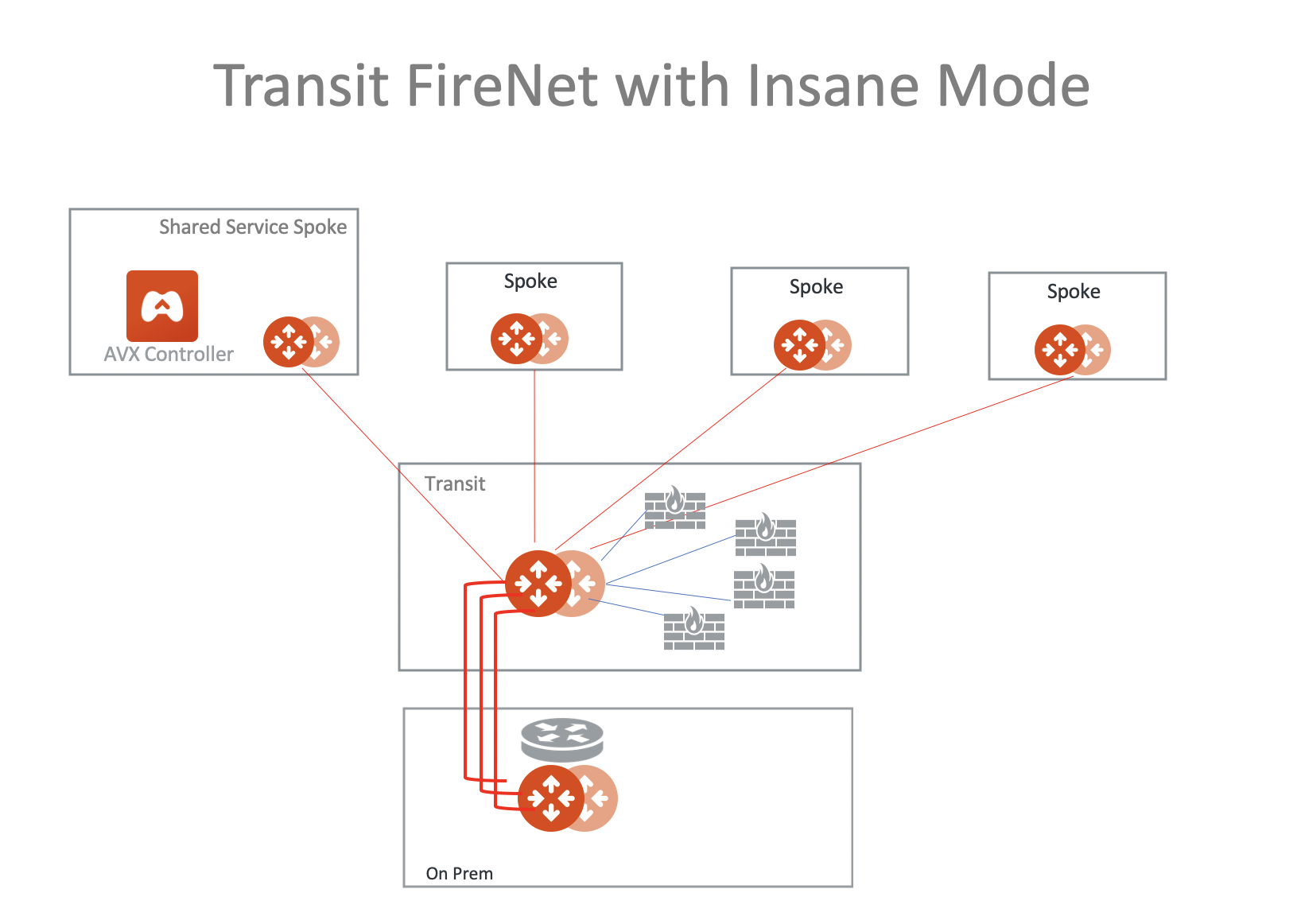
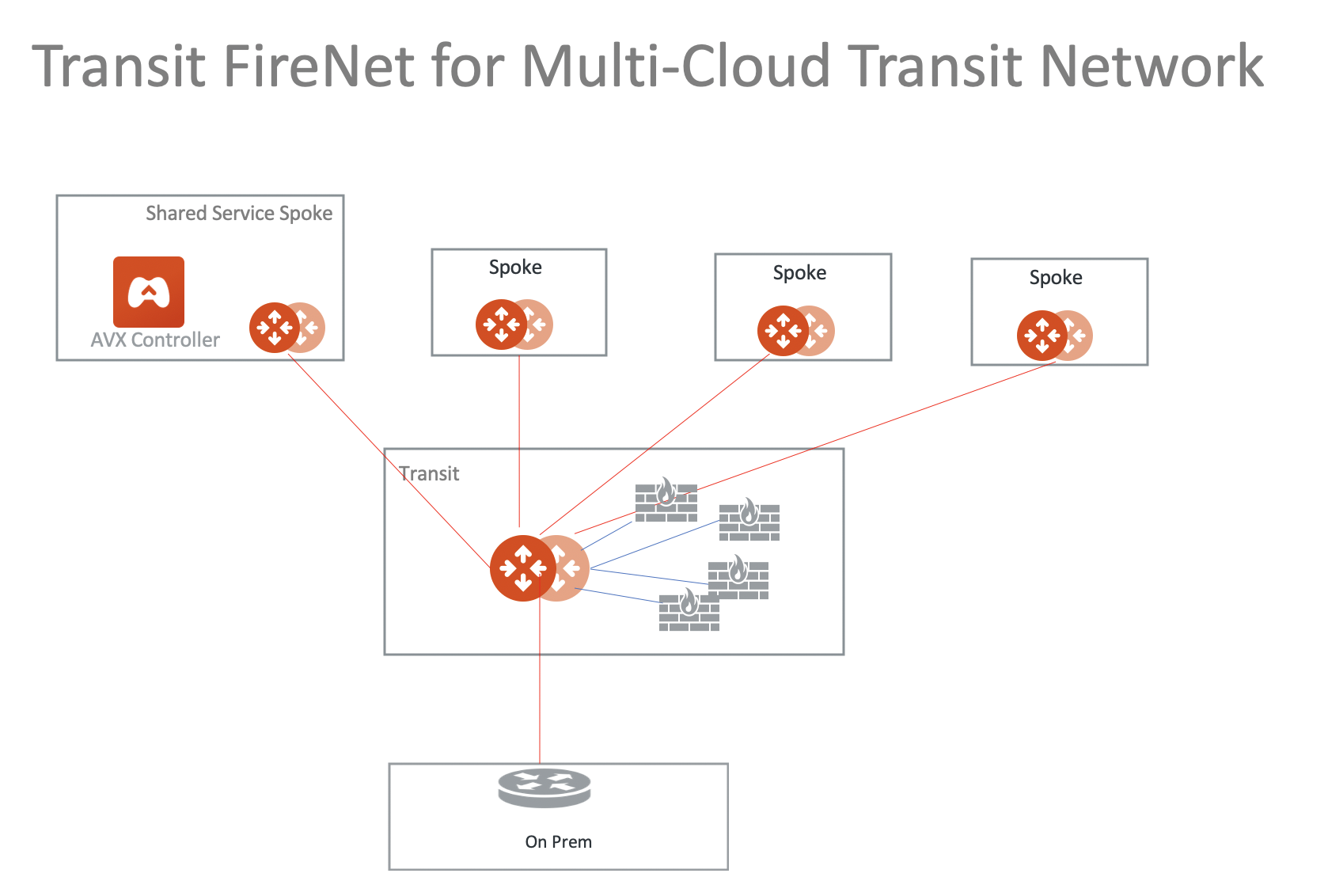
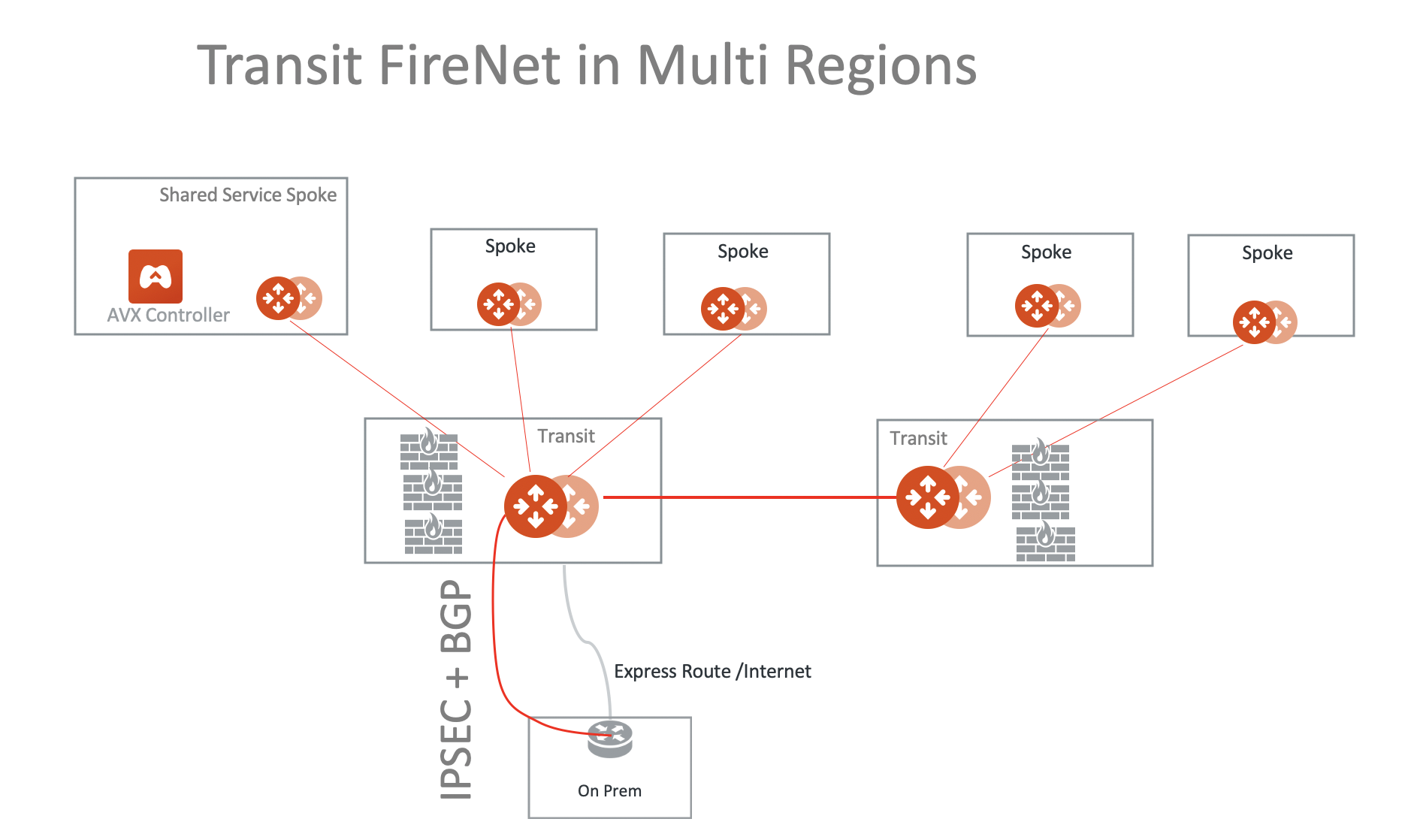
Transit FireNet Design Patterns
This document describes common design patterns when Aviatrix Transit Firewall Network (Transit FireNet) is deployed.
