Deploying Aviatrix Secure Edge on Equinix Network Edge
This document provides instructions for deploying Aviatrix Secure Edge on Equinix Network Edge.
Aviatrix Secure Edge on Network Edge Connectivity
The following diagram shows an example of network connectivity for Aviatrix Edge Gateway to Transit Gateway in AWS.
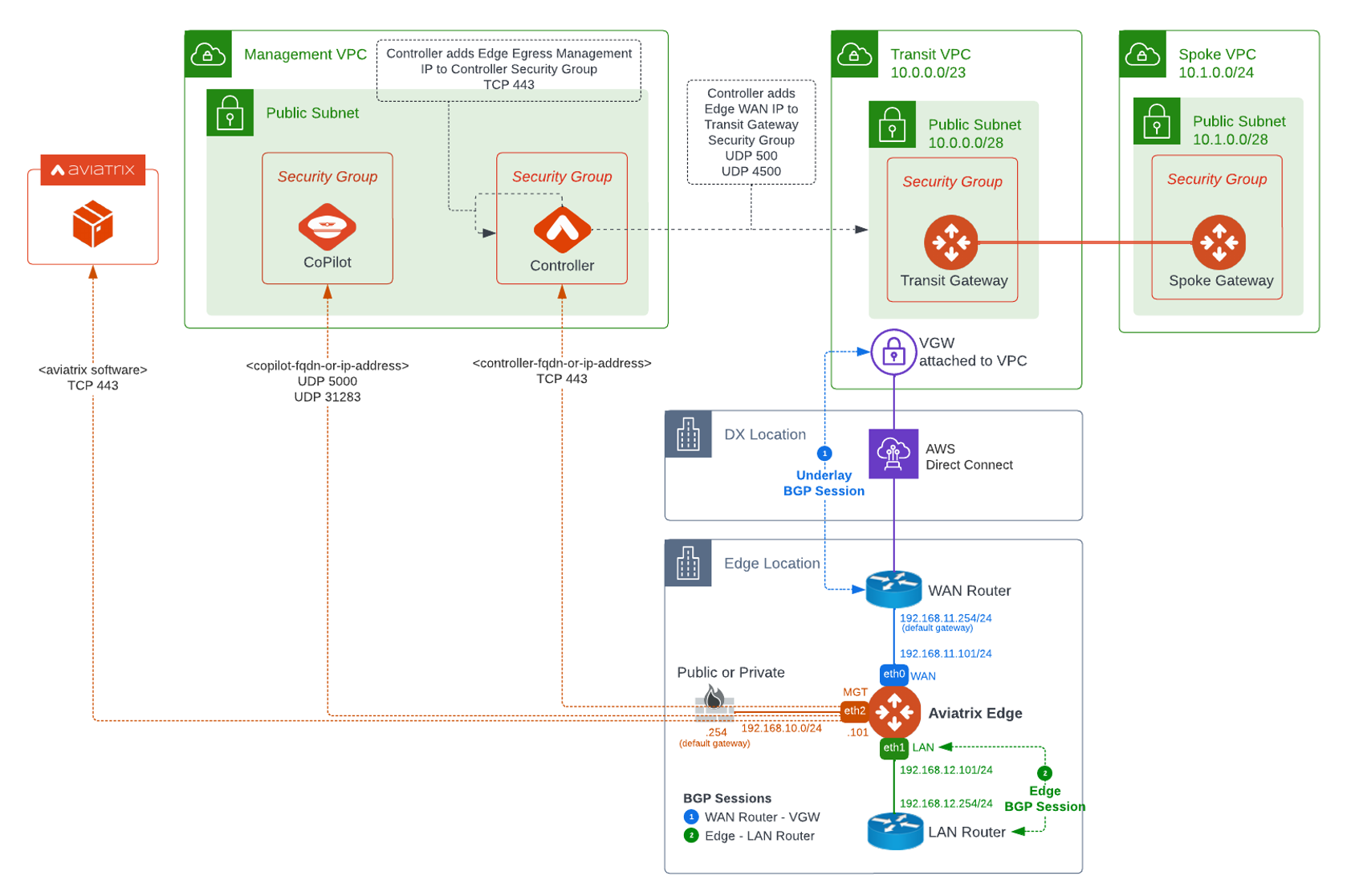
Aviatrix Secure Edge Installation Requirements
Aviatrix Secure Edge for Equinix Network Edge requires the following:
-
Aviatrix Controller 6.8 or later.
