Example Configuration for FortiGate VM in GCP
You can follow this example to set up the FortiGate Next Generation Firewall instance for GCP, to validate that packets are sent to the FortiGate Next Generation Firewall for VPC-to-VPC and from VPC-to-internet traffic inspection.
|
You must first create a Transit FireNet in GCP, and deploy a Fortinet FortiGate firewall in that Transit FireNet. If you do not use Aviatrix vendor integration, you can manually configure Fortinet route table entries. In GCP, the RFC 1918 routes should point to the firewall LAN interface subnet cloud provider’s default gateways. |
After the firewall launch is complete, you click the Management UI link displayed on the FireNet > Firewall tab to access the FortiGate Next Generation Firewall instance.
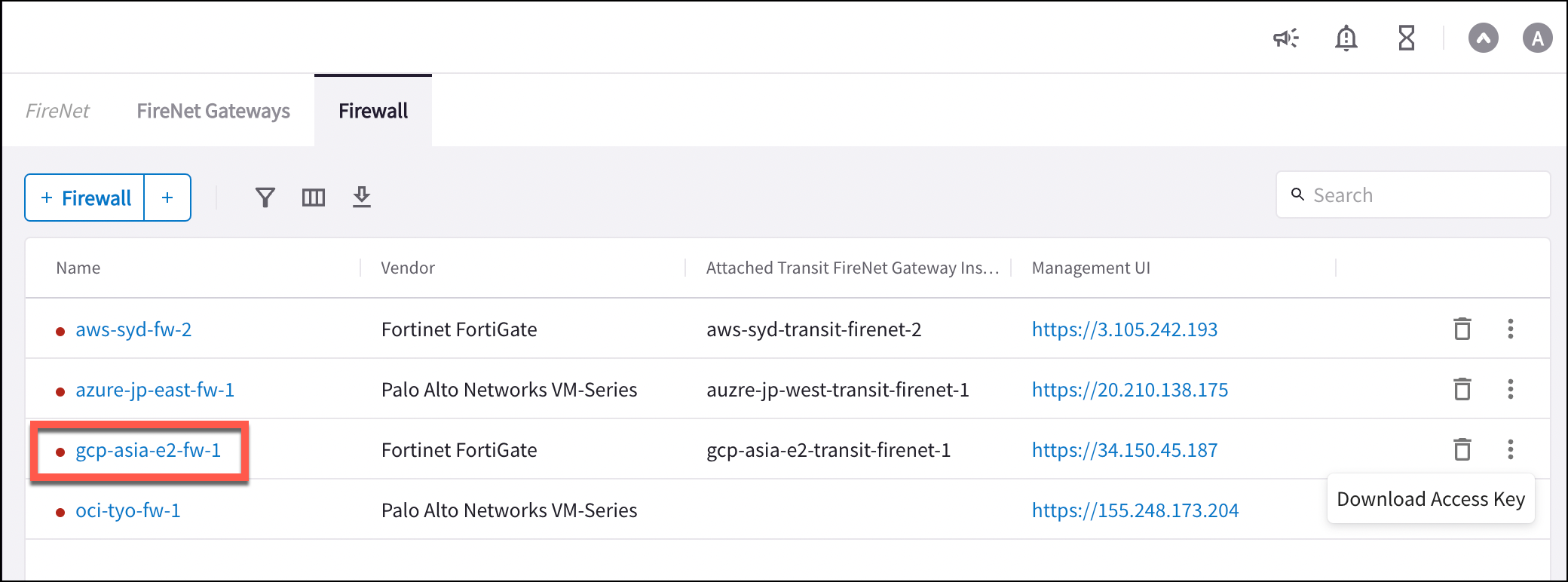
FortiGate Next Generation Firewall Initial Setup
Use the default username and password to log in. Since this is the initial setup of this FortiGate UI, you may be prompted to specify your hostname; change your password; upgrade your firmware; and complete your dashboard setup.
After completing those steps, go to Network > Interfaces in the FortiGate UI and review the interface configuration. This interface configuration was completed by the Aviatrix CoPilot during the firewall launch.
