Firewall Instance Health
Palo Alto VM-Series
When vendor integration is enabled, Aviatrix CoPilot pings the individual firewall management interface every 10 seconds. If two consecutive pings fail, the firewall is declared down and is moved to "down" state. CoPilot continues to ping the management interface. If consecutive pings become successful, the firewall instance is attached back to the FireNet Gateway pool.
You can also check the health of a firewall instance by pinging its LAN interface from the connecting FireNet gateway. This alternative approach improves firewall failure detection time and accuracy. The FireNet gateway pings the LAN interface every five seconds with a ping time out of 20 milliseconds. If the first ping times out, it immediately pings again. Two consecutive ping failures indicate the firewall is in Down state and it is detached from the FireNet gateway pool. The ping function will continue, and after it detects that the firewall instance is back up (successful pings) it is reattached to the FireNet gateway pool.
Enabling Ping on VM-Series Firewall
-
Go to Network > Network Profiles > Interface Mgmt and create profile to allow ping.
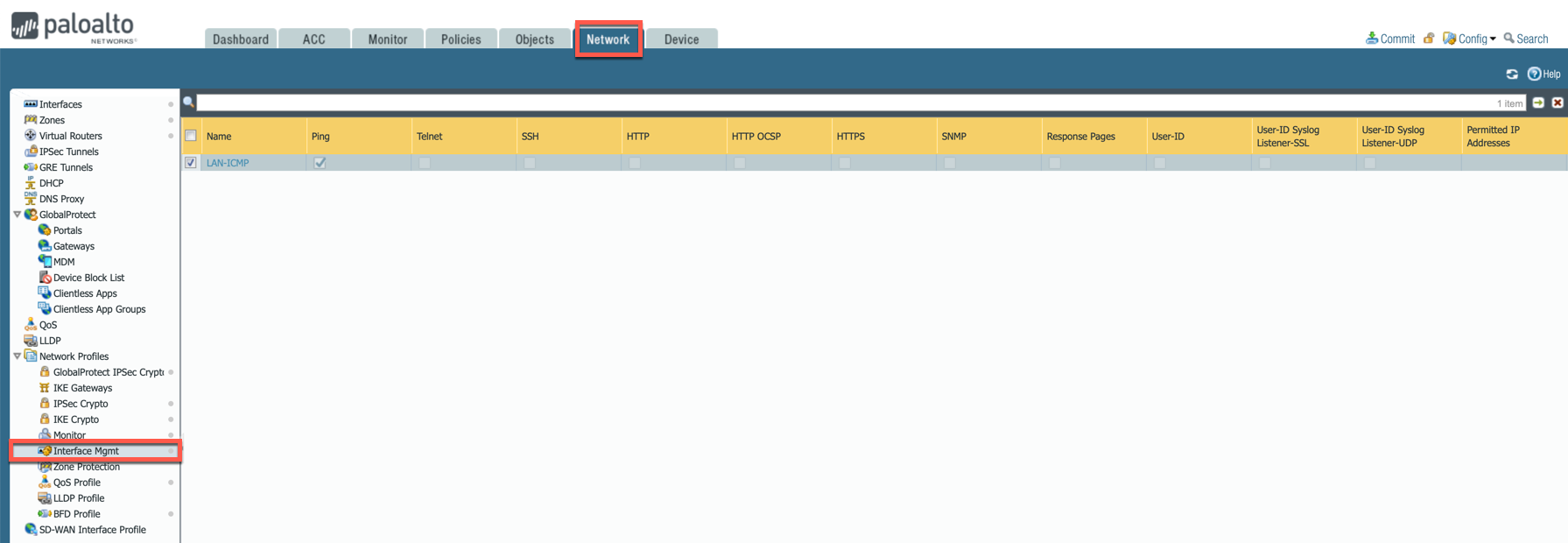
-
Go to Network > Interfaces, select Ethernet 1/2, go to the Advanced tab > Management Profile and select the profile just created in the step above.
