Extending VLAN Segmentation to the Cloud with Aviatrix Secure Edge
This document describes the Aviatrix Secure Edge solution to extend virtual LAN (VLAN) network segmentation into cloud.
Before reading this document, you should be familiar with the following:
-
Aviatrix Multicloud Transit Network architecture
-
Aviatrix Gateway High-Availability
-
Virtual LAN networking concepts
-
Virtual Router Redundancy Protocol (VRRP) concepts
Virtual Local Area Networks (VLANs) enables you to create network segmentation to maintain separation between Local Area Networks. Businesses may deploy network segmentation for additional security or to keep workloads in their network separate.
Aviatrix Secure Edge supports multiple VLANs and VRRP architecture. This capability enables you to segment your on-premises network traffic for your LAN network segments. For example, you can segment the workload in the cloud that supports PoS (Point-of-Sale) application to the PoS application at the Edge in that specific LAN segment only.
| VLAN and VRRP support is only available on the Aviatrix Edge Platform and Self-Managed Platform. It is not available on the Equinix Platform. |
VLAN TOPOLOGY
Single VLAN Topology
The topology below illustrates an Edge site with a single VLAN, Virtual Router Redundancy Protocol (VRRP), and the Edge Gateway deployed as the default LAN router.
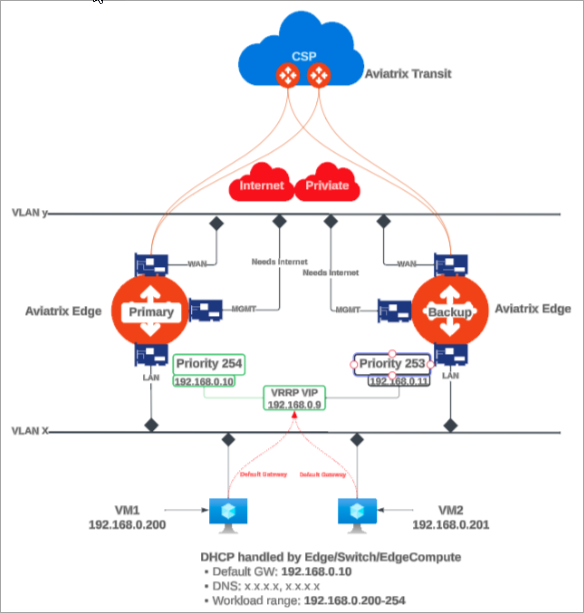
In this diagram:
-
The VRRP and VLAN segment is configured on the primary Edge Gateway.
-
The VLAN segment is automatically created symmetrically on the secondary Edge Gateway.
-
The VRRP Virtual IP is used by the LAN hosts as the Default Gateway IP.
|
Multiple VLAN Topology
The topology below illustrates an Edge site with multiple VLANs, Virtual Router Redundancy Protocol (VRRP), and Edge Gateway deployed as the default LAN router.
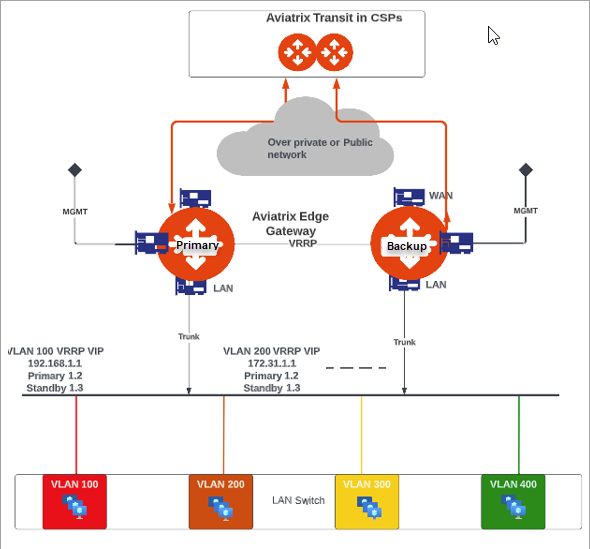
In this diagram:
-
The VRRP and VLAN segments are configured on the primary Edge Gateway.
For multiple Edge Gateways deployed on an Edge site, you configure the VLAN segments on each primary Edge Gateway. The VLAN segments must be configured with the same VLAN ID and CIDR across all the Edge Gateways on the Edge site. -
The VLAN segments are automatically created symmetrically on the secondary Edge Gateway(s).
-
The VRRP Virtual IP is used by the LAN hosts as the Default Gateway IP for the VLAN segments.
-
The Edge gateway provides the trunk interface connectivity to the LAN side switch.
|
Extending On-Premises VLAN Segmentation into Cloud
To extend on-premises VLAN segmentation into cloud involves these two steps.
Configuring VLAN Interfaces on the Edge Gateway
You can configure VLAN interfaces on the Edge Gateway during or after the gateway is created.
To configure VLANs for a new Edge Gateway, follow the instructions for:
To configure VLANs for an existing Edge Gateway, perform the steps below.
-
In Aviatrix CoPilot, go the Cloud Fabric > Edge > Gateways tab.
-
In the table, locate the Edge Gateway and click the Edit icon on its right.
