Aviatrix Transit Network Segmentation Workflow
Aviatrix Multicloud Transit Segmentation provides network isolation and enhanced security through network domains and connection policies to Aviatrix Transit network where both Spoke and Transit networks deploy Aviatrix Gateways across multi-region and multi-cloud. You can have up to 200 network domains on each Aviatrix Transit gateway.
| Aviatrix does not currently support duplicated CIDRs that cross domains or Transit networks. Overlapping CIDRs advertised from on-prem to different Spoke network domains connected to one Aviatrix Transit gateway is not supported. |
A network domain is an Aviatrix-enforced network of VPC/VNet members, where VPCs/VNets in the network domain can communicate with each other. VPCs/VNets not in the network domain cannot communicate with each other. One or more Spoke VPCs/VNets can be members of a network domain and communicate with each other via an Aviatrix Transit gateway. The Aviatrix Controller dynamically programs and updates both VPC/VNet route tables so that instances in different Spoke VPC/VNets can communicate.
| The network domain concept also applies to a hybrid connection between an Aviatrix Transit gateway and on-prem or remote sites. Each BGP peer or connection can be associated with one network domain. |
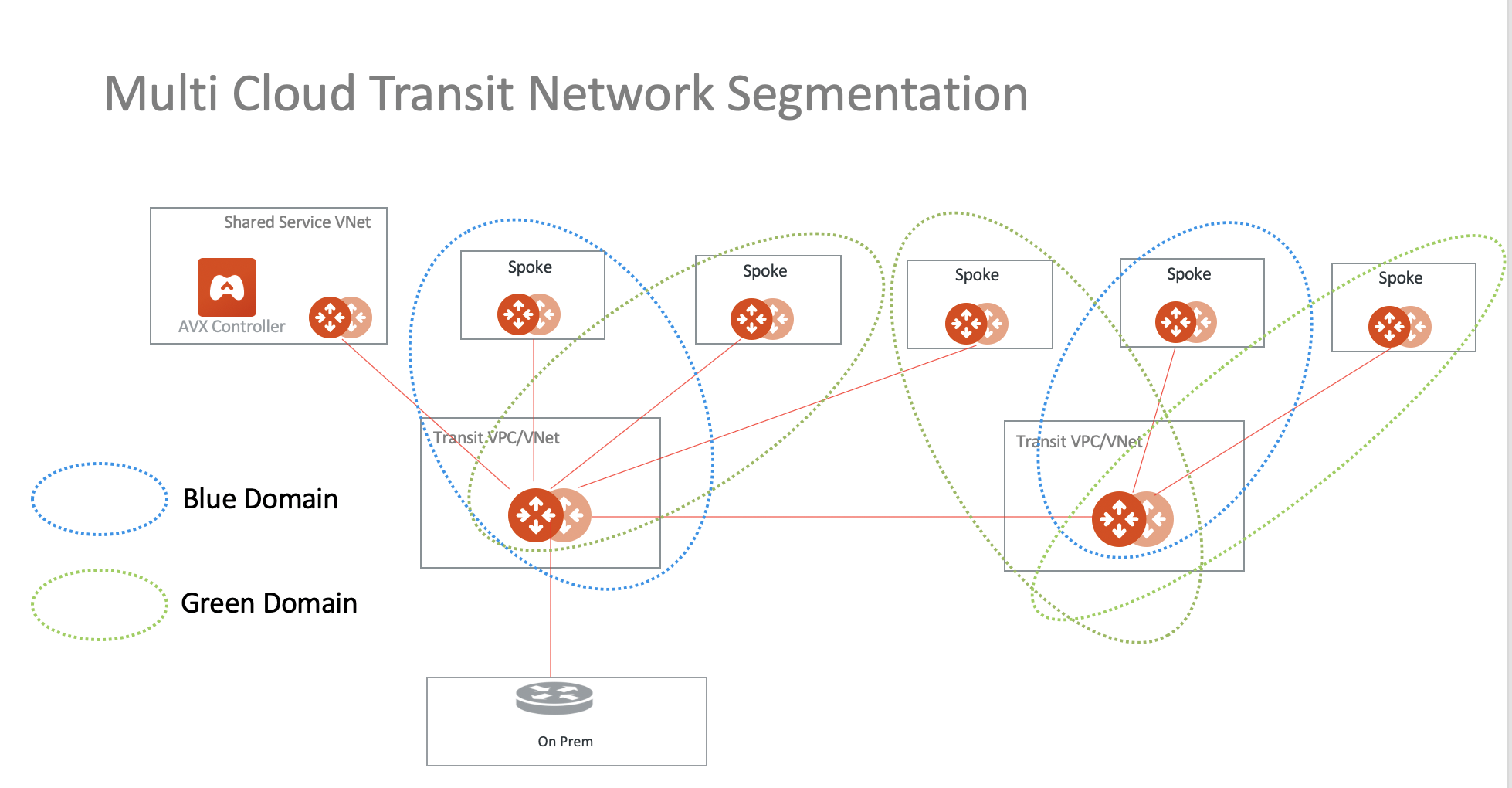
In the above diagram, Spokes associated with the Blue Domain can communicate with each other, and Spokes associated with the Green Domain can communicate with each other. However, there is no cross-communication between the Blue and Green Domains unless there is a connection policy. These connection policies are implemented with Aviatrix Transit where both Spokes and the Transit VPC/VNet deploy Aviatrix gateways.