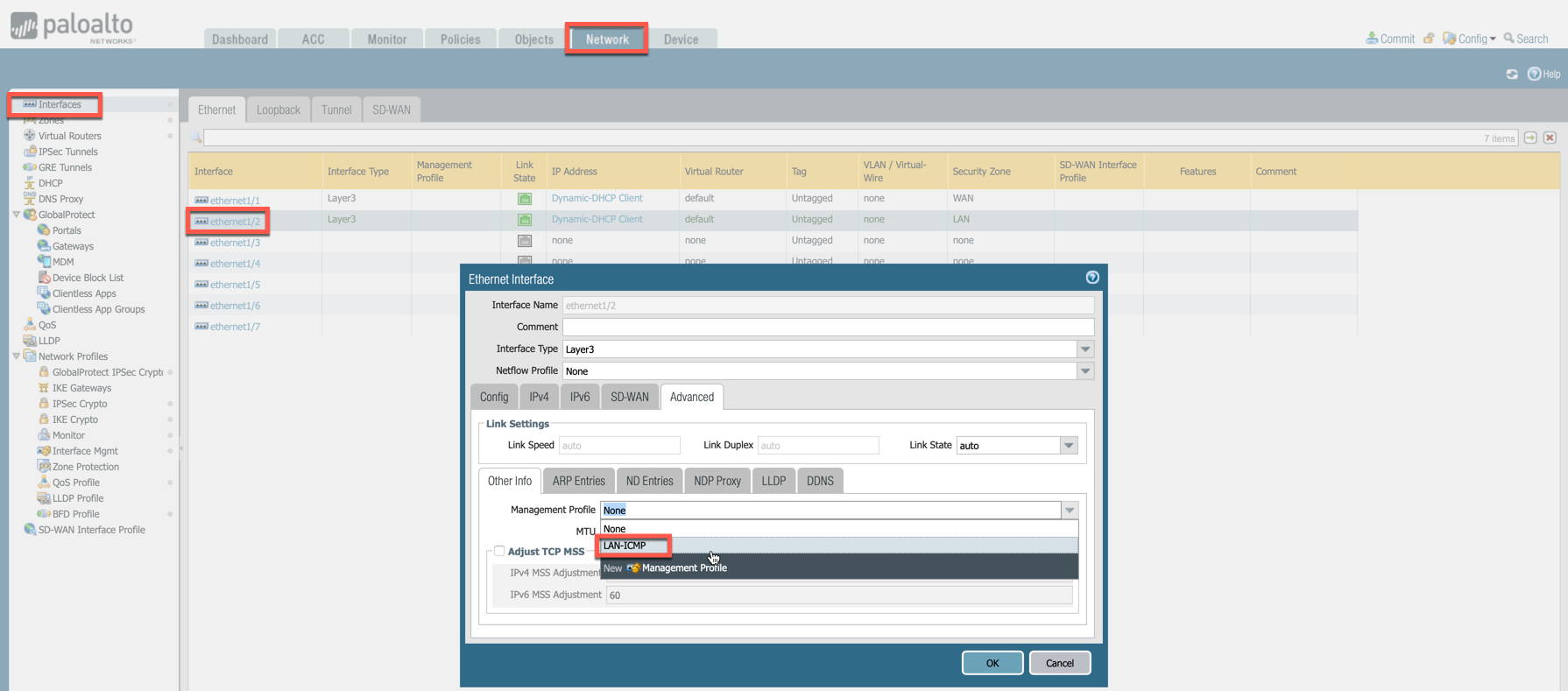
-
Commit changes.
Check Point and Fortinet
For Check Point CloudGuard and Fortinet FortiGate, CoPilot uses AWS API to check instance health.
Enabling Ping on Check Point and Fortinet
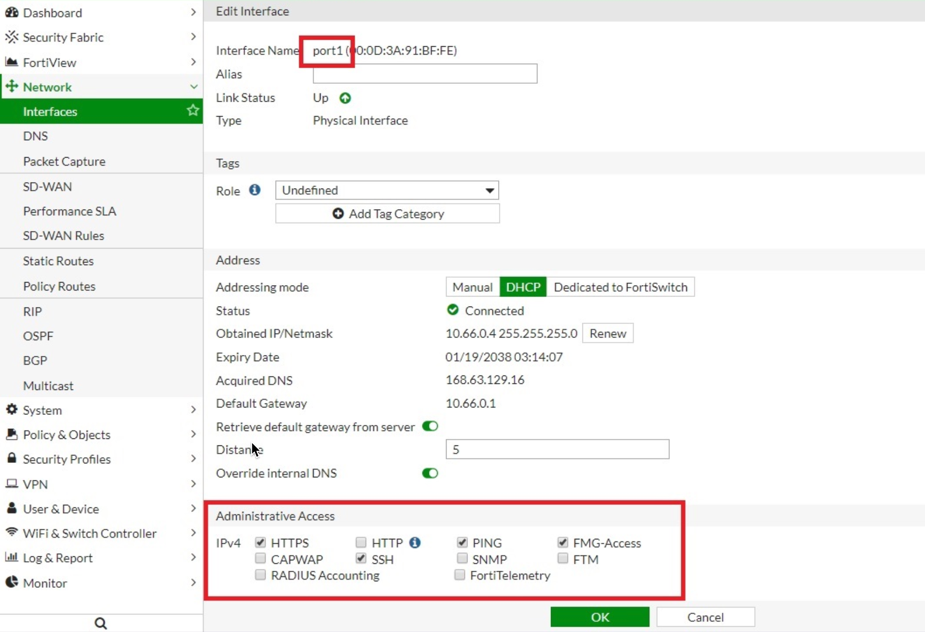
In the Fortinet FortiGate UI, navigate to Network > Interfaces > Edit Interface and select the PING checkbox.
