Planning Your Egress Control Deployment
Any vendor specific comments to be noted?
Any GCP instance (excluding Controller-created gateways) that needs to participate in egress control (FQDN, SNAT and FW Egress) has to be tagged as "avx-snat-noip". The GCE network tag "avx-snat-noip" can be associated during GCP instance creation or by editing an existing instance.
What happens if I enable FQDN and there are route tables that have an existing default route?
When enabling egress filtering on a VPC/VNet, each subnet’s route table is reviewed. If there is an existing default route (0.0.0.0/0) in the route table, the following logic is used:
| Target | Aviatrix action |
|---|---|
igw-* |
Ignore this route table |
anything other than igw-* |
Update the Target to point to the AVX GW ENI and remember the current value of Target. (see note below) |
|
If the Gateway is detached from the VPC/VNet (via the egress configuration page), the route table will be updated with the original values. |
Can FQDN gateway be deployed in central place?
Yes. The Aviatrix FQDN gateway can be deployed centrally in the TGW environment as shown in the diagram below.
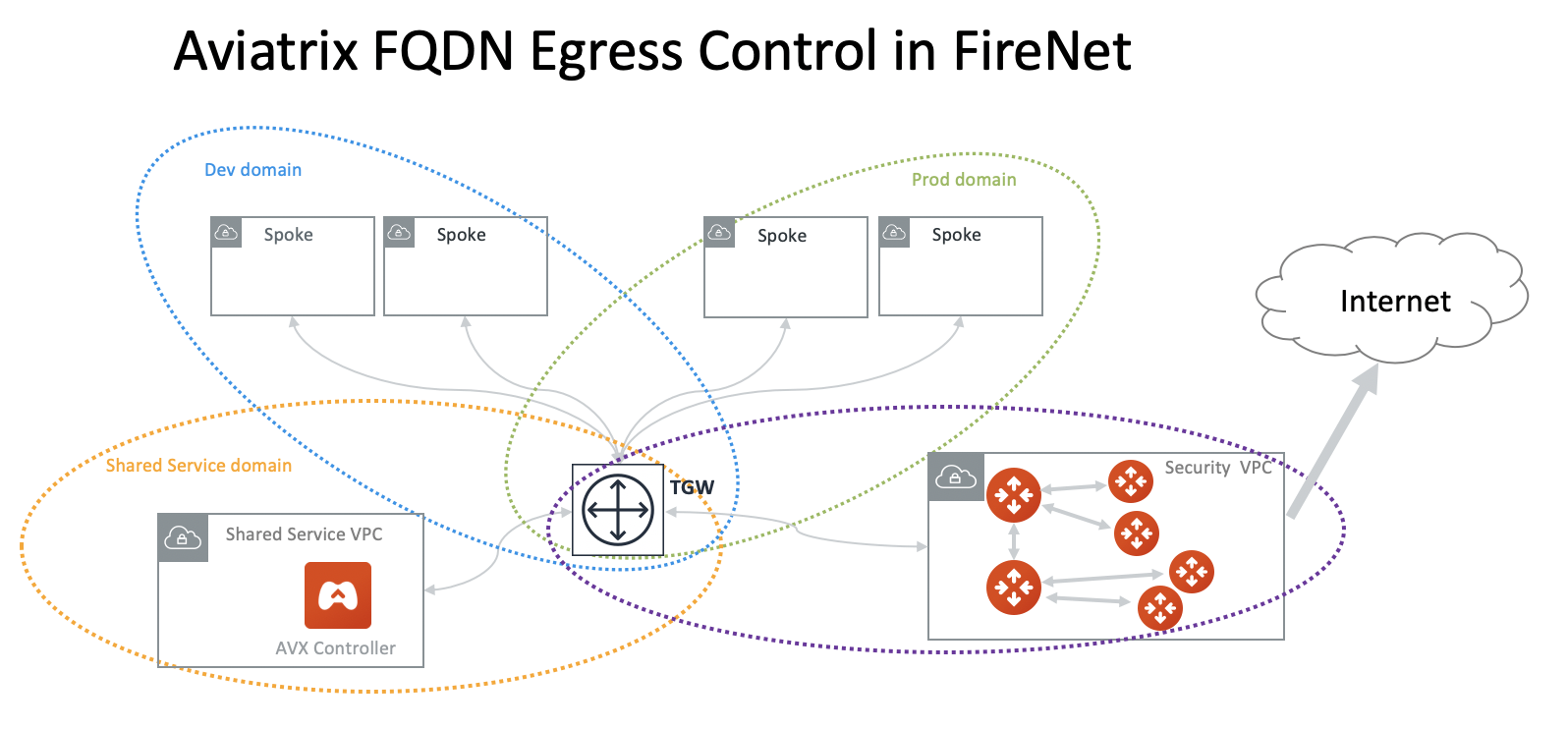
One use case is if you need to limit the public IP addresses to a third-party public service. Follow the Firewall Network workflow to deploy.