-
In the Edit Edge Gateway dialog box, scroll to the Interfaces section and click LAN and enable VRRP, if applicable.
Parameter Description IP Assignment
The default is Static for static IP assignment on this LAN interface.
DHCP for dynamic IP address assignment is not supported.
VRRP
To enable Virtual Router Redundancy Protocol (VRRP) on the Edge Gateway, click this switch to On.
-
Click + VLAN Interface to add one or more VLAN sub-interfaces.
Parameter Description Interface CIDR
Enter the native VLAN interface IP address.
This interface is where untagged packets are sent.
Default Gateway IP, VRRP Gateway IP
Enter the Default gateway IP address.
-
If VRRP is enabled, enter the VRRP Gateway IP address.
-
If VRRP is disabled, enter the Default gateway IP address for the native VLAN interface.
Interface Labels
Enter a name to identify this native VLAN interface.
VLAN ID
Enter the VLAN ID.
VLAN ID must be a number between 2 and 4092.
VLAN Interface CIDR
Enter the VLAN’s interface IP address.
Default Gateway IP
Enter the Default gateway IP address for this VLAN interface.
Sub-Interface Tag
Enter a name to identify this VLAN interface.
When Edge Gateway high availability is enabled, the VLAN configurations are added to the secondary Edge Gateways. If the properties are shared, the fields are disabled on the secondary gateway and non-editable.
-
-
If multiple Edge Gateways are deployed on the Edge site, repeat the steps above for each primary Edge Gateway.
-
VLAN segments must be configured with the same VLAN ID and CIDR across all the Edge Gateways for the edge site.
-
You cannot edit the VLAN ID after it is configured. To edit the VLAN sub-interface attributes, it is highly recommended to delete and recreate the VLAN sub-interface configuration.
-
Associating VLANs to Aviatrix Network Domains
Aviatrix Secure Edge enables you to segment your on-premises network traffic through network domains and connection policies. The Edge Gateway routes on-premises and inter-VLAN traffic flow based on the network domain connection policies.
To segment the on-premises network traffic, you associate the VLAN segment and its workload in the CSP to the same network domain.
For example, the diagram below illustrates on-premises network traffic flow between the yellow and orange domains that are segmented.
-
VLAN 100 is associated to the same network domain as its workload in the CSP.
-
VLAN 200 is associated to the same network domain as its workload in the CSP.
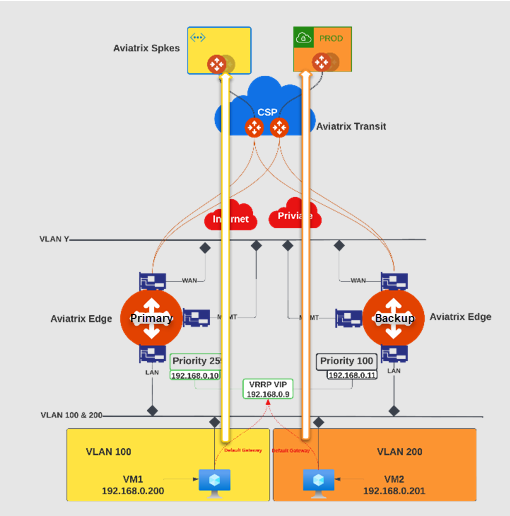
To create network segmentation between VLANs and Spoke VPCs Or VNets, you associate the VLANs and Spoke VPCs or VNets to network domains. When network segmentation is configured with multiple Edge Gateways using VLAN, the same VLAN ID is associated to the network segment across all the gateways for the edge site.
|
|
If VLANs are created or added after the network domain association is created, the association must be removed and reconfigured.
|
To associate VLANs to Aviatrix Network Domains:
-
In Aviatrix CoPilot, go to Networking > Network Segmentation > Network Domains tab.
-
To add a new network domain, click + Network Domain.
Provide the following information:
Parameter Description Name
Enter a unique name for this network domain.
A network-domain name can only have letters, digits, a hyphen (-), and an underscore (_). The name must start with a letter and must have 2-27 characters. For example, Dev_Domain.
After you create and save a network domain, you cannot change its name. Association
From the dropdown list, select the Spoke VPC/VNet and the VLAN that are in this network domain.
Connect to Network Domain
To connect this network domain to another network domain, from the dropdown list, select the other network domain.
This enables traffic flow between both network domains.
-
Click Save.
Disabling LAN and VLAN CIDR Propagation to the Transit Gateway
The Aviatrix Edge Gateway exchanges routes with the Transit Gateways. The Edge Gateway advertises the CIDRs associated with the LAN and VLAN interfaces to the Aviatrix Transit Gateway, by default. If you do not need LAN CIDR propagation, you can disable this feature.
| If there are workloads on the LAN or the VLAN CIDR, then disabling LAN and VLAN interface CIDR propagation may cause network traffic to be dropped, since Transit Gateway will not have learned the LAN or VLAN CIDRs. |
To disable LAN and VLAN CIDR propagation:
-
In CoPilot, go to Cloud Fabric > Edge > Gateways tab.
-
In the table, select the Edge Gateway for which to disable LAN CIDR propagation.
-
In the Edge Gateway’s Settings tab, expand the Routing section.
-
Click LAN/VLAN Interface CIDR Propagation toggle to Off.