-
An Equinix Fabric account.
-
Aviatrix Transit Gateway BGP ASN configured. High-Performance Encryption (HPE) is optional for Edge Gateway attachments.
-
Access to Aviatrix Controller with DNS resolution from the Edge Gateway Management Interface.
Aviatrix Edge Gateway Network Interfaces
Aviatrix Edge Gateway has three interfaces: one WAN interface on eth0, one LAN interface on eth1, and on Management interface on eth2.
| Interface | Description | ||
|---|---|---|---|
WAN on eth0 |
Interface to connect to the Aviatrix Transit Gateway. Requires a default gateway and Layer 3 reachability to Transit Gateway over private circuit. |
||
LAN on eth1 |
Interface to connect to the LAN network. Requires a BGP session with a third-party LAN Router. This can be the same router providing private circuit connectivity to the CSP. |
||
Management on eth2 |
Interface to connect to the Aviatrix Controller. Requires a default gateway, DNS access and Internet access to Aviatrix Controller, Aviatrix software download, and tracelog upload. This interface is configured using Day 0 file cloud-init.txt with the parameters $PUBLIC_ADDRESS_MASK and $PUBLIC_GATEWAY.
|
Aviatrix Secure Edge Deployment Workflow
The diagram below provides a high-level view of the five-step process for deploying Aviatrix Secure Edge on Equinix Network Edge.
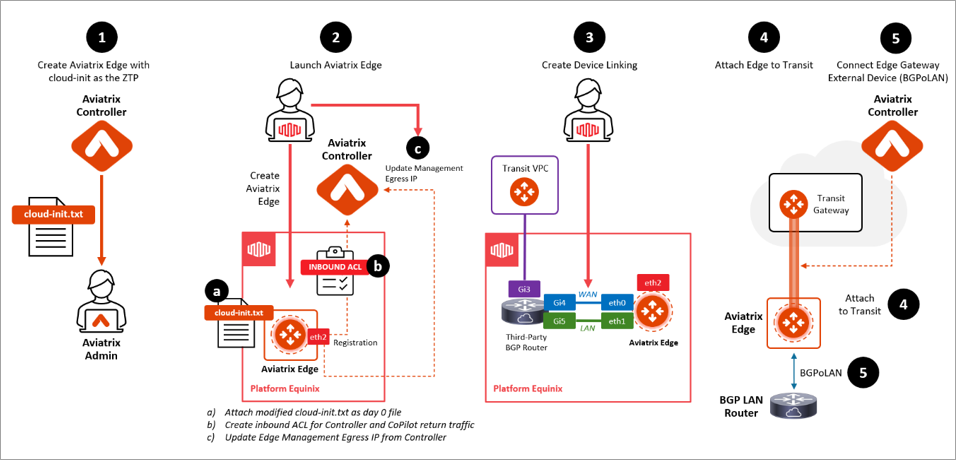
Creating the Edge Gateway Cloud-Init ZTP File
The Edge Gateway cloud-init ZTP file is used to provision the Aviatrix Edge Gateway virtual device in Equinix Fabric.
To create the Edge Gateway cloud-init ZTP file, follow these steps.
-
Log in to Aviatrix Controller 6.8 or later.