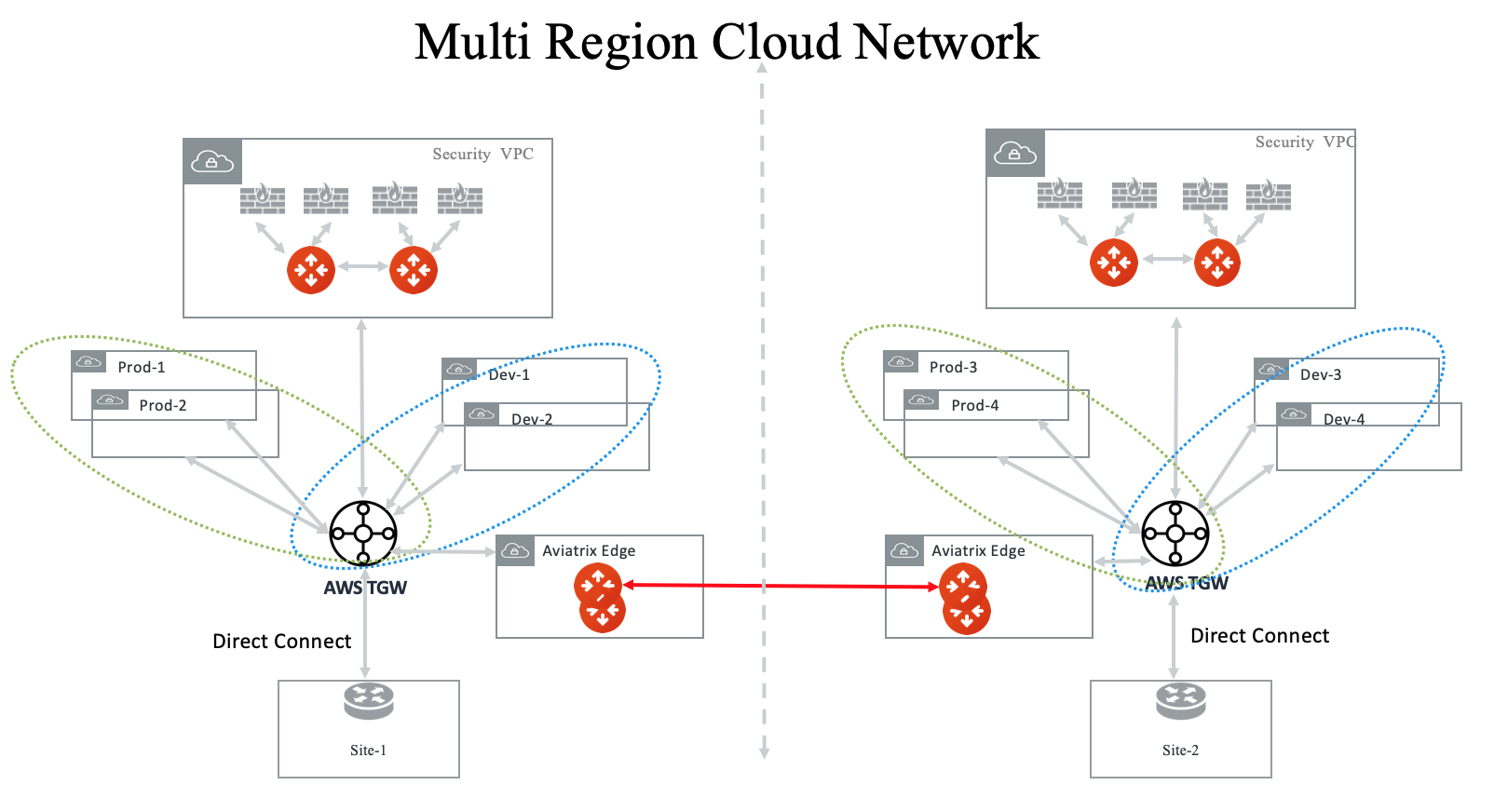
Multi Region Transit with Native TGW integration
Connect to on-prem with AWS Direct Connect Gateway (DXGW) and use the Aviatrix Edge gateway to connect to multiple regions.
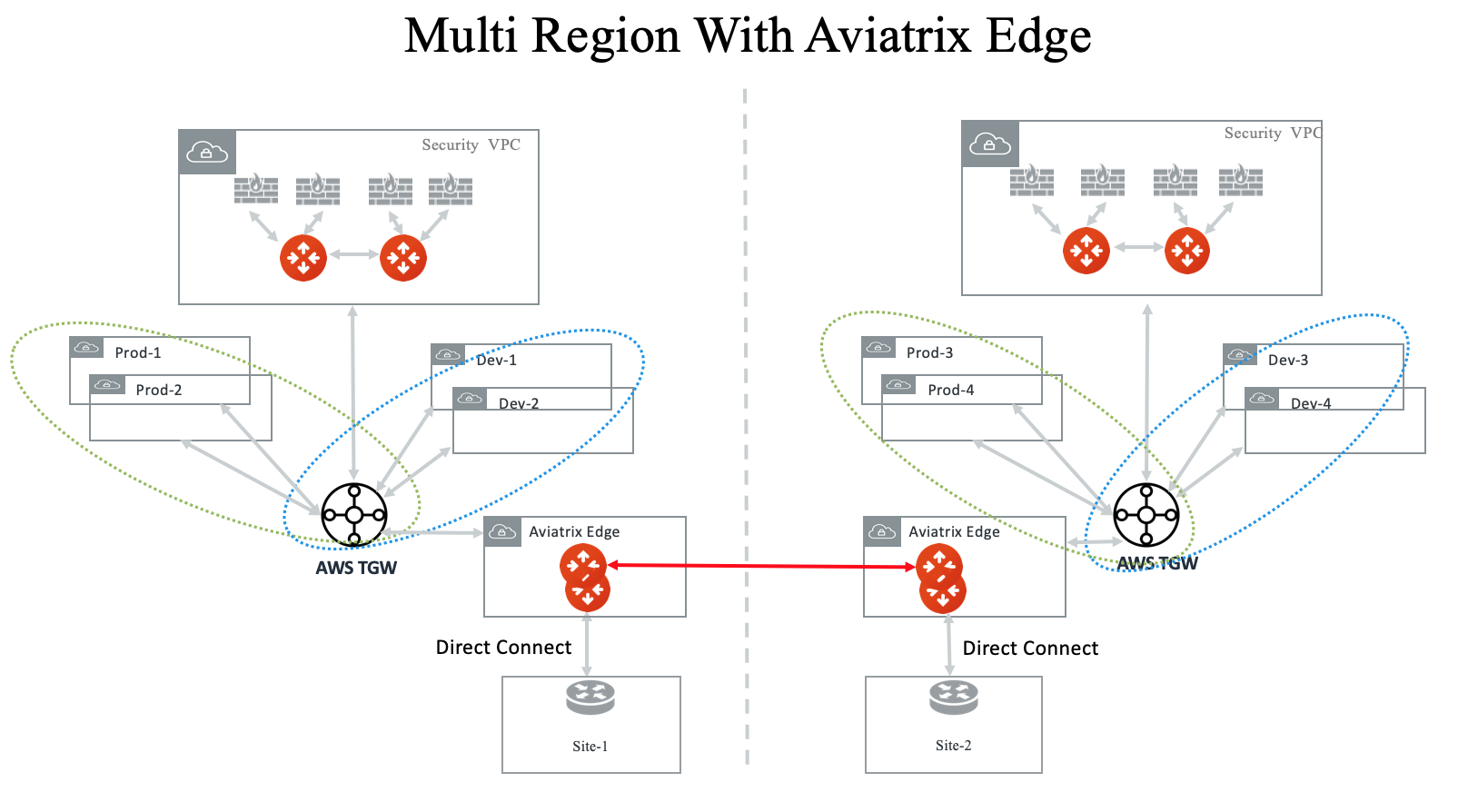
Multi-Region Transit with Aviatrix Edge
Connect to on-prem with an Aviatrix Edge gateway for both hybrid and multi-regions.