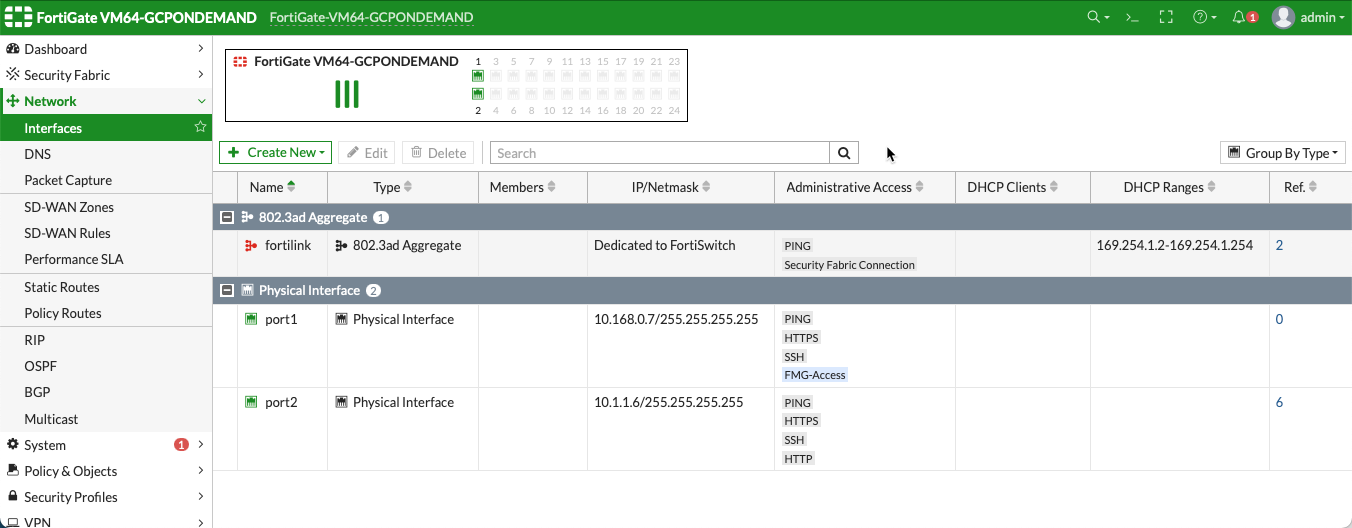
Configuring the LAN Interface
Before configuring the static routes you must configure the port 2 (LAN) interface as follows. The port 1 (WAN) interface does not need to be configured; it is the default management port and is configured during the deployment.
-
In the FortiGate UI, navigate to Interfaces > port2. Configure the interface as follows:
-
Alias: LAN
-
Administrative Access > IPv4: FortiGate requires administrative access to reply to health probes from a network load balancer (load balancers are created automatically in GCP when you set up your Transit FireNet connection). Select the HTTP, HTTPS, SSH and PING checkboxes. When you select HTTPS this opens TCP port 443 to check the health of the firewall.
-
-
Click OK.
-
SSH into the firewall instance using the following command:
ssh I <firewallname.pem>. -
Run the following commands to disable the source check. This enables the firewall to forward packets recieved on that interface:
config system interfaceedit "port2"set src-check disableend
(Optional) Firewall Vendor Integration
Integrating a FortiGate firewall with Aviatrix enables the Aviatrix Controller to make automatic RFC 1918 and non-RFC 1918 route updates to the FortiGate routing tables. You may also manually enable the integration with your cloud management tools. FortiGate integration is supported in AWS, Azure, and GCP clouds.
In this procedure you generate a Firewall API Token from FortiGate. This token is required to integrate the FortiGate firewall with Aviatrix Controller.
-
In the FortiGate UI, navigate to System > Administrators > Create New > REST API Admin.
-
Provide a username and profile for this user.