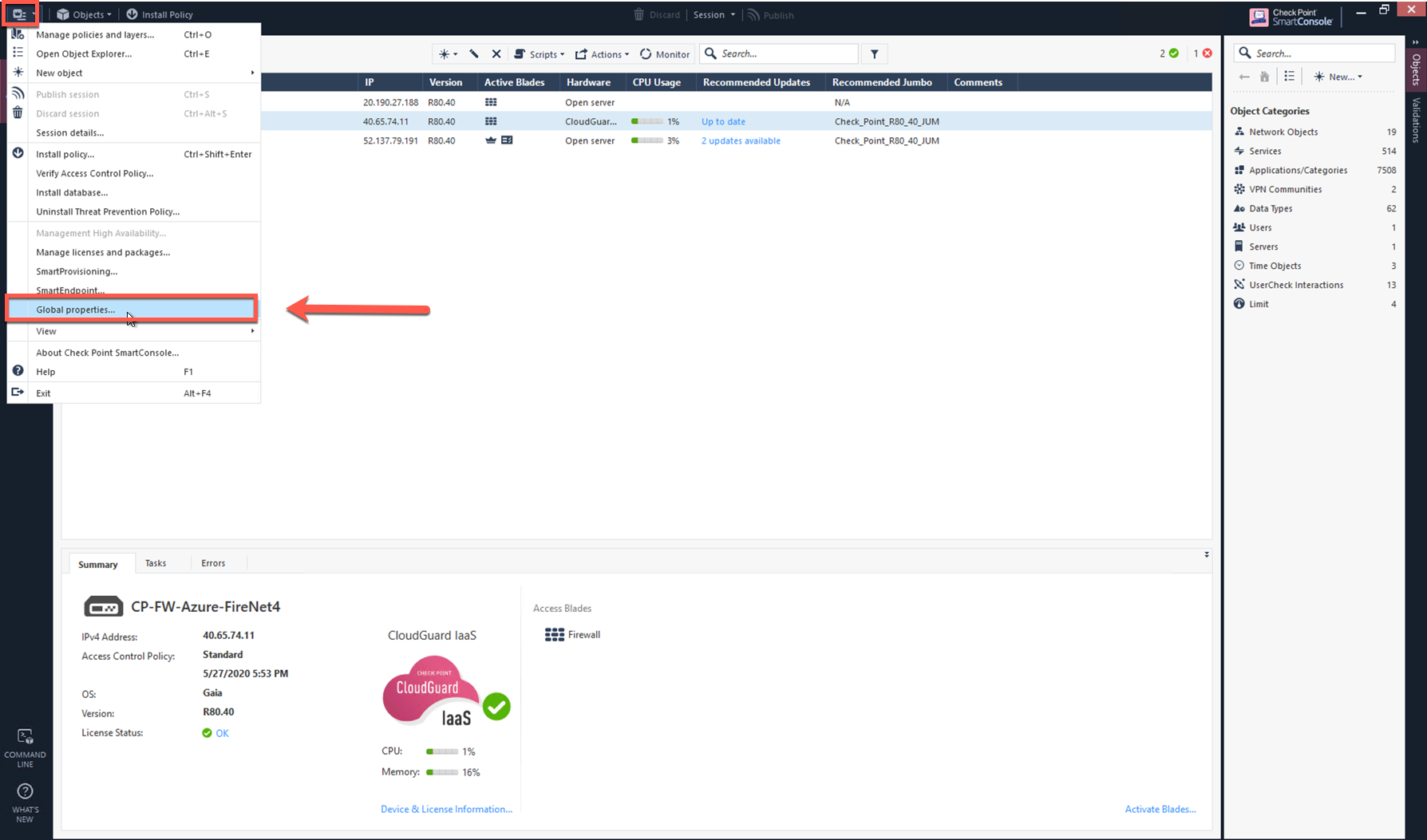
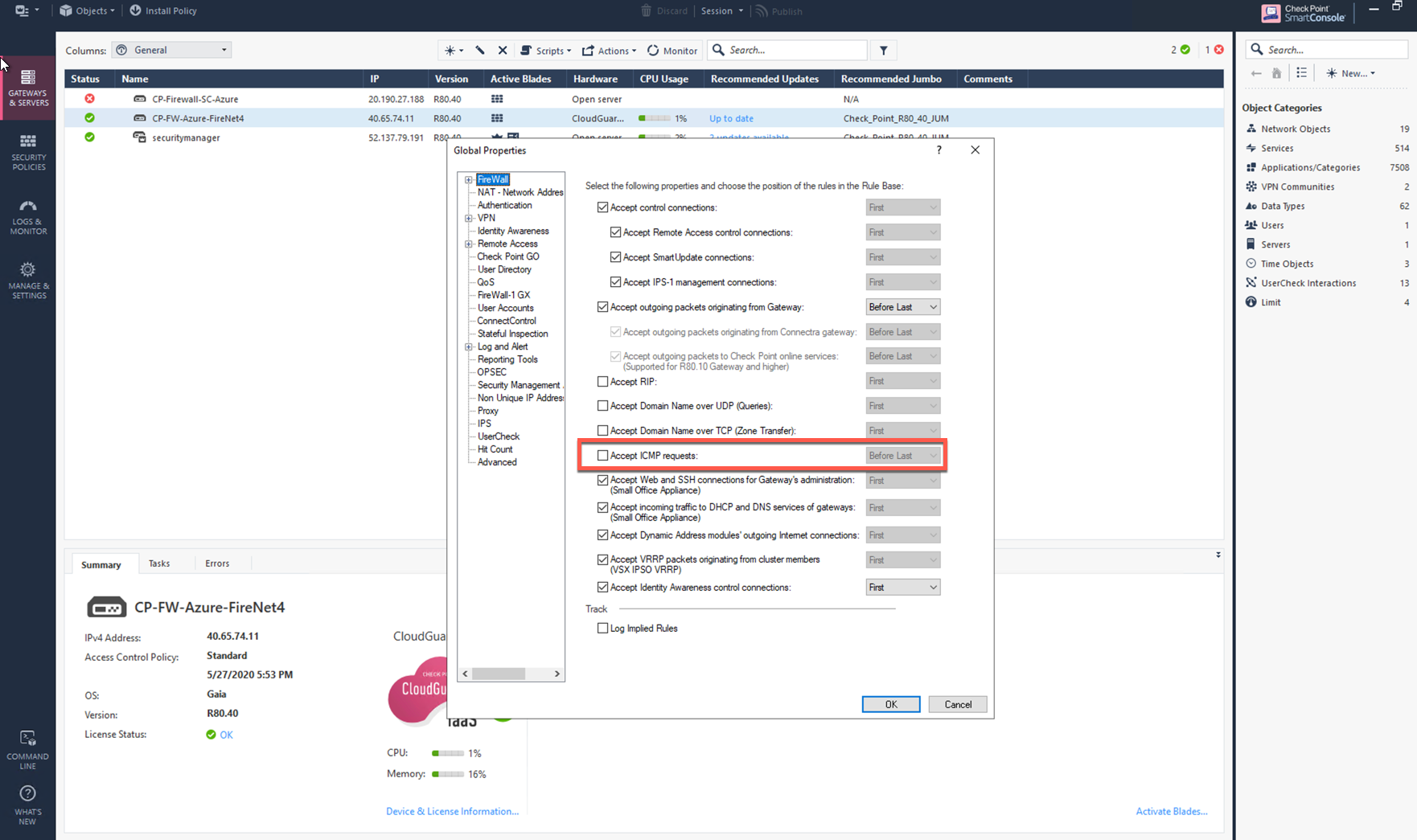
In the Check Point UI, navigate to SmartConsole > Global Properties > Firewall > Accept ICMP Requests.
CoPilot can also check firewall instance health on its LAN interface.