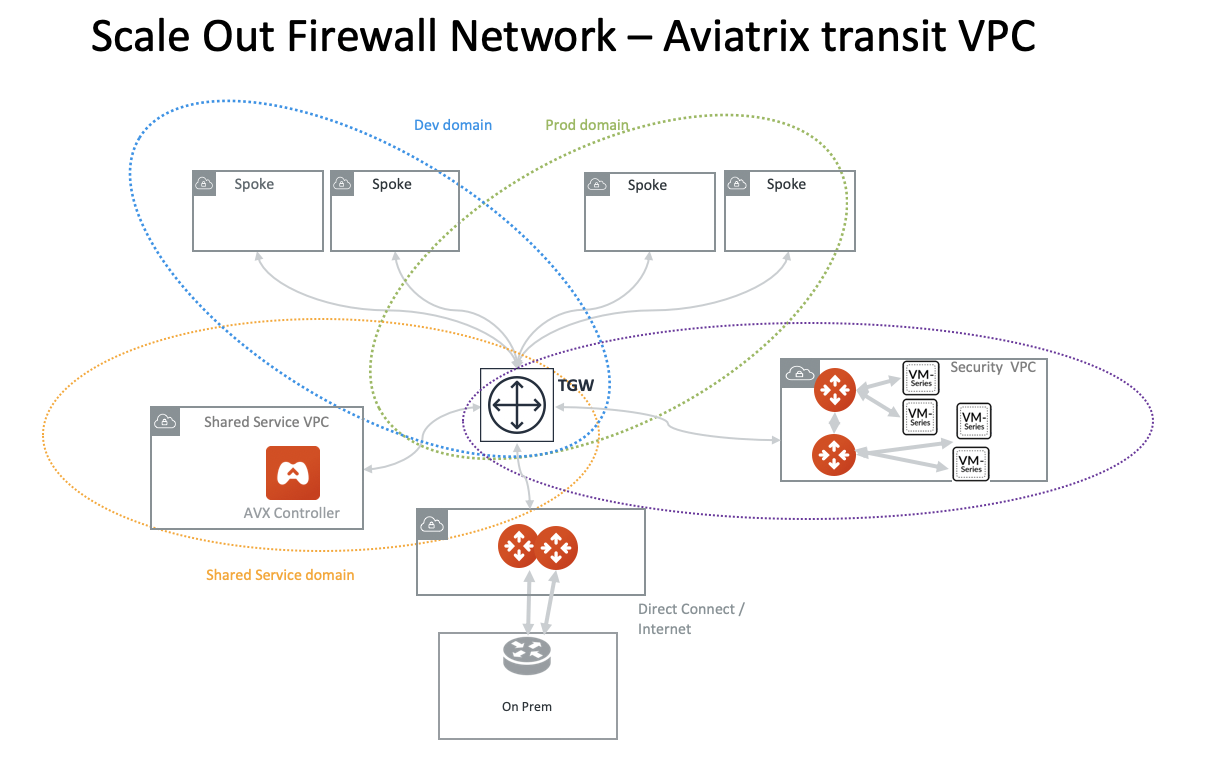
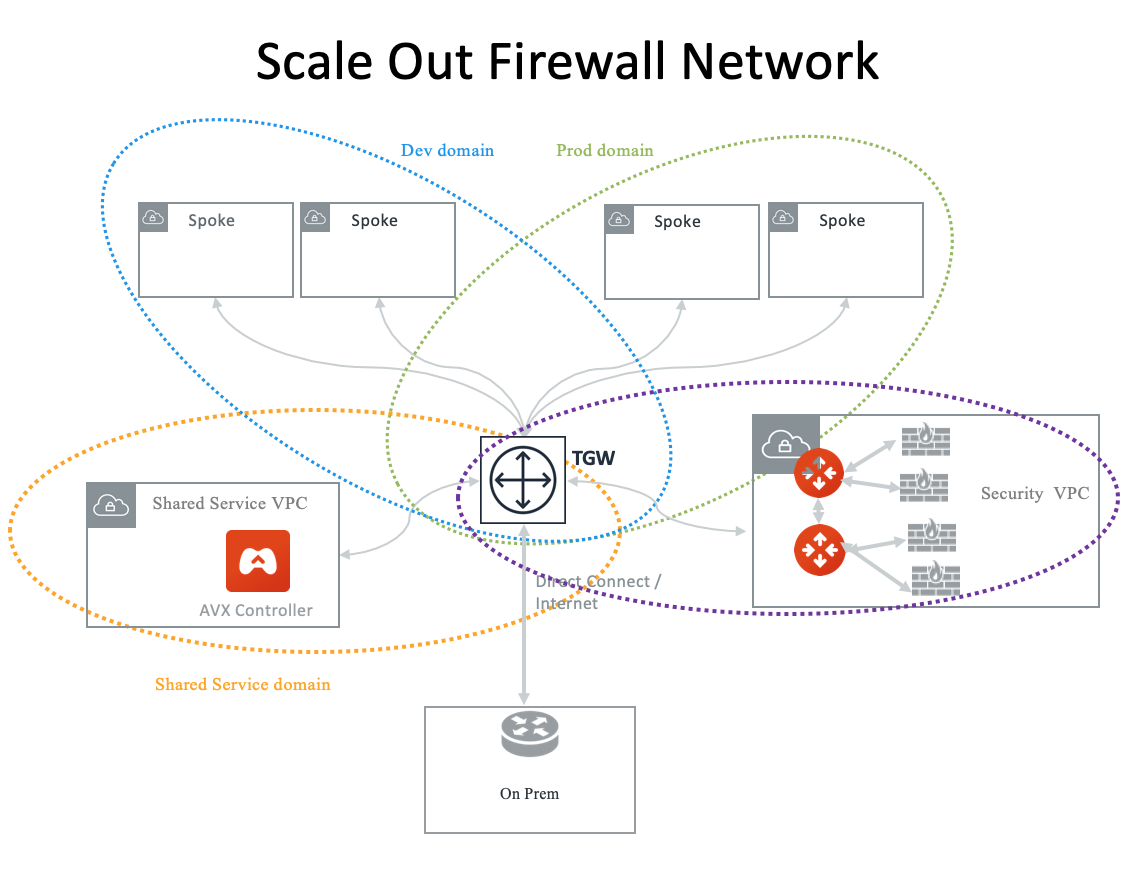
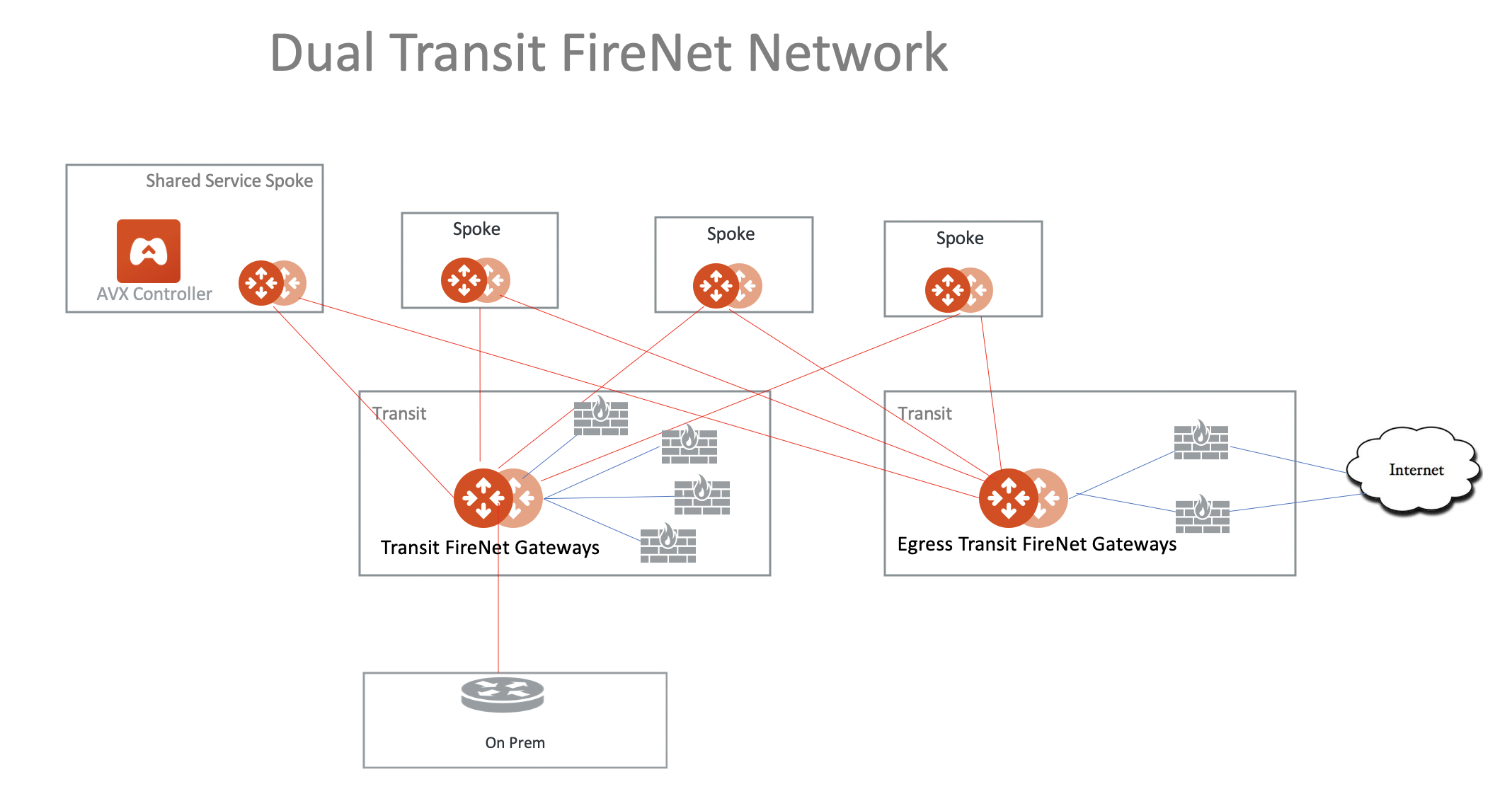
Two Firewall Networks
You can deploy two Firewall Networks, one dedicated for East-West traffic inspection and another for egress inspection.