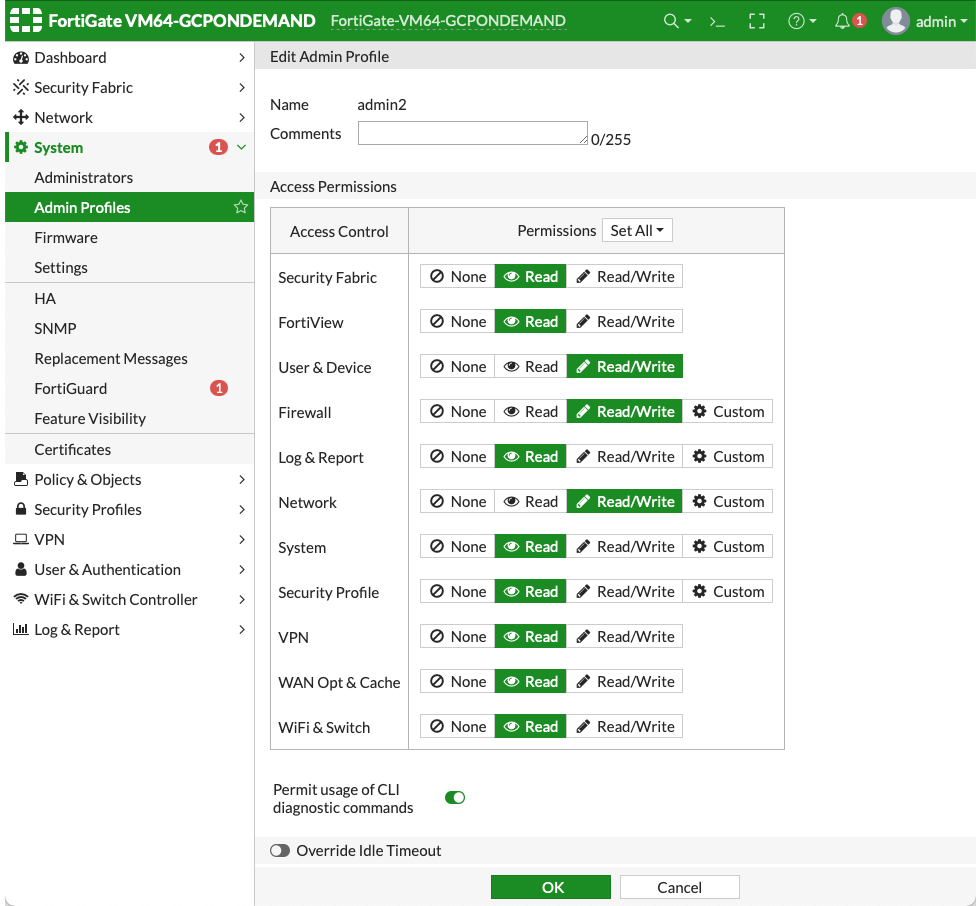
-
Click OK to create the user with this profile. An API key is generated.
-
Copy the key string that displays. It is only displayed once.
-
You now need to make sure that the FireNet configuration information for this firewall is pushed to the firewall management interface. On the FireNet > FireNet Gateways tab, next to the FireNet where you launched this firewall, click the vertical ellipsis
 and select Vendor Integration.
and select Vendor Integration.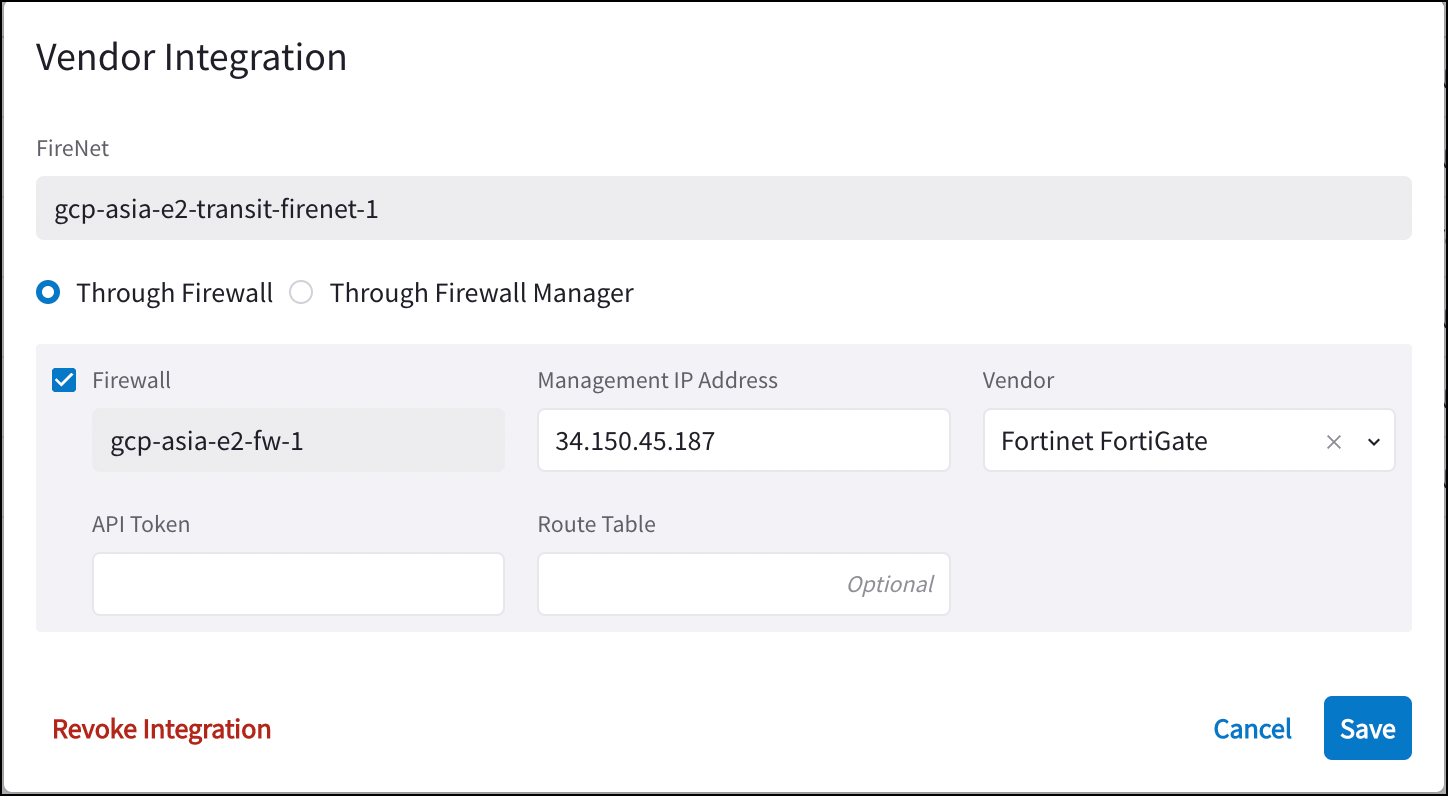
-
Enter the vendor firewall information:
-
Through Firewall or Through Firewall Manager (latter typically only used for Palo Alto firewalls using Panorama).
-
Firewall Management IP Address: IP address of your firewall.
-
Vendor: Fortinet FortiGate.
-
API Token: paste the API token string from step 1 here.
-
Route Table (optional).
-
-
Click Save. Aviatrix Controller is now enabled to make automatic route updates to the FortiGate routing tables.
-
On the FireNet > Firewall tab, you can click the name of the firewall and then click Sync Routes to Firewall in the Details area to sync to the firewall.
| If the necessary routes are not created via vendor integration, you must manually configure routes to the health probe IP ranges on each interface that receives traffic. This prevents the reverse path forwarding check from blocking the health probes. The 0.0.0.0/0 route on the external interface covers the ranges that the external network load balancer uses. |
Configuring a DNAT Policy for Health Check
A DNAT policy is required on the firewall to translate the destination of the health check packets to the firewall interface IP address.
Before you begin, you need the TCP and UDP load balancer front end IP addresses from your GCP portal, along with the firewall instance nic0 internal IP address.
-
In the firewall UI, navigate to Policy & Objects > Virtual IPs and click Create New > Virtual IP.
-
In the New Virtual IP dialog, configure the following:
-
Name: ilb-vip (or an equivalent name of your choosing)
-
Interface: port2
-
Type: Static NAT
-
External IP address/range (TCP load balancer front end IP address)
-
Map to IPv4 address/range (firewall instance port2 IP address)
-
-
Click OK.
-
Repeat steps 1-3 for creating a UDP virtual IP. In this case the External IP address/range is the UDP load balancer front end IP address.
Configuring a Security Policy for Health Check
You now need to create a security policy granting health check access to the virtual IPs you just created.
-
Create two new GCP health check source IP address ranges:
-
In the firewall UI, navigate to Policy & Objects > Addresses and click Create New > Address.
-
Enter a name for the address.
-
In the IP/Netmask field, enter 130.211.0.0/22.
-
Select the port2 interface.