-
Go to MULTI-CLOUD TRANSIT > Setup
-
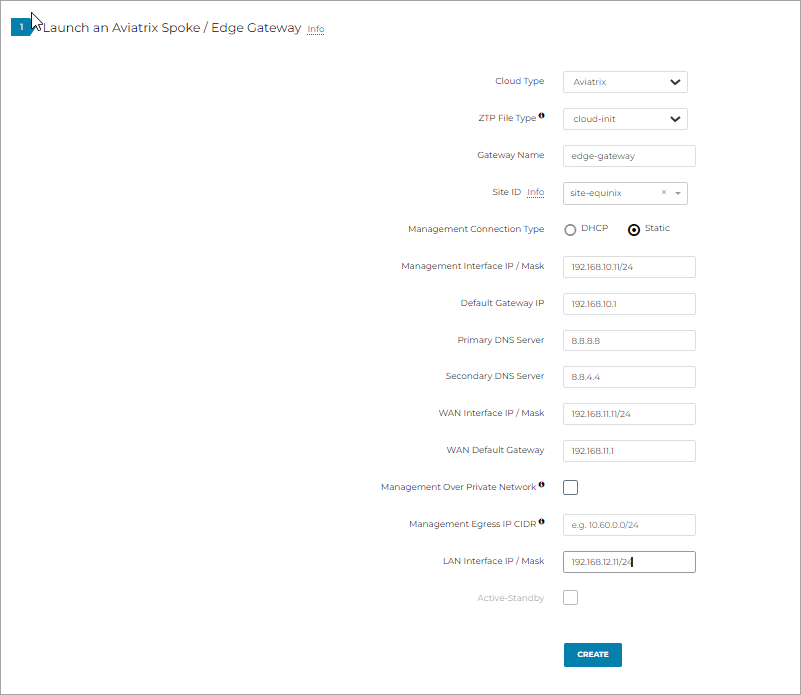
In the Launch an Aviatrix Spoke Gateway page, enter the following values:
-
Cloud Type: Select Aviatrix.
-
ZTP File Type: Select cloud-init.
-
Gateway Name: Enter a name for the new Edge Gateway.
-
Site ID: Select an existing Site ID or create a new Site ID by entering a name (such as, site-equinix) and click Add item.
For guidance on whether to select an existing Site ID or create a new one, see Edge Site ID Guidelines.
-
Management Connection Type: Select Static.
DHCP will not work.
-
(Steps f-n) For IP and DNS settings, enter using the applicable format. For example, if the Edge Gateway’s WAN IP is 10.1.1.151, enter 10.1.1.151/24 or what your netmask is.
-
Management Interface IP/Mask: Enter a placeholder IP address for the management interface IP/mask.
This is a unique placeholder IP address that will be replaced with cloud-init $PUBLIC_ADDRESS_WITH_MASK parameter value. -
Default Gateway IP: Enter a placeholder IP address for the Default Gateway of the Management Subnet.
This is a unique placeholder IP address that will be replaced with cloud-init $PUBLIC_GATEWAY parameter value. -
Primary DNS Server: Enter the DNS server IP address.
-
Secondary DNS server: Enter the DNS server IP address, this field is optional.
-
WAN Interface IP/Mask: Enter the WAN interface IP/mask.
-
WAN Default Gateway: Enter the third-party virtual device WAN interface IP address (for example, CSR Gi4).
-
Management Over Private Network: Leave unchecked. Management IP will be assigned with public IP address with internet access.
-
Management Egress IP CIDR: Leave unchecked. Management Egress IP will be updated later from Aviatrix Controller.
This field adds a security bypass filter rule for the incoming traffic on TCP/443 to your Controller.
-
LAN Interface IP/Mask: Enter the third-party virtual device LAN interface IP/mask (for example, CSR Gi5).
-
To create the ZTP cloud-init image file, click Create.
Controller downloads the ZTP cloud-init file to your Downloads folder.
Controller displays a message that confirms it has successfully downloaded the cloud-init file you created for the Edge Gateway. The cloud-init file is valid for 24 hours after you create it, so you must launch an Aviatrix Secure Edge VM on Equinix platform within that timeframe, as you cannot download it again and will have to recreate the cloud-init file.
Launching the Edge Gateway in Equinix Network Edge
To launch the Aviatrix Edge Gateway in Equinix Network Edge, see Create an Aviatrix Edge in the Equinix documentation.
|
You will need to create an Access Control List Template to allow CoPilot access to the Aviatrix Edge virtual device. |
Once the Aviatrix Secure Edge virtual device is created and provisioned, an email is sent to the notification email you provided informing that the Aviatrix Secure Edge virtual device is provisioned.
