Bootstrap Configuration Example for VM-Series in AWS
Using the bootstrap option significantly simplifies VM-Series initial configuration setup. In this document, we provide a bootstrap example to set up an "Allow All" and Egress NAT policy for the VM-Series to validate that traffic is sent to the VM-Series for VPC-to-VPC traffic inspection. This example does not use Panorama.
For a manual setup, follow the manual setup example.
If you plan to select AWS S3 Bucket when you create your Palo Alto VM-series firewall using a bootstrap configuration, you must do the following in the AWS console first:
-
Create an IAM Role and Policy
-
Create Bootstrap Bucket Structure
After the firewall is deployed, do the following:
-
(in CoPilot) Upload Config Files
-
(in CoPilot) Configure API Vendor Integration
Creating an IAM Role and Policy
-
Log in to the AWS console and create an IAM role with the name "bootstrap-VM-S3-role" or similar.
-
Attach an IAM policy with the name bootstrap-VM-S3-policy (or similar). The policy has the following statements.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::*"
]
},
{
"Effect": "Allow",
"Action": [
"s3:GetObject"
],
"Resource": [
"arn:aws:s3:::*"
]
}
]
}
Creating the Bootstrap Bucket Structure
In AWS S3, at the top level create a bucket for bootstrap with a unique name (for example "bootstrap-bucket") with the following structure:
bootstrap-bucket/
config/
init-cfg.txt
bootstrap.xml
content/
license/
software/
Only add the folders listed here. Do not add any extra folders or files.
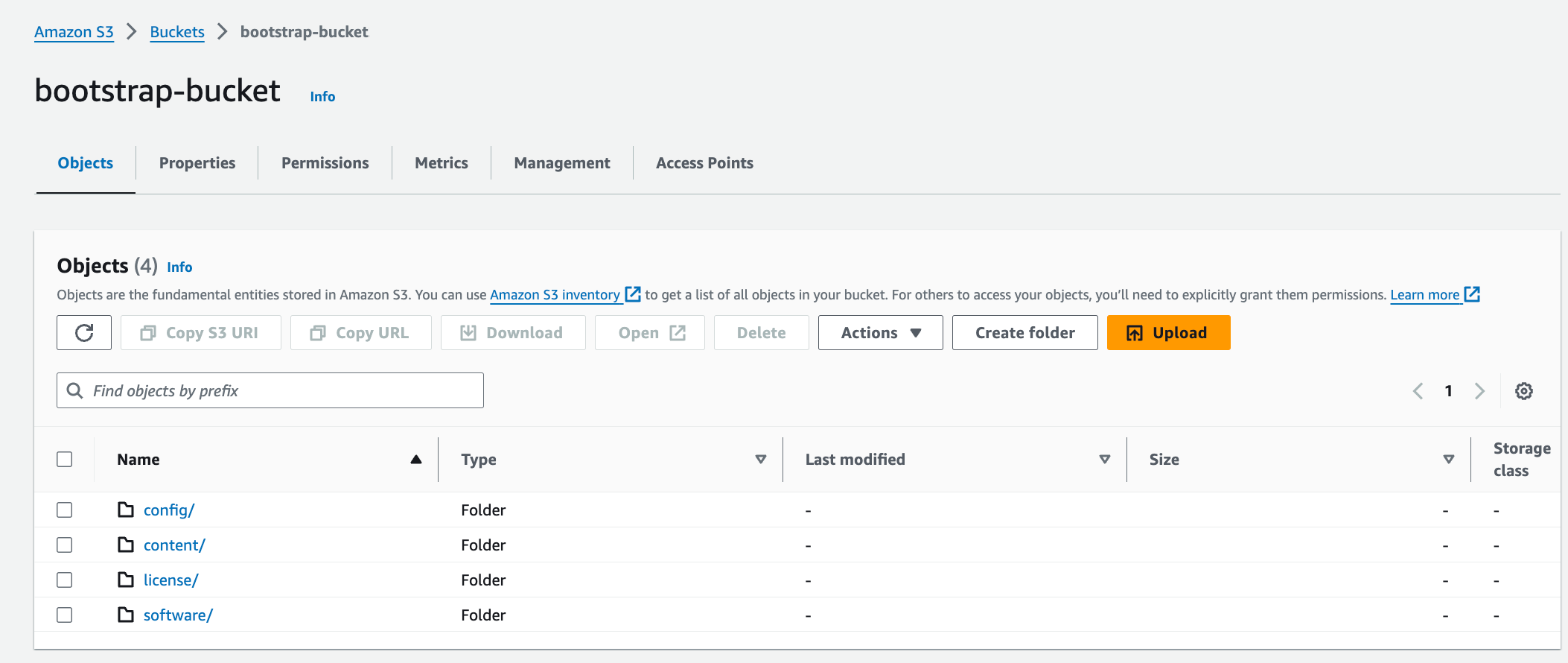
See Prepare the Bootstrap Package (Palo Alto website) for more information.
Uploading Config Files
Complete the following procedures from the Palo Alto VM-Series Deployment Guide to upload the configuration:
Example bootstrap.xml and config files are provided below.
-
The example bootstrap.xml file contains the "Allow All," Egress and API admin setup. To download the file, click bootstrap-aws.xml.
-
For the example init-cfg.txt file, click init-cfg.txt.
|
In the example bootstrap.xml, you must specify custom usernames and passwords for the <https_interface_admin_username> and <api_admin_username>, and generate hash strings for the passwords. |
-
Upload these two files to your config folder under Storage Account > File Shares. <where is this?>
Launching your VM-Series Instance
Go to Deploying a Firewall to launch your Palo Alto VM-Series firewall instance.
Configuring API Vendor Integration
For CoPilot to automatically update firewall instance route tables, monitor firewall instance health, and manage instance failover, you need to set up API access permissions.
-
Navigate to Security > FireNet > FireNet Gateways.
-
In the firewall row, click the vertical ellipsis icon
 and select Vendor Integration.
and select Vendor Integration. -
In the Username field, enter the username specified in the bootstrap.xml file.
-
In the Password field, enter the password specified in the bootstrap.xml file.
If you are manually configuring the firewall from scratch, follow the instructions here to enable API access.
Ready to Go
Now your firewall instance is ready to receive packets.
The next step is to specify which Network Domain needs packet inspection by defining a connection policy that connects to the firewall domain. This is done by Configuring Allow Outbound Policies (see the section above) in the Firewall Network workflow.
For example, deploy Spoke-1 VPC in Network_Domain_1 and Spoke-2 VPC in Network_Domain_2. Build a connection policy between the two domains. Build a connection between Network_Domain_2 to Firewall Domain.
Launch one instance in Spoke-1 VPC and Spoke-2 VPC. From one instance, ping the other instance. The ping should go through.