-
Click OK.
-
You may need to create another IP address for 35.191.0.0/16.
-
-
In the firewall UI, navigate to Policy & Objects > Firewall Policy and click Create New.
-
In the Edit Policy dialog, configure the following for the TCP load balancer health check:
-
Name: a name of your choosing
-
Incoming Interface: port2
-
Outgoing Interface: port2
-
Source: select the 130.211.0.0/22 and 35.191.0.0/16 IP addresses you created in the previous step.
-
Destination: ilb-vip (or equivalent, as per what you configured in the previous section)
-
Schedule: always
-
Service: All
-
NAT: disabled
-
-
Click OK.
-
Repeat steps 2-4 to create the UDP load balancer health check.
-
Make sure these are added to the static routes (manually or via Vendor Integration).
Configuring Basic Policy to allow VPC to VPC Traffic
You can configure a basic traffic security policy that allows traffic to pass through the firewall.
-
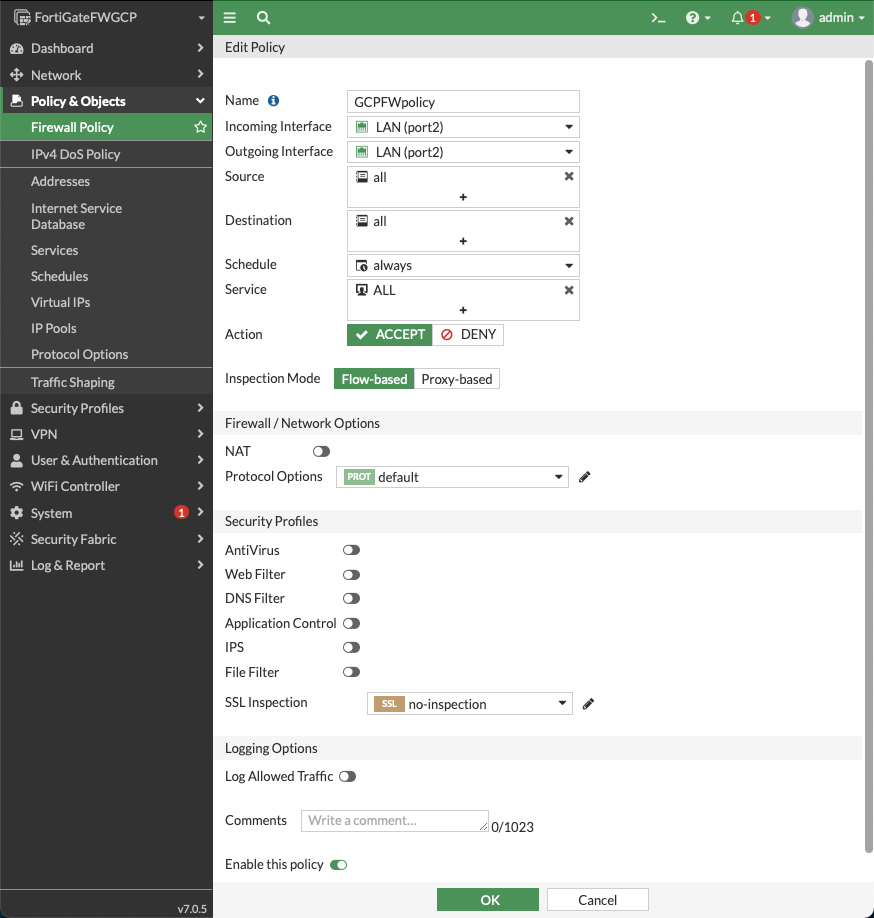
In the FortiGate UI, navigate to Policy & Objects > Firewall Policy and click Create New to configure the policy as per the following screenshot.
-
In the New Policy dialog, configure the following for the basic traffic security policy:
-
Name: configure any name
-
Incoming Interface: port2
-
Outgoing Interface: port2
-
Source: all
-
Destination: all
-
Schedule: always
-
Service: All
-
Action: Accept
-
NAT: disabled
-
-
Click OK.
After validating that your traffic is being routed through your firewall instances, you can customize the security policy to your requirements.