Creating the Access Control List Template for CoPilot
The Access Control List Template defines the inbound rules for the Aviatrix Secure Edge virtual device to allow specific inbound traffic. Aviatrix Controller and CoPilot needs to communicate with the Aviatrix Edge Gateway. Inbound traffic from the Controller and CoPilot must be allowed on the Edge Gateway virtual device.
|
Controller’s IP address will be automatically allowed based on the cloud-init. |
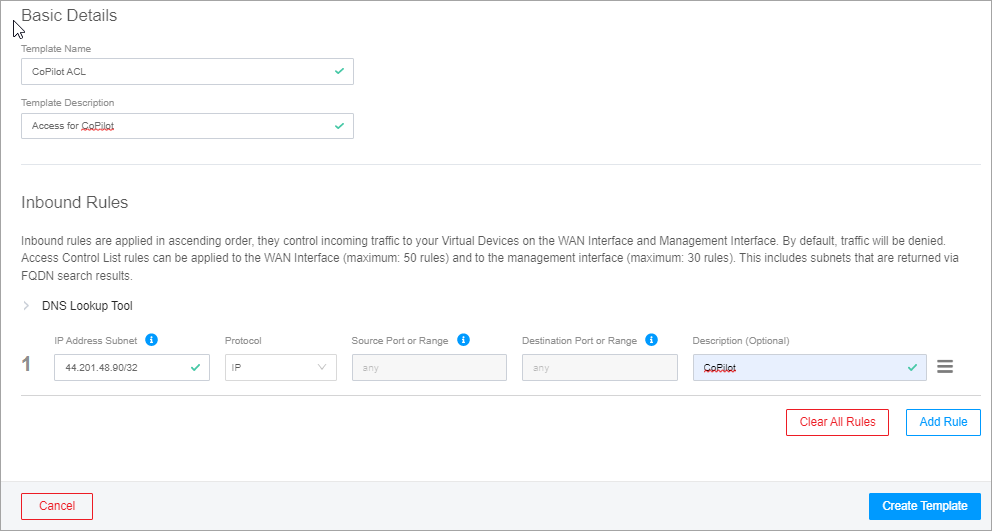
To define the inbound rules for CoPilot, in the CreateNew Access Control List Management Template page, provide the following information.
-
In the Basic Details section, enter a name for the Access Control List template and a description.
-
In the Inbound Rules section, enter the following information:
-
For IP Address Subnet, enter the CoPilot public or private IP address.
-
For Protocol, select IP from the drop-down.
-
For Description (Optional), enter a description for this rule.
-
Click Add Rule.
-
-
To create the Access Control List template, click Create Template.
Configuring the Edge Gateway Management Egress IP Address
