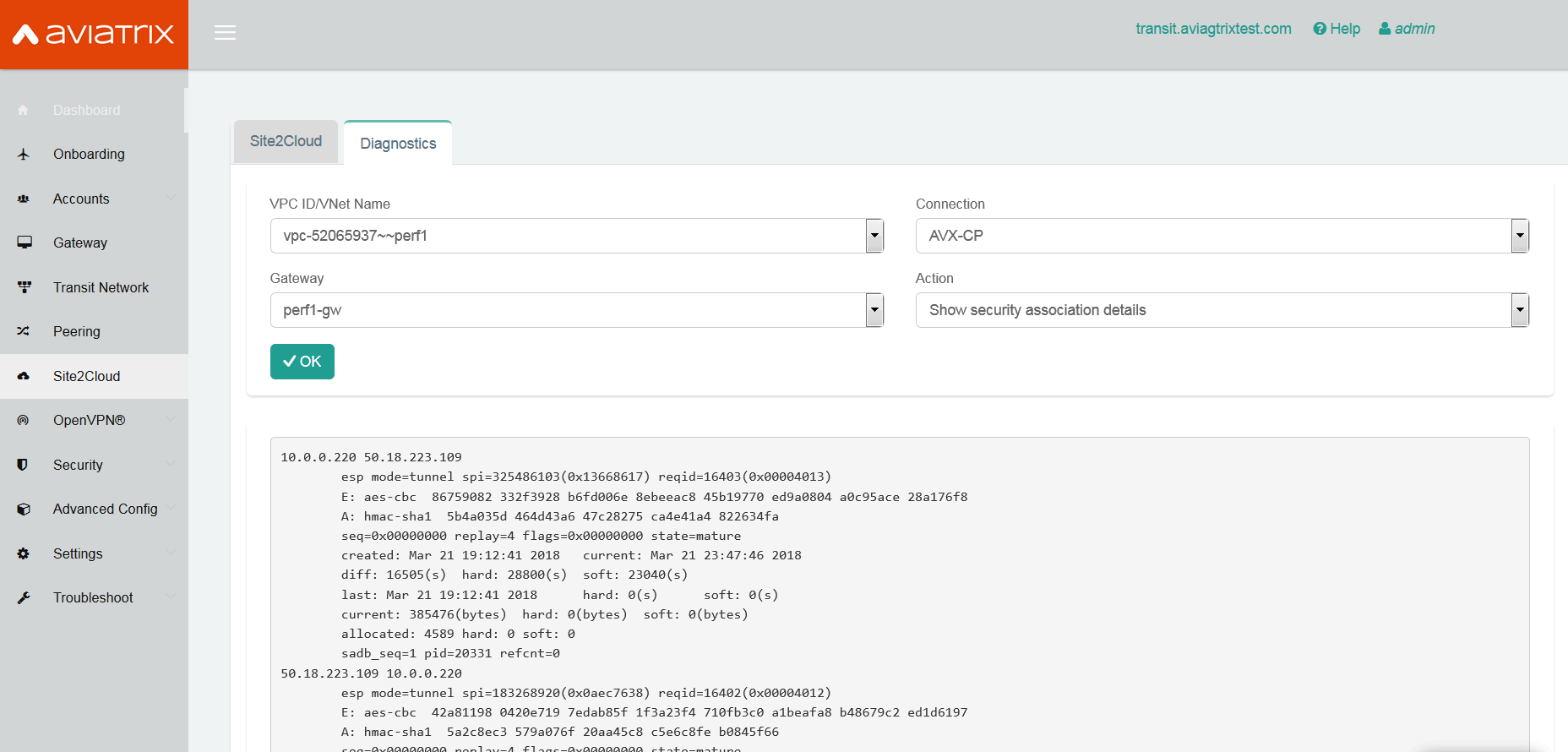
Field Value VPC ID/VNet Name
VPC1 (Aviatrix Gateway VPC) ID
Connection
Name of Site2Cloud connection created above
Gateway
Name of Aviatrix Gateway
Action
One of the supported diagnostics commands
For support, please open a support ticket at Aviatrix Support Portal.