(Optional) Configuring Basic Policy to Allow Traffic from VPC to Internet
You can configure a basic traffic security policy that allows internet traffic to pass through the firewall. Given that Aviatrix gateways will only forward traffic to the LAN port of the firewall, you set your policy condition to match any packet that is going into the LAN interface and out of the WAN interface.
First you must enable egress inspection (if it is not enabled already):
-
On the FireNet > FireNet Gateways tab, click the pencil icon next to the FireNet.
-
In the Edit FireNet dialog, under FireNet Configuration, toggle the Egress slider to On. The Egress column on the FireNet Gateways page indicates that Egress is enabled.
-
Click Save.
In the FortiGate Next Generation Firewall console, you create the new traffic security policy:
-
Navigate to Policy & Objects > Firewall Policy and click Create New.
-
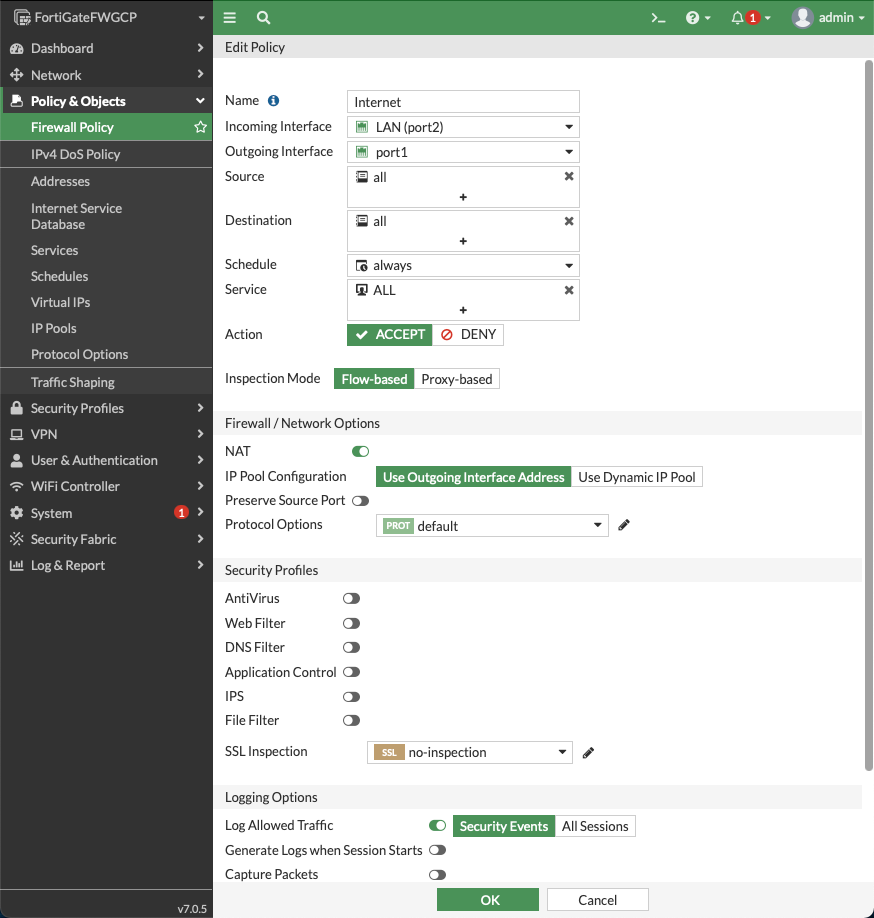
In the New Policy dialog, configure the following:
-
Name: configure any name
-
Incoming Interface: port2 (LAN)
-
Outgoing Interface: port1 (WAN)
-
Source: Click on the + sign and add all
-
Destination: Click on the + sign and add all
-
Schedule: always
-
Service: All
-
Action: Accept
-
NAT: Enable
-
| The NAT function must be enabled on this VPC to internet policy. |
After validating that your traffic is being routed through your firewall instances, you can customize the security policy to your requirements.
Validating Your Configuration
Now your Security Gateway instance is configured and ready to receive packets. The next step is to validate your configurations and polices using FlightPath and Diagnostic Tools (ping, traceroute etc.).