The Management Egress IP address of the Aviatrix Edge Gateway virtual device must be updated from the Aviatrix Controller so that the Security Group is updated with the correct Egress IP address.
-
Locate the public IP assigned by Equinix during Aviatrix Edge virtual device creation.
-
From Equinix Fabric Portal, go to Network Edge > Virtual Device Inventory > Details and locate the public IP address of the device.
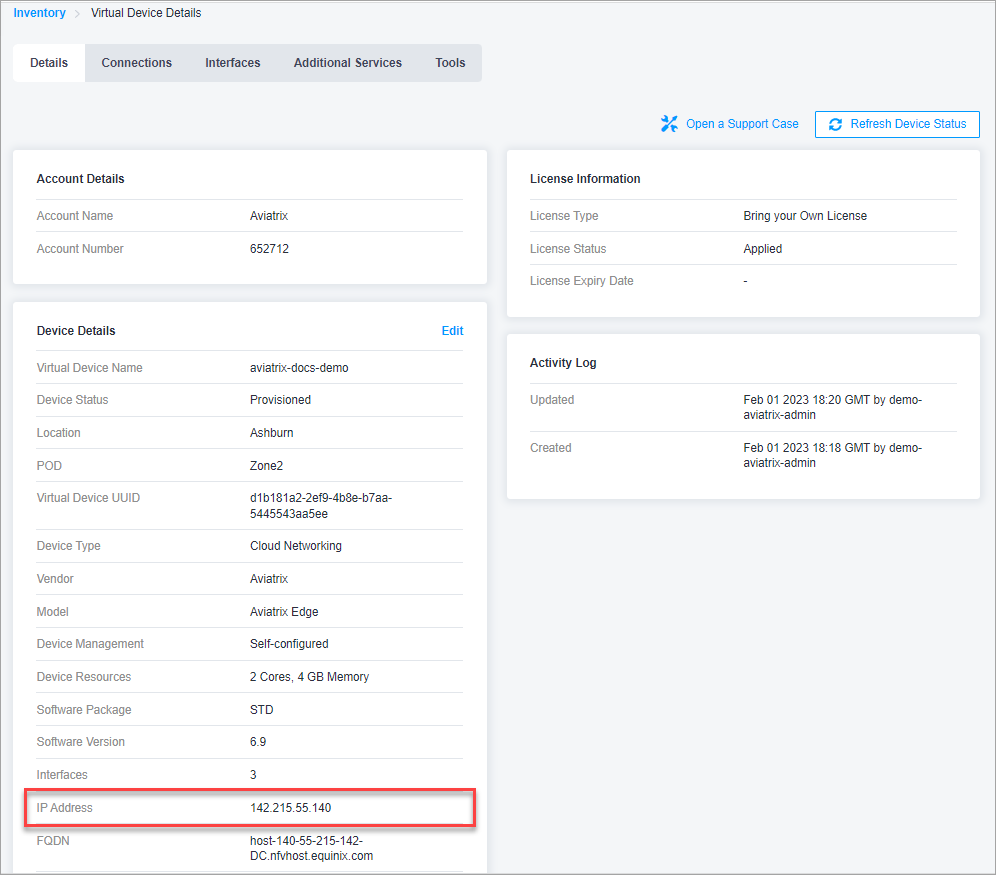
-
-
From Aviatrix Controller, go to Gateway> Select Edge Gateway > Edit >and navigate to the IP Configurations section.
-
In Management Egress IP, copy the public IP from the Equinix Fabric Portal.
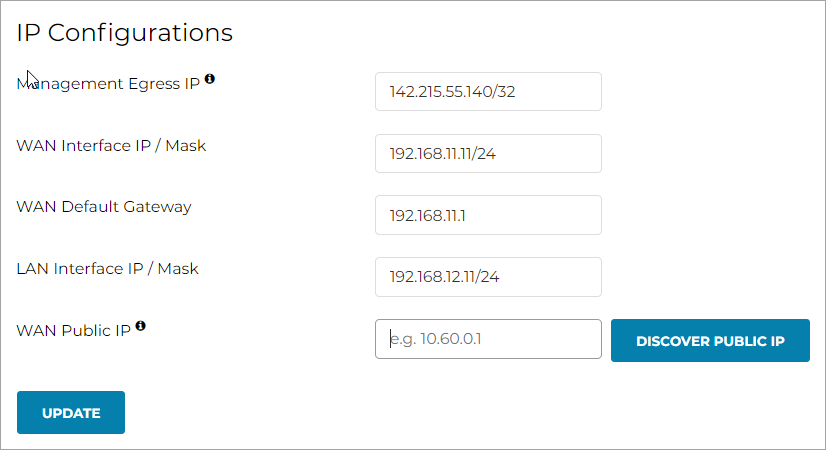
-
Click UPDATE.
Next, verify Edge Gateway is up.
Verifying the Edge Gateway in Controller
To verify the Edge Gateway is up, wait for several minutes after you have configured the Management Egress IP address then do the following:
-
In Aviatrix Controller, go to Multi-Cloud Transit > List > Spoke.
-
In the State column, verify that the Edge Gateway you created is in the up state.
Click the refresh button to update the registration status.