| This segmentation works with Azure native Spoke VNets. |
Enabling the Aviatrix Transit Gateway
-
Enable the Aviatrix Transit Gateway for segmentation by navigating to Multi-Cloud Transit > Segmentation > Plan.
-
Under 1) Enable Aviatrix Transit Gateway for segmentation, select the Aviatrix Transit Gateway Name from the list. This is an Aviatrix Transit gateway deployed using the Multi-Cloud Transit Network workflow.
-
Click Enable.
-
Create a Multicloud network domain by entering a unique name in the Network Domain Name field (such as Dev_Domain) and clicking Create.
Creating Connection Policies
You now add/modify connection policies. Using network domains and connection policies allows you to identify groups of Spokes and Edges that have the same requirements from a networking point of view, and then apply connection policies at the group level.
This step specifies the connection relationship of one domain to others. Two connected domains imply that Spokes in each domain can communicate with each other despite the fact that they are in different domains.
Highlight a domain in the left panel and click Add. The domain displays in the right-hand panel.
Associating a Spoke /TGW Domain/ Edge Gateway to the Network Domain
-
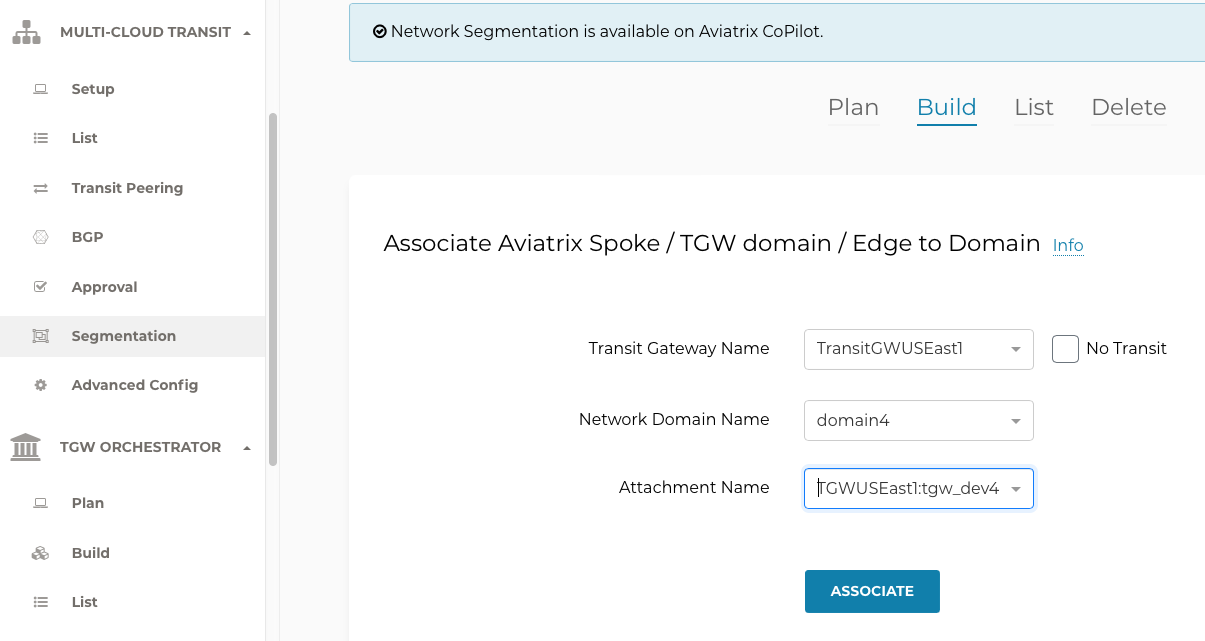
On the Multi-Cloud Transit > Segmentation > Build page, you associate a Spoke or Edge gateway, or a TGW domain, to the network domain.