You must follow this configuration sequence:
-
Disable the Traffic Inspection of the FireNet Gateway intended for egress control.
-
Enable Egress Control for FireNet Gateway intended for egress control.
-
Build connection policies.
Ingress Traffic Inspection
Follow the Ingress firewall instructions to deploy the solution for Ingress traffic inspection.
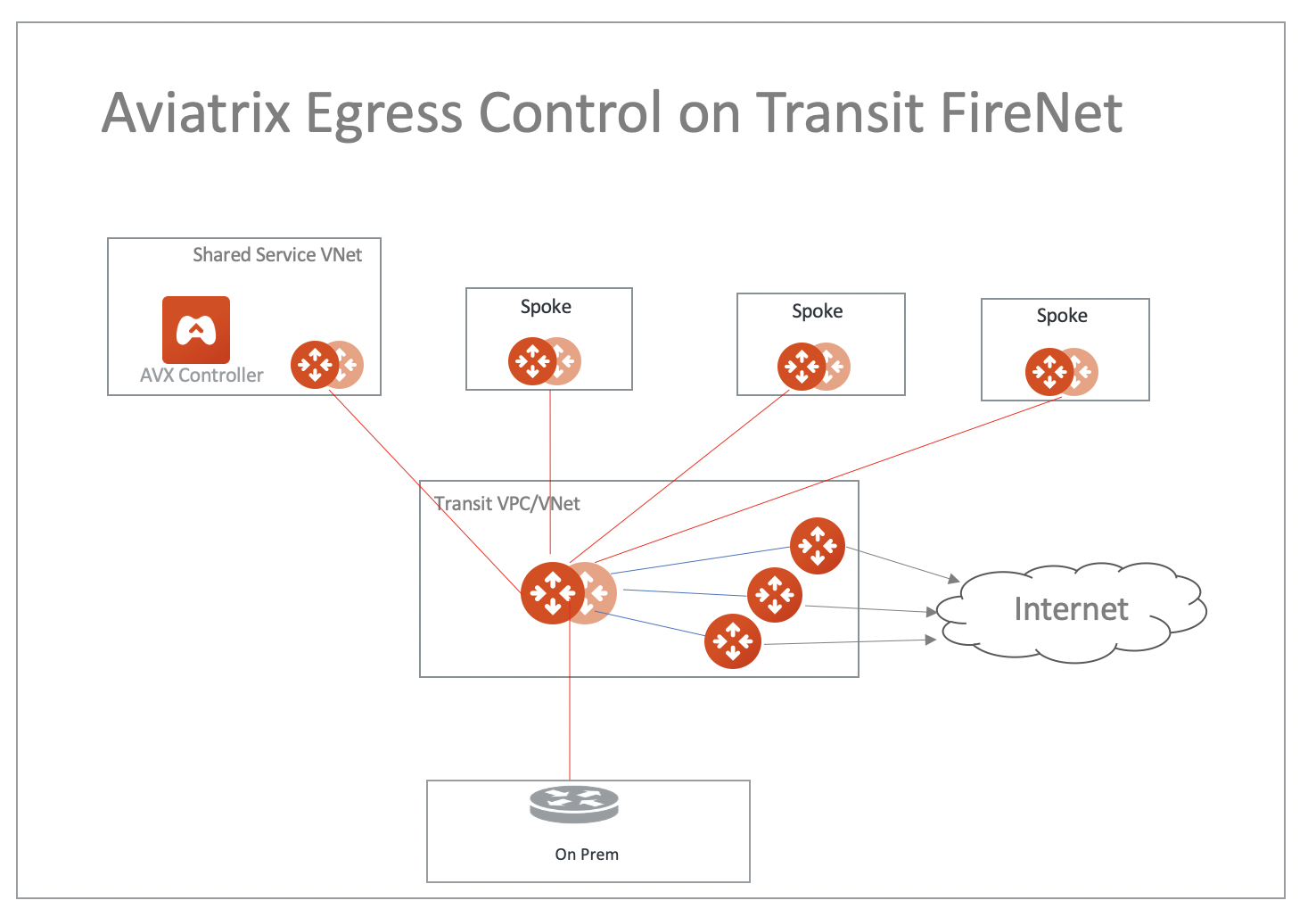
Aviatrix FQDN in FireNet for Egress Control
When an Aviatrix FQDN gateway is deployed in a VPC/VNet, it uses a public IP address to perform both whitelisting and NAT function for Internet-bound traffic. Sometimes these Internet bound traffic are partner API calls and these partners require to limit the number of IP addresses for each customer of theirs. In such situations, you can deploy FQDN in a centralized manner as shown in the diagram below.