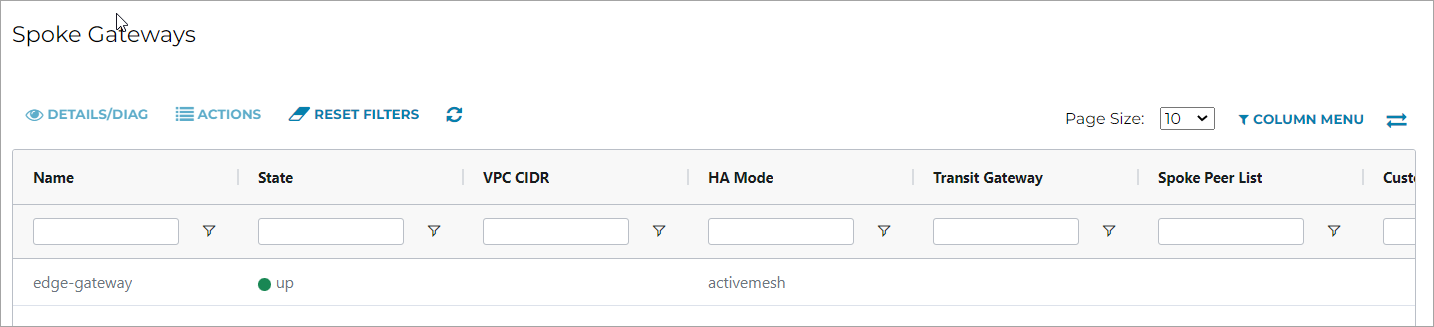
If the Edge Gateway status is not up, you can troubleshoot Edge Gateway connectivity by using CLI commands on the Edge Gateway console. For the Edge Gateway console credential information, see Aviatrix Products: Required Access for External Sites.
Connecting Third-Party Router to the Edge Gateway
Aviatrix Secure Edge for Equinix Network Edge requires a third-party router to provide access to the WAN and LAN networks. The third-party router’s WAN network must provide connectivity to Aviatrix Transit VPC/VNet over private circuits: AWS Direct Connect, Azure Express Route, and GCP Interconnect. The WAN and LAN routers can be separate or a single router leveraging feature such as VRF/VRF-lite. If connectivity to an external LAN (for example, on-prem) is not required, the LAN router is not necessary.
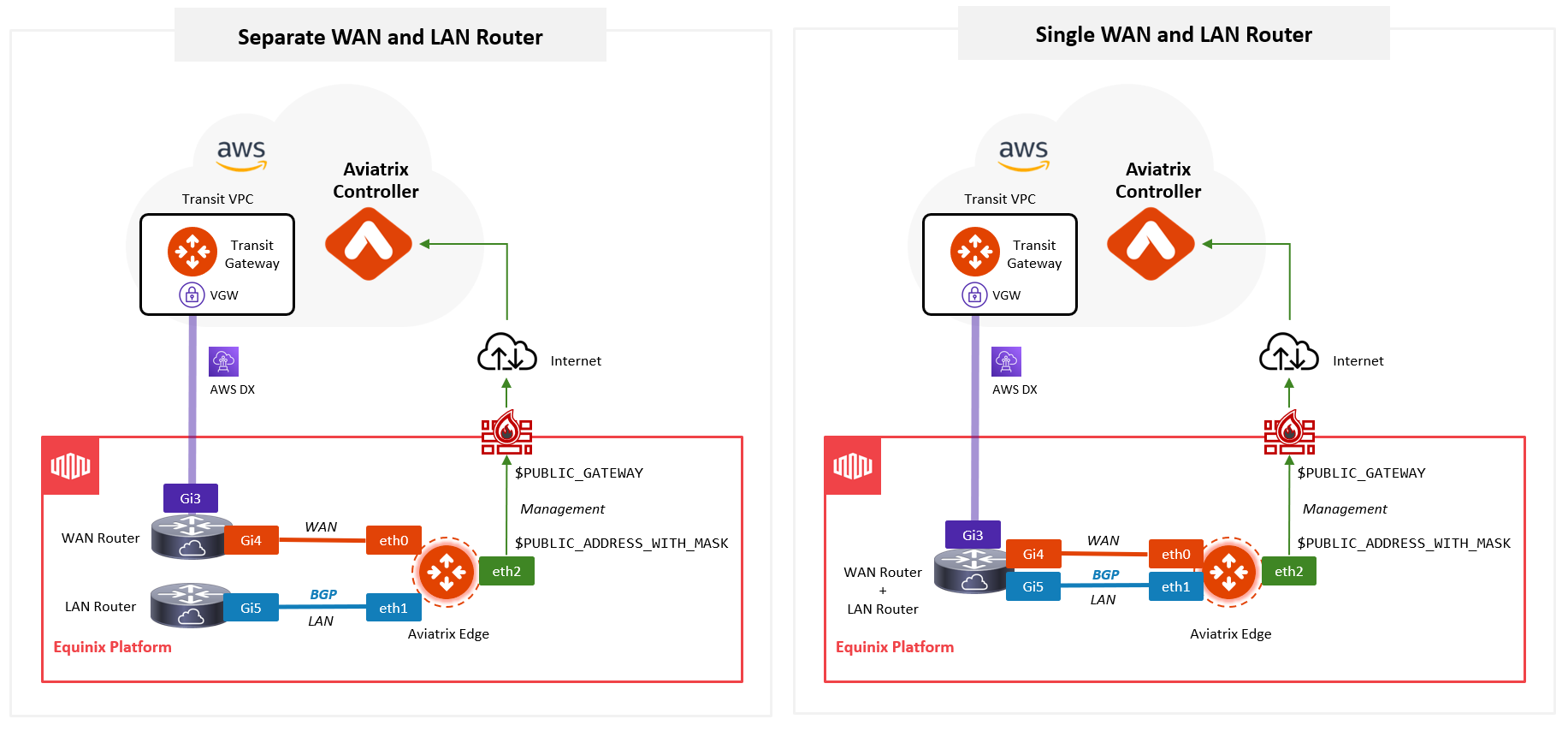
Connect the third-party router to the Edge gateway by using Equinix Network Edge Device Linking.
Attaching the Edge Gateway to the Transit Gateway
You must configure BGP ASN on the Edge Gateway before you attach Edge Gateway to the Transit Gateway.