-
Transit Gateway Name: the name of the Aviatrix Transit gateway
-
Network Domain Name: the name of the network domain
-
Attachment Name: the name of a Spoke or Edge connection, or a TGW domain, to associate to the network domain
-
-
Click Associate.
| Click here for information on AWS TGW interoperability. |
If you associated a TGW domain to the network domain, now any resources (regardless of whether they are AWS TGW or Aviatrix Transit) that share the network domain can communicate with each other. The following is now also possible:
-
AWS TGW native Edge connections can route to Spokes attached to an Aviatrix Transit network.
-
Can peer an AVX Transit to an AWS TGW that is connected to on-prem. The network domains in both of these domains will work across Transit gateway peering and vice versa (but not AWS TGW peering).
-
Any two Aviatrix network domains that are connected are able to route to TGW Shared Services (for example, if Transit domain 1 is connected to Transit domain 2, and TGW domain A is associated with Transit domain 1, then TGW domain A can communicate with Spoke gateways in Transit domain 2).
-
TGW domains associated with any two connected Aviatrix network domains can communicate with each other (as long as they are not in the same TGW).
|
VPCs in the same AWS TGW but in different domains cannot communicate with each other unless you configure a connection policy. For a VPC attached to the TGW domains that are connected to an Edge domain, its VPC CIDR is propagated to the main route table of the Transit gateway and its connected Transit/Spoke gateways. |
Disassociate Aviatrix Spoke/Edge or TGW from Domain
If desired you can disassociate an Aviatrix Spoke/Edge or TGW domain from the network domain.
-
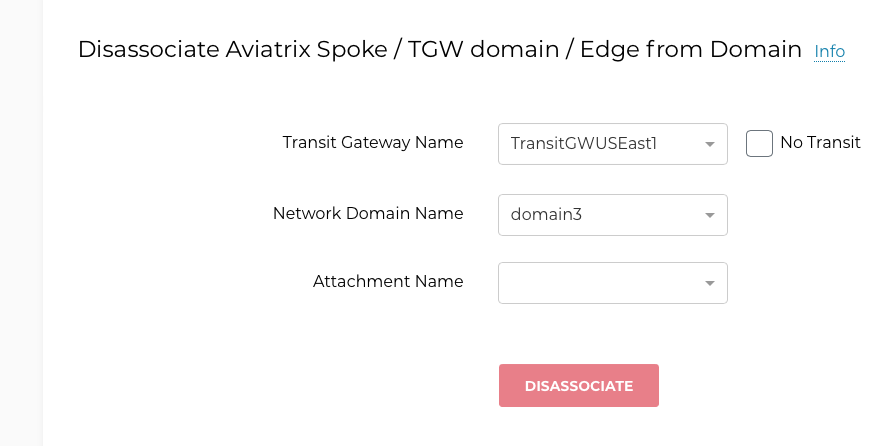
On the Multi-Cloud Transit > Segmentation > Build page, you can disassociate a Spoke or Edge gateway, or a TGW domain, from the network domain.
-
Transit Gateway Name: the name of the Aviatrix Transit gateway
-
Network Domain Name: the name of the network domain
-
Attachment Name: the name of a Spoke or Edge connection, or a TGW domain, to disassociate from the network domain
-
-
Click Disassociate.
Deleting and Disabling Functions
You can delete the Multicloud Security domain.
| Setting | Value |
|---|---|
Security Domain Name |
The name of the Security Domain |
You can disable the Aviatrix Transit Gateway for segmentation.
| Setting | Value |
|---|---|
Aviatrix Transit Gateway Name |
An Aviatrix Transit Gateway deployed in the Multicloud Transit Network workflow |