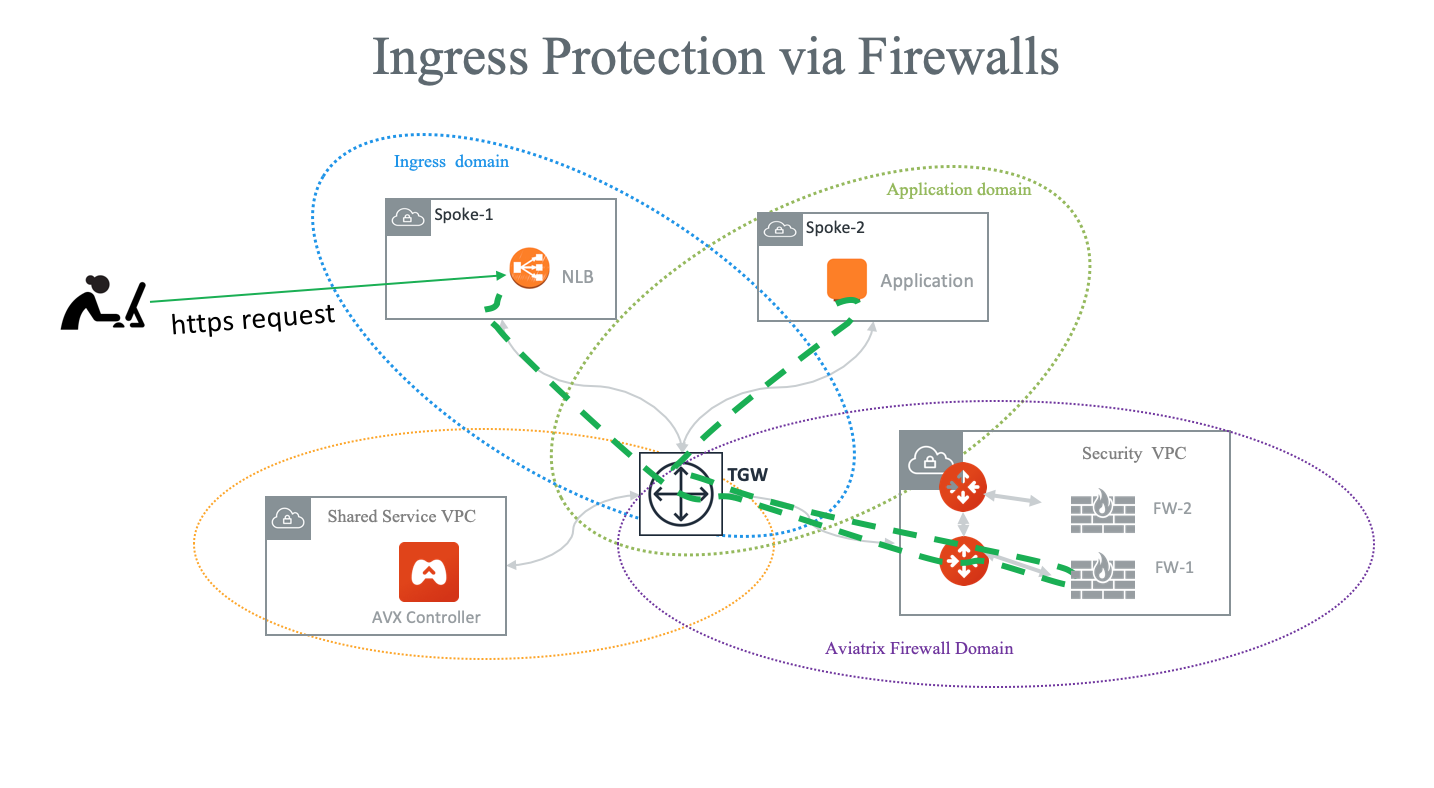
Ingress Directly through Firewall
Another often configured Ingress Egress design pattern is to have the traffic forward to firewall instances directly as shown in the diagram below. In this design pattern, each firewall instance must configure SNAT on its LAN interface that connects to the Aviatrix FireNet gateway. The drawback of this design is that the source IP address is not preserved when traffic reaches the application. If you need to preserve source IP address, refer to this recommended design for Ingress.
For more information, follow the FireNet workflow.
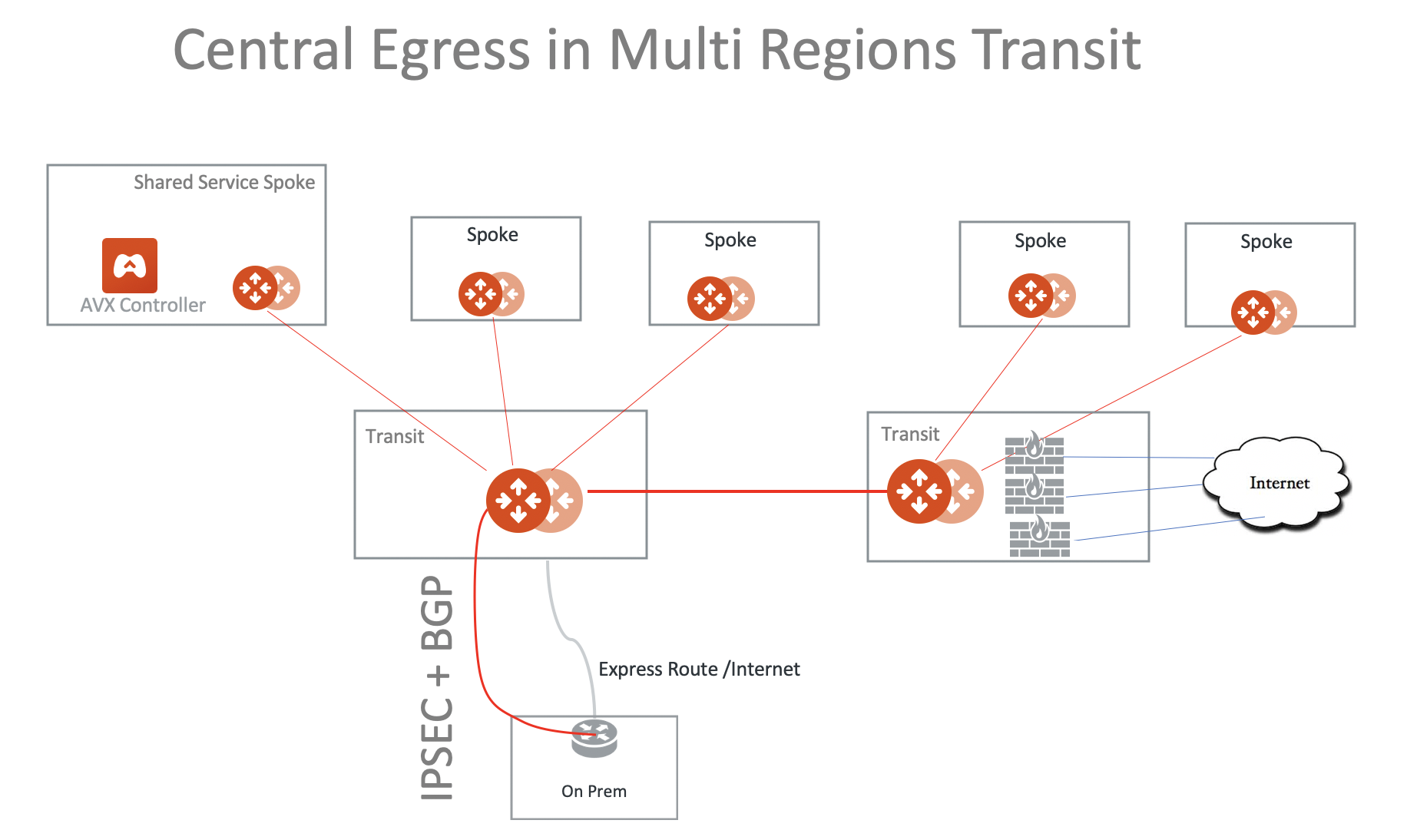
Central Egress in a Multi-Region Deployment
Since the default routes are propagated over the Aviatrix Transit Gateway peering, you can consolidate the Internet-bound egress traffic to the firewalls in one region, as shown in the diagram below.