Configuring BGP ASN on the Edge Gateway
To configure BGP AS Number (ASN) on the Edge Gateway, follow these steps.
-
In Aviatrix Controller, go to MULTI-CLOUD TRANSIT > Advanced Config > Edit Spoke.
-
In the BGP Spoke Gateway pull-down menu, select the Edge Gateway you created and enter the Local AS Number for the Edge Gateway.
-
Click CHANGE.
Attaching Edge Gateway to Transit Gateway
After you have configured the BGP ASNs on both the Transit and Edge Gateway, follow these steps to attach the Edge Gateway to the Transit Gateway.
|
To create an High Performance Encryption Mode attachment, make sure the Transit Gateway is created with High Performance Encryption Mode enabled. |
|
If you want Jumbo Frame enabled on the Edge Gateway, make sure to enable Jumbo Frame on the Edge Gateway before you attach it to the Transit Gateway. See Jumbo Frame. |
-
In Aviatrix Controller, go to MULTI-CLOUD TRANSIT > List > Spoke. Confirm that the Edge Gateway you created is up.
-
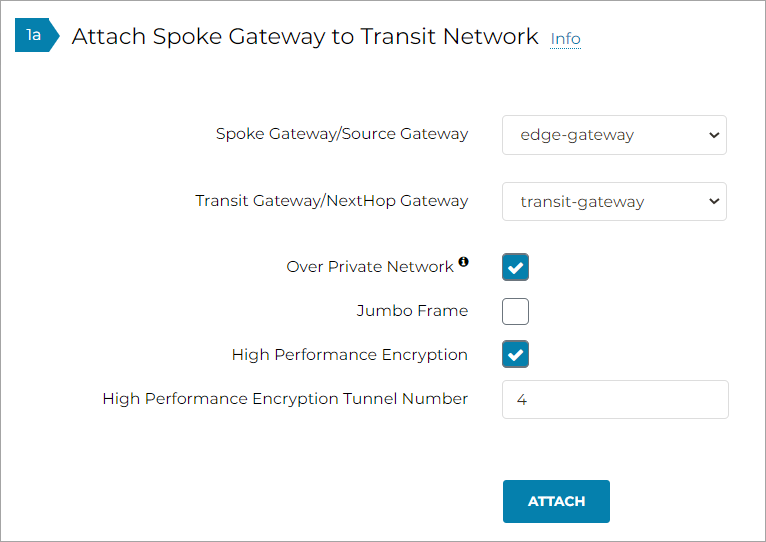
Navigate to MULTI-CLOUD TRANSIT > Setup > Attach / Detach > 1a Attach Spoke Gateway to Transit Network.