Viewing the Traffic Log
You can view if traffic is forwarded to the firewall instance by logging in to the FortiGate Next Generation Firewall console. Navigate to Dashboard > FortiView Sessions or FortiView Destinations. Traffic can also be viewed from Log & Report.
| To view Forward Traffic logs under Logs & Report, navigate to Policy & Objects > Firewall Policy. Select a policy and click Edit. Under Logging Options, select All Sessions for Log Allowed Traffic. |
Testing Traffic Flow
You can configure a packet capture in the FortiGate UI to test traffic flow.
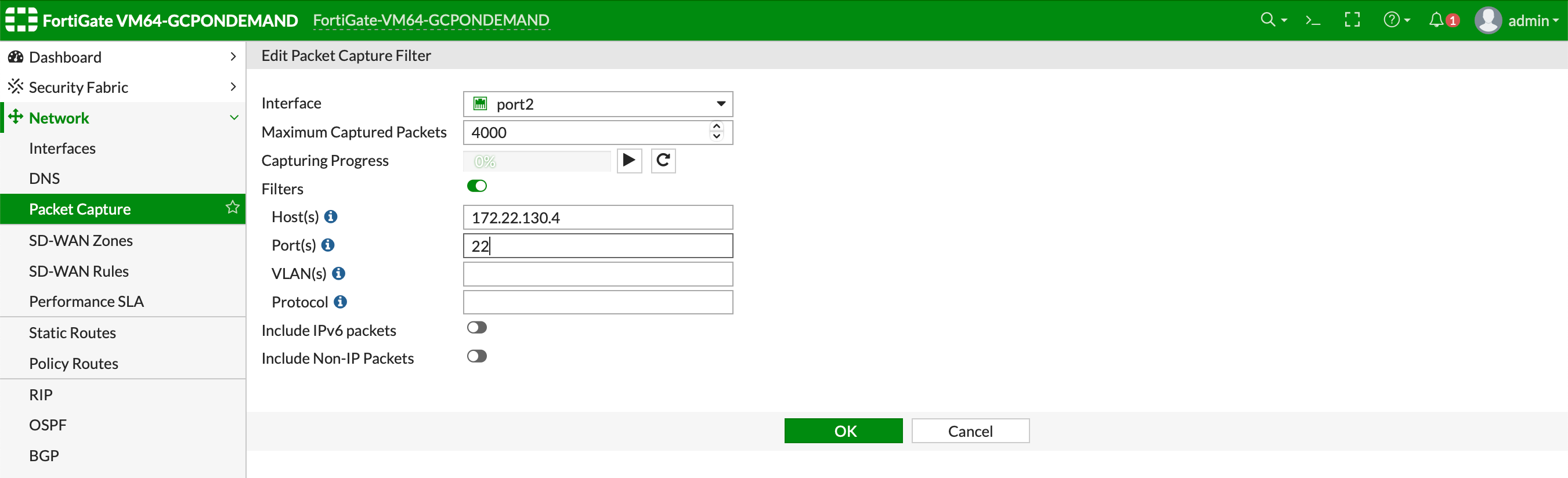
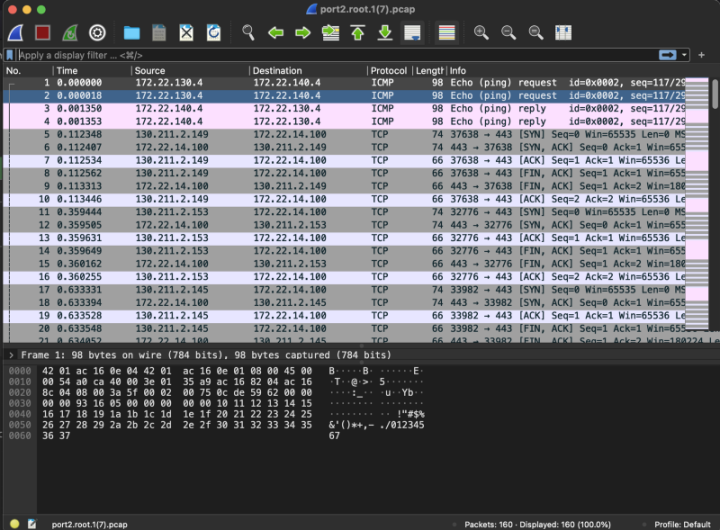
In this example, the spoke10 instance (172.22.130.4) pings the spoke20 instance (172.22.140.4).
You can also use CoPilot AppIQ to check traffic flow and troubleshoot any issues.