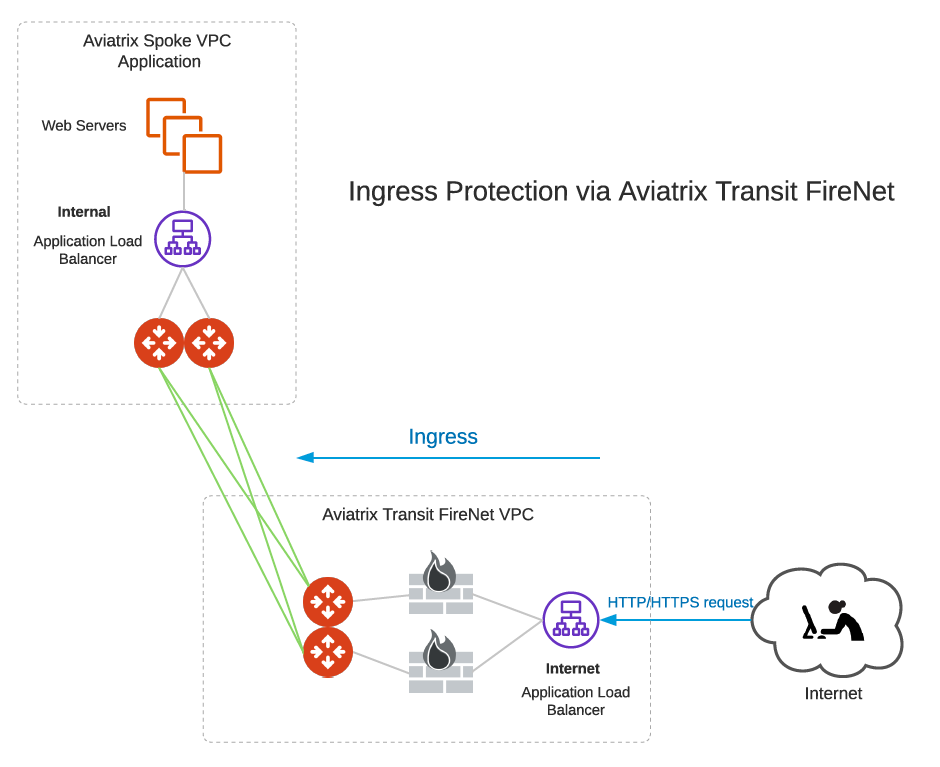
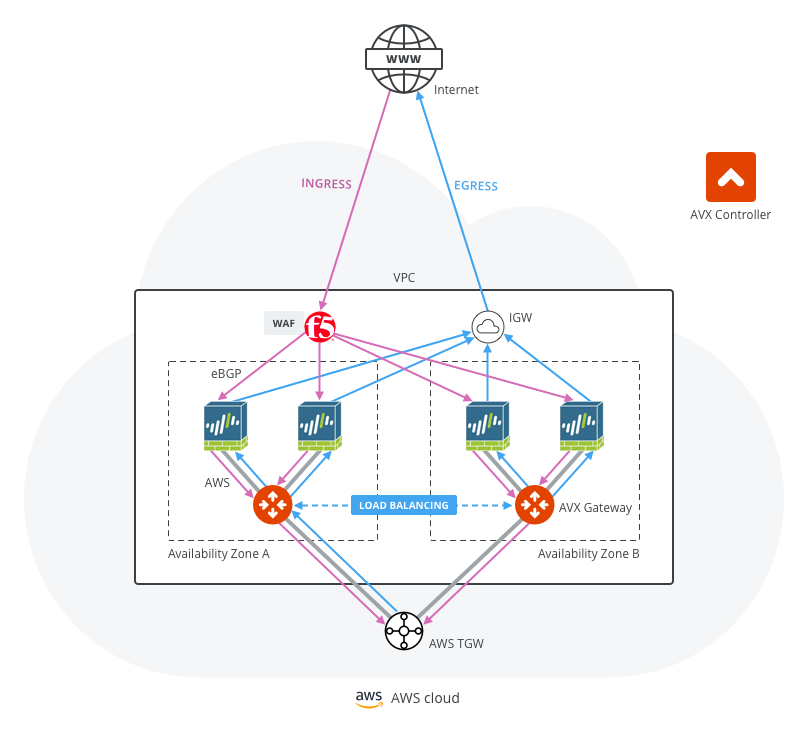
Ingress Protection via Aviatrix Transit FireNet
This Ingress Protection design pattern is to have the traffic forward to firewall instances directly in Aviatrix Transit FireNet VPC/VNet as shown in the diagram below. In this design pattern, each firewall instance must configure (1) SNAT on its LAN interface that connects to the Aviatrix FireNet Gateway and (2) DNAT to the IP of application server/load balancer. The drawback of this design is that the source IP address is not preserved when traffic reaches the application.
For an example configuration workflow, see Ingress Protection via Aviatrix Transit FireNet with FortiGate.