Attaching an Aviatrix Transit GW to TGW
Attach the Aviatrix Transit Gateway and its VPC to the AWS TGW’s Aviatrix_Edge_Domain to allow the Aviatrix Transit Gateway to send and receive packets from the AWS Transit Gateway.
| An Aviatrix Transit Gateway can only be attached to one AWS TGW, and they need to be in the same region. To attach AWS TGWs from different regions, use the AWS TGW Peering tab. |
In this step, route entries are added to the two created private subnet route tables as described in the table below.
| subnet | route table | route entry | description |
|---|---|---|---|
-tgw-egress (for eth1) |
-tgw-egress |
0.0.0.0/0 → TGW |
for traffic from Aviatrix Transit GW to TGW |
-tgw-ingress |
-tgw-ingress |
0.0.0.0/0 → eth1 |
for traffic from TGW to Aviatrix Transit GW |
|
There is no IPSec tunnel between the AWS Transit Gateway and the Aviatrix Transit Gateway. The Aviatrix Gateway behaves as an EC2 instance in a Spoke VPC (The Aviatrix Edge VPC) attached to the AWS Transit Gateway, as shown in the diagram below. Such a setup allows the Aviatrix Edge VPC to leverage the high performance provided by AWS Transit Gateway. |
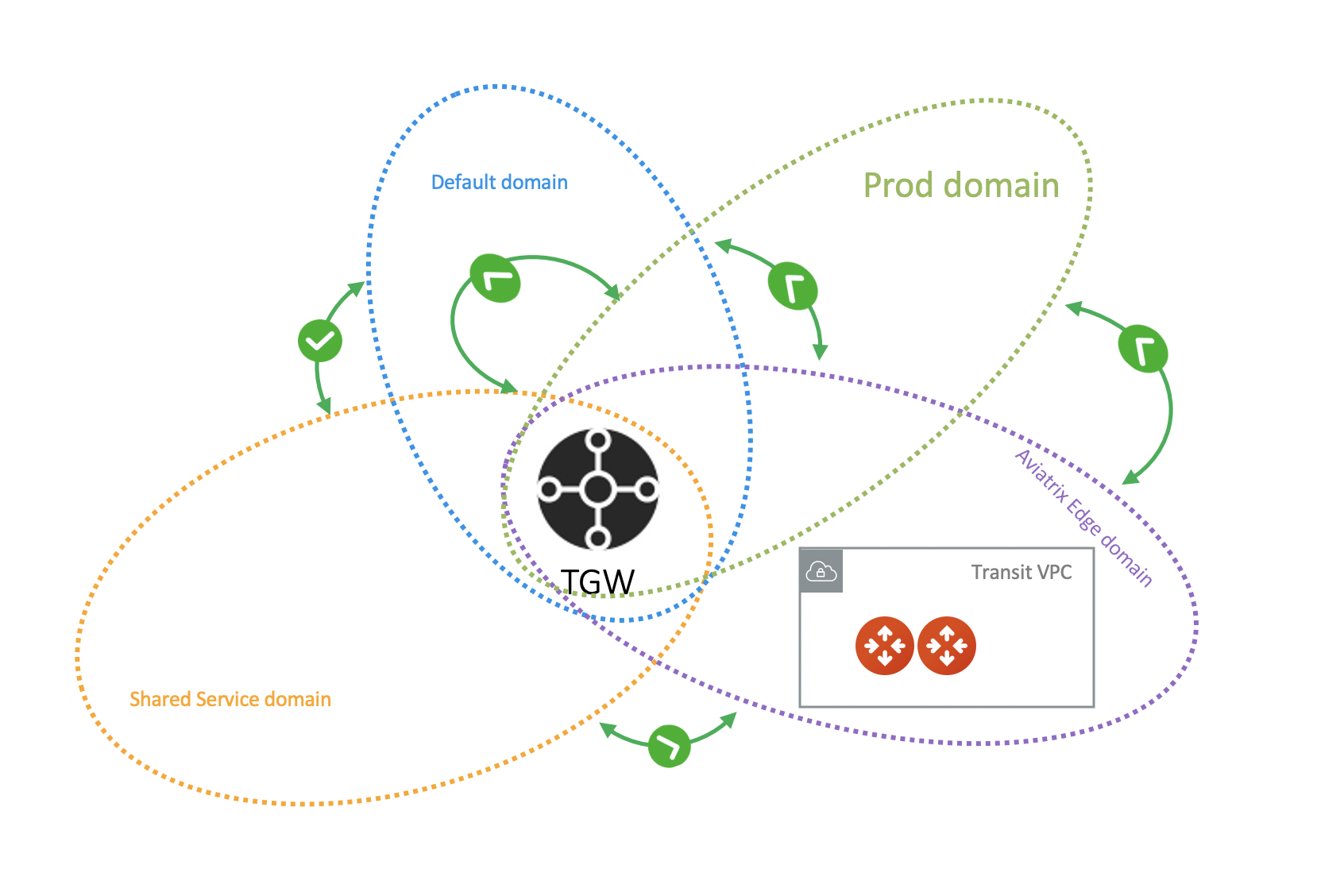
To attach an Aviatrix Transit Gateway to an AWS TGW:
-
Go to Aviatrix CoPilot > Networking > Connectivity > AWS TGW tab > select the AWS TGW > select the Transit Gateway tab.
-
Click Attach Transit Gateway. Note that you can only attach one Aviatrix Transit Gateway at a time.
-
Enter the following information:
| Setting | Value |
|---|---|
Transit Gateway |
Click on the dropdown menu and select an Aviatrix Transit Gateway. Note that this gateway must be in the same region as the AWS TGW. |
Network Domain |
Aviatrix Edge Domain is the only option. |
Click Attach.
After you finish these steps, your hybrid connection using Aviatrix Transit Gateway for TGW setup is complete. You will also be able to perform network segmentation for the AWS TGW domains that are now attached to the Transit Gateway.
In the above example, if you have any Spoke VPCs attached to the prod_domain, EC2 instances should be able to communicate with on-prem. Make sure instance security groups and any on-prem firewalls are configured properly.