-
In the Spoke Gateway/Source Gateway pull-down menu, select the Edge Gateway you created.
-
In the Transit Gateway/NextHop Gateway pull-down menu, select your Transit Gateway.
-
To connect over a private network, check Over Private Network box. Leave unchecked to connect using a public network.
-
To configure Jumbo Frame on Edge Gateway, check Jumbo Frame box.
-
To build High-Performance Encryption (HPE), check High Performance Encryption (HPE) Mode box. Leave unchecked if you do not require HPE.
For High Performance Mode Tunnel Number, enter the number of HPE tunnels to create for High Performance Encryption Mode over the Internet or private network.
-
Click ATTACH.
-
Verify the Edge Gateway attachment in the following ways:
-
From Controller: Navigate to Multi-Cloud Transit > List > Spoke
-
From CoPilot: Navigate to Topology > Network Graph > Network.
-
Connecting the Edge Gateway to an External Device (BGP over LAN)
To connect the Edge Gateway to LAN Routing using BGP over LAN, follow these steps.
-
In Aviatrix Controller, go to MULTI-CLOUD TRANSIT > Setup > External Connection.
-
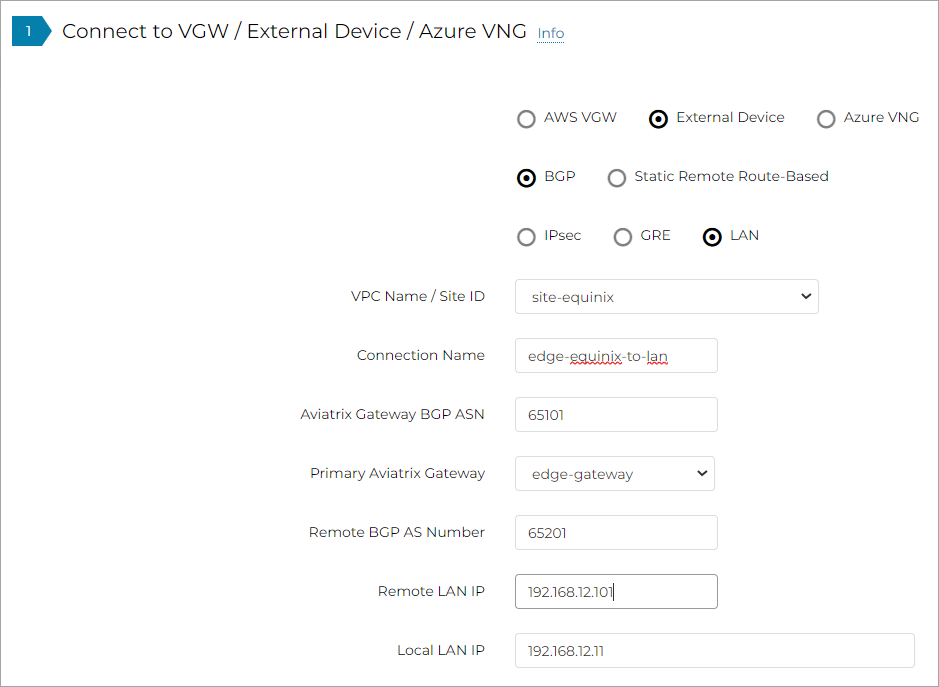
In Connect to VGW/External Device/Azure VNG, enter the following values:
-
Select these options: External Device, BGP, and LAN.
-
VPC Name/Site ID: Select an existing Edge Site ID from the drop-down list.
-
Connection Name: Enter a unique name to identify the connection to the LAN router.
-
Aviatrix Gateway BGP ASN: Enter the BGP AS number the Edge Gateway will use to exchange routes with the LAN router.
-
Primary Aviatrix Gateway: Select the Edge Gateway you created.
-
Remote BGP AS Number: Enter the BGP AS number configured on the LAN router.
-
Remote LAN IP: Enter the LAN router IP address for BGP peering.
-
Local LAN IP: Enter the Edge LAN interface IP address for BGP peering.
-
-
Click CONNECT.