Overview of Public Subnet Filtering
Public Subnet Filtering Gateways (PSF gateways) provide both Ingress and Egress security for AWS public subnets where instances have public IP addresses. It includes two parts: Ingress filtering via GuardDuty enforcement and Egress FQDN.
The Public Subnet Filtering function is described in the diagram below.
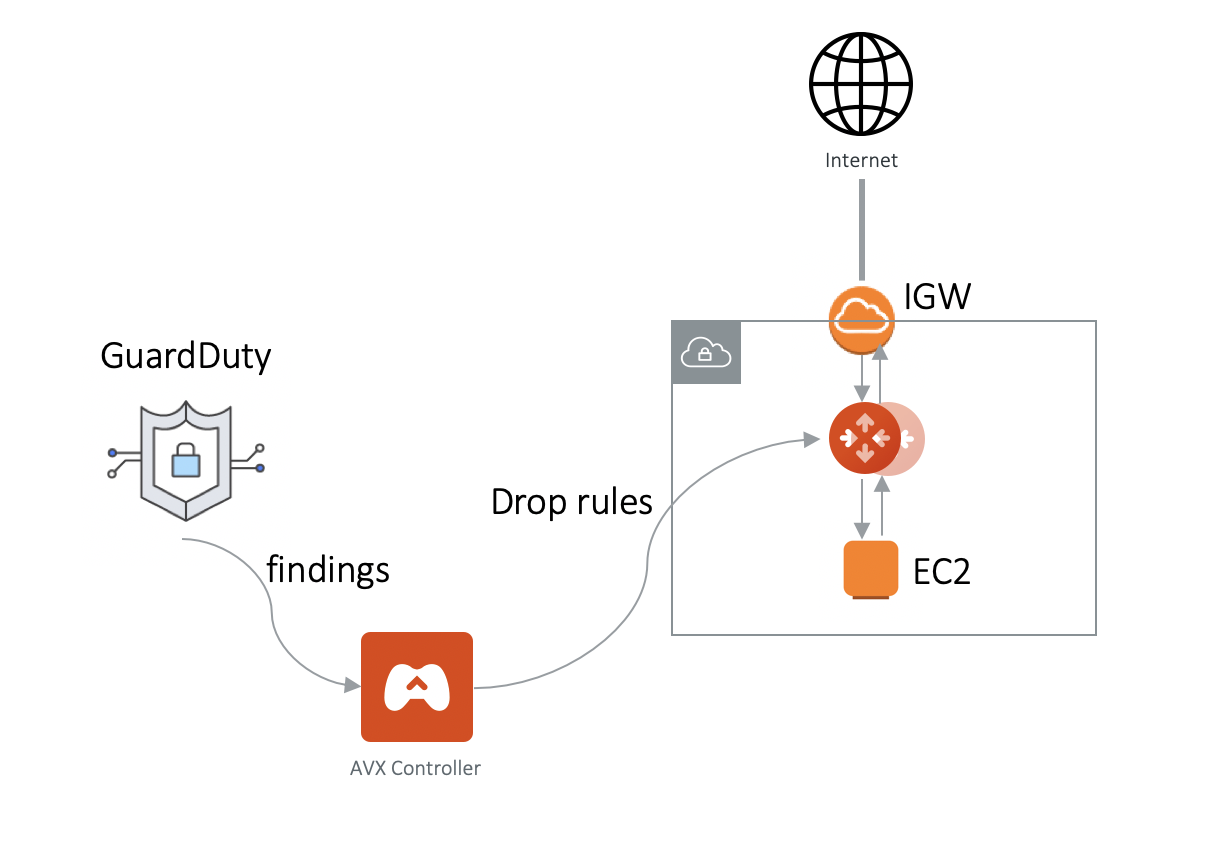
Ingress protection via GuardDuty enforcement is a feature where Aviatrix Controller periodically polls the AWS GuardDuty findings and blocks the malicious source IP addresses from attacking the public subnet instances by programming stateful firewall rules in the filtering gateway.
Egress FQDN is an existing FQDN feature applied to the public subnets. Previously, this feature was only available to filter egress traffic initiated from instances in the private subnets.
Deploying a Public Subnet Filtering gateway
Follow the workflow below.
Launching a Public Subnet Filtering Gateway
-
In the Aviatrix Controller, navigate to Security > Public Subnet > Add New.
-
Fill in the fields as shown in the below table.
| Setting | Value |
|---|---|
Cloud Type |
AWS |
Gateway Name |
Input a unique gateway name |
Account Name |
Select the Access Account |
Region |
Select the AWS region |
VPC ID |
Select the VPC in the chosen AWS region |
Unused Subnet |
Aviatrix Controller creates a public subnet and creates a route table associated with the subnet to launch the filtering gateway |
Gateway Size |
Select an instance type |
Route Table |
Select a route table whose associated public subnets are protected. |
-
Click Create.
After the PSF gateway is launched, Ingress traffic from IGW is routed to the gateway in a pass through manner. Egress traffic from instances in the protected public subnets is routed to the gateway in a pass through manner.
Enabling GuardDuty Enforcement
-
In the Aviatrix Controller, navigate to Security > AWS GuardDuty.
-
Select an Access Account and AWS Region.
-
Click Actions > Enable.
Once GuardDuty is enabled, malicious source IP addresses attacking instances in the public subnets in the region will be polled by the Controller. The Controller then programs rules into the filtering gateway to drop these packets.
|
if you enable AWS GuardDuty without launching the PSF gateway, GuardDuty does not have enforcement functionality. |
Enabling Egress FQDN
Once the PSF gateway is launched, you can configure the FQDN feature.
In the Aviatrix Controller, navigate to Security > Egress Control and follow the instructions in the